Microsoft is the productivity partner for most enterprises and organizations today. These organizations trust Microsoft Office products as secure cornerstones for their cloud migration. This same widespread adoption attracts attackers to target enterprises’ productivity partners. Proofpoint has written about this in the context of third-party OAuth abuse, threat actors using Microsoft services for attacks and cloud credential compromise campaigns from early 2022.
Microsoft Sway is such a tool for attackers. One of the less-commonly used apps in the Microsoft 365 suite, Sway allows users with Microsoft accounts to combine text and media to create a presentable website.
In 2019 and 2020, there were reports of “PerSwaysion” attacks and other phishing campaigns using Microsoft Sway. In this blog, we build on prior research reports by exploring the actual techniques in depth through a proof of concept (POC). We discuss how attackers can use Microsoft Sway to easily circumvent Microsoft’s basic protections in the app to phish users and distribute malware within organizations.
An attacker can weaponize a Sway page by either compromising a Microsoft 365 account within the target organization (to phish more users) or creating a Sway page within their own Microsoft 365 account outside the target organization. The malicious Sway pages function like weaponized webpages, except they’re hosted on Microsoft infrastructure. It’s also very difficult for end users receiving attacks in Sway to spot any indications of malware or phishing.
Proofpoint recommends educating users to be aware of Microsoft Sway-based embedded phishing and malware risks, set up comprehensive account compromise detection using a cloud access security broker (CASB) solution, and isolate end user traffic when users click on links within Microsoft Sway pages. If need be, limit usage of Microsoft Sway in your cloud environment.
Using Microsoft Sway to phish users
Most phishing attack vectors involve clicking a direct link to a phishing page. Some of the previous attacks within customer environments we observed used this method. Microsoft uses a warning pop-up to attempt to discourage users from falling prey to such phishing attempts.
In this first visual of a Sway page below, we show a potential phishing attempt using a hyperlinked URL to a malicious phishing page.
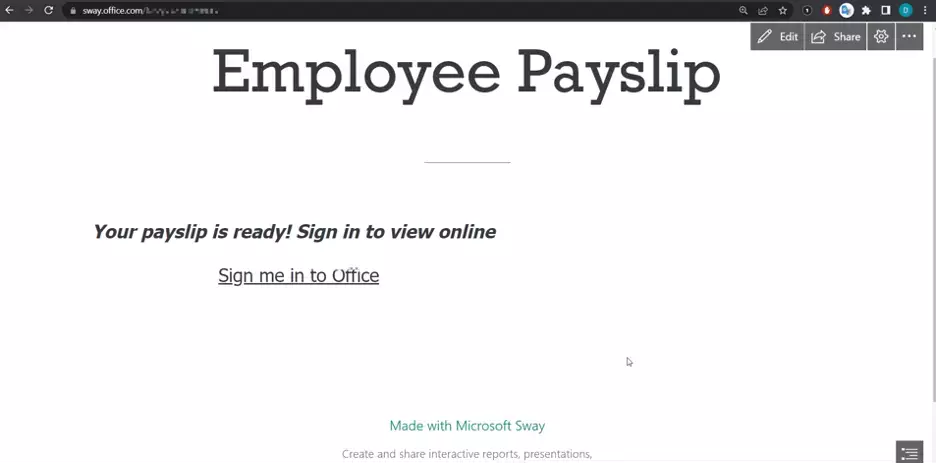
Figure 1. A simulated phishing attack using a malicious URL within a Sway page.
The Sway page in this example contains a seemingly important “Employee Payslip” with a hyperlink—“Sign me in to Office”—to view it. Unbeknownst to the user, the link is to a phishing page. When the user clicks on the link, Microsoft has a warning pop-up to dissuade the user from going to the eventual phishing page. Users can still click the “OK” button and go to the phishing page, but at least they’ve been warned.
However, Proofpoint cloud security research indicates that attackers can phish users using an embed method within Microsoft Sway without a warning pop-up. This involves a user clicking on a link in an embedded malicious document within a Sway page.
