Overview
So-called “sextortion” scams, in which threat actors send blackmail emails claiming to have compromising information about the recipient and threaten to expose a range of observed illicit activities, are becoming increasingly common. In general, these emails simply demand payment to avoid publication of the purported evidence of compromising information. However, this week Proofpoint researchers observed a sextortion campaign that also included URLs linking to AZORult stealer that ultimately led to infection with GandCrab ransomware.
Common sextortion techniques
Proofpoint researchers have been observing pervasive sextortion campaigns for many months now, most without links or attachments. They generally include:
- A statement that the recipient’s computer has been compromised with some type of spyware or a keylogger
- To make the email more believable often a method such as the following is used:
- A password associated with the email account, sometimes obtained via previous data breaches is included
- Information that can be obtained from open sources is included such as spouse, employer, or occupation
- Accusations of impropriety online or of inappropriate files stored on the device
- A demand for a payment to a Bitcoin wallet to avoid having evidence of the purported impropriety exposed on the Internet or sent to the recipient’s contacts
Sextortion campaign with ransomware - December 5, 2018
On December 5, we observed a new sextortion campaign involving thousands of messages sent to a variety of targets primarily in the United States. A sample email shown in Figure 1 follows the basic formula for these types of attacks but also includes a URL that resolves to jdhftu[.]tk. The URL purportedly takes recipients to a presentation showing them video of the compromising activities captured on their device. However, it actually leads to AZORult stealer malware, which, in turn, installs GandCrab ransomware, version 5.0.4 with affiliate ID "168;777".
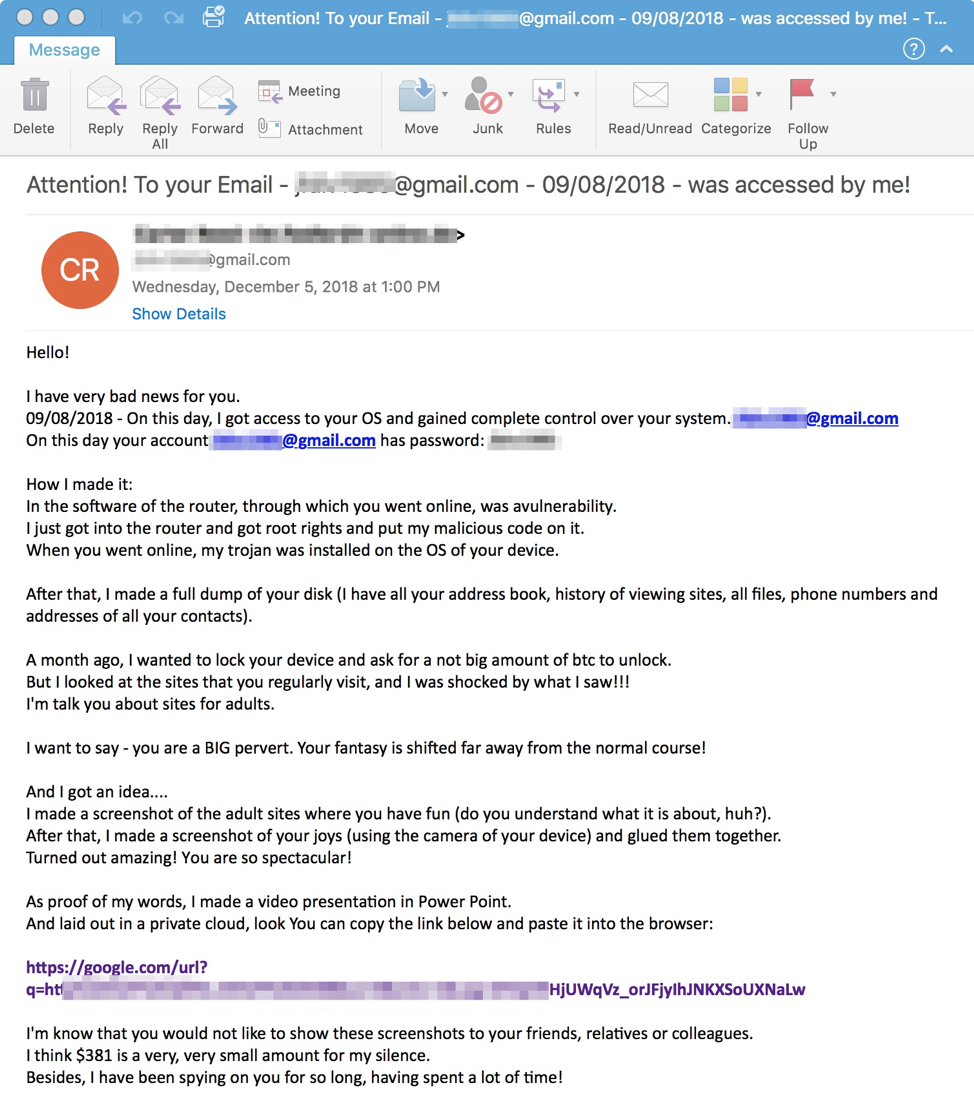
Figure 1: Sextortion email from December 5, 2018, with a URL linking to AZORult stealer
This particular attack combines multiple layers of social engineering as vulnerable, frightened recipients are tricked into clicking the link to determine whether the sender actually has evidence of illicit activity.
