Overview
While cryptocurrencies like Bitcoin and Monero were once used largely in underground criminal markets because of the anonymity associated with financial transactions, the user base for these currencies and the underlying blockchain technology is growing rapidly. Retailers, online gaming platforms, and more now accept Bitcoin, while major technology players with interests in transactional systems and databases are investing heavily in blockchain. At the same time, the appeal for cybercriminals remains strong, with most ransomware actors requiring payment in Bitcoin and underground markets continuing to operate with a variety of cryptocurrencies.
The mainstreaming of Bitcoin in particular, along with built-in mechanisms for ensuring a reasonable degree of scarcity, has dramatically driven up the value of the currency (Figure 1). At current exchange rates, one bitcoin is now worth over $2600 USD, although the exchange rate recently exceeded $3000 USD per bitcoin. Not surprisingly, threat actors are now looking at new ways of stealing bitcoins, including through sophisticated phishing schemes. We examine several phishing templates targeting cryptocurrencies below.
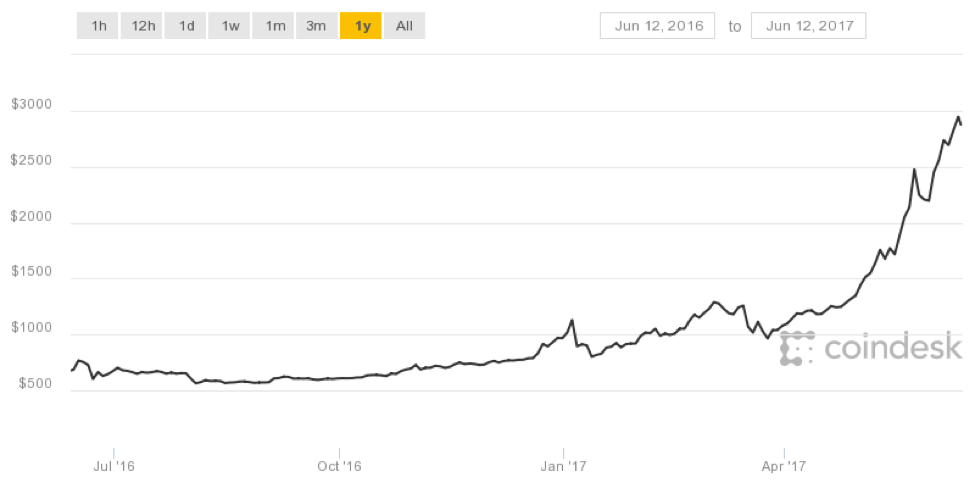
Figure 1: Increase in Bitcoin value over the last year (chart courtesy of Coindesk.com)
Analysis
Blockchain.com is the largest provider of Bitcoin wallets in the world as well as a leading provider of distributed ledger technology - the software platform underlying Bitcoin and many other transactional systems. This popularity has made Blockchain.com a frequent target for cryptocurrency phishing. We have observed regular updates to phishing templates keeping them in step with design changes to the legitimate blockchain.com website. As recently as May 2017, we continued to see the following email and phishing templates in use.

Figure 2: Blockchain email lure with stolen branding from May 2017
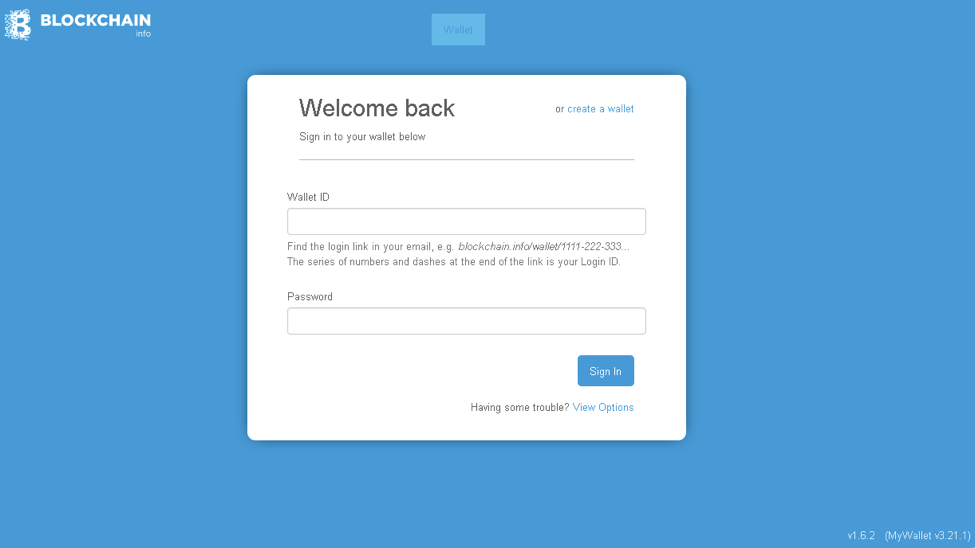
Figure 3: Blockchain phishing landing with stolen branding from May 2017
Recently, we also observed a new phishing template and email lures in use that are consistent with the latest blockchain.com website redesign.
