Means, Intent, and Opportunity are often cited as the requirements to prove a legal case in a court of law. When it comes to phishing, the means is email, and the intent is to make money, a process that starts with duping someone into clicking a link, filling a form, or opening an attachment. Tax season is an opportunity for scammers to find new victims, where the desire for a refund or fear of an audit may lead unsuspecting victims to click on malicious links. Indeed, the IRS has started to see this trend and have issued a warning, and other outlets have similarly urged caution.
Although April 15 is still months away, Proofpoint researchers have already been tracking this kind of activity: seen in the example email below from a very large, very widespread campaign (hundreds of thousands of messages across thousands of organizations) intended to spread the Dyre banking Trojan.
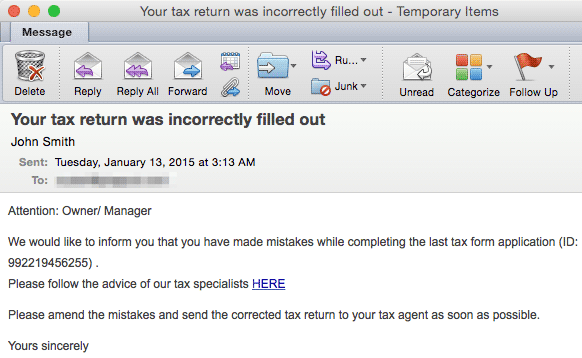
Dyre, which is a banking Trojan, is designed to help attackers drain bank accounts, making the email lure even more ironic. Victims were lured by a tax email to correct their tax return and avoid penalties but if they click and become infected, they pay a different penalty: hackers draining their bank account.
More importantly, however, is the creativity and innovation that scammers use to pursue the tax season scamming opportunity.
Proofpoint also detected other IRS-themed phishing attacks, with one phish using what appears to be a very convincing IRS form in PDF format that victims need to fill out and fax to a 1-800 number.
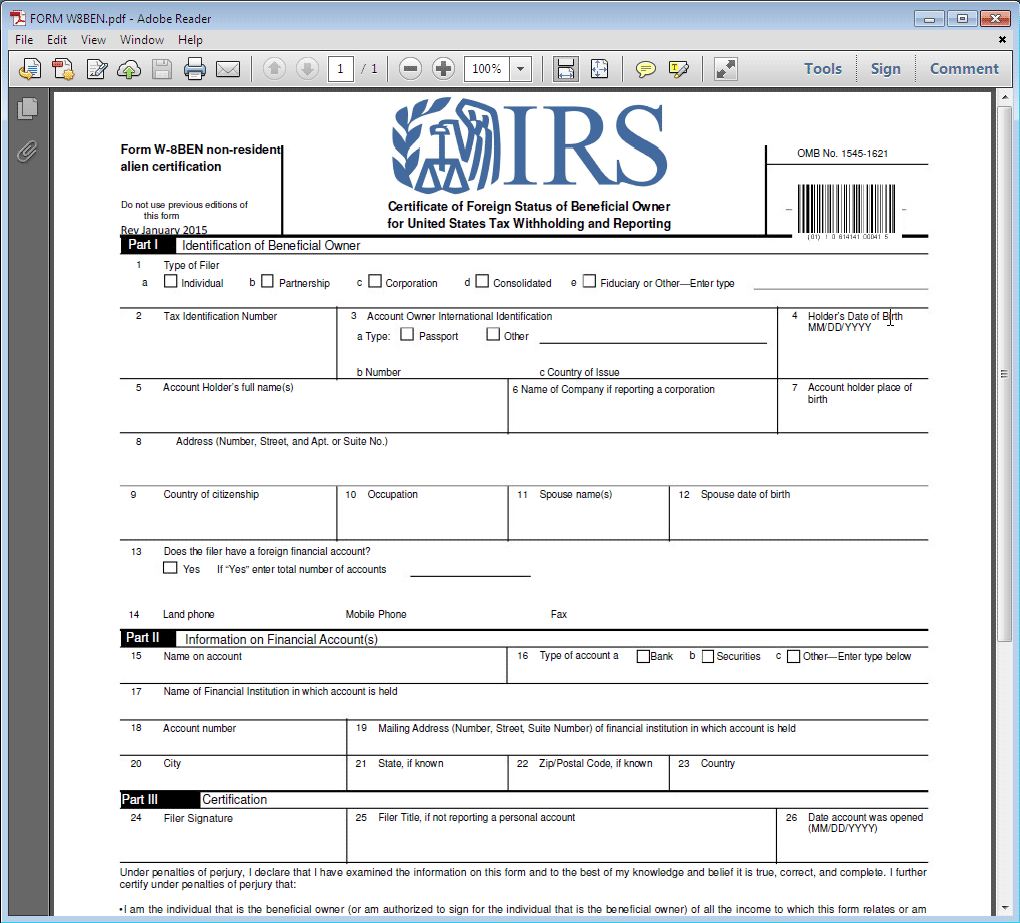
While filling a form and faxing it is normally considered a high friction activity, it’s clear that these attackers have a business and attack model that they believe lowers perceived risk to victims. By using a US toll-free number that has real costs per call, they appear more legitimate, potentially lowering engagement fears, which could increase response and justify the investment in infrastructure that is more complex and expensive than email.
To clarify for the public what the IRS will or will not do, they issued a warning, including the following statement: "The IRS won't send you an email about a bill or refund out of the blue. Don't click on one claiming to be from the IRS that takes you by surprise," said IRS Commissioner John Koskinen.
As a counter to this message, cybercriminals are also taking alternate approaches that use the name of the IRS as part of their lure: for example, sending a phishing email that claims to be from a third party and accuses the recipient of an unspecified wrong, and warns that they have alerted the US tax authority, as well as law enforcement.
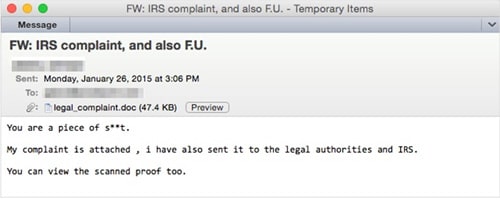
In contrast to the relatively polished phishing attempts described above, this phishing email is simple and crude, but also clever in that it attempts to exploit the recipient’s fear of legal and tax action to trick them into opening the attached Word document, which unsurprisingly includes macro-enabled malware. While many phishing campaigns attempt to use honey, so to speak, to trick the recipient, this one gambles that vinegar will trap more flies.
The large opportunity to exploit the IRS and tax season to steal funds and credentials from the general public means that bad actors and scammers are taking multiple paths to make money. We cannot understate the importance good email hygiene and knowing who you are communicating with via email, phone, or fax when it comes to this tax season.
Subscribe to the Proofpoint Blog

