The Dridex banking Trojan is already well-known and documented in analyses by security researchers from Proofpoint and other organizations. Over the last week, Proofpoint researchers detected a sudden change in Dridex behavior that represented the entrance of a new actor and a significantly increased danger to many organizations.
Normally, Proofpoint sensors detect a small number (less than ten) of Word document attachments delivering the same Dridex malware. For example, the Dridex actor that uses botnet 125 (which we analyzed previously) typically distributes only two different Word documents in their total volume of unsolicited emails on a given day. This means that the same malicious attachment will likely be received – and therefore detected by gateway security engines – many times across many organizations, creating a strong chance that it will quickly be classified as malicious and blocked by gateway filters.
Beginning December 12, Proofpoint sensors detected a spike in document attachments distributing Dridex, from the normal 2-4 documents to eighty-seven. The filenames followed a format of “billing_details_<random numbers>.doc”, continuing the recent popularity of “financial account update” phishing templates. These distinct documents were being distributed more thinly, with on average 2-3 variants of each document being received at any single company, but some larger organizations received as many as ten different document attachment variants. (By comparison, in prior campaigns a single company may have seen thousands of emails, all containing the same document attachment.) This combination of greater variants and thinner distribution resulted in higher rates of evasion of antivirus and spam filters. (Proofpoint Targeted Attack Protection was able to detect and block them, however.)