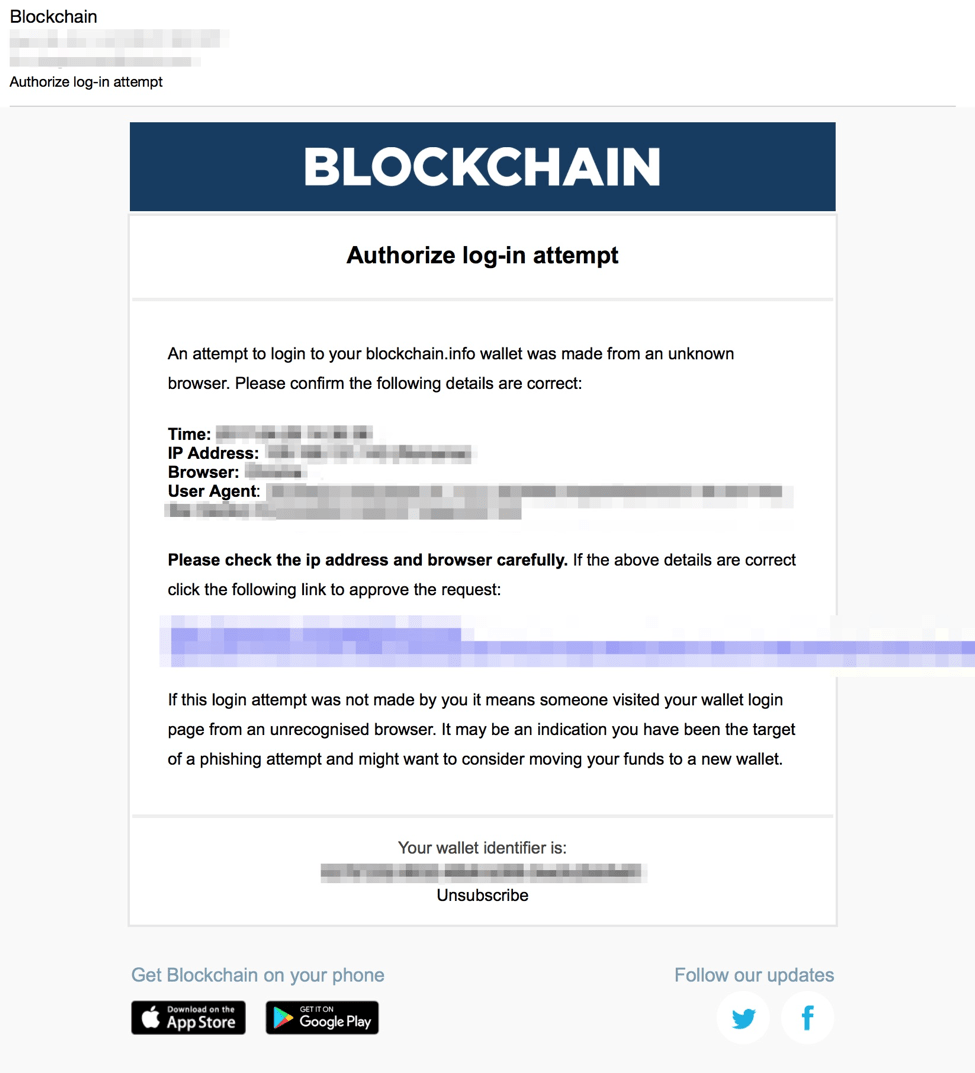
Figure 4: Updated Blockchain email lure; note that the app store icons link to the legitimate Blockchain app and are simply part of the stolen branding used throughout the campaigns
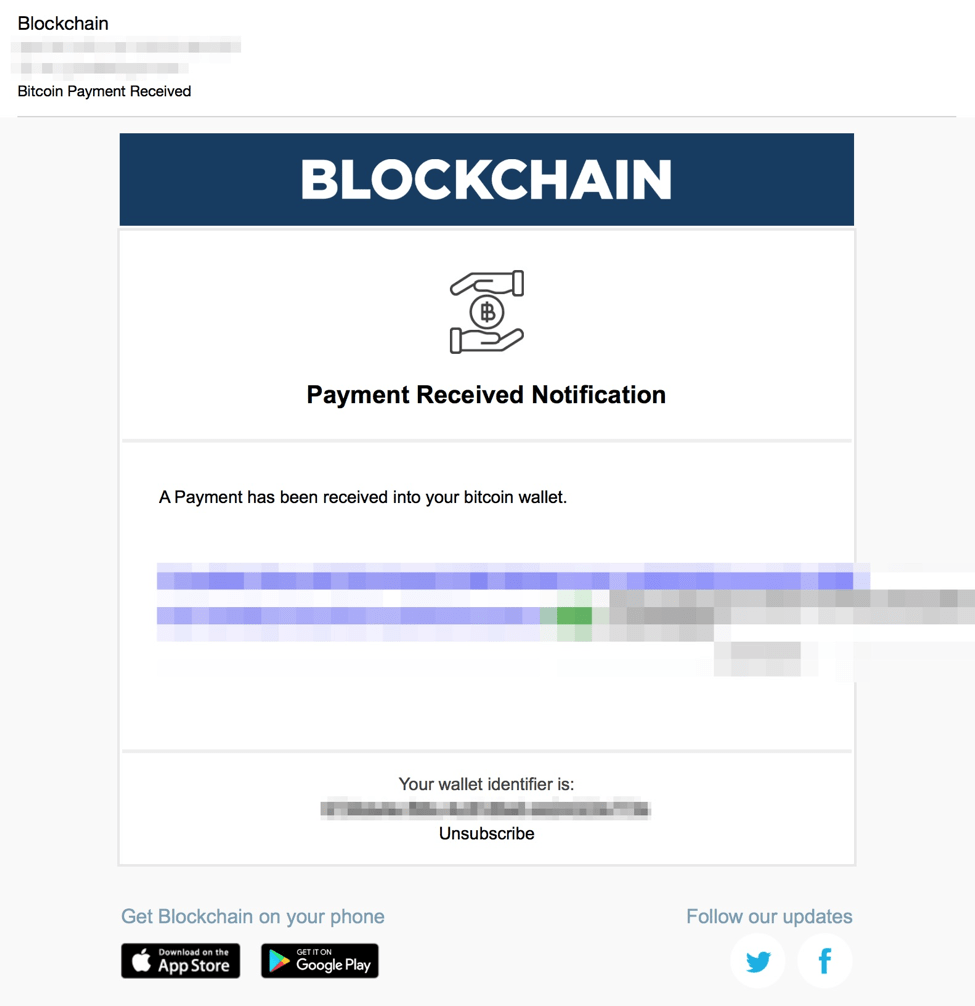
Figure 5: Another updated Blockchain email lure
The landing page for this phishing template has been upgraded as well and is difficult to distinguish from the legitimate site. The stolen branding and careful replication of the real site are clearly visible in Figure 6.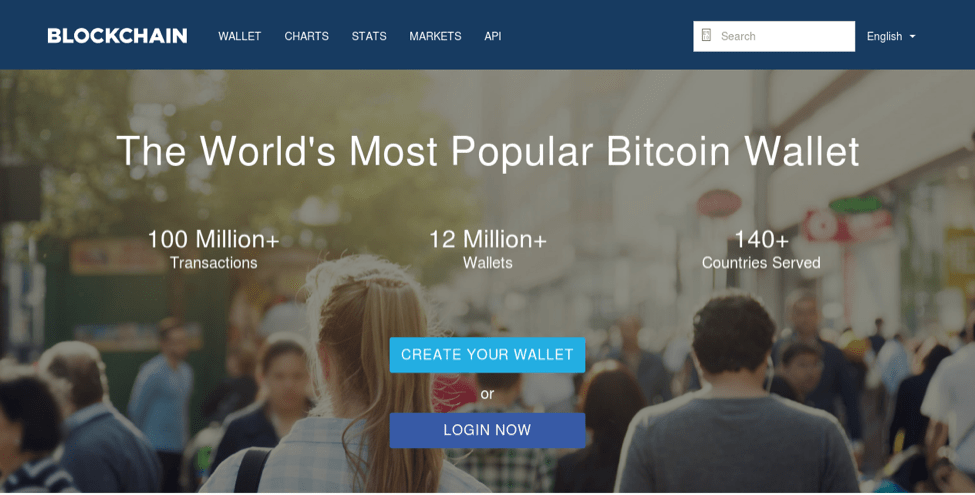
Figure 6: Updated Blockchain phishing landing page, with stolen branding
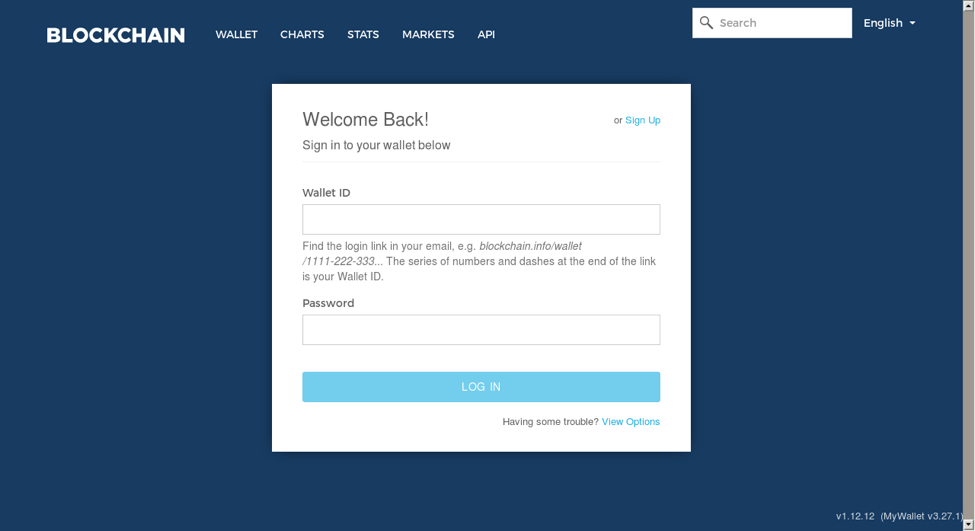
Figure 7: Updated Blockchain phishing login, with stolen branding
The actors behind these instances of Blockchain phishing frequently use typosquatted domains that resemble the target domain for their scams. As these scams register their hosting and domains through legitimate services, they often have a lifespan much longer than those used in most phishing scams today. Examples of these domains appear in Table 1.
