Overview
The Proofpoint Nexus™ compliance and security platform blends the industry’s best security research, technology and threat data to protect you at every stage of the attack lifecycle. This modern, cloud-based graph database architecture drives the effectiveness of our products. And it powers our ecosystem of partners and integrations. Our Nexus platform extracts and correlates intelligence across email, social media and mobile—learning from each new attack to stay ahead of evolving threats.
NEXUS PLATFORM
Today’s cybersecurity challenge involves three key objectives: let in as few attacks as possible, exposing as little as possible, as briefly as possible.
The Nexus platform helps you achieve all three with intelligence that helps our tools block network threats, identify and safeguard sensitive information, and respond quickly when threats get through.
With real-time data that spans email, social media, and mobile devices, Nexus correlates threat intel from more than:
- 1 billion daily emails
- 20 billion mobile apps
- 200 million social media accounts
- 250,000 daily malware samples
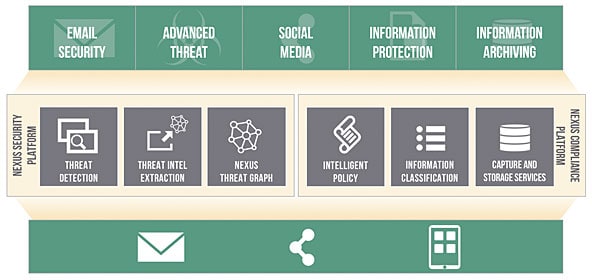
This vast threat graph enables Nexus to recognise and make sense of cyber attackers’ tools and infrastructure. It’s powered by multiple detection techniques, including:
- Next-generation analysis that correlates all aspects of attacker tradecraft and reputation— not just IP addresses and domains
- Advanced cloud-based sandboxing of attachments, URLs, and mobile apps
Nexus’ intel-extraction environments are built from the ground up to wrest the deepest level of forensic detail from detected malware. The Nexus technology platform feeds that threat intelligence back into its graph database. It correlates this detail to better detect future attacks. It connects the dots to verify, investigate, and prioritise threats. And it provides insight that helps resolve threats quickly and effectively.

