Data doesn’t lose itself. People lose it.
Careless users mishandle it. Malicious users walk out the door with it. And compromised user accounts are hijacked to steal it. Legacy solutions are not only siloed and limited to one channel, but they also fail to leverage user behavioral data. Information protection is a people problem. A new approach is needed.
Transform your information protection with a human-centric, omni-channel approach
Proofpoint's adaptive, human-centric solution transforms information protection across email, cloud, endpoint, and web by leveraging AI-augmented data classification, user behavior analysis, and threat context.
This integrated approach enables organizations to preemptively address data loss and insider risk from careless, malicious or compromised users, ensuring comprehensive coverage.
Trusted by over 6,000 organizations including more than half of the Fortune 100

Our cloud-based architecture minimizes operational costs and simplifies scaling, while advanced content scanning swiftly identifies sensitive information, and behavioral insights prevents unknown risk and uncovers user intent. In a single, consolidated platform, we reduce the burden on IT teams, mitigate reputational damage, reduce customer attrition and address compliance risks—all while upholding user privacy.
Behavioral visibility
We understand user behavior patterns with behavioral AI, CERT institute-based rules, and behavioral research to detect anomalies that may indicate risky activities or potential insider risk and provide early warnings and preventing data leaks or breaches.
Advanced content scanning
We accurately identify and classify sensitive data across all communication channels, enabling proactive protection tailored to the specific needs of the organization.
Solve the use cases that matter most
We enable you to tackle your most pressing use case first. As you expand your use case coverage, you can stay within a single solution approach to streamline policy management, enhance incident response, and gain comprehensive visibility into all data interactions, significantly improving overall security posture.
Managed services
Shorten time to value with our highly skilled experts who help you design, implement and co-manage your DLP and insider risk program.
Proactive information protection that analyzes user behavior and content
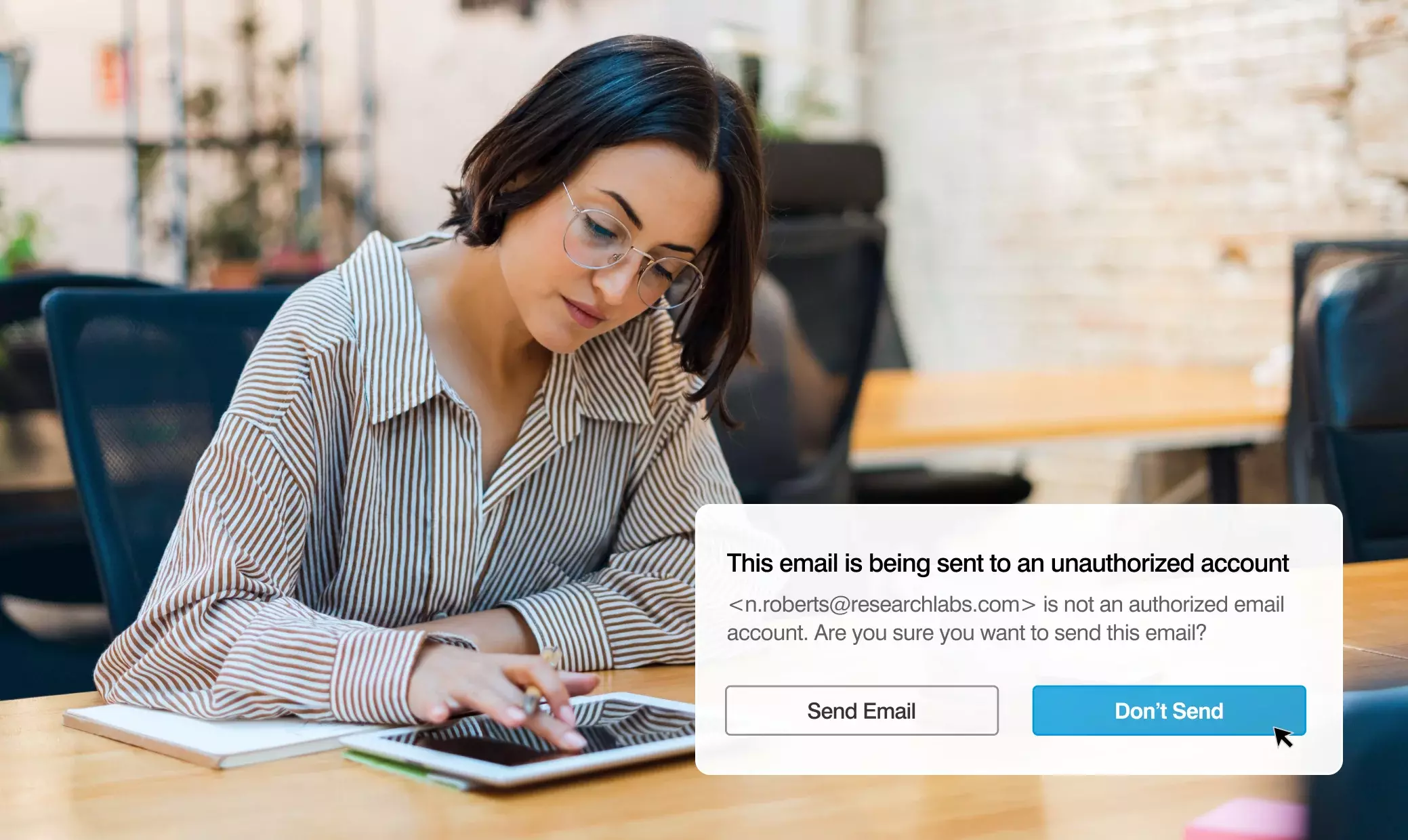
Prevent email misdelivery
Adaptive Email DLP uses behavioral-AI to prevent accidental and intentional data loss over email, reducing risk and remediation cost – you can’t stop any other way.