|
Date Observed |
Domain |
IP |
Registrant |
|
June 11, 2017 |
blockhian[.]info |
153.92.6[.]10 |
WhoIs Protected |
|
June 10, 2017 |
blockchan.ru |
81.177.141[.]227 |
WhoIs Protected |
|
June 9, 2017 |
blockchonin[.]info |
217.23.13[.]20 |
WhoIs Protected |
|
June 8, 2017 |
blockcha[.]info |
104.27.168[.]84 |
thommy@airmail[.]cc |
|
June 8, 2017 |
blokcchainn[.]info |
153.92.6[.]16 |
WhoIs Protected |
|
June 7, 2017 |
btockchain[.]info |
95.85.22[.]97 |
WhoIs Protected |
|
June 7, 2017 |
blockhchain[.]ru |
81.177.135[.]153 |
WhoIs Protected |
|
June 7, 2017 |
Blockchaen[.]ru |
87.236.16[.]186 |
WhoIs Protected |
|
June 6, 2017 |
blockchaln[.]ru |
81.177.135[.]153 |
WhoIs Protected |
|
June 5, 2017 |
Blockcchain[.]com |
198.54.116[.]78 |
WhoIs Protected |
|
June 5, 2017 |
Blockkcchaiin[.]info |
31.220.16[.]214 |
WhoIs Protected |
|
June 5, 2017 |
Blockchamin[.]info |