The steps to compromising a user’s account using the embed method are as follows:
- Create or edit a Sway page
- Embed a Microsoft-supported document (such as .docx, .xlsx, .pptx and .pdf files) that contains a phishing link in the new Sway page
- Include some common social engineering methods to make the malicious Sway page appear convincing
- Share the Sway page with users within or outside the organization (through email, chat, text messages or any other messaging platform)
- Redirect users who click on the phishing link in the embedded document to a phishing website that asks for their credentials
In the second visual below, we show a phishing attempt using the same phishing page, but this time it’s embedded within the Sway page. This is a socially engineered .docx file with a Microsoft SharePoint logo, a blurred pay slip and an inviting link to click on, which is embedded in the Sway page. When the user clicks on the “View online” link, they’re redirected to a phishing site without any warning.
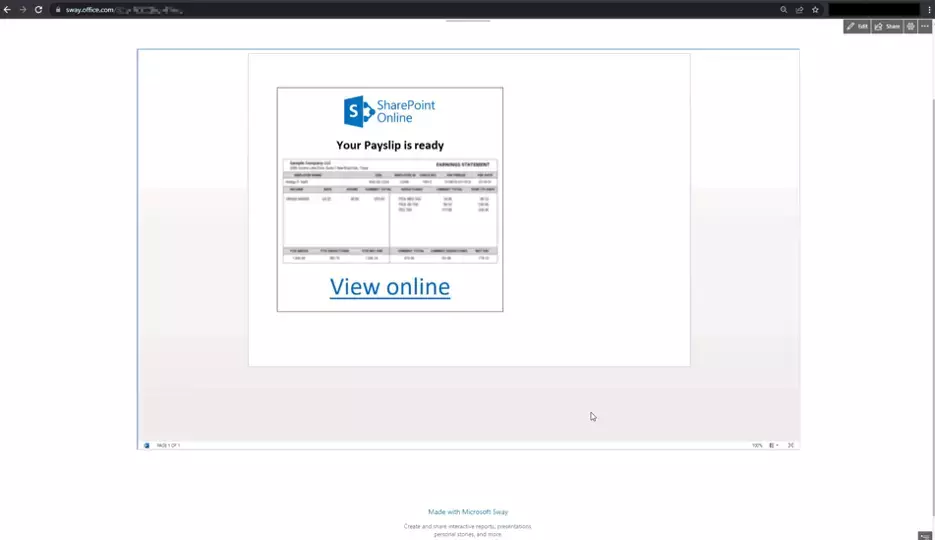
Figure 2. A simulated phishing attack using a malicious URL in an embedded Word document within a Microsoft Sway page.
In the background, the attacker would publish a Sway page that contained an embedded Microsoft Word document stored on SharePoint, which contains a phishing link. When embedded, Sway will create an iFrame of the document. It’s essentially a window to an external resource—a Word document that resides outside of Sway. Now the document is no longer “governed” by Sway; it complies with the rules of the source within the iFrame.
It’s easy to see how attackers could potentially use this basic feature to create and distribute seemingly benign Sway pages that contain phishing URLs or alternative threats. The actual dangerous link will appear as a generic Sway page, hosted on the office.com domain, in the following format: https://sway.office.com/<16 random chars>.
Attackers can also use various social engineering techniques in the referenced Word document to make the page look legitimate to potential victims.
Using Microsoft Sway to distribute malware
Microsoft only allows uploads of media files in Sway pages, and it actively blocks uploads of executable files. However, attackers can still use Sway to distribute malicious executables by embedding the hosted malware within Sway. They can:
- Create or edit a Sway page.
- Host a malicious file on Microsoft OneDrive or SharePoint and embed it in the new Sway page.
- Publish the new Sway page after including some common social engineering methods to make it look convincing.
- Send it to users within the organization, who may open the suspicious file containing malware. (Note: In the case of OneDrive, the file is automatically downloaded, while SharePoint users may have to download the file manually.)
As an aside, research for “The Human Factor 2022” report from Proofpoint found that popular cloud services like Microsoft OneDrive, Google Drive and Dropbox are the most commonly used services to host attackers’ campaign infrastructure.
