Proofpoint and CrowdStrike have partnered for almost three years, building multiple integrations to enhance protections for our mutual customers. Our solutions protect more than 7 million end-users across 650+ joint customers. Proofpoint has also added 250K+ IOCs previously unknown to CrowdStrike to protect our mutual customers’ endpoints better.
Our existing set of integrations focuses on email protection and posture checking. You can read more about each of them here:
- Pre-delivery Protection for Internal Email
- Pre-delivery Protection for External Email
- Post-delivery Automated Remediation
Organizations adopting more cloud infrastructures to support their remote and hybrid work environments must not forget to focus on protecting people and defending data. In this changing environment, enterprises must take a people-centric approach to cloud security and protecting their data – so users can securely access the web, cloud services, and private apps. This requires not just one, but a combination of solutions. This combination should include access controls, threat protection, data security, app governance and Zero Trust policy controls.
The Proofpoint Advantage: Securing cloud information, not just access
To secure user and data activity across endpoints, controls must be enforced by sensors across all channels, and must be backed by common analytics, investigation, and policy-management platforms. Our cloud-native Information and Cloud Security platform combines many of our products to address secure access, as well as data loss prevention (DLP) and insider-risk use cases.
With Proofpoint’s Information and Cloud Security platform, customers can:
- Gain people-centric visibility into cloud risks: Identify top users at risk and monitor for alerts with our powerful analytics dashboard. Use Nexus People Risk Explorer for security control recommendations to mitigate the risk of cloud account compromise and malicious files.
- Gain forensic insights and automate threat and data protection: Automate your security response with flexible policy controls, customizable alerts, and threat correlation.
- Enable safe web and cloud applications access: Apply advanced threat protection and dynamic access controls, including browser isolation, without hampering user productivity.
- Protect data against threats and negligence: Discover sensitive data in the cloud and reduce data exposure. Prevent data loss and ensure compliance with inline data controls when users browse the web or collaborate using cloud applications.
What’s New: Multi-layered people-centric approach to Zero Trust
While our current Zero Trust implementation with CrowdStrike checks for the CrowdStrike Falcon® agent running on a user’s endpoint, this year we have added an additional layer of trust with the ability to ingest the CrowdStrike Falcon Identity Threat Detection™ user risk score.
Attackers can gain access to your sensitive data by taking over cloud accounts. Proofpoint’s Cloud Security products (Web Security, CASB, and Secure Access) can leverage CrowdStrike intelligence to manage access to our customers’ cloud and web apps before malicious actors gain access and cause damage. Our combined threat intelligence and risk scores allow us to reduce risk from data loss and lateral movement within cloud and web apps.
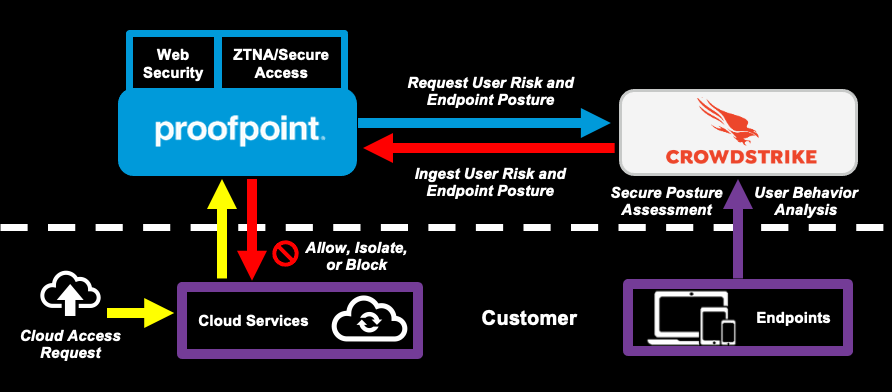
Figure 1. Zero Trust risk- based access control
Here is how this integration works:
- Proofpoint checks for Endpoint Posture
- Proofpoint queries CrowdStrike for ITD (User Risk) Score
- CrowdStrike provides ITD Score
- Proofpoint applies access rules (allow, isolate, or block) by incorporating NPRE, Endpoint Posture, and ITD Scores
This integration addresses use cases such as blocking or isolating:
- Users who are attempting to access cloud or web applications from compromised devices
- Users who have downloaded documents or executables when their device does not have its endpoint protection enabled
- Users who previously accessed sensitive data on a compromised device
Multi-layered Protection with CrowdStrike
Inside or outside the cloud, your people remain the top target for attackers, making it imperative to implement a multi-layered defense to stop targeted attacks. Our partnership enables the automation of threat intelligence sharing across both email and cloud attack vectors, allows for better detection and prevention against attacks, and enhances your ability to automate triggered actions in both platforms to reduce overall risk against attack.
“The integrations between Proofpoint and CrowdStrike have elevated our overall security posture as we have two industry-leading security vendors working together to help mitigate risk and potential exposure of our organization.”
- Leo Sanchez, Incident Response, Tetra Pak
While no single vendor can provide best-in-class solutions for all your security challenges, it is incumbent on leaders like Proofpoint and CrowdStrike to collaborate to transform your security programs. By working together to share threat intelligence, we are advancing threat and information protection/remediation across email, cloud and endpoint.
Please reach out with recommendations on challenges that we should further collaborate on. Meanwhile, to learn more about this and other CrowdStrike integrations, please visit our partner webpage.
You can also join us at CrowdStrike’s Fal.con 2022: Cybersecurity Conference from Sep 19-21 in booth #804 in the Expo Hall or at our Partner Theater Session on Sep 21 at 12:00p PT on the Partner Theater Stage.