After a day-long spike and return to normal rates, the campaign surged again on December 15, with similar volume (eighty-seven distinct document attachment variants again) and characteristics. The phishing template and filename format remained the same, with the exception that the filename became “ship invoice_<random number”, as this example shows:
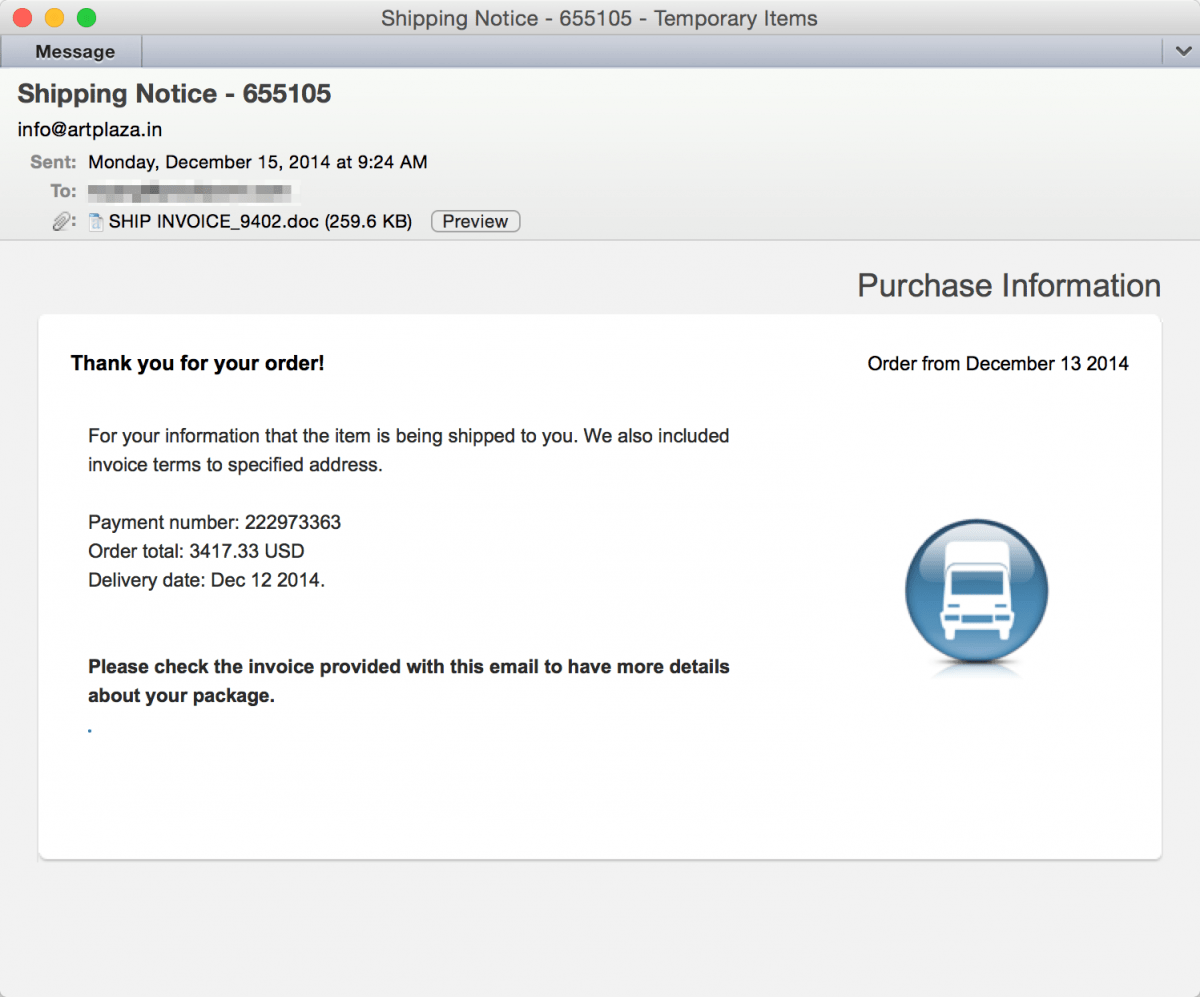
From this wave, Proofpoint researchers were able to extract the configuration file of a Dridex sample and identify a new Dridex botnet, with ID number 305. The combination of a new behavior with a new botnet suggested that a new actor was entering the scene. As the next days would show, the new actor was just getting started…
Within days Proofpoint detected a massive surge in the new actor’s activity: from several dozen unique documents (itself significantly greater than normal), the volume of unique documents spiked to hundreds, generating a fresh document attachment every 2-3 minutes. In the space of a single day, almost 600 confirmed malicious documents connected to botnet 305 were detected, a quantity hundreds of times greater than normal, as the chart below demonstrates:
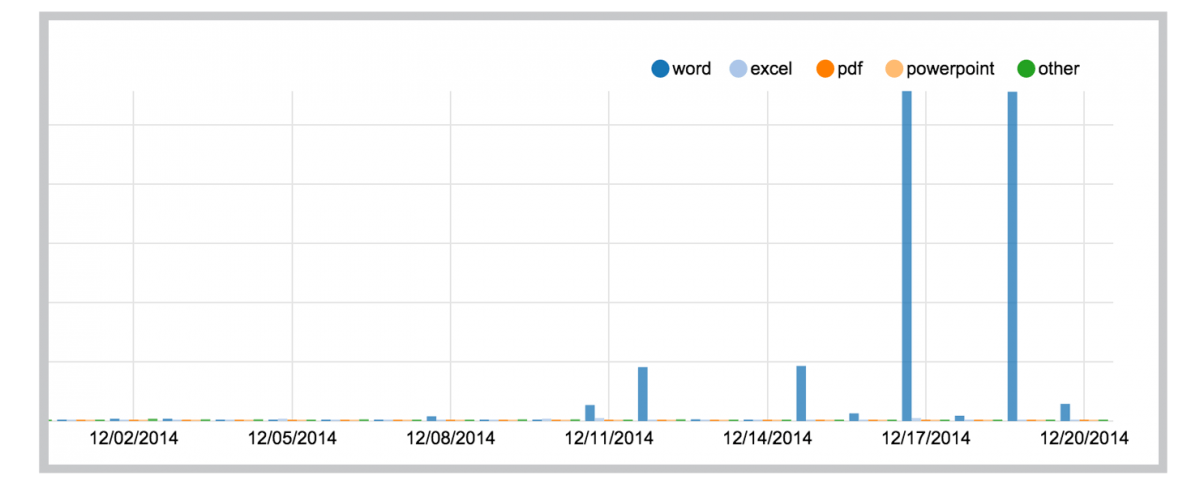
As the chart shows, the quantity of unique, confirmed malicious Word documents generated for this single botnet was both massive and anomalous. The documents were sent through over half a million messages, making this a relatively high volume campaign as well. For the day, the number of scanned documents remained roughly consistent with normal volumes, meaning that a much higher proportion of attachments were malicious than usual – almost two orders of magnitude greater than normal.
By comparison, for example, Dridex botnet 125 continued at their normal volume of approximately two unique documents per day. As a result, while the volume of malicious messages was almost evenly divided between the two actors, the new botnet 305 actor accounted for 99 percent of malicious document attachments.
