Overview
As is often the case during major events that generate significant public attention, Proofpoint researchers observed a number of phishing lures capitalizing on Hurricane Michael. However, while phishing schemes related to natural disasters often attempt to steal credit card numbers used for fake donations or steal funds directly via fraudulent donations, many of these recent campaigns were focused on webmail credential theft. Interestingly, the campaigns also leveraged blob storage on Microsoft Azure infrastructure to inexpensively host phishing templates.
Phishing campaigns
Many of the recent phishing campaigns with Hurricane Michael lures used PDF documents attached to email. They include file names such as:
- florida hurricane michael emergency and recovery procurement.pdf
- florida hurricane michael emergency and disaster recovery procurement.pdf
- vdot hurricane michael emergency and recovery procurements.pdf
As shown in Figures 1 and 2, the lures are fairly generic, relying on embedded links and social engineering to entice recipients to click. Both figures show stolen branding for actual government agencies.
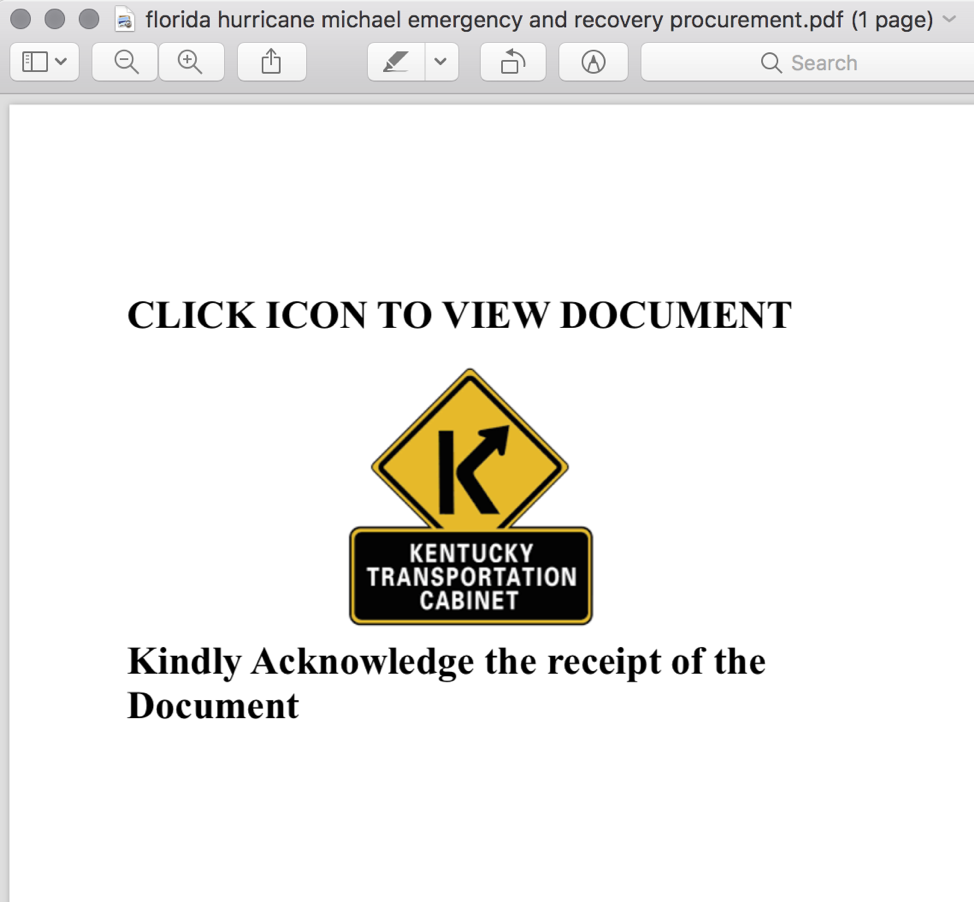
