Table of Contents
Keylogger Definition
Keyloggers are programmes that run as a background process on a computer or other device and collect keystrokes as a user types on their keyboard. They can be malicious or used with good intentions, depending on the goals of the person installing them. Keyloggers are notoriously known for malicious intent to collect a targeted user’s credentials and other important information, but they can also be used for parental control and child safety.
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
How Do Keyloggers Work?
A keylogger’s main goal is to silently capture a targeted user’s keystrokes as they type on their device. Installation of a keylogger could be intentional for business purposes, or a user could install it after being tricked by a malicious attacker. Attackers have several modes of infection, including phishing, drive-by installations, vulnerable browsers, or adding malicious content to a seemingly innocent programme installation package.
A truly stealth keylogger runs as a background process without any clues that could give it away. For example, a Windows installation could be performed without any input from the computer owner and immediately log keystrokes without noticeable performance degradation on the device. Targeted users who investigate running processes must identify the malicious background process, but many users cannot differentiate between necessary Windows executables and malicious content.
Good keyloggers organise keystrokes so that an attacker can identify credentials linked with specific accounts. For instance, a targeted user types their bank website into a browser window and then types their credentials into the banking website. The keylogger captures all these keystrokes into a file stored on the local device or directly in the cloud. To avoid losing information due to a loss of Internet connection, a keylogger will usually log keystrokes in a hidden folder and transfer the content to an attacker-controlled server when an Internet connection is available.
Organising log files by application allows an attacker to quickly identify and link stolen credentials with account locations such as websites, local applications, or local network services. Some Trojan malware includes keyloggers but also gives remote control to an attacker, so that transfer of log files is unnecessary. The attacker can instead remotely access the system and obtain the log files from the local device.
Keylogger programmes are often used for parental monitoring on a minor’s device. For instance, if a minor uses chat programmes to talk to friends online, parents may want to monitor conversations. The keylogger works in the same way as a malicious keylogger, but its use is for protecting a child rather than for nefarious purposes.
Some other standard functionality in a keylogger includes:
- Regularly emails an attacker with the latest keystrokes. This method of sending keystrokes to an attacker is more easily detected when the targeted user’s email account is used, leaving a trail in the “Sent” box pointing to the attacker’s email address.
- Wireless transmission of stolen data using Wi-Fi technology or the device’s data plan, if it’s available.
- In some cases, keyloggers include malicious applications that allow remote control of the local devices.
- Copying clipboard content to detect stored passwords when users copy and paste a password into a window. For instance, stealing clipboard content could give an attacker access to the keys associated with a user’s cryptocurrency wallet.
- Screenshots of desktop windows. With this feature, an attacker can capture information when the user has autofill configured on their browsers. For instance, a user might have a cookie stored that remembers the account name for a financial website. The user types the password into the website, but only the password and not the username is captured. With screenshots, the attacker has the auto-filled username in the image, and the password is then key-logged.
- Activity tracking to capture user mouse clicks and device actions. By tracking mouse clicks, the attacker can determine the files and folders commonly opened. This could give a remote attacker the ability to determine important files that contain sensitive information.
Targeted Attack Protection
Stay ahead of attackers with an innovative approach that detects, analyses and blocks advanced threats before they reach your inbox
How to Detect a Keylogger
Malicious software authors code stealth features into their programmes to avoid detection, but users have several resources available to help them detect an installed keylogger. Good anti-malware applications detect keyloggers and block them from being installed. Still, malware writers continually change the payload and strategies coded into their software to avoid detection from device defences. It’s still difficult for anti-malware software to detect zero-day threats, which means the malware has not been seen in the wild.
If you suspect that you have a keylogger running on your computer, the first step is to review a list of processes running on the machine. On Windows computers, these processes are shown in Task Manager.