104.18.44[.]38 |
WhoIs Protected |
|
June 2, 2017 |
Blcekchain[.]info |
81.177.135[.]153 |
drujinin.sergey2018@ya[.]ru |
|
June 2, 2017 |
Htpps-blockchain [.]info |
185.35.137[.]204 |
WhoIs Protected |
|
May 22, 2017 |
Blocklchaln[.]info |
198.15.115[.]235 |
WhoIs Protected |
|
May 22, 2017 |
Blockchiean[.]info |
185.35.139[.]31 |
WhoIs Protected |
|
May 2, 2017 |
www.https-blolkchieins[.]info |
185.35.139[.]31 |
WhoIs Protected |
|
April 15, 2017 |
www.wallet .blockschain[.]pw |
185.188.204[.]96 |
WhoIs Protected |
|
April 4, 2017 |
Blockchaiin-wallat [.]info |
166.62.10[.]143 |
WhoIs Protected |
|
April 4, 2017 |
Blockchain-login3 [.]info |
91.218.247[.]90 |
boatbits@yandex[.]com |
|
April 4, 2017 |
Blockchain-login2 [.]info |
91.218.247[.]90 |
boatbits@yandex[.]com |
|
March 22, 2017 |
Blokchain-wallet5 .info |
91.218.247[.]90 |
boatbits@yandex[.]com |
|
March 11, 2017 |
11-blockchain[.]info |
91.218.247[.]90 |
boatbits@yandex[.]com |
|
March 9, 2017 |
7-blockchain[.]info |
