The remote and hybrid work environments of our pandemic-driven “new normal” have workers relying heavily on collaboration applications and social media, both public and enterprise. These trends have opened the door even wider to phishing, malware and a whole host of other cyber threats. In response, we’re seeing both regulated and unregulated companies revamping their cybersecurity policies and practices so that they can better manage these risks.
We’ve also noticed forward-thinking companies doing something else as the work to enhance their cybersecurity measures: reviewing and improving information governance (IG) policies. They are taking a closer look at how information in the organization is being handled—from its creation to its deletion. And hopefully, as they do this, they’re looking at the following three, critical and intertwined areas:
- Shadow IT — the use of unsanctioned or unsecured company apps (more on this topic below)
- Compliance — for both enterprise collaboration apps and social media (corporate pages)
- A litigation readiness plan — this plan (informed by the two areas above) is needed because risk is increased exponentially by an unmonitored, policy-driven, corporate social media presence and the lack of ability to capture, store and preserve information across multiple channels and collaboration platforms
In this post, the first in a series about the importance of IG in the new normal, we’ll look specifically at the first area— shadow IT—and why it should be top of mind for organizations that are currently assessing and shoring up their IG plan.
Productivity issues a major driver for shadow IT expansion
Many employees forced to work from home during the COVID-19 pandemic have downloaded and installed applications and tools without IT’s approval because they needed them to do their daily tasks remotely. These collaboration apps, like Slack, Teams and Monday.com, have modular capabilities embedded, such as collaborative whiteboards, customer support, messaging, chat, and live video meeting and streaming components. These downloaded tools may or may not have been made available or certified by the company’s IT department. Most problematic are the apps not approved for internal use; in many cases, employees didn’t seek input from IT before adopting these apps because they saw IT as an inhibitor to productivity.
The hassle of internal red tape or not knowing what applications the company makes available to the workforce are often root causes for employees downloading unsanctioned applications or tools on a corporate device. Understandably, many employees find it easier to download free (or limited use) collaboration tools, online storage or utilities that help them complete their daily work tasks.
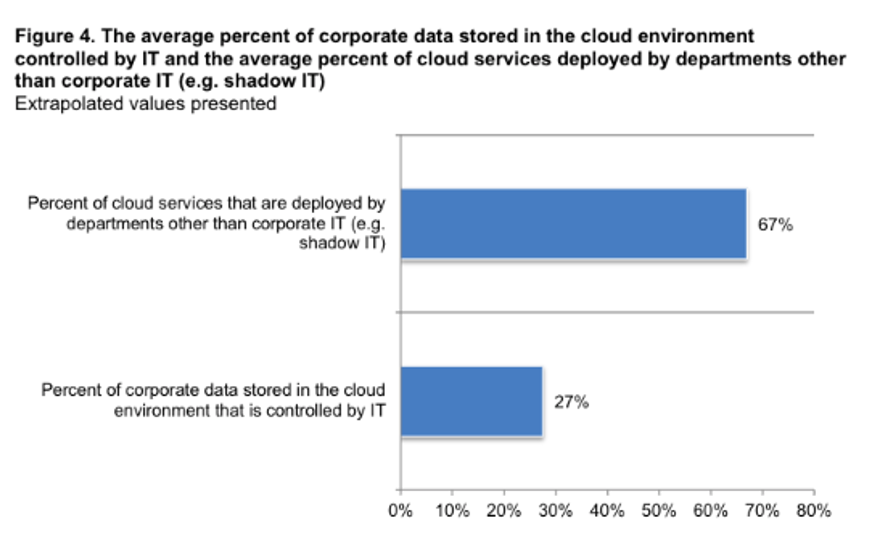
Figure 1: Very little corporate data in the cloud is controlled by IT. Survey data from, The Cost of Cloud Compromise and Shadow IT.
However, the result of this behavior is that suddenly, applications in the public cloud are populated with sensitive corporate data, like human resources (HR) information and intellectual property. And without a solid IG plan, it’s entirely possible that your company’s initial public offering or costly research and development data might now be blended in an employee’s Google Drive folder that’s also accessible to that worker’s personal contacts outside of your organization.
What your organization should do
It’s not too late for most organizations to do some damage control. The fix is prescriptive, as well as tactical. IT needs to be seen as both “a partner” and “productivity enabler” and not a gatekeeper/hindrance to employee productivity. Managers need to periodically submit IT surveys to employees in order to get a finger on the pulse of productivity tools needed. In response, IT needs to make a list of applications by tasks available internally, provide easy access to employees, as well as provide training to encourage use.
Finally, solutions like Proofpoint Content Capture makes it easy to capture, manage, and retain content from the tools your employees use to communicate. It unites and normalizes feeds across popular enterprise collaboration apps, such as Slack and Teams, as well as instant messenger social media, chats, text messaging and more.
Next up: shadow IT meets enterprise collaboration and social media
Most shadow IT apps are enterprise collaboration tools. Some may have a niche focus like customer relationship management, while others are designed for project management. The ability to capture data created and communicated within these enterprise collaboration applications is just as critical as an organization’s need to capture emails, text messages and customer interactions.
Enterprise collaboration tools and social media are closely related. Both can present the same high level of risk in terms of HR, brand reputation, regulatory governance and litigation readiness issues. In the next installment of this blog series, we’ll cover the impact social media can have on organizations that lack a layer of governance and approval. And we’ll examine key questions organizations should ask as they work to update their cybersecurity and IG policies and implement tools and/or processes to create a “corporate memory” that provides discoverable evidence with plenty of context.
For more information on content capture, head here. Also, be sure to subscribe to our blog so that you don’t miss the next post in this two-part series.