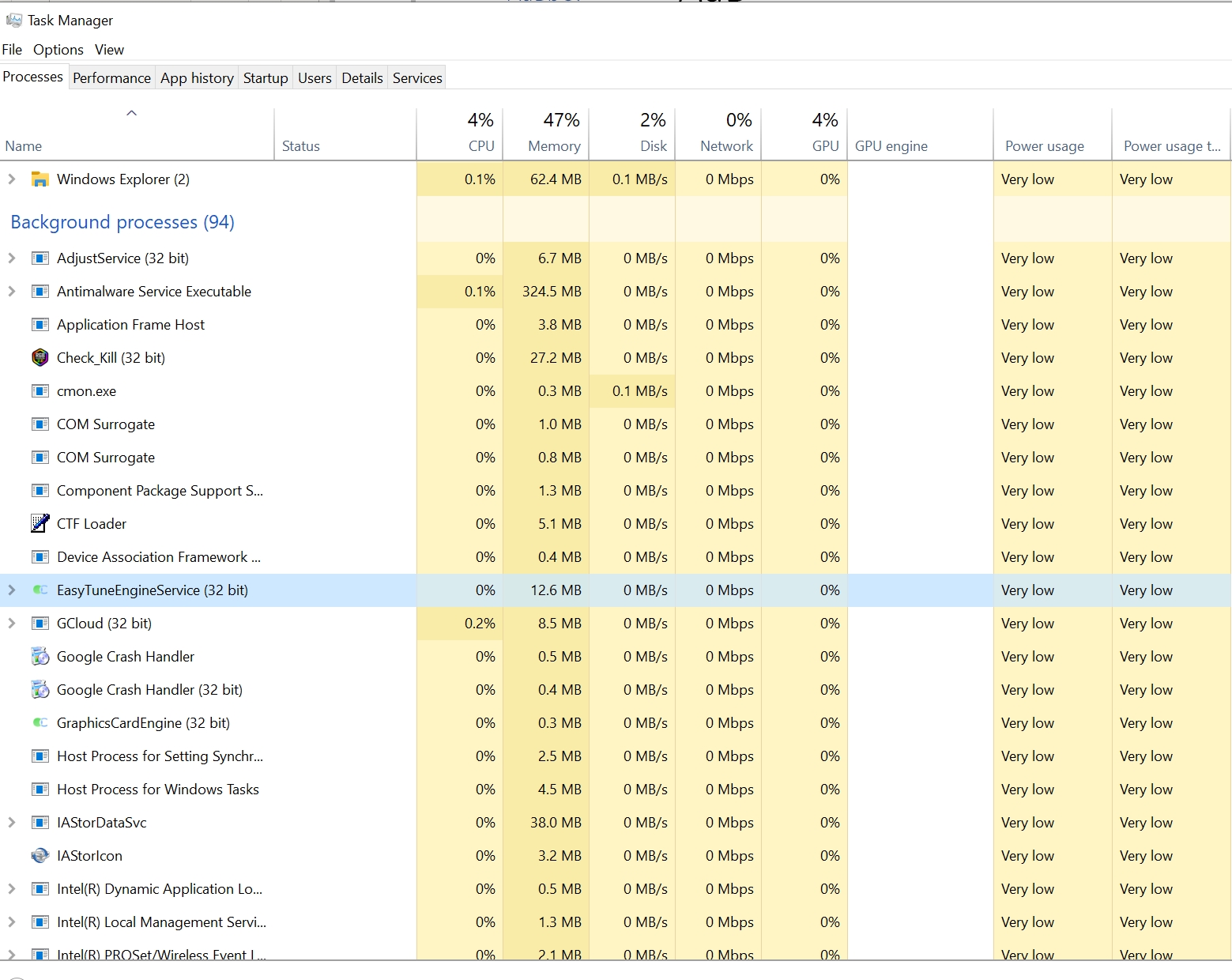
In the screenshot above, 94 background processes are running. A keylogger would appear on this list, but as you can see, it would be difficult to identify a legitimate programme from malware.
For a keylogger to run after a reboot, the service must be configured in Windows to load automatically. Click the “Startup” tab in Task Manager to view a list of executables that run after a reboot.