91.218.247[.]90 |
boatbits@yandex[.]com |
|
March 9, 2017 |
6-blockchain[.]info |
91.218.247[.]90 |
boatbits@yandex[.]com |
Table 1: Examples of recent typosquatted and otherwise fraudulent domains used for Blockchain phishing
The email address boatbits@yandex[.]com was used to register a large number of typosquatted blockchain phishing domains in June 2016. Many of these domains are still active and have been used recently in phishing campaigns. Most recent domain registrations are concealed via WhoIs protection.
We have also observed similar typosquatting tactics being used against coincheck[.]com, which is described as “The Leading Bitcoin and Cryptocurrency Exchange in Asia” (Figure 8).
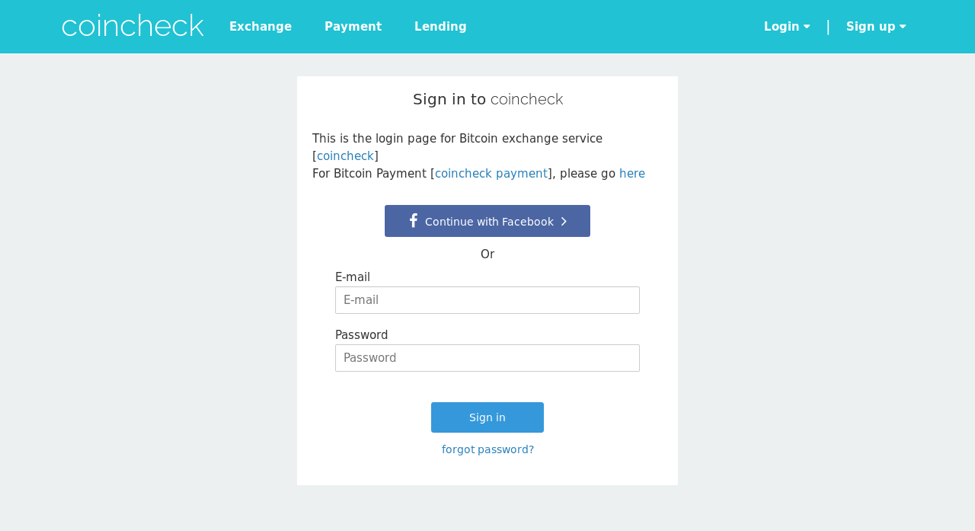
Figure 8: Coincheck phishing landing - coin-check[.]com
Some recent domains that have been registered are currently just redirecting to the legitimate coincheck[.]com. They will likely be activated at some point to lead visitors to a fake page when needed.