In the following GIF, we created a simple POC in which a malicious executable can be embedded within a Sway page. This includes multiple social engineering methods—using a .com file format, saving the document within SharePoint and featuring a blurred pay slip on the Sway page.
SharePoint, in this example, is unable to handle the .com file format, meaning the user will fail to run it directly from the Sway page. Instead, after clicking the “Open” button, it will simply disappear. The user is then likely to download the file to their local machine, after which the nefarious code runs immediately.
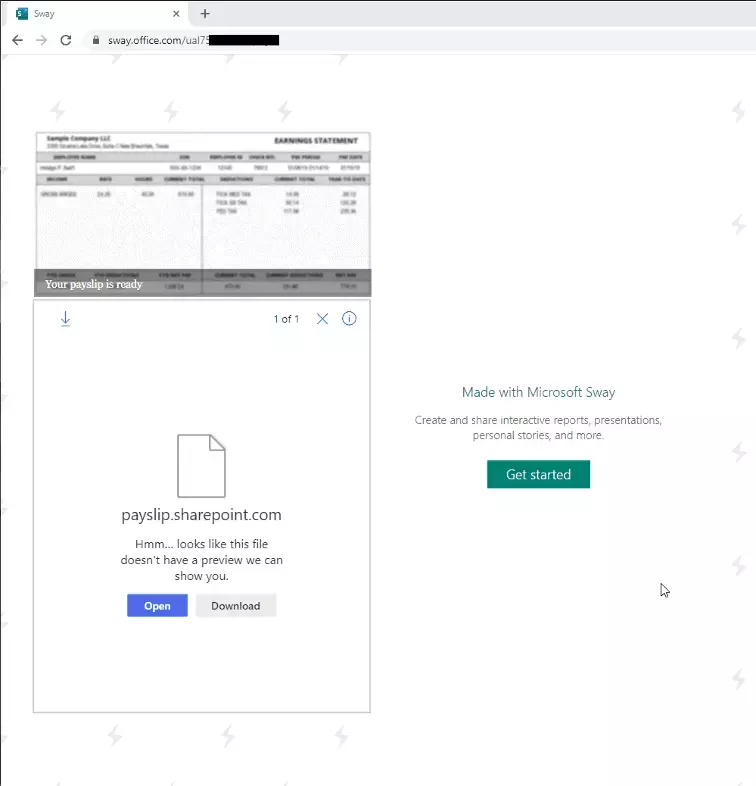
Figure 3. Malware execution method using Sway as a delivery platform.
In the background, the attacker would need to follow these steps:
- Save the file in Microsoft SharePoint or OneDrive (as they’re approved or supported by default)
- Change the file name to something more innocuous
- Create the embedding code for the file
- Add the embed code into the Sway page
- Edit the embed code to point to the shareable link
Using Microsoft 365 apps to hide the malware and changing the file name to hide the executable file format makes it harder for everyday users to suspect the embedded malicious file. Similar to the above-described phishing scenario, the Sway page will appear benign, hosted on the office.com domain, in the following format: https://sway.office.com/<16 random chars>.
An attacker can potentially use a Sway page to distribute malware to other Microsoft 365 users. It’s easy to launch malware hidden within a Sway page that impersonates an important document.
Recommendations to protect your organization
Following are ways to help your organization defend against Microsoft Sway-based embedded phishing and malware risks:
- Security awareness: Educate users to be aware of these risks when using Microsoft Sway.
- Cloud security: Identify attackers creating or editing malicious Sway pages within your cloud accounts. This requires the detection of the initial account compromise and the post-access suspicious file activity within Microsoft Sway.
- Web security: Isolate the end user traffic from Sway pages from the rest of your network.
- Review Microsoft Sway usage: If you’re facing these types of attacks regularly, limit usage of Microsoft Sway in your cloud environment.
Threat actors constantly seek new ways to steal users’ credentials and acquire access to users’ accounts. As this blog illustrates, Microsoft Sway serves as a suitable platform for various forms of cloud attacks since it’s a legitimate application hosted on a seemingly benign domain.
Contact Proofpoint to learn more about how we can help your organization protect cloud apps and secure Microsoft environments.