The supposed password for the potential victim’s email address in this case appears to be the same as the email account. Therefore, in this case it may simply be a bluff and the attacker does not actually possess the victim’s password.
If the potential victim does click and follow through with installing ransomware linked in the email, GandCrab ransomware is installed. GandCrab in this case demands a payment of $500 in Bitcoin or DASH.
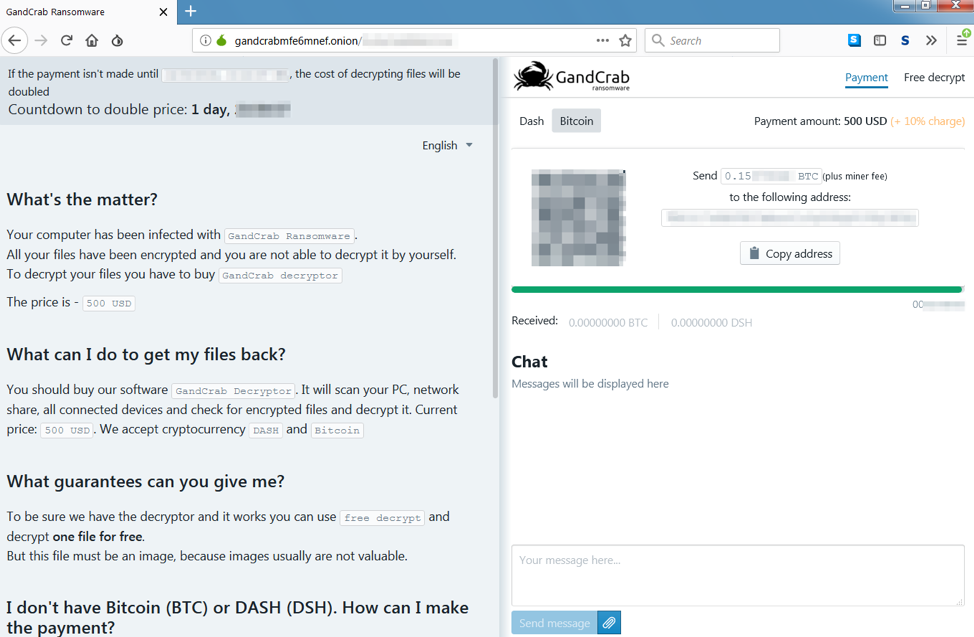
Figure 2: Payment portal for GandCrab
Conclusion
Sextortion preys on the fears and insecurities of recipients, using stolen passwords and other social engineering tricks to convince recipients that their reputations are actually at risk. Adding a URL linking to ransomware that purports to be a presentation showing the recipients illicit activities is a new technique, increasing the risk associated with this type of attack. Individuals receiving sextortion emails should 1) assume the sender does not actually possess screenshots or video of any compromising activity and 2) should not click any links or open attachments to verify the sender’s claims.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
hzzp://jdhftu[.]tk/&4448<anonymized> |
URL |
URL in email |
|
a7ba2c9def86e54086f0624a73597865a90cb93aa72dec7fdf264f655cf1bb56 |
SHA256 |
Foto_Client89661_01.zip (Compressed AZORult) |
|
29b42b0ecd874bcad5a5d9d03ed8f8dee320892305312b4898a0b64f9fbde93a |
SHA256 |
Foto_Client89661_01.scr (AZORult) |
|
hxxp://egorgerov3[.]temp[.]swtest[.]ru/index.php |
URL |
AZORult C&C |
|
hxxp://supermainers[.]online/exp.exe
|
URL |
AZORult payload (GandCrab) |
|
ef07905923461ce13a3ca18ef6eb1833a8c8d327d47e9cc8641a2ca3d5ce97f3 |
SHA256 |
GandCrab |
|
gandcrabmfe6mnef[.]onion |
Domain |
GandCrab Payment portal |
ET and ETPRO Suricata/Snort Signatures
2025638 || ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activit
Subscribe to the Proofpoint Blog