Enforce Email DLP and Encryption policies
We protect sensitive data and automate compliance with our Email DLP and Encryption solution, enabling you to maintain strict control over your email communications. Through our email threat protection platform, we manage and enforce DLP and encryption policies, meticulously scanning and analyzing sensitive content in messages and attachments.

Mitigate data loss
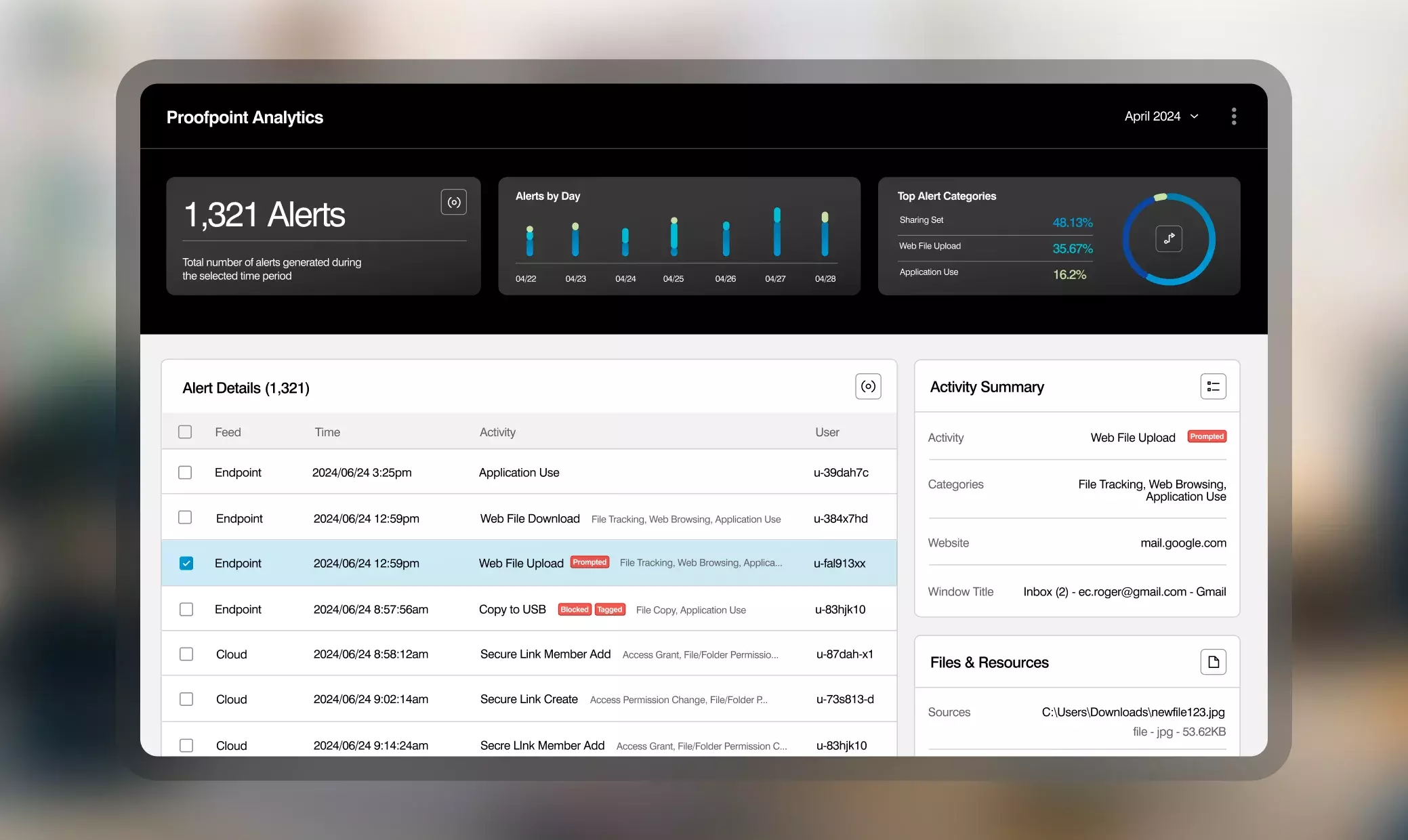
Modernize your DLP program with human-centric data loss prevention across email, cloud and endpoint. Rich context around content and user behavior surfaces data exfiltration by careless, malicious and compromised insiders. Triage, investigate and resolve alerts faster. Deploy quickly, scale automatically and maintain with ease. Service options to guide, measure and report on program success.