Figure 1: A PDF lure with an embedded link and stolen branding for the Kentucky Transportation Cabinet
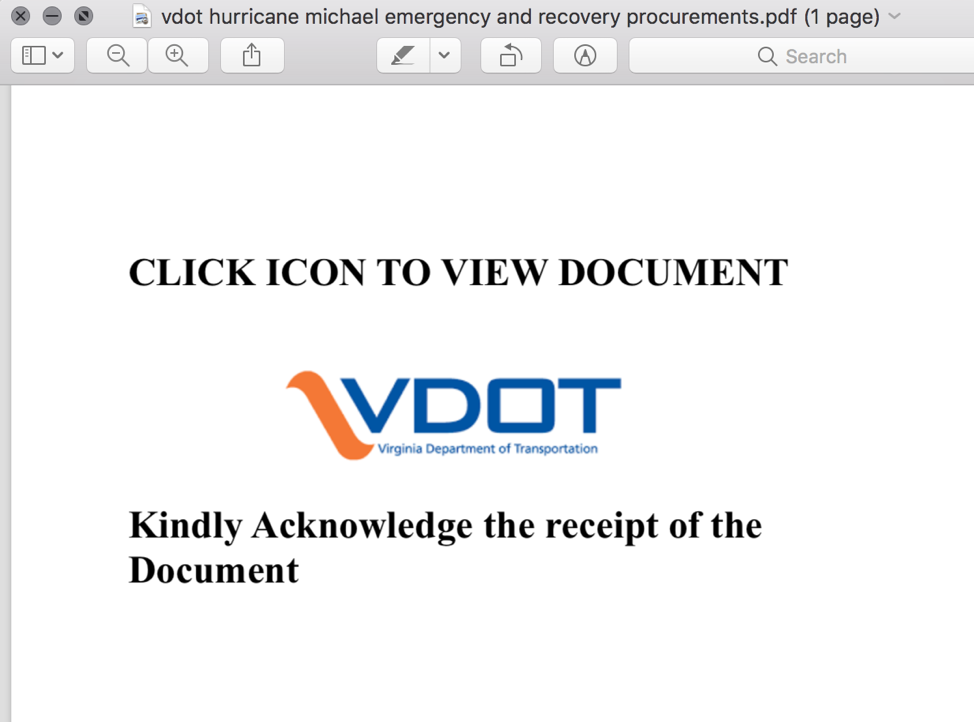
Figure 2: Another PDF lure with an embedded link and stolen branding for the Virginia Department of Transportation
Clicking on the linked icons opens a bit.ly link, a secondary link shortener, and then the final link to the phishing landing page.
The clickthrough rates appear to be relatively low for these links, with just over 500 total clicks for the three URLs we observed associated with this campaign (Figure 3).
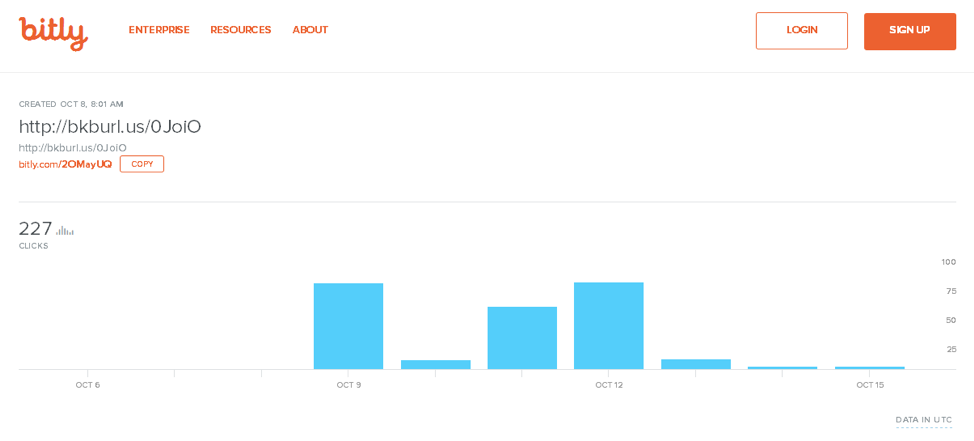
Figure 3: Statistics for clickthroughs on the initial links from PDFs associated with these phishing campaigns
Despite the overall low click rates, however, the final URLs are of interest:
- https:[//]dropboxembright19604.blob.core.windows[.]net
- https:[//]onedriveunfragrant26.blob.core.windows[.]net
- https:[//]onedrivechowry495462.blob.core.windows[.]net
These are HTTPS-only phishing pages hosted on official windows[.]net domains. We have observed phishing pages hosted using Microsoft Azure blob storage since August of this year. The tactic is inexpensive and especially effective for scams purporting to be legitimate Microsoft services.
