Over the last decade, we’ve witnessed a lot of change in the cybersecurity world. This decade has introduced mobility, migrating to the cloud and the new “work from anywhere” reality. With all the change we’ve seen in the landscape, threat actors have altered their techniques, leveraging new trends and how they target. But through it all, the biggest risk remains the same: people.
In this two-part blog series, we will overview the evolving threat landscape and how you can protect your people.
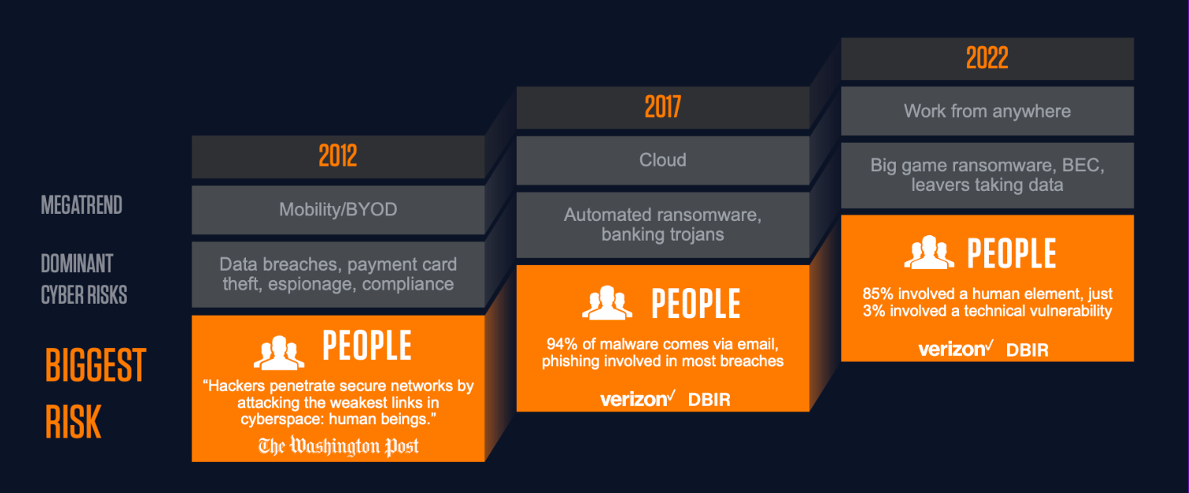
Figure 1. Throughout the evolution of the cybersecurity industry, cyber threats have continuously targeted people. Find out what else is new for 2022 in our threat landscape webinar.
Today’s top cybersecurity risks are people-centric. Below are the three most common attack types:
- Ransomware frequently starts with email that includes an attachment or a link that downloads a malicious file. Cyber criminals want to get inside your organization to collect data and understand the infrastructure before they launch their ransomware attacks.
Learn more about ransomware in our short video.
- Business email compromise (BEC) includes phishing, email fraud and social engineering tactics. Cyber criminals are spoofing identities of trusted individuals and suppliers. They’re sending simple emails without malicious links and focusing on social engineering to trick your people into wiring money or sending sensitive data.
Learn more about BEC and spoofing in our short video.
- Data breaches are typically due to one of the following three types of users:
- A malicious user who shares data on purpose
- A careless user who doesn’t understand the impact of sharing data
- A compromised user who has fallen victim to an attack and been tricked into sharing data
Understand the impact of social engineering on your people
Cyber criminals are using a combination of techniques to gain access to your organization, including impersonating your employees and suppliers. They want to gain access to accounts with credentials—and, if they succeed, they can gain the trust of your workforce.
Ransomware actors also use social engineering to spoof trusted apps and access to steal data.
This is why it’s so important to understand the impact of social engineering on your people.
Malicious actors work to get your people to run their code for them, hand over credentials to them, and in the case of BEC, transfer funds or data to them. They try to trick people into doing all the hard work for them, so they don’t need to “hack in” at all.
Get a comprehensive view of your risk posture across your email infrastructure with a free email rapid risk assessment.
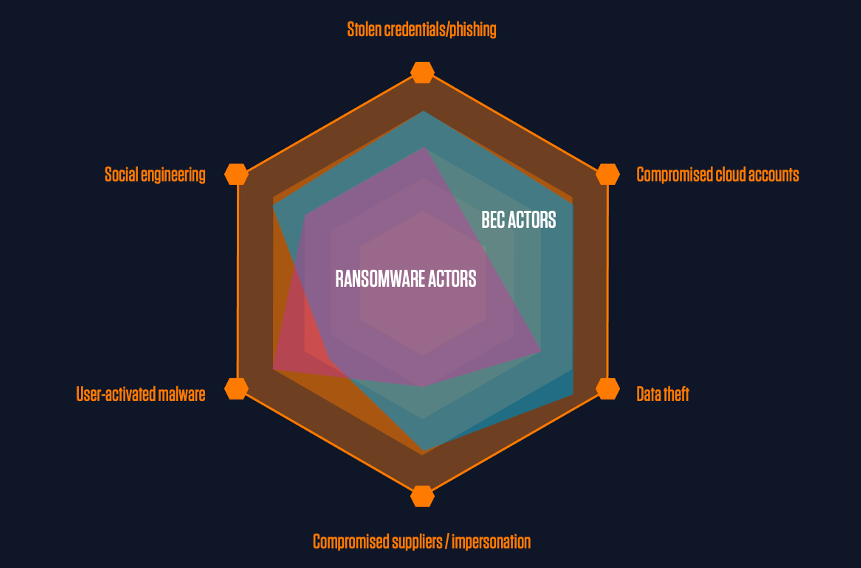
Figure 2. Different attacks don’t share just one threat technique.
Protect your people: email first
Most cyber attacks today start with a phishing email. And most ransomware campaigns begin with a simple email. For example:
- An employee receives a seemingly innocent email spoofing the identity of a trusted individual such as a colleague or supplier.
- They click the link in the email or open an attachment that runs malicious code.
- Cyber criminals then gain access to the organization’s infrastructure, systems, user credentials and important data.
- Eight weeks later, cyber criminals deploy the ransomware activity and cause widespread disruption to the organization.
It’s time for organizations to “shift left” and move up the attack chain with their email security so they can prevent malicious attachments from even entering employees’ inboxes.
Learn more about protecting your number one threat vector: email security.
Watch the Proofpoint webinar, “Protecting People: The New Perimeter,” to learn the importance of a people-centric approach to cybersecurity. And, be sure to subscribe to our blog so you don’t miss part 2 of this series to further understand the importance of a people-centric approach to cybersecurity.
