Terminology like behavioral analysis and AI/ML (artificial intelligence and machine learning) are so overused in cybersecurity marketing, it’s easy for information security pros to tune them out. And the truth is, it’s probably a good thing to take these terms with a grain of salt.
In some respects, these models are nothing new. Proofpoint has been using AI/ML technology all along to block malicious and unwanted emails. This field is also advancing at a stratospheric pace, enabling new capabilities and use cases for organizations to protect themselves. So, it’s not just important to do behavioral analysis and AI/ML, but also do them well.
Let’s take a deeper dive into the specifics of how Proofpoint uses these technologies to tackle email threats. (Or feel free to watch our webinar replay, “Using Behavioral Analysis and AI/ML to Stop Phishing Attacks,” featuring our data science team.)
New Supernova Behavioral Engine builds on Supernova for BEC
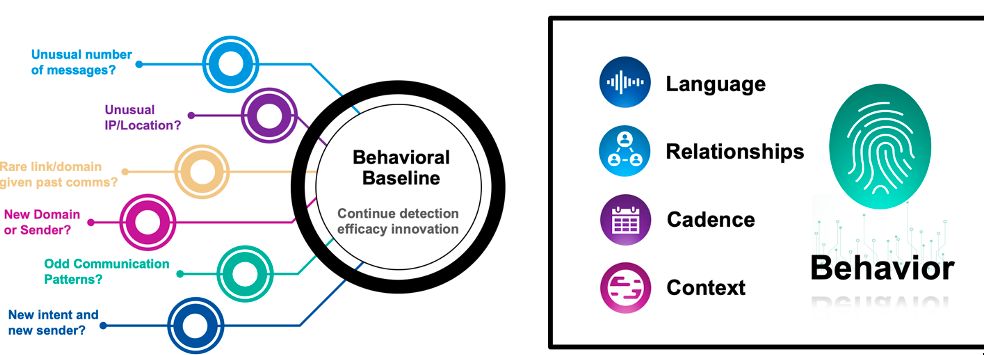
Figure 1. The new Supernova Behavioral Engine analysis from Proofpoint uses language, relationships, cadence, and context to detect anomalies and prevent threats in real-time using AI/ML.
In Q2 2022, we released our Supernova Behavioral Engine to all email security customers globally, at no additional cost and with no additional configuration needed. Supernova Behavioral Engine better detects email patterns that fall outside of the norm, improving detection of all threat types, from business email compromise (BEC) to credential phishing and much more. It builds off the work we did with Supernova as part of Advanced BEC Defense in 2021, incorporating signals and learnings from that engine.
Here are some of the signals Supernova Behavioral Engine will use to determine if a message is malicious (as the engine evolves, we’ll add more signals):
- Unknown sender, i.e. someone who has never communicated with you before
- Uncommon language or sentiment, such as discussing a financial transaction for the first time)
- Uncommon URL or subdomain
- Unusual SaaS (software-as-a-service) tenant, which is often a sign of supplier account compromise
- Unusual SMTP infrastructure, which is likewise indicative of possible account compromise
Supernova Behavioral Engine doesn’t just include detection, though. It will also tag messages from uncommon senders using email warning tags with “Report Suspicious” to give the user a heads up with valuable context, and even allow them to report the message directly to the incident response team or our automated abuse mailbox solution. And customers will be able to see behavioral insights directly in the Proofpoint Targeted Attack Protection (TAP) Dashboard when messages are condemned.
The new Supernova Behavioral Engine improves our already leading efficacy, while ensuring low false positives for customers. We’re also committed to transparency, especially given how much vendor noise there is around the use of AI/ML: our current false positive rate is 1 in over 4.14 million, which leads the industry and which we will continue to investing in improving. And this data science approach is nothing new to Proofpoint.