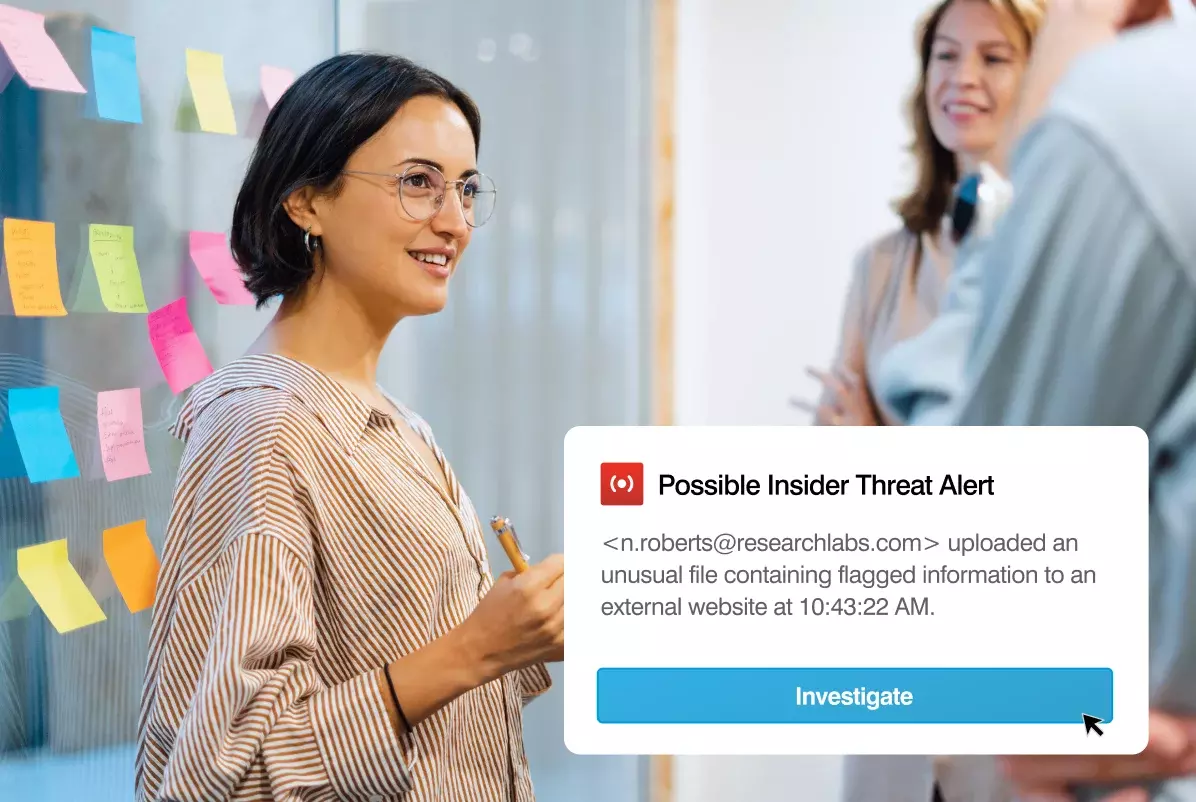
Contain insider threats
Safeguard data from malicious, careless and compromised insiders. Proofpoint gives you the "who, what, where, and when" you need before, during and after an incident to determine user intent and the best response. Detect risky behavior and data interaction in real time. Service options to guide program success.
Intelligent compliance
Intelligently detect misconduct in seconds across an array of popular e-communication platforms. Proofpoint provides an AI-based platform that helps unify, manage, store, investigate and supervise a vast array of digital communications for corporate and regulatory compliance protection.
“Before Proofpoint, it was the Wild West.
We relied on email archives, and there was no context behind threat information. There was a lot of deniability. Now we can piece together what happened and come up with hard evidence when we need it.”
Simon Knox
IT Director, Your World Recruitment Group
The latest resources on defending your data

2024 Data Loss Landscape Report
Read More
Redefining Data Loss Prevention (DLP)

Defend Data and Manage Insider Threats Solution Brief
Protect more than your people: Defend Data
See Product Packages