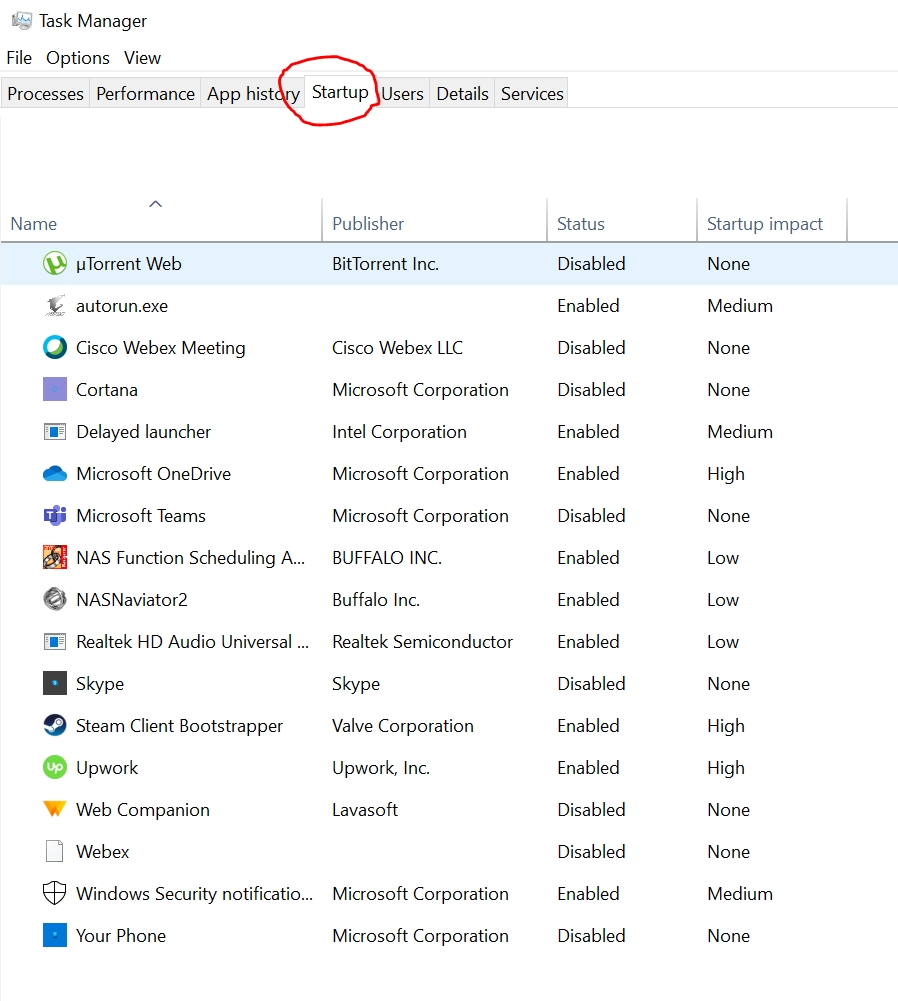
Browse through the list of startup executables to identify if Task Manager shows suspicious programmes. You can disable a startup programme from this tab, but it doesn’t entirely remove the malware from your computer. The executable still exists, and malware developers code for when the application is disabled and restart it.
The best way to detect keyloggers is to run anti-malware applications designed to quarantine and remove malicious software. It’s best if the anti-malware programme detects the malicious code before it loads into memory, but false negatives are a possibility if malware can avoid detection. Avoid false negatives by consistently updating your anti-malware software. Updated anti-malware software will detect the latest attacks, including keyloggers. Don’t install software that is not distributed by the official vendor, and never run executable files attached in email messages. If your operating system includes a firewall, outgoing connections might be blocked, but never rely on application firewalls to completely block keyloggers or any malware.
How to Remove a Keylogger
The steps to remove a keylogger depend on the installed malware. Complex, well-written keyloggers can persist on the system even after you think it’s been removed. The best way to remove a keylogger is to run a scan on your system and let the anti-malware application remove it. Most anti-malware software allows you to quarantine suspicious applications instead of automatically deleting them. In a quarantined scenario, the executable files are moved to a directory on the device where users can review them before permanently deleting the files.
If you think that you have a keylogger installed on your device, the first step is to disconnect from the Internet so that any attacker with remote control on the machine will no longer be able to connect. It also stops the malware from communicating with an attacker-controlled server and uploading stolen data to a third-party cloud location.
An infected machine should not be on your private network, but you must transfer an anti-malware application to the infected device. If you don’t already have anti-malware installed, you must download it from the Internet or transfer the installation files from a network computer to the infected one. You can also transfer files from a mobile device such as a smartphone or a portable drive. You should be careful when transferring files from another device as malware will occasionally transfer files to the connected device.
After installing anti-malware software, run a scan on the computer. The anti-malware programme can be configured to automatically delete files or quarantine them. It should also remove the binaries from memory so that the keylogger can no longer record keystrokes.