A key finding in Gartner’s 2021 Market Guide for Security Awareness Computer-Based Training is that “The human element (85%) continued to be a primary catalyst for data breaches over the last 12 months, with phishing accounting for 36% of breaches.”
This finding is evidence that attackers are targeting people rather than vulnerabilities in an organization’s IT infrastructure. Human error caused by careless users who fall for social engineering attacks has become organizations’ greatest threat. And that’s why user education is one of the most important things you can do to protect your organization.
In its Market Guide, Gartner provides key findings and recommendations that organizations should use to evaluate security awareness solutions. Beyond check-box training, measurable programs, content diversity, centralized management and more were specifically called out by Gartner. Here’s how industry-leading Security Awareness Training from Proofpoint delivers on all of these fronts:
Beyond check-box training
According to Gartner, “Security awareness is more than phishing simulation and computer-based training. Leading programs leverage vendor platforms that enable and augment the execution of a multichannel, context-specific and employee-centric approach to educate employees and change behaviors.”
Proofpoint takes a holistic approach to security awareness training that goes beyond phishing simulations and compliance check-box training. We’re here to help you improve security outcomes. And to help your organization build a culture of security awareness by shaping users’ existing behavior, Proofpoint organizes our solution into three key steps ¾ ACE (Assess, Change Behavior and Evaluate).
The ACE framework provides the methodology for organizations to continuously assess, execute and monitor security awareness programs and campaigns.
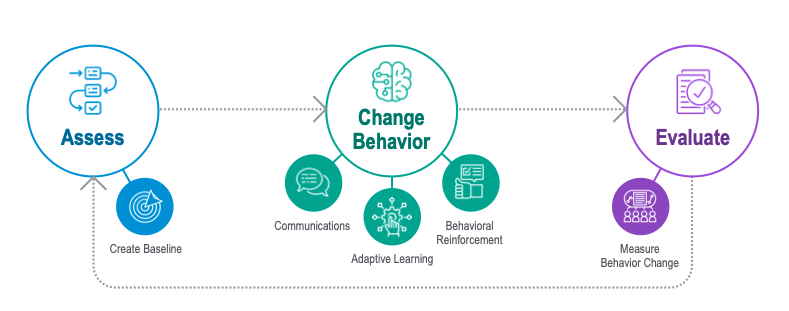
Figure 1: Proofpoint Security Awareness Training adopts the ACE framework, which goes beyond check-box training to help organizations build a culture of security awareness
- Assess: The first step in the ACE framework is to assess user knowledge and skills to establish your baseline and identify user vulnerability. Proofpoint provides various tools, such as phishing simulations and knowledge assessments, to help you gauge user knowledge and vulnerabilities.
- Change behavior: Next is changing unsafe behavior, and Proofpoint has incorporated communication tools, such as threat alerts and newsletters; adaptive learning, including microlearning sequences based on domain and skill level; and reinforcement mechanisms, like threat-guided training, one-click reporting and Teachable Moments, to help you execute on your program, make an impact and change behavior for the better.
- Evaluate: Finally, our solution helps you regularly measure and evaluate your program to reach the results you desire. Our recently released CISO Dashboard helps you level up your program’s visibility, so you can better communicate that success to your executives, focus on areas of improvement, benchmark against your peers, and see how you’re improving over time.
Incorporate key performance indicators
Gartner reports that “Providers are increasingly using scoring methodologies with the intent of helping organizations quantify the human risk element and helping to deliver more personalized security awareness program content.”
