Business email compromise (BEC) and email account compromise (EAC)—a collective $26B problem—are issues that organisations of all sizes, in all industries, must address.
Our “Combatting BEC and EAC” blog series dives into account takeover fraud prevention in your organisation using Cloud App Security. Each post focuses on one of seven key steps. We tackle the third in this blog post: cloud app protection.
Compromise Email Accounts - Priceless for Threat Actors
Email Account Compromise (also referred to as account takeover fraud) is a cyber attack that attempts to gain unauthorised access and control of your employees' email accounts. Attackers use tactics such as password spraying, phishing, malware, 3rd party application authentication tokens, and brute force attacks to compromise email accounts. But regardless of the tactic they use, their ultimate goal is to become you. And, once they have access to your legitimate account, they can carry out many other crimes, including BEC or email fraud.
Once your email account is compromised, attackers now have unfettered access to not just the victim's email. Still, all the applications associated with your cloud account - documents in file shares, key meetings with clients or partners in the calendar, corporate directory, notes from projects or meetings. They use this access to execute the next step— conduct extensive reconnaissance of your organisation to either steal data or fraudulently request payment from your suppliers, partners, or customers.
More importantly, when they've identified the opportune moment to strike (e.g. when an invoice due), emails sent from a compromised account will be virtually indistinguishable from legitimate email. These messages have the same display name and domain name, and they will pass email authentication protocols (SPF, DKIM, DMARC) because they are sent from a genuine email account.
Proofpoint threat research has observed that attackers often combine EAC with impersonation tactics (e.g. display name spoof, domain lookalikes) as a means to maintain the deceptive email discussion with the target. In several supplier fraud attacks, the threat actor inserted a new email address using a lookalike domain into the cc or reply-to field.
Regardless of their strategy, attackers are here to get in your cloud accounts to steal your money. For account takeover fraud prevention, your employees may unconsciously overlook these serious threats and can go about their work without noticing the impact it can have on your business.
Account Takeover Fraud Prevention- A Critical Element to Combat Email Fraud
As attackers continue to blend email and cloud attack vectors, it's critical that organisations implement multi-layered defences. Proofpoint's Nexus Threat Graph correlates data across multiple attack vectors - email, cloud, network and social media - to better protect you from email fraud attacks. Here are three ways Proofpoint can help you mitigate EAC risk.
1. Monitor for compromised accounts
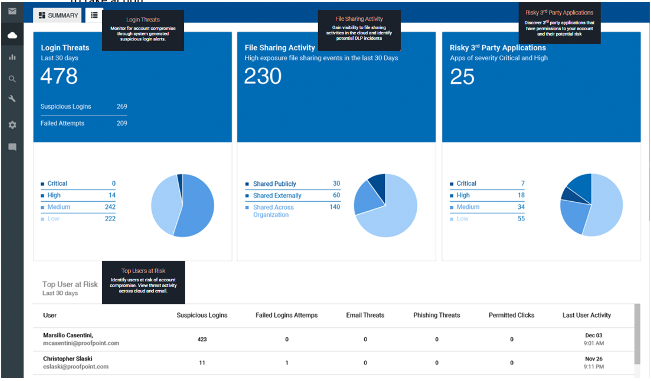
Proofpoint protects your customers, partners and employees from threats to your cloud apps by detecting brute-force attacks and identifying suspicious logins. With visibility into both the cloud and email threat vectors, we can connect the dots between credential phishing email attacks and suspicious logins to identify the top users at risk within the organisation. We also show high exposure file-sharing events that could be a potential data loss incident and leaked sensitive data through a compromised attack. We even identify third-party applications with overreaching permissions to email, calendars, contacts and files. All this insight provides you with the visibility of any potential email account compromise incident and the necessary data to take action.
2. Prevent account takeover
For both email account compromise and business email compromise prevention, our threat intelligence monitors over ten million cloud accounts and shares that intel across all our customer base. It can automatically block nefarious logins and prevent further damage.
Blocking risky third-party apps is another way we prevent account takeover. Many useful third-party apps add more features to Office 365, G Suite, Box and other platforms. But some are poorly built or overtly malicious. Attackers use third-party add-ons and social engineering to trick users into granting broad access via token-based authentication to your cloud apps. Once an OAuth token is authorised, access continues until it's manually revoked.
We have a catalogue of more than 46,000 applications with over 50 attributes per app. This helps you identify vendor credibility, vulnerabilities and security and compliance gaps. Our technology can discover and control third-party add-ons, including malicious ones. Our powerful analytics allow you to grant the right access levels to third-party add-on apps based on the risk factors that matter to you.
3. Engage Remediation Capabilities
When we detect a high-risk suspicious login based on threat intelligence and user behaviour analytics, we can notify the admin immediately. From there, security teams can configure and apply risk-based policies based on the user's role, their device and threat intelligence we have on the user and the attacker. For example, we can revoke a cloud session, suspend the user account, force a password change, or do both.
With our multi-layered approach, you get visibility and control across cloud and email threats. You can protect your organisation from EAC and subsequent financial loss via fraudulent payment requests.
To find out if your organisation is protected against BEC and EAC attacks, take our assessment here.