|
Date Observed |
Domain |
IP |
Registrant |
|
June 12, 2017 |
coinchec[.]com |
119.28.48[.]240 |
WhoIs Protected |
|
June 12, 2017 |
coinchck[.]com |
119.28.48[.]240 |
WhoIs Protected |
|
June 12, 2017 |
coinceck[.]com |
119.28.48[.]240 |
WhoIs Protected |
|
June 6, 2017 |
coin-check[.]com |
88.212.244[.]12 |
WhoIs Protected |
Table 2: Examples of recent typosquatted and otherwise fraudulent domains used for coincheck[.]com phishing
The recent increase in the value of Bitcoin has carried over to a lesser extent in alternative cryptocurrencies. While targeting online wallets is one vector of attack, another is to gain access to exchanges where users may keep virtual currency for the purpose of selling or exchanging them for other crypto or traditional currencies. For example, we observed scams targeting the popular cryptocurrency exchange Poloniex, one of the most active exchanges for alternative crypto coins such as Ethereum, Dash, Stratis, Monero, and many others. One phishing page in particular, poloniex-login[.]info, was taken down after we notified the host.
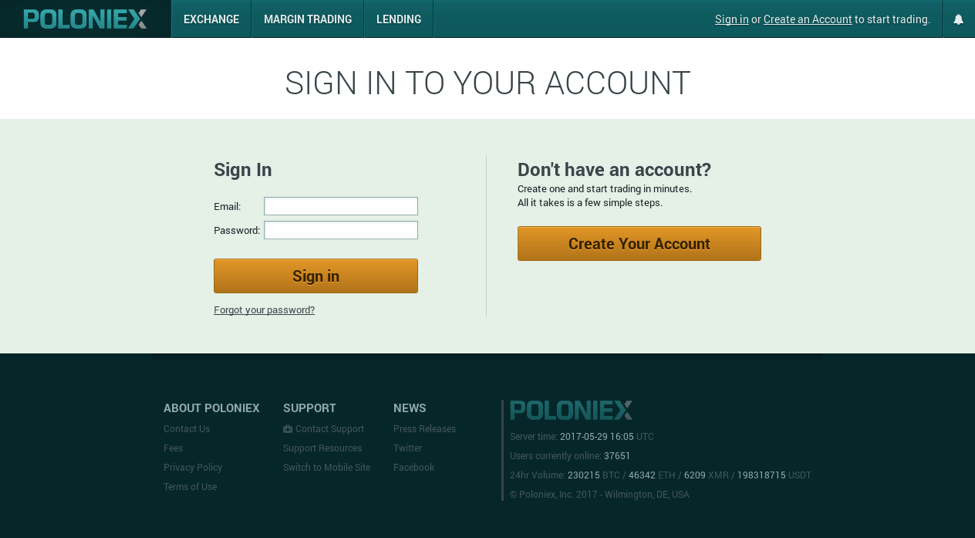
Figure 9: Poloniex phishing landing - poloniex-login[.]info with stolen branding. This site has since been taken down.
Moreover, we observed phishing scams for coins.ph, a blockchain service in the Philippines that provides banking and payment services to those in the Philippines and Southeast Asia (Figure 10).
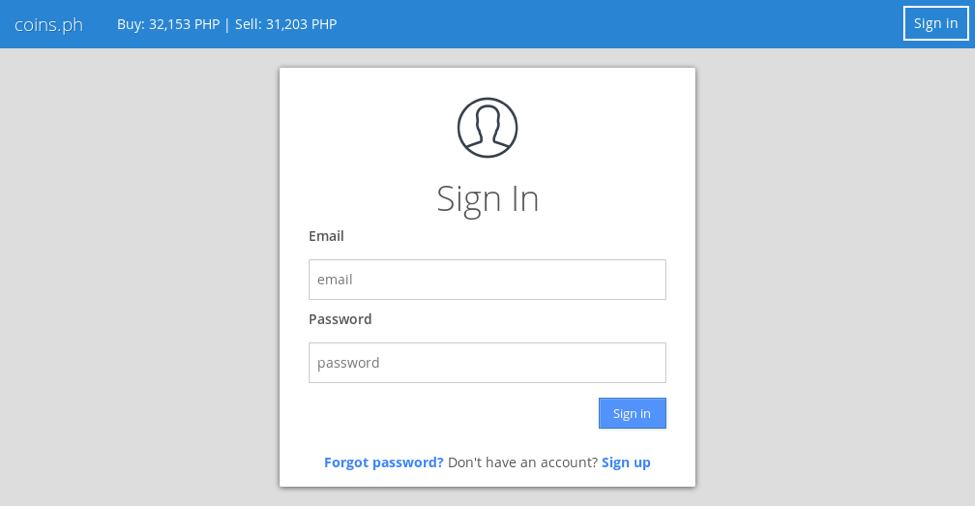
Figure 10: Coins.ph phishing landing with stolen branding
Other cryptocurrency brands and services such as Coinbase have also been the subjects of phishing scams; actors continue to promote their kits for sale via YouTube (Figure 11).