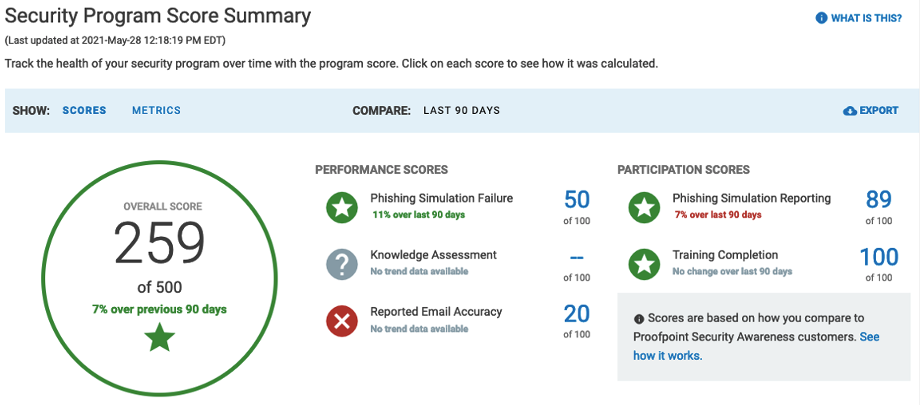
Figure 2: The Security Program Score Summary helps you communicate program performance quickly to your chief information security officer (CISO)
The unique CISO Dashboard from Proofpoint helps you better track user performance and program participation over time. You can even benchmark user performance against industry peers. The dashboard identifies the users who are most vulnerable and provides a User Vulnerability Summary. For customers who use Proofpoint Security Awareness Training as part of our Threat Protection Platform, you get additional insights into top clickers and Very Attacked People™ data. With those insights, you can run a more focused, high-impact program based on user vulnerability.
The real-time reporting feature allows you to see progress quickly and provide updates. You can pull up-to-date information on who has completed assignments (and who hasn’t) and dig deeper into assignments and user behavior as needed. This allows you to ensure the completion of assignments and keep stakeholders in the loop.
Content diversity and centralized management
Gartner recommends that organizations “Construct truly context-specific and employee-centric security awareness programs by being prepared to use multiple content sources for security training curriculums where necessary.” Additionally, we feel one of the key findings in the Market Guide indicates that most organizations are looking for centralized management of their security awareness programs.

Figure 3: Proofpoint provides diverse training materials to support various security topics that best align with user roles, competencies and learning styles
Proofpoint provides a broad assortment of security training materials to support email, compliance, insider threats, cloud threats and other critical topics in the modern threat landscape. Newly added engaging content includes microlearning, choose-your-own-adventure, and edgy and humorous styles. We allow you to customize your curriculum with content that aligns with user roles, competencies and learning styles and supports more than 40 languages.
Meanwhile, Proofpoint provides powerful administrative capabilities to support complex programs. You can run parallel campaigns by department, location and role, supported by single sign-on (SSO) and Active Directory sync. You can also discover and manage new content easily through a single console. You can preview, customize, review, assign and export the content, allowing you to streamline the assignment process.
Contextual and timely awareness
Gartner also recommends“Increase the effectiveness of their program by augmenting traditional regular, curriculum-based training approaches with “in the moment” communications that alert an end-user prior to, or directly after, they have undertaken an action that exposes the organization to cybersecurity risks.”
