We are Proofpoint
We secure how people, data and AI agents connect across email, cloud and collaboration tools.
Stopping
BEC attacks per year
Protecting
customers
Of the F100
use Proofpoint to stop attacks and defend their data
Numbers only ever tell part of the story.
See customer storiesWhy Proofpoint
Two million customers including 83 of the Fortune 100 rely on Proofpoint security solutions
AI is transforming the digital workspace and giving rise to the agentic workspace, where every collaboration—whether by a person or an AI agent—introduces new risks to data.
We give organisations the security solutions they need to protect and empower their people while embracing AI securely and productively.
Threat Protection
Stop all human-centric threats for today’s and tomorrow’s landscape
Protect humans with world leading AI-based detection from threats targeting them across all the different ways they work in the new digital workspace – email, collaboration and messaging tools, social media platforms, cloud apps and file-sharing services.
Data Security & Governance
Safeguard information and digital communications
Data doesn’t lose itself. Behind every incident are the actions of a human being.
Careless users mishandle it. Malicious users walk out with it. Compromised user accounts are hijacked to steal it. Non-compliant users abuse it. A new transformed human-centric approach that leverages behavioural data is needed to safeguard information and digital communications.
Data and SaaS Security Posture
Contain SaaS and identity sprawl
Corporate identities are the root of many ways employees work—from cloud accounts in SaaS apps and authentication tokens that access application databases, to permissions to traverse across the corporate network. This human-centric risk exploited by threat actors must be countered by responding to account takeovers and understanding your risk posture.
Security Awareness
Provide employees with continuous guidance
A new human-centric approach to security awareness is needed in a world of increasing threats targeting humans across the different ways they work. Help make your users resilient against human-targeted attacks and guide them to make the correct decisions in the face of risky scenarios.
Why Proofpoint
Two million customers including 83 of the Fortune 100 rely on Proofpoint security solutions
AI is transforming the digital workspace and giving rise to the agentic workspace, where every collaboration—whether by a person or an AI agent—introduces new risks to data.
We give organisations the security solutions they need to protect and empower their people while embracing AI securely and productively.
Threat Protection
Stop all human-centric threats for today’s and tomorrow’s landscape
Protect humans with world leading AI-based detection from threats targeting them across all the different ways they work in the new digital workspace – email, collaboration and messaging tools, social media platforms, cloud apps and file-sharing services.
Data Security & Governance
Safeguard information and digital communications
Data doesn’t lose itself. Behind every incident are the actions of a human being.
Careless users mishandle it. Malicious users walk out with it. Compromised user accounts are hijacked to steal it. Non-compliant users abuse it. A new transformed human-centric approach that leverages behavioural data is needed to safeguard information and digital communications.
Data and SaaS Security Posture
Contain SaaS and identity sprawl
Corporate identities are the root of many ways employees work—from cloud accounts in SaaS apps and authentication tokens that access application databases, to permissions to traverse across the corporate network. This human-centric risk exploited by threat actors must be countered by responding to account takeovers and understanding your risk posture.
Security Awareness
Provide employees with continuous guidance
A new human-centric approach to security awareness is needed in a world of increasing threats targeting humans across the different ways they work. Help make your users resilient against human-targeted attacks and guide them to make the correct decisions in the face of risky scenarios.
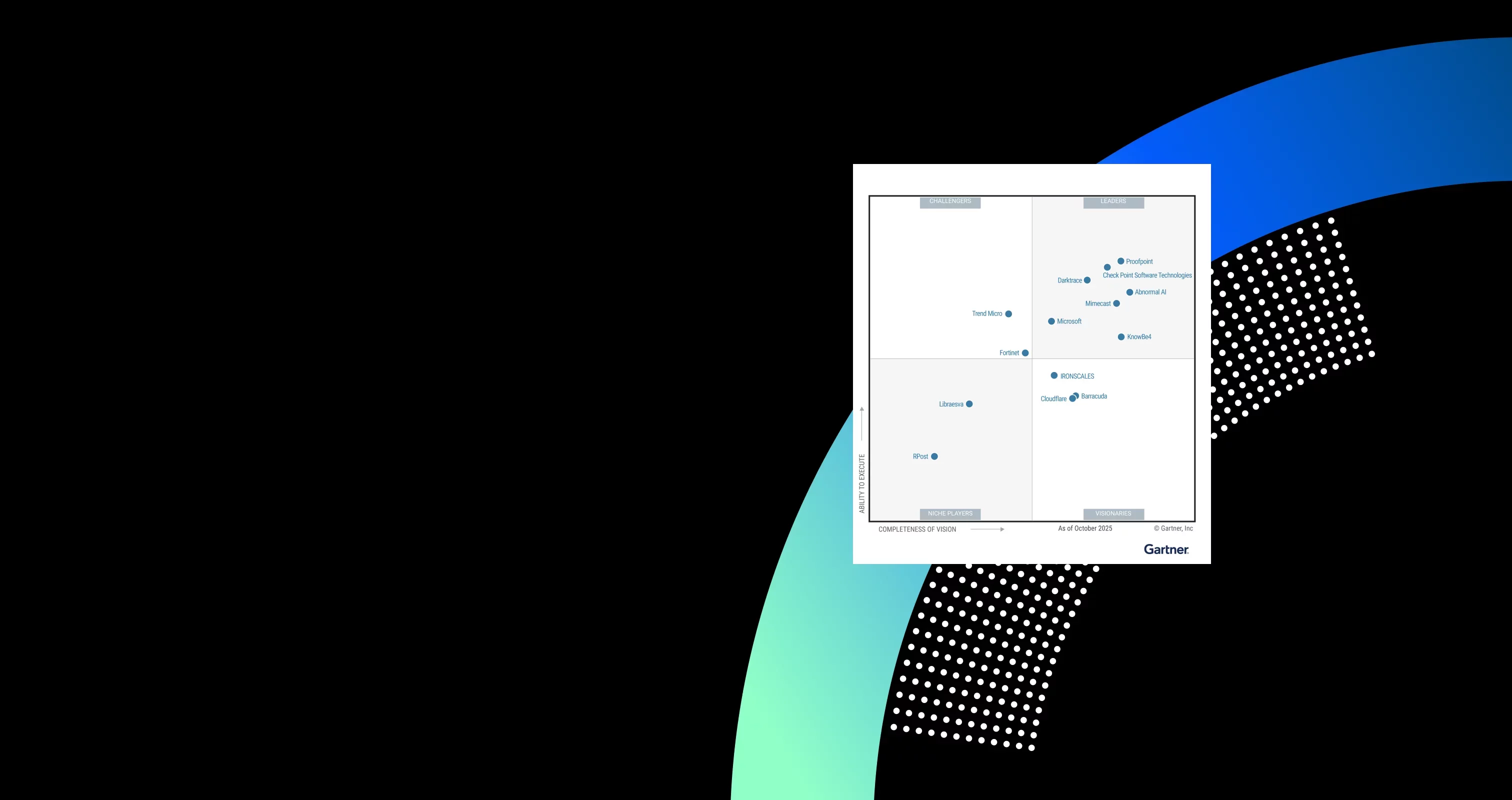
THE PROOF
We’re recognised as an industry leader by our peers and customers alike
-
Threat Protection
-
Data Security
-
Digital Communications Governance




Proofpoint helps Accenture secure people, data and operations.

Wyndham blocks 99.99% of threats, significantly reducing BEC risks while employees reporting increased phishing awareness with Proofpoint ZenGuideTM.