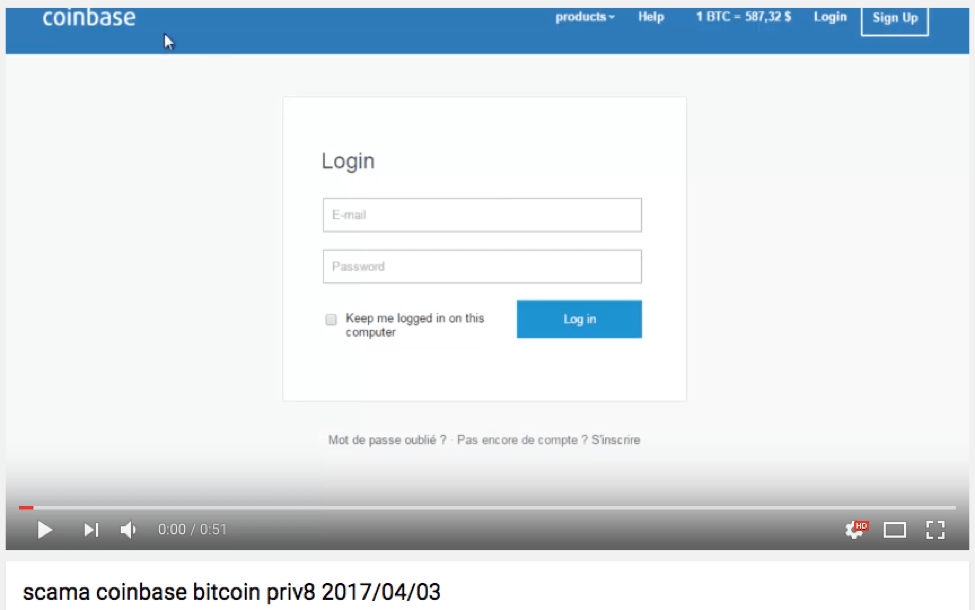
Figure 11: YouTube promotional video for a Coinbase phishing template
Conclusion
The term “phishing” dates back over 20 years and was coined by attackers stealing America Online credentials. Since then, phishing schemes have continued to evolve, with actors changing their techniques to capitalize on the latest trends and new avenues into victims’ credentials and, ultimately, their wallets. In the cases described here, those wallets are virtual and contain cryptocurrencies, a means of exchanging value anonymously that has only recently received mainstream attention.
Recently, we have observed a number of phishing templates and email lures that mimic online wallets like Blockchain.com and cryptocurrency exchanges like Poloniex. These templates attempt to steal wallet IDs and credentials that allow actors to conduct fraudulent transactions with third parties or withdraw funds directly. Unfortunately, the anonymous nature of cryptocurrency transactions makes fraud even harder to detect. Users should guard their credentials carefully and be vigilant for typosquatted domains and unexpected notifications from wallet and exchange services. More importantly, online wallets and exchanges should never be considered trusted storage for cryptocurrencies.
ETPRO Signatures
2820803 - Possible Successful Generic Phish Jun 22
2821772 - Successful Blockchain Phish Aug 19 2016
2824382 - Successful Blockchain Phish Jan 11 2017
2825960 - Successful Blockchain Phish Apr 13 2017
2826611 - Blockchain Phishing Landing Jun 02 2017
2826612 - Successful Blockchain Phish Jun 02 2017
2826602 - Successful Poloniex Cryptocurrency Exchange Phish Jun 02 2017
2826662 - Blockchain Phishing Landing Jun 07 2017
