In my previous blog, I noted that the Proofpoint Attack Index provides insight and visibility. But, so what? How do we act upon that? What can we do with this? Let’s answer those questions with some examples.
Addressing Very Attacked Persons with Security Awareness Training
The Attack Index shows who the Very Attacked Persons (VAPs) are within your organization. It will also surface which of those people are clicking on things they shouldn’t be. In either case (or especially in the case of people that are both VAPs and heavy clickers), we need to do something to help them, because they represent a heightened level of security risk to the organization.
In our demo example below, James Smith looks to be both very attacked and predisposed to clicking on links he shouldn’t be.
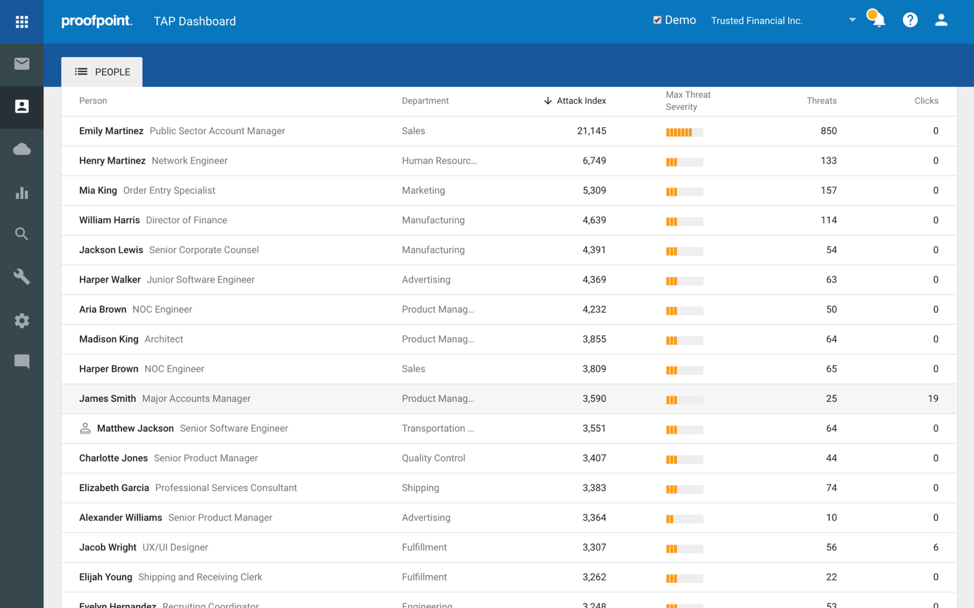
List of People Who Have Experienced Cyber Attacks
In this case, the logical solution is to apply a control that effectively adapts to the specific situation. That control is to direct Very Attacked Persons to Security Awareness Training on effective lures and what to avoid clicking on. As we implement this type of control for Very Attacked Persons and/or heavy clickers, we improve the overall resilience and security awareness of the organization.
The mechanics for this are straightforward: We can export a CSV file of VAPs from the Targeted Attack Protection (TAP) Dashboard, and import that into Proofpoint Security Awareness Training (PSAT, formerly Wombat), so that those users can benefit from training modules customized for Very Attacked People (see graphic below). And you can expect to see further automation and integration to make this even simpler and faster in the future.
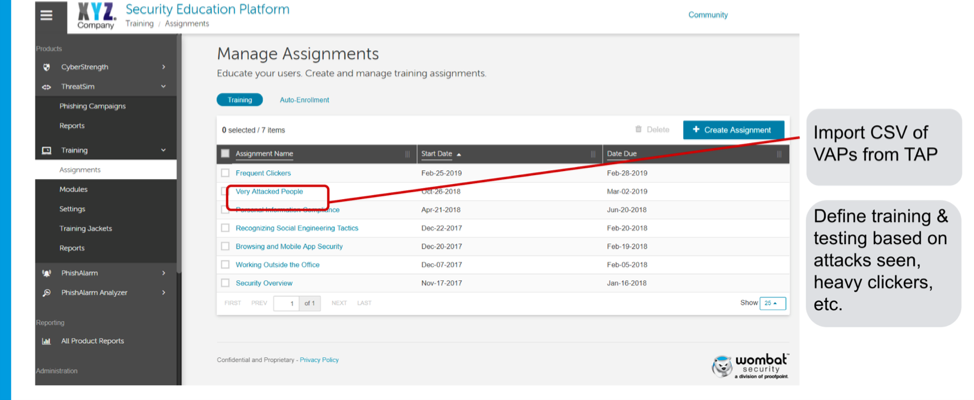
It is also worth noting that we’ve already implemented significant integration between TAP and PSAT by combining advanced threat protection capabilities with real-time phishing simulation and cybersecurity awareness/training. This moves training from a model based on what the user theoretically might need to a model where security awareness training is based on the specific threats they are actually being attacked with.
Addressing Very Attacked Lists with Browser Isolation
As we analyze our customers’ most attacked targets, we find that in