The SSL/TLS certificate commonName field present in this case is a wildcard certificate that cannot be used as an effective means of detection, as seen in Figure 4. There are other ways to detect the malicious activity, such as DNS requests by inspecting the TLS server name indication.
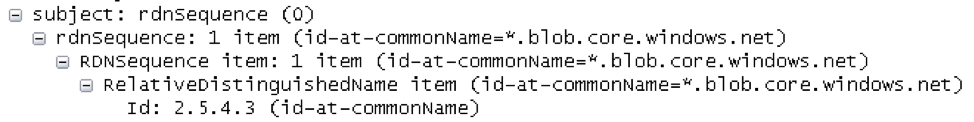
Figure 4: Wildcard certificate issued for all domains (good and bad) on this domain
Some other recently observed phishing domains abusing Microsoft Azure blob hosting include:
- Oct 14 2018 dropboxmarling951049.blob.core.windows[.]net
- Oct 12 2018 cs7a779f8678a3dx443cxbf5.blob.core.windows[.]net
- Oct 12 2018 onedrivedocument3.z13.web.core.windows[.]net
- Oct 11 2018 krdas56-secondary.z19.web.core.windows[.]net
- Oct 11 2018 excelouttravel858824.blob.core.windows[.]net
- Oct 11 2018 onedrivemyliobatoid4.blob.core.windows[.]net
- Oct 11 2018 onedrivemoton8532961.blob.core.windows[.]net
- Oct 11 2018 godaddyreimplant9949.blob.core.windows[.]net
- Oct 11 2018 onedrivedocs3.z13.web.core.windows[.]net
- Oct 11 2018 onedrivedocument0.z13.web.core.windows[.]net
- Oct 11 2018 onedrivebroadwayite7.blob.core.windows[.]net
- Oct 10 2018 office365totalized87.blob.core.windows[.]net
- Oct 10 2018 darkcloud.z13.web.core.windows[.]net
- Oct 10 2018 ducosignsurahs721013.blob.core.windows[.]net
- Oct 10 2018 dropboxsphingurus894.blob.core.windows[.]net
- Oct 10 2018 adobeadvanceable4826.blob.core.windows[.]net
- Oct 10 2018 onedriveexactas84338.blob.core.windows[.]net
- Oct 9 2018 henricocountyassiste.blob.core.windows[.]net
- Oct 9 2018 office365parasyphilo.blob.core.windows[.]net
- Oct 9 2018 office365funguses335.blob.core.windows[.]net
- Oct 9 2018 adobeinthralls778398.blob.core.windows[.]net
- Oct 9 2018 onedrivenonalphabeti.blob.core.windows[.]net
- Oct 9 2018 ducosignunkept514717.blob.core.windows[.]net
- Oct 9 2018 onedriveunfragrant26.blob.core.windows[.]net
- Oct 9 2018 onedrivesuiogothic82.blob.core.windows[.]net
- Oct 9 2018 godaddybeautifier270.blob.core.windows[.]net
- Oct 8 2018 dropboxovertalkative.blob.core.windows[.]net
The resulting phishing landing page is also a relatively generic template that attempts to trick victims into giving away their webmail credentials for the promised hurricane-related document.
