Welcome to our new series, Cybersecurity Stop of the Month. Each month, we’ll explore threat actors’ ever-shifting tactics and reveal how they play out in the critical first steps of the cyber attack chain. We’ll dive deep into how the attack unfolded, why it slipped through other security tools and, ultimately, how Proofpoint stopped it.
Our goal is to provide insights that help you protect your people and defend your data from today’s evolving threats.
This series focuses on the initial access phase of the attack chain: reconnaissance and initial compromise.
In our first post, we will unravel the intricate nature of a business email compromise (BEC) and supply chain attack. BEC is one of the most financially damaging email attack vectors. In these attacks, threat actors often pretend to be trusted external entities. Oftentimes, they use the compromised accounts of trusted suppliers or partners for infiltration.
The scenario
We’re starting with a BEC incident that Proofpoint detected at a global retailer with more than 40,000 users. The attack came from the retailer’s supply chain, and its existing security solution failed to detect it. This example is helpful because it highlights how quickly the cybersecurity landscape evolves and how important it is to break the attack chain.
The threat: How did the attack happen?
The global retailer received an email from a “legitimate” sender within its customer supply chain who requested an update to their payment information. But what seemed like a routine request was malicious, as the sender’s account had been compromised. The attacker was trying to redirect response emails to a newly registered lookalike domain, with an aim to intercept sensitive information and divert funds.

An attacker’s initial email, shown with forensic observations by Proofpoint.
Detection: How did Proofpoint detect the attack?
Here are a few reasons why the customer’s existing security solution missed this threat:
- An overreliance on domain age as a detection factor
- An inability to identify lookalike domains
- An absence of reply-to pivot analysis
Relying solely on domain age can generate excessive noise and overwhelm security teams with a high number of false positives. (Note: When domain age is combined with other identifiers of malicious intent, it can be a valuable signal for identifying potential malicious attacks.)
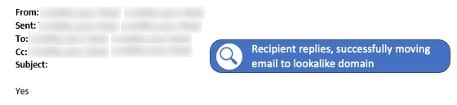
The customer’s response, which was sent to a lookalike domain.
Proofpoint has a multi-layered approach to detecting this type of threat. Our behavioral engine, Supernova, uses artificial intelligence, machine learning and behavioral analysis to help us identify key indicators of compromise. It detects email patterns that fall outside of “normal” behavior and improves the detection of all threat types—from BEC to credential phishing.
In this example, Proofpoint Supernova identified language that indicated there was a financial request. While the request did not appear unusual on its own, when combined with the change in the reply-to address it was suspicious. The domain was also registered on the same day that the email was sent.
Our new Supplier Threat Protection solution helped detect this threat because it combines behavioral data with our threat intelligence. That allowed us to pinpoint which compromised supplier accounts to investigate.
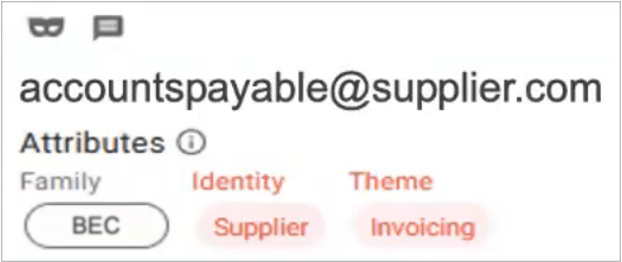
The Proofpoint Targeted Attack Protection (TAP) dashboard categorizes every threat. For this example, it shows that we identified the threat as BEC, that the threat came from a supplier and that invoicing was involved.
Remediation: What were the benefits or outcomes?
After our threat assessment, Proofpoint helped our customer take swift action:
- Our response team alerted the customer to the presence of the BEC and supply chain attack.
- With our guidance, the customer neutralized the threat to prevent any data breaches or financial losses.
- We provided a comprehensive remediation plan that included use of the Proofpoint Supplier Threat Protection solution to gain in-depth insights into compromised supplier accounts and isolate links from those accounts.
- We helped the customer to enhance security protocols around the compromised accounts and implement strict email authentication measures.
The global retailer, by following these steps, was able to maintain the trust of its customers and partners while reinforcing its resilience against future attacks.
Proofpoint also learned from this experience. We updated our comprehensive threat intelligence with valuable data from this incident. In doing so, we effectively increased threat visibility, which better safeguards all our customers against future attacks.
Proofpoint helps break the attack chain
The attackers in the example above took advantage of vulnerabilities within our customer’s existing email security solution. If Proofpoint had been the incumbent solution, we would have mitigated the risk entirely, as we would have prevented the message from reaching employees’ inboxes.
Next month, we invite you to come back and learn about how we helped foil another cyber attack in our Cybersecurity Stop of the Month series. By shedding light on the attack chain, we seek to do our part to help break it—and empower businesses to build better defenses.
Download our e-book, The Definitive Email Cybersecurity Strategy Guide, to learn more about how Proofpoint can protect your business against BEC and supply chain attacks.
