Table of Contents
Definition
Most people have heard of phishing; vishing is a different attack that falls under the general phishing umbrella and shares the same goals. Vishers use fraudulent phone numbers, voice-altering software, text messages, and social engineering to trick users into divulging sensitive information. Vishing generally uses voice to trick users. (Smishing, yet another form of phishing that uses SMS text messages to trick users, is often used in tandem with voice calls depending on the attacker’s methods.)
Cybersecurity Education and Training Begins Here
Here’s how your free trial works:
- Meet with our cybersecurity experts to assess your environment and identify your threat risk exposure
- Within 24 hours and minimal configuration, we’ll deploy our solutions for 30 days
- Experience our technology in action!
- Receive report outlining your security vulnerabilities to help you take immediate action against cybersecurity attacks
Fill out this form to request a meeting with our cybersecurity experts.
Thank you for your submission.
What Is the Difference between Vishing and Phishing?
Phishing and vishing have the same goal: to obtain sensitive data from users that could be used in identity theft, monetary gain or account takeover. The main difference between phishing and vishing is the medium used to target potential victims. Whereas phishing is primarily an email-based attack, vishing uses voice, typically calls to a user’s cell phone number.
Both vishers and phishers send messages to potential victims, usually in high volumes. Phishing attackers send a large number of email messages to a list of potential targets. If the attacker targets a specific organization, only a list of high-privileged user email addresses from the targeted business might be used. Phishers generally use compelling email messages to trick users into replying with sensitive information or convince the user to click a link where malware is hosted. Malicious attachments are also used in some phishing attacks.
The visher might first send a text message to potential victims in high volumes from a long list of phone numbers. The message might ask users to make a phone call to the attacker’s number. Another vishing method creates an automated message and robo-dials potential victims. It uses computer-generated voice messages to remove accents and build trust. The voice message then tricks the user into connecting to a human agent who continues the scam, or the it might ask users to open an attacker-controlled website.
Although there are minor differences between vishing and phishing, the end goal is always the same: credentials, personal identifiable data and financial information. Users familiar with phishing might not be familiar with vishing, so attackers increase their chance of success.
What Is the Difference between Vishing and Smishing?
Smishing is a closely related phishing attack that also uses smartphone numbers. But instead of voice mail, smishing uses text messages to trick users. These messages could contain a phone number for a targeted user to call or a link to an attacker-controlled website hosting malware or a phishing page.
Smishing relies mainly on users trusting text messages. The messages usually promise prize money, coupons or threaten to cancel accounts if the user does not authenticate and reset credentials. Because text messages are more informal, victims may trust text messages more than a suspicious email.
There is a lot of overlap between smishing and vishing. A vishing attack might also start with a text message and contain a phone number asking users to call, but vishing attacks could also use automated messages and robocalls. Smishing can also include a phone number in a text message, but many attacks focus mainly on tricking users into clicking links and opening a malicious website page.
Protect Against Phishing
Choose the No. 1 email security solution in preventing phishing attacks
Vishing Techniques
It’s more challenging to identify a vishing attack than a phishing and smishing attack. Vishing attacks start with a text message and usually contain a phone number.
The following image is an example of a vishing attack:
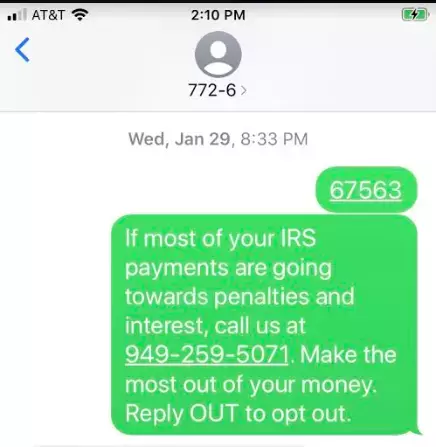
Scammers use scare tactics to convince users to make a phone call. In this message, the attacker pretends to be with the IRS. Most users are afraid of penalties and fees from the IRS, so any users who call this phone number will be told that they owe money. The attacker convinces the targeted user to charge their credit card or to transfer money directly from the targeted user’s account. IRS scams are one of the more common attacks targeting users in the U.S.
The following image is another example of a vishing attack starting with a text message:
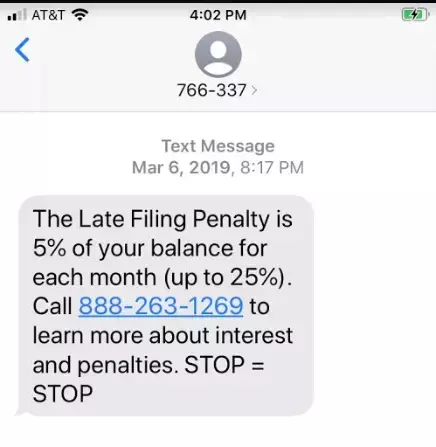
In the above picture, the same threats and scare tactics are used to convince users to call. If the targeted user responds with STOP, the messages will continue. By replying to the attacker, the targeted user verifies that the phone number is valid and will continue to be a target.
Notice in both images that the number listed in caller ID is a short 6-digit invalid contact number. These numbers are used by telecoms to send users messages, but it’s also an indication that the message was sent from an auto-dialer API or an email account. If a message comes from one of these numbers, always be suspicious that it could be a smishing or vishing scam.
Not every message with an invalid number in caller ID is malicious. These numbers are also used in multi-factor authentication requests when the user is sent a PIN to complete the authentication process. Social engineering attackers will trick users into sending the PIN, but this involves contacting the user and tricking them into divulging the PIN. Vishing, phishing and smishing can all be combined with social engineering for more large-scale attacks on high-privilege accounts.
Among attackers who stick to phone calls, it’s become more popular to use computer programs to mask voices and geographical accents. Attackers can even use a different gendered voice to launch an attack. Often, these voices are audibly computer-generated and obvious vishing attempts. But always be aware of phone calls asking for private information over a call.
How to Prevent Vishing
The best way to avoid being a victim of vishing is to ignore the messages. Telecoms have fraud systems in place that display “Fraud Risk” (or something similar) on caller ID when a known malicious call is received. However, you can’t rely on the telecoms to catch all malicious calls. Users can take their own precautions to avoid becoming a victim.
SIM swapping and social engineering leave your number vulnerable to attackers. SIM swapping involves socially engineering a telecom representative into giving an attacker access to your phone number. If you receive a strange message about a multi-factor PIN or changes to your cell phone account, always contact the telecom to ensure that you have not been the victim of SIM swapping and hijacking.
Here are a few steps to avoid becoming a victim of vishing and related attacks:
- Be aware of vishing. For organizations, educating users helps them identify vishing attacks, so they can ignore and report them. For individuals, never give out private information to someone contacting you from a text message or voice call. A legitimate institution will give the main number to call so that you can verify it’s an official call.
- Identify pressure and scare tactics. Scammers will pressure targeted users into sending money immediately, either using credit cards, bank transfers, or even gift cards. For instance, a common way to get users to fall for the IRS scam is to threaten jail time if money is not sent immediately.
- Ignore calls from unknown numbers. If you do not recognize the number, let the caller go to voicemail.
- Be skeptical of any caller that wants sensitive information. Never give any caller sensitive information regardless of where the caller claims to work.