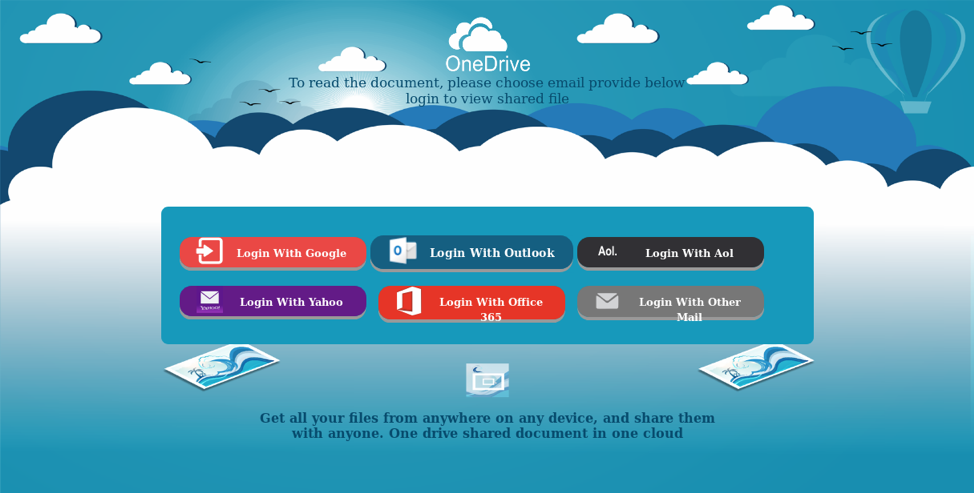
Figure 5: Phishing landing page abusing Microsoft Azure blog hosting
We detected several other landings related to this threat abusing Microsoft azure blob hosting. Examples of these pages that also abuse other frequently phished brands appear in Figures 6-9.

Figure 6: A phishing landing page abusing similar infrastructure and stolen branding for email credential theft
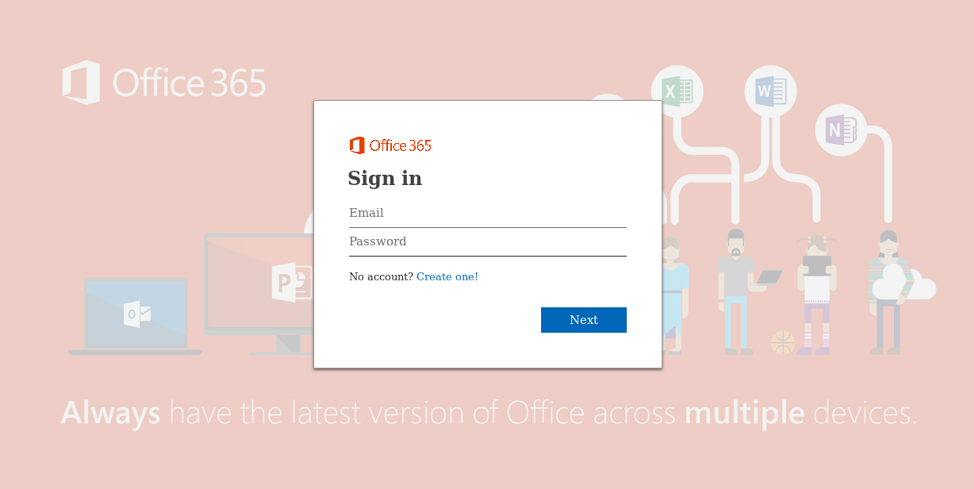
Figure 7: A phishing landing page abusing similar infrastructure and stolen branding for Microsoft Office 365 credential theft
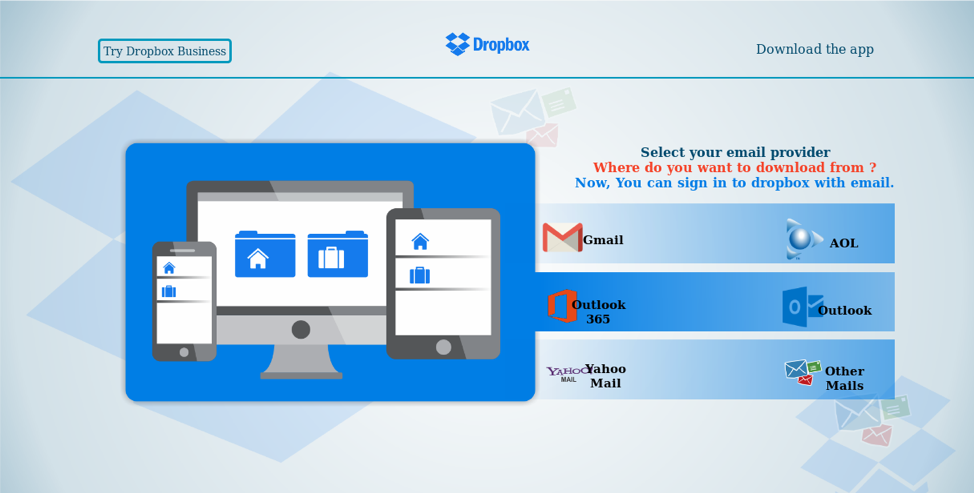
Figure 8: A phishing landing page abusing similar infrastructure and stolen Dropbox branding for email credential theft
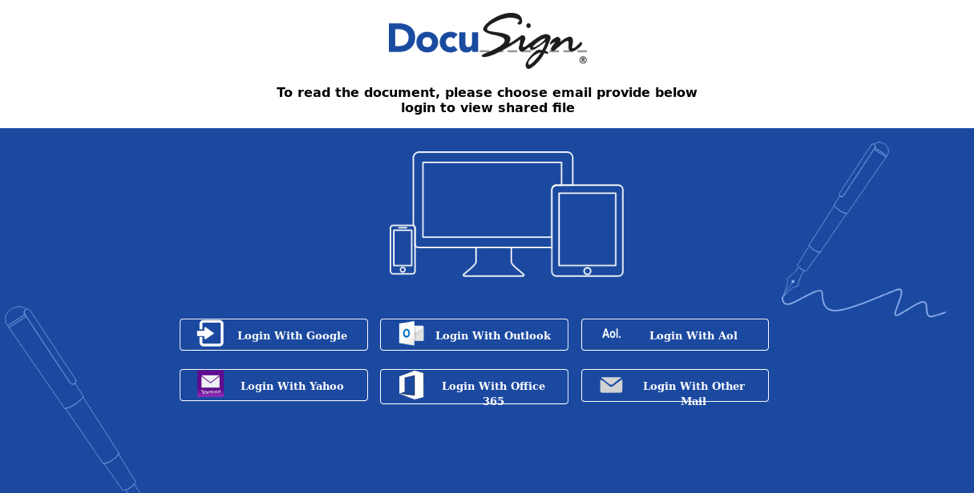
Figure 9: A phishing landing page abusing similar infrastructure and stolen Docusign branding for email credential theft
Conclusion
Fraud and scams always appear around major events, whether the Olympics, presidential races, or hurricanes. These events serve as lures for both related and unrelated phishing, fraudulent transactions, and straight theft. In this case, the phishing schemes stand out because the threat actors are directing recipients to credential theft pages for both corporate and personal email rather than credit card or financial theft. This is consistent with dramatic increases we have observed recently in corporate credential phishing. However, this should also serve as a warning for recipients who are accustomed to entering email credentials to log into multiple services. Threat actors are capitalizing on both this desensitization and our desire to do good. While none of these are new tactics on their own, the combination is of interest to defenders and potential victims. Those wishing to make charitable donations or seeking assistance should go directly to websites associated with known disaster relief organizations and should never enter webmail or social media credentials to enable donations.
ET OPEN IDS Signatures:
2026486: DNS Lookup for Possible Common Brand Phishing Hosted on Legitimate Windows Service
2026487: Request for Possible Common Brand Phishing Hosted on Legitimate Windows Service