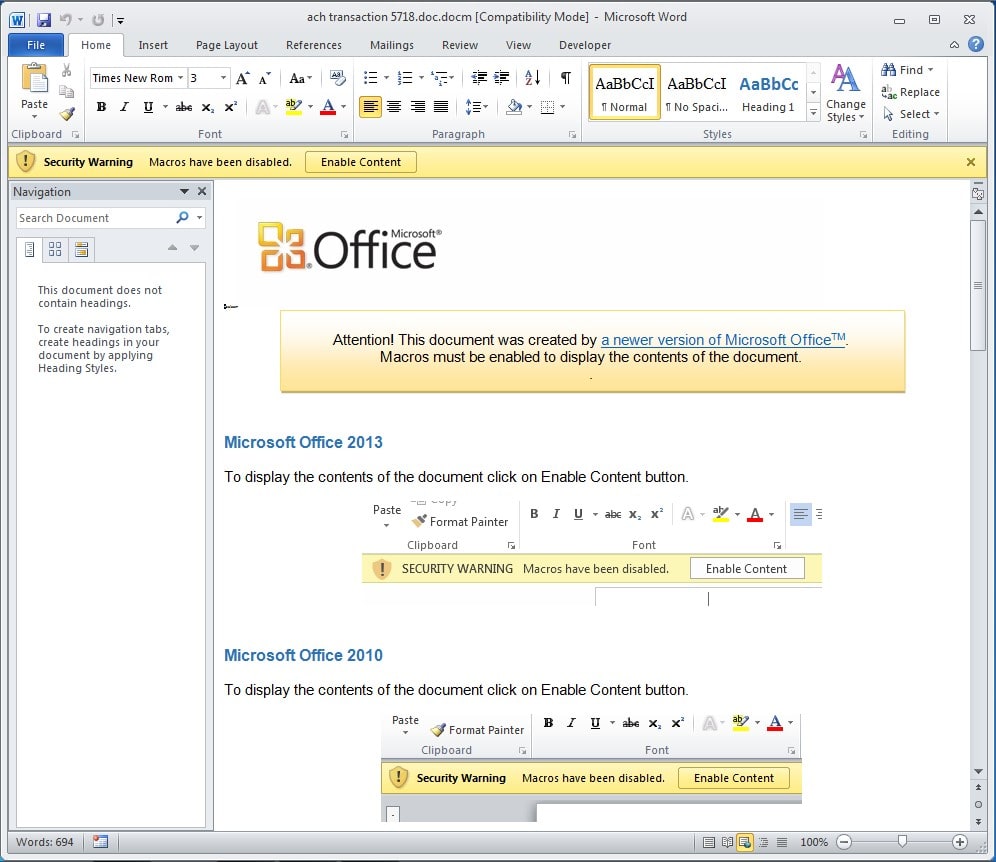
The succeeding waves used a filename format of “ACH transaction <random number>, presumably in order to improve evasion of filters that had adapted to look for the previously used filename formats. For the documents themselves, these were typical of the malicious Office attachments that have been very popular with attackers in 2014. The documents incorporate social engineering in order to persuade the recipient to click the Enable Content button, presenting the following message when the Word attachment is opened:
Attention! This document was created with a newer version of Microsoft Office™.
Macros must be enabled to display the contents of this document.
The attackers even helpfully provide instructions on how to enable the malicious content on multiple versions of Microsoft Office:
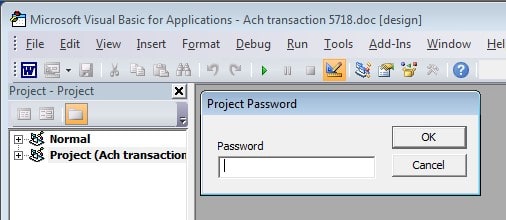
While the attackers try to make it easy for end-users to run the malicious macro that will lead to the infection of their system, they take the opposite tack for security researchers and antivirus engines by password-protecting the macro code itself. Attempting to examine the macro code brings up a prompt to enter a password: requiring a password makes it more difficult for researchers to view and analyze the code, and may thwart automated analysis tools.
