Phishing Email Reporting and Analysis
 Security Awareness Training
Security Awareness Training
Even with advanced email protection tools, a small percentage of malicious messages still end up in users' inboxes. Our PhishAlarm® phishing button empowers users to report phishing emails and other suspicious messages with one mouse click, and PhishAlarm® Analyser helps response teams identify the most pressing threats with Proofpoint threat intelligence. Both tools are integral to Proofpoint’s automated Closed-Loop Email Analysis and Response (CLEAR) solution which quarantines malicious messages and provides users with customised feedback.
Closed-Loop Email Analysis and Response
An informed employee can be your last line of defence against a cyber-attack. With CLEAR, the cycle of reporting, analysing and remediating potentially malicious emails is taken from days to just minutes. Enriched with our world-class threat intelligence and Security Awareness Training solutions, CLEAR stops active attacks in their tracks with just a click. And your security team can save time and effort by automatically remediating malicious messages.
Request a Demo of CLEAREmail Reporting Made Easy
It’s important to identify—and stop—phishing attacks that slip through perimeter technology. And the key to this is making sure you have knowledgeable users. All Proofpoint Security Awareness packages include our simple but effective email client add-in, PhishAlarm®. This makes it easy for your users to report phishing, which dramatically reduces the duration and impact of an active phishing attack. A valuable addition to security awareness training, it also immediately thanks your users (via a pop-up message) for reporting phishing and suspicious emails. And this reinforces positive behaviour.
PhishAlarm helps your busy incident response teams:
- Cut down on the back-and-forth of having users send headers and attachments of reported messages
- Reduce the noise of reported messages with automatic and available safelisting
- Provide automatic feedback via a pop-up to users if they report a simulated attack, notification email, or safelisted from our solution
- Easily integrate into today’s leading email clients like Microsoft Outlook and Google Gmail
Advanced Analysis Using Leading Threat Intelligence
It’s important to understanding which reported user emails are malicious. And it’s the key to quickly removing active phishing and spear phishing attacks. All Proofpoint Security Awareness packages include our PhishAlarm Analyser email analysis tool. This tool uses rules from Proofpoint threat intelligence that are being updated continuously. These rules leverage insight from one-fifth of the world’s daily email volume. And this includes social and cloud threats.
PhishAlarm Analyser helps your busy incident response teams:
- Proactively identify malicious emails by using Proofpoint threat intelligence and dedicated sandboxing of URLs and attachments
- Specify what was malicious about the reported message in the Threat Report Overview (TRO), which can be sent to admins
- Classify reported messages quickly, so they can act and remediate or quarantine messages
- Save the time and hassle of manually writing and maintaining countless YARA rules or relying on user reputation
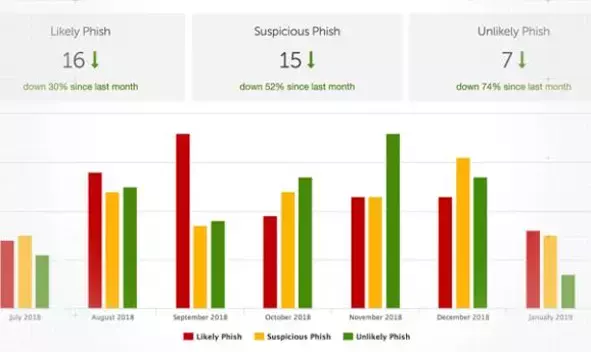
- View how many malicious, suspicious or nonmalicious messages are being reported by users over time
Automated Remediation Using Closed-Loop Email Analysis and Response (CLEAR)
Our CLEAR solution can save your IT and security teams time and effort in managing an abuse mailbox. Threat Response Auto-Pull (TRAP) is the tool within the solution that can be configured to:
- Automate or with one click quarantine or delete malicious reported messages from all users who received them, including forwards
- Automatically close reported cases when messages are classified as safe
- Send users customised feedback emails based on the message classification
- Provide your incident response teams with all the context they need about suspicious messages