Overview
CryptXXX has rapidly grown into one of the most prevalent ransomware variants in the wild with widespread distribution via exploit kits (EKs) such as Neutrino and Angler. As exploit kit traffic has declined (a 96% decrease between April and June), though, particularly in the wake of Angler's disappearance, threat actors normally reliant on EKs are diversifying approaches and looking to other vectors like email. For the first time, Proofpoint researchers have observed CryptXXX ransomware being distributed via malicious document attachments in email campaigns.
Analysis
On July 14, Proofpoint researchers detected an email campaign with document attachments containing malicious macros. If opened, these attachments download and install CryptXXX ransomware. The messages in this campaign had the subjects "Security Breach - Security Report #123456789” with attachments such as "info12.doc" or "i_nf012.doc." The report numbers and digits in the file names were composed of random numbers. The scale of this email campaign was relatively small, with only several thousand email messages observed, suggesting a test of the new distribution mechanism.
Figure 1 shows an example email message with one such malicious document attached.
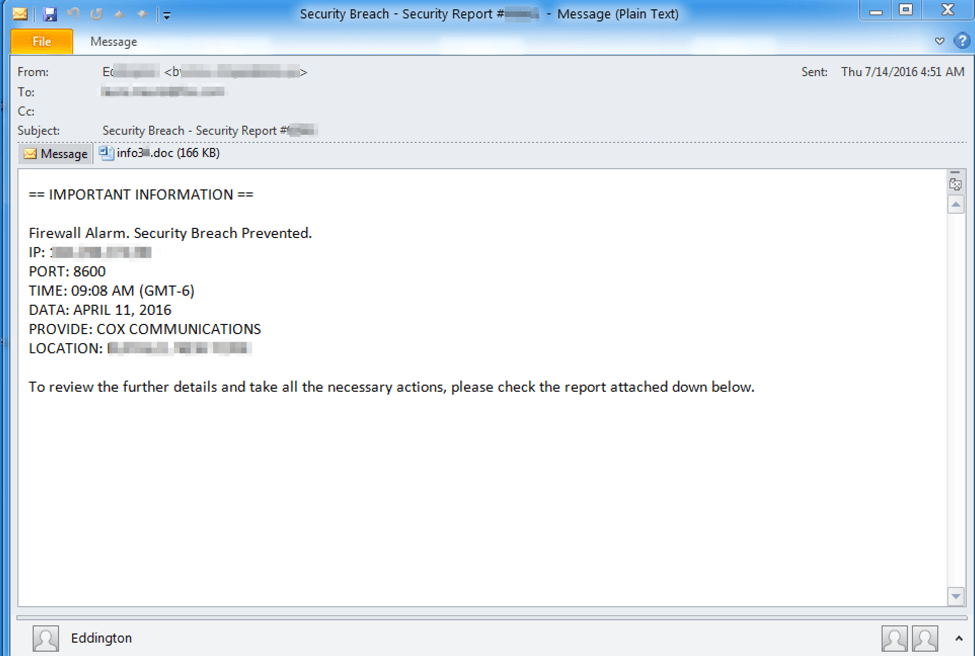
Figure 1: Email delivering the documents that download CryptXXX ransomware. Although the IP address is obscured in the figure, it is worth noting that both the second and third octets in our samples were numbers above 255; these would be obviously invalid to a network administrator but would maintain an air of urgency and credibility for many average users.

Figure 2: Document attachment that downloads the CryptXXX ransomware
The specific instance of CryptXXX delivered in this campaign is from affiliate ID U000022. We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis.
Conclusion
CryptXXX ransomware has propagated rapidly since appearing earlier this year. The ransomware was initially linked to groups associated with Angler and was distributed almost exclusively via Angler. As Angler activity dried up over this quarter, many actors turned to instances of the Neutrino exploit kit for distribution. Not surprisingly, with the disruption in the EK market, it appears that CryptXXX actors are turning to email as well. We will continue to monitor this trend and see if malicious document-based distribution of CryptXXX expands in the coming months.
Indicators of Compromise (IOC)
|
IOC |
IOC Type |
Description |
|
484a67c3d1d223792ab57f89a1bbd8a1fdee8b337d0c532cbc88115650b09001 |
SHA256 |
Macro document |
|
19be8d1cbce9c5c2bdad689308a3f17c29ef273b6717e1bebcea81282ca4e09a |
SHA256 |
Macro document |
|
770872484789ebc0e6b309920849041c3936fde2ceed85455917c278631ccdd6 |
SHA256 |
Macro document |
|
b41d38c0ebbda25f2fea33d2118583f26e3a0aa596192b891be7a191161e5df1 |
SHA256 |
Macro document |
|
f4715d018b5e9d93cf75d97559412c6783e16765b88eb8e36759fa059bf3ed4d |
SHA256 |
Macro document |
|
[hxxp://ubz[.]com[.]ua/plugins/system/ossystem/com_loader.jpg] |
URL |
CryptXXX downloaded by Macro document |
|
964608f4521362526e64d566d28072c2f145b4c69e09caea500d2db63b1e26b7 |
SHA256 |
CryptXXX |
|
91.220.131[.]147 |
IP |
CryptXXX C2 |
|
jchiyogcbhkamxv5[.]onion |
Hostname |
CryptXXX payment site |
Select ET Signatures that would fire on such traffic:
2819805 || ETPRO TROJAN CryptXXX CnC Beacon
2022840 || ET TROJAN Possible CryptXXX Ransomware Renaming Encrypted File SMB v2
Subscribe to the Proofpoint Blog