This campaign combined high volume, high variability, frequent new variants, and research-resistance, and the result was high effectiveness at evading existing antivirus and anti-spam rules. Rather than pushing out almost 600 different document variants simultaneously, the attackers rotated to a new document every 20-30 seconds, continuously injecting new document attachments into the campaign in order to stay ahead of antivirus and reputation filters. In short, this approach highlights a system that was clearly designed with the express purpose of thwarting any reputation-based defenses.
Extracting the configuration file revealed an extensive list of target banks comprised primarily of national and regional US-based banks. The botnet 305 Dridex thus resembles its peers in its efforts to steal online banking credentials from the widest possible range of banking targets, but in this case seems to be driven by a new actor seeking to “drain the swamp” and mine the largest possible number of victims before defenses finally adapt to the malicious macro exploits of 2014 and reduce the viability of this avenue of infection. Are these the death throes of malicious macros, or the beginning of a new chapter in the resurgence of this attack technique?
UPDATE 1/7/15
In the days after this post was published, Proofpoint detected a surge in unsolicited email from multiple Dridex botnets, including the two mentioned above. In addition to the 125 and 305 botnets, Proofpoint also saw activity from a Dridex botnet with the ID 120. Comparing their campaigns highlights the difference in their respective approaches to using malicious documents to infect client systems.
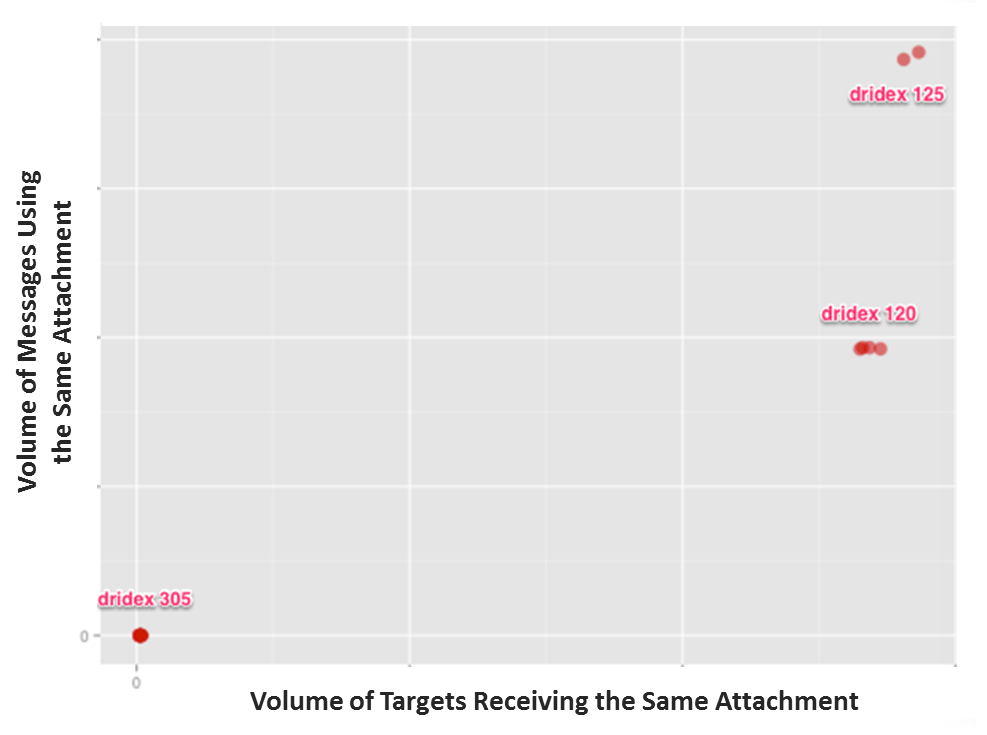
As the chart above shows, the 305 Dridex actors continued their practice of creating a very large number of malicious Word document variants and then spreading them thinly across their pool of targets: each document variant was attached to a relatively small number of messages and sent to a small handful of target organizations.
By contrast, the 120 and 125 actors generated a relatively small number of malicious Word document variants, then attached each variant to hundreds of thousands of messages, and sent them to hundreds of target organizations.
While the infrastructure employed by cybercriminals has become somewhat standardized, one of its chief strengths lies in the flexibility it offers attackers as they plan and carry out their campaigns. Using the same tools and techniques, these Dridex campaigners still demonstrate very different approaches to one of the most important stages of the process: evading detection in order to infect a client system. Organizations need to adopt similarly flexible and effective defenses if they hope to meet this challenge.

