Looking ahead at trends for 2024 on our threat research blog and podcast. And all the latest news on the Five-Minute Forecast.
This week on The Threat Hub: Selena Larson from the Proofpoint threat research team looks back at some of the most notable trends in the threat landscape during 2023—and explores what they could mean for the future of cybersecurity. From the rise of QR codes in phishing and malware campaigns, to the creative use of zero-day and N-day (disclosed and not-yet-patched) vulnerabilities by both e-crime and APT actors, to the increasing sophistication of AI-powered tools and techniques, the threat landscape is always changing and evolving. In the blog post, Selena also discusses best practices and recommendations for defending against these threats, such as leveraging threat intelligence, sandboxing and community sharing.
Or if you prefer your 2024 prognostications in podcast form, the Discarded team is back with episode two of their series on predicting cyber threats in 2024. This time, Selena and Crista are joined by Randy Pargman and Rich Gonzalez, who manage detections and Emerging Threats at Proofpoint. Topics covered include high profile incidents such as WinRAR, Citrix NetScaler ADC, and ScreenConnect vulnerabilities, as well as a discussion about the role of public-private partnerships and international cooperation in enhancing cyberdefenses.
And on this week’s Five-Minute Forecast, 23andMe shares details of stolen data in last year's breach, ransomware payments drop to a new low, and senior threat researcher Greg Lesnewich explains the inspiration behind the 100 days of YARA initiative.
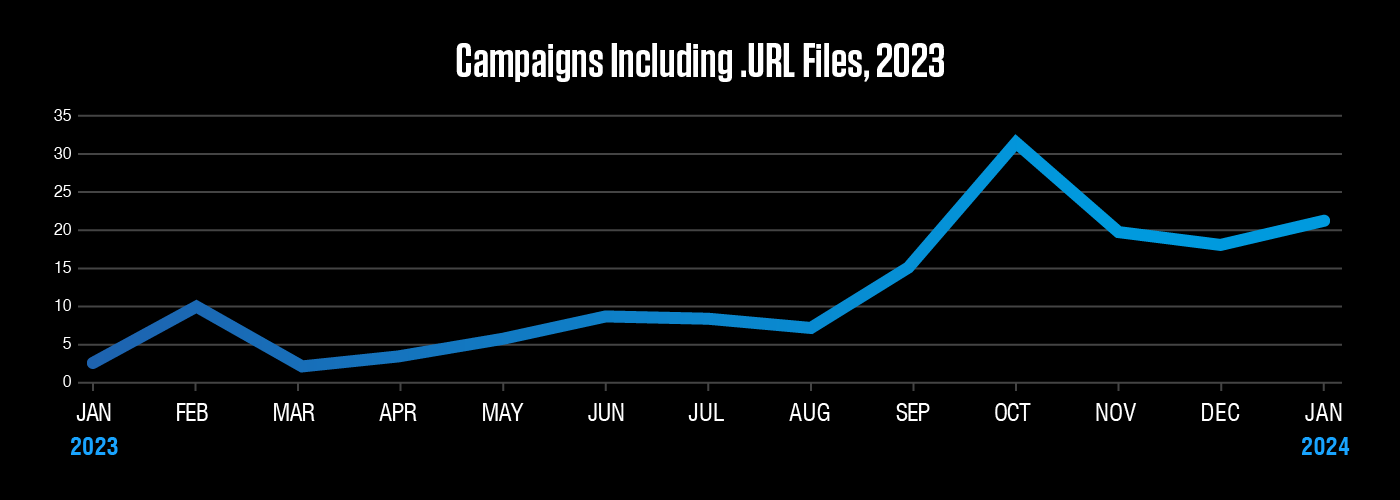
Use of .URL files increased significantly in the fourth quarter of 2023. Threat actors abuse this file type to embed links hosting malware payloads or credential phishing websites. Much of the increase can be attributed to actors abusing CVE-2023-36025, a vulnerability in Windows SmartScreen.
Equip your team with threat intelligence
Go Deeper with Proofpoint Threat Intelligence Services
Connect with threat analysts, understand threats with intelligence specific to your situation, and gain 24/7 visibility into the latest threat discoveries.
Learn MoreCyber attackers target people. They exploit people. Ultimately, they are people. That's why people—not technology—are the most critical variable in today’s cyber threats. This year, the 2023 Human Factor report takes an even closer look at new developments in the threat landscape, focusing on the combination of technology and psychology that makes the modern attack chain so dangerous.
About The Threat Research Team
Our threat researchers are responsible for tracking shifts in the cybersecurity landscape, identifying new attacks as they emerge, and monitoring how threat actor tactics, techniques and procedures change over time. The threats they detect and the signatures they write feed into our platforms and are keystones in a system that analyzes more than 2.6 billion emails, 49 billion URLs and 1.9 billion attachments every single day.
By studying what cyber criminals are doing now, our threat researchers are better able to anticipate what they’ll do next. Every day, their work keeps our customers protected—not just from today’s attacks, but tomorrow’s threats as they evolve.

Browse the threat hub
Subscribe to the Proofpoint Blog