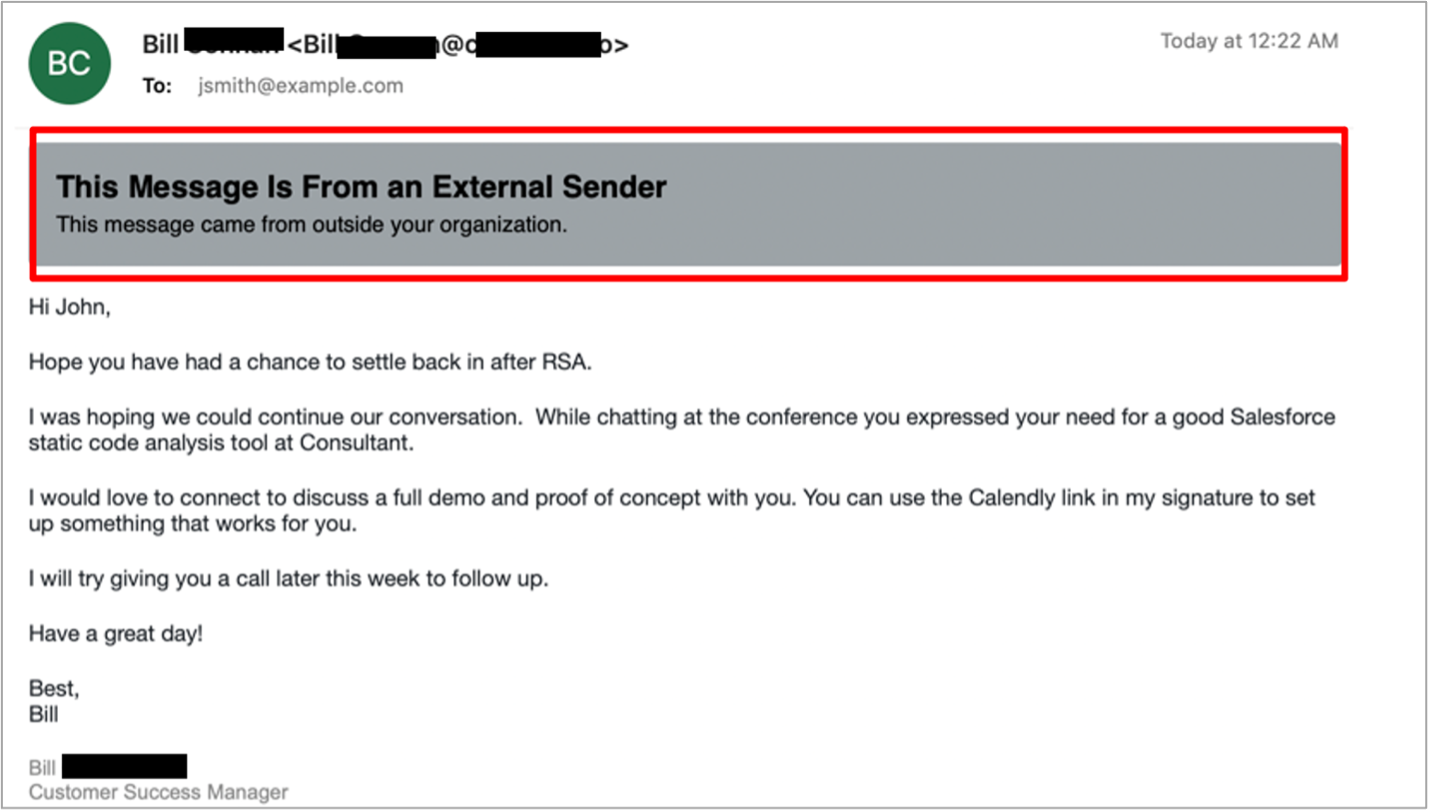
Figure 4: The Email Warning Tag feature allows users to leverage their awareness “in the moment” and alerts them before they take an unsafe action
The Email Warning Tag feature within the integrated Threat Protection Platform from Proofpoint guides your users to take extra caution and make more informed decisions about uncertain emails. The feature allows users to leverage their awareness “in the moment” and alerts them before they take an unsafe action. Users can report a suspicious email directly from the warning tag itself, which reinforces real-time reporting behavior.
Furthermore, the depth of threat intelligence that Proofpoint provides helps you stay ahead of attackers. We equip you with monthly released threat-centric education and alerts. That way, you can quickly give your users a heads up on emerging and trending threats. And by making risks and lures easier to comprehend, the entire education experience becomes more relevant to users.
While the ability to automate threat response was not called out specifically in the new Market Guide from Gartner, our customers routinely share positive feedback with us about our CLEAR (Closed-Loop Email Analysis and Response) solution. With CLEAR, our customers reduce their remediation workload by up to 90%. It saves them time and effort by automating and streamlining the following processes:
- Analyzing user-reported messages with powerful threat intelligence from Proofpoint
- Notifying users about the analysis result of their reported messages
- Finding and pulling back similar messages delivered to other employees
Augment with managed services
For those who struggle with budget constraints or gaps in the security awareness expertise of their in-house staff, Gartner suggests evaluating security awareness training as a managed service.
Proofpoint offers security awareness training as a managed service. Our experts can help you design and manage programs that best match your goals. We save you time and effort by focusing on actionable data while managing all administrative and deployment tasks. You can focus on other strategic IT initiatives while our experts apply the best practices for you.
Learn more
Download the Market Guide from Gartner today to learn more about what to look for in a security awareness computer-based training solution. Also, explore the Proofpoint website to see how we deliver on Gartner’s recommendations and key findings on security awareness computer-based training.
Gartner, Market Guide for Security Awareness Computer-Based Training, 26 July 2021
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
