Table of Contents
Email Scam Definition
Email is one of the most beneficial ways to communicate with anyone. But it is also a primary tool used by attackers to steal money, account credentials, and sensitive information.
Types of email scams come in many forms including:
- Phishing
- Credential theft
- Malware
- Monetary theft
- Wire fraud
- Supply-chain attacks
If users interact with the email scammer and provide sensitive information, it can cause long-term issues for your organisation, including identity theft, financial loss and data corruption.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we'll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
Recognising Email Scams
Email scammers use several strategies to bypass email defences and trick users into divulging information or running malicious code. Some types of scam emails include a link to an attacker-controlled malicious website where the attacker collects sensitive data from victims. When one method stops working, attackers often revise their approach to improve the number of targeted users affected by their email scams.
Red flags of an email scammer:
- Claims that you must log into a website or your account will be closed. This tactic includes a link to an attacker-controlled website.
- Claims that your payment information is invalid, and you must log into your account and change this information to keep the account active.
- Tells you that personal information is inaccurate, and it must be sent to the attacker either using a reply message or on a website.
- Attaches an invoice for payment.
- Conveys a sense of urgency or confidentiality.
- Claims that you could receive a government refund and asks for sensitive data such as social security number.
- Requires you to submit private data to obtain free products, coupons or money.
But a growing number of email scams don’t exhibit any of the typical behaviours. They don’t include attachments or URLs. And they hide in plain sight by disguising themselves as normal everyday business.
These attacks are sometimes called business email compromise (BEC) or email account compromise (EAC). They usually start when the attacker impersonates someone the recipient trusts—perhaps a boss, colleague or business partner—and asks for something that seems like a normal business request. It might be making a wire transfer or changing payment details, things that take place all the time in the regular course of business. By the time the organisation senses something is off, the email scammer already has the money.
What to Do After Responding to a Phishing Email
Email Scam Examples
Attackers have dozens of common strategies. If you have a free email solution such as Gmail and use your email address on contact forms across the internet, you probably have scam emails in your spam inbox.
Attackers might cast a wide net by sending email scams by the thousands. In this model, the more emails sent, the better chance of tricking numerous targeted users.
Other attackers might take a more targeted approach, carefully choosing a recipient with the right access to data, systems or resources. The attacker researches the victim online and tailors the emails to be as personal and convincing as possible. In some cases, the attacker has already compromised a legitimate email account and has access to previous email conversations, calendars and contacts—ammunition for highly convincing impersonations.
Here’s an example of an email scam:
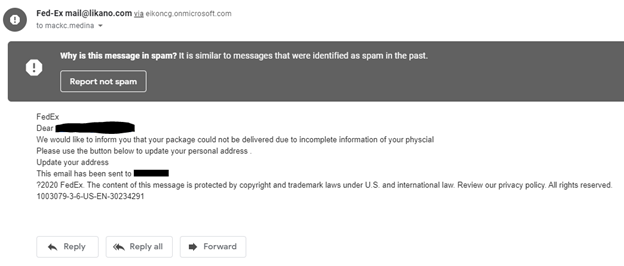
The above image is a message (sent to Gmail’s spam inbox) that an attacker sent, using FedEx to trick a targeted user into sending private data. Attackers use this type of message because someone is always waiting on a FedEx package. If the message is sent to thousands of recipients, it can trick many of them.
Email spoofing is common in scams, but the sender’s email address in the above image is from a public domain unassociated with FedEx. The email gives no contact number but has a single link that points to a malicious web page.
Another giveaway in this email scam example is that the email does not address the recipient by name or have any personal information that an account vendor would have. The email is generic with only the recipient’s email address used in the greeting (the email address is blacked out).
Here are a few common factors in most email scams:
- Use of a trusted common business (such as FedEx, Netflix, PayPal, your bank, and so on).
- Conveys urgency such as losing an account or product if the targeted user does not respond.
- Includes a generic greeting that does not use a name.
- Includes a convenient button for the targeted user to click and access the malicious site.
- Uses an email address not associated with the official business but deceptively similar to it. For instance, the sender could use the fedexx.com domain trick users, most of whom don’t bother looking at the return address.
Protecting Against and Avoiding Email Scams
You can’t prevent scammers from using email. But you can take steps towards avoiding email scams to prevent being a victim. For enterprise users, fraud prevention using email filters and authentication (such as DMARC) can block spoofed messages and those from malicious domains. For individuals, always use an email provider that has fraud prevention built into the system.
Email scams target people, not systems. That’s why you need a people-centric approach to stopping them. Here are ways you can protect people from email scams:
- Deploy an email defence that customises controls based on each users’ unique vulnerability, attack profile and access privileges. It should detect malicious attachments, unsafe URLs and social engineering techniques.
- Use email domain authentication technology such as DMARC to prevent email fraud schemes from using your trusted domain, including attacks aimed at your users.
- Prevent email and cloud account compromise with technology that reveals suspicious activity and other signs of takeover. Scan internal email, which could come from compromised accounts. Use multifactor authentication (MFA) where possible but keep in mind that it’s not a failsafe solution to account compromise.
- Isolate risky websites and URLs. Web isolation technology can assess suspicious web pages and unverified URLs in a protected container within a users’ normal web browser.
- Train users on the latest phishing tactics and to be on alert for return email addresses that don’t match the sender (including those with domains that are slightly off-brand).
- Always keep your security (antivirus and antimalware) software updated for threats that reach the endpoint.
- Update your operating system when patches and new releases are available. Many of these patches remediate vulnerabilities made public by researchers and cybersecurity experts.
- Back up data frequently in case you accidentally fall victim. Your backups can be used as data recovery. Consider using cloud backup storage for the best protection. But remember that many of the costliest email scams don’t use malware at all.