A leading data science team with some of the largest global cybersecurity data sets
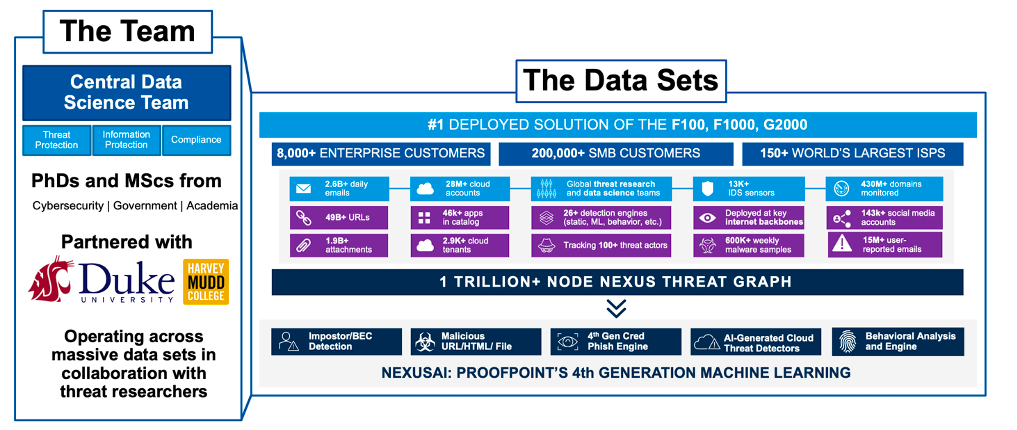
Figure 2. Proofpoint uses a centralized data science team working with some of the largest cybersecurity data sets in the world to train our models.
Our centralized data science team has been using advanced techniques for more than 20 years to detect and stop advanced threats. The team works across Proofpoint product lines and includes professionals with advanced degrees in cybersecurity, government, and academia. We partner with Duke University, Washington State University, and Harvey Mudd College among other institutions to ensure our skills and technology are cutting edge.
And with the Proofpoint Nexus Threat Graph, which has access to massive cybersecurity data sets across email, cloud, networks, domains and more, our teams can feed and improve our models more effectively. Being the number one deployed solution of the Fortune 100, Fortune 1000, and Global 2000 and having more than 200,000 small and midsize (SMB) customers means we can feed our models with data more quickly and detect threats faster and with greater accuracy.
Without a substantial corpus of data, these models become ineffective at identifying threats and sometimes even counterproductive due to excessive false positives.
Supernova for BEC and Supernova Behavioral Engine can improve detection across the board
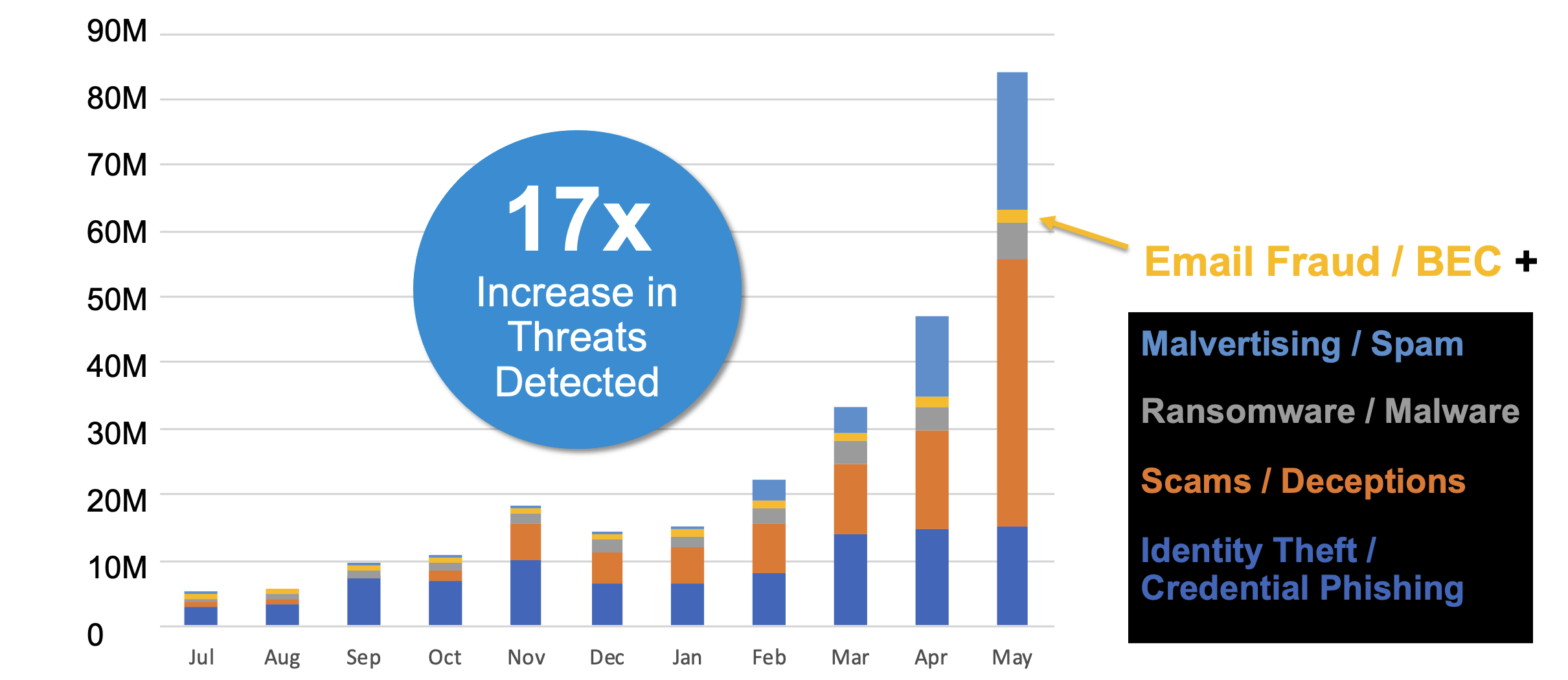
Figure 3. Supernova, released by Proofpoint in 2021 as part of our Advanced BEC Defense capability, now condemns more than just BEC threats; it also effectively stops credential phishing, deceptions (many of which are commodity “scams”, like advanced fee fraud or romance scams), malware, and even TOADs.
The results of both engines have been astonishing. Supernova, as part of the Advanced BEC Defense capability that Proofpoint released in 2021, condemns mostly BEC attacks. However, because we’ve been able to feed the engine so much data, it’s been able to learn, adapt and detect much more—including credential phishing, malware attacks and even spam threats.
Supernova Behavioral Engine will similarly be able to better detect and prevent all threat types. In early Q1, Proofpoint released the engine in shadow mode and discovered—in less than four weeks—that it improved detection efficacy against invoicing threats by 6x. Now that the new engine is live for all of our global customers, we can’t wait to see how it learns and improves detection for different advanced threats.
Samples of how Supernova Behavioral Engine improves detection
Here are some samples of where Supernova Behavioral Engine signals can improve detection.
Sample: Lookalike BEC threat: improved likelihood of detection
Proofpoint effectively stops millions of BEC attacks every month. But we’re always aiming to raise the bar on detection. In this sample, our existing Supernova for BEC detection engine would have detected the potential lookalike domain and payment language.
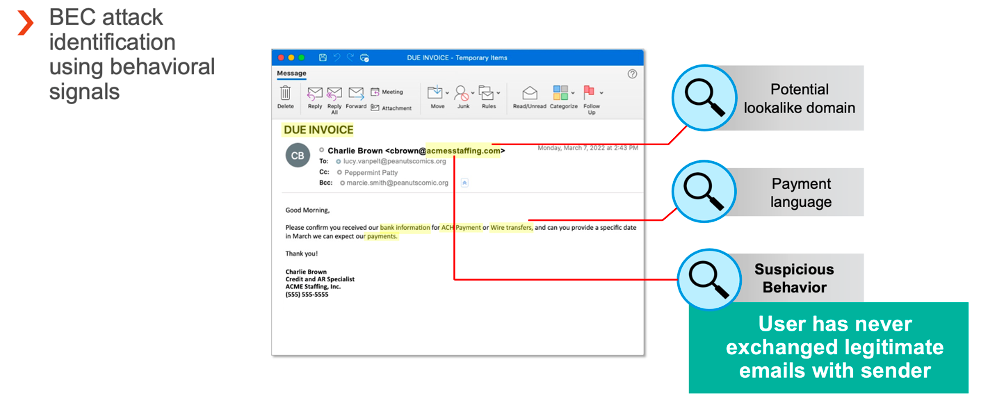
Figure 4. Supernova Behavioral Engine from Proofpoint will add additional detection capabilities for BEC attacks, determining the relationship between two parties dynamically.
Our new Supernova Behavioral Engine will now detect that this is an unknown sender to the recipient, improving the likelihood of Proofpoint detecting and condemning this attack pre-delivery. It does advanced relationship mapping by looking at inputs like cadence, language and context of inbound and outbound messages to determine the relationship status dynamically over time between the two parties.
Even if a dormant, previous sender was compromised and started a fresh attack, Supernova Behavioral Engine would view that communication as anomalous and take a closer look.
Sample: Compromised supplier using a URL-based file-sharing threat

Figure 5. The Supernova Behavioral Engine will better detect compromised suppliers, even if attackers are using a file-sharing site in their attempts to defraud victims.
Let’s say one of your supplier has a compromised Microsoft 365 account. A threat actor takes over the account, does some research on the specifics of your relationship with the supplier and then sets up a lookalike OneDrive SaaS tenant in an attempt to commit fraud.
The email the threat actor sends comes from a legitimate, common sender, SharePoint, and passes DMARC. In terms of reputation, this email seems legitimate. And the language, a contract, is not unusual given past OneDrive correspondence with this supplier. But there are some tells here that Supernova Behavioral Engine will pick up on.
Supernova Behavioral Engine will notice the subdomain of the file-sharing URL is different and anomalous, and it will sandbox the file-sharing URL to inspect the content. That means Proofpoint can better detect and stop attackers compromising supplier accounts and using lookalike domains or even new subdomains of file-sharing tenants.
AI/ML and behavioral analysis: part of a broader detection ensemble
Using AI/ML for content inspection and behavioral analysis can improve detection efficacy. Alone, however, we’ve seen these engines create a lot of noise. That’s why they’re just a few of the engines Proofpoint uses in our 26 layer detection ensemble.
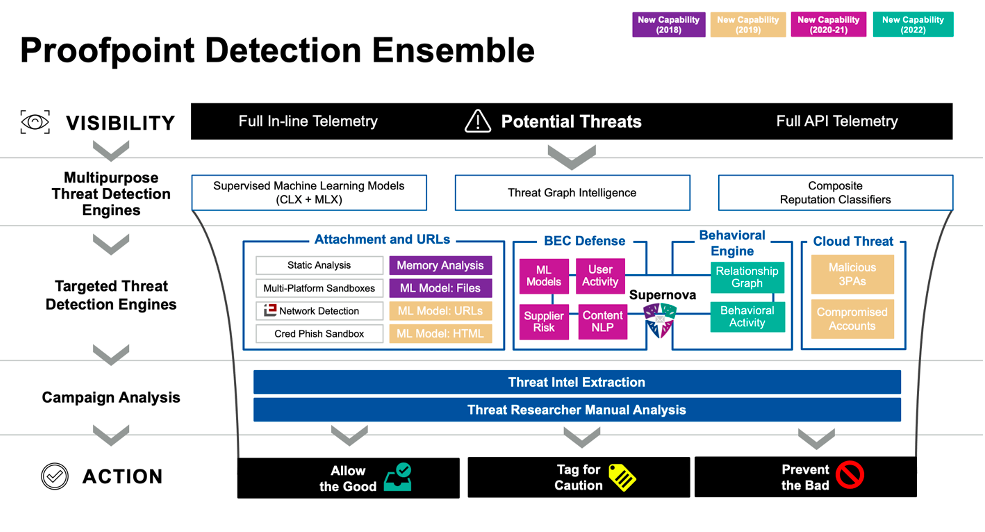
Figure 6. The Proofpoint detection ensemble includes more than 26 layers, improving the likelihood of condemning malicious messages while not creating false positives
Broad reputation classifiers combined with our Nexus Threat Graph intelligence frequently stop more than 80% of all malicious and spam messages from ever reaching end users. For some customers, that can be tens of millions of messages.
We build our attachment and URL sandboxing in-house and use ML models to determine malicious URLs, HTML, files and memory left from potential malware or tampering.
Proofpoint Emerging Threat (ET) Intelligence feeds can quickly identify high-risk IP addresses even if they’ve only recently become malicious. Our cloud threat data can identify malicious third-party applications or compromised accounts and stop those threats from activating. And our threat intelligence team ties it all together, extracting 7,000+ campaigns annually for a deep dive into emerging, advanced threats to see the latest trends.
Put the tech to the test with our Email Rapid Risk Assessment
Ultimately, what matters most is how well these technologies translate to your organization’s risk reduction. If you want to understand your organization’s current risk posture, quickly, the Proofpoint Email Rapid Risk Assessment will allow you to:
- Understand your risk posture and uncover threats your email security solution is missing
- Gain visibility into who in your organization is being targeted by threats
- Discover how Proofpoint can provide the best, integrated protection against evolving threats
To learn more about this free risk assessment and schedule one for your organization, see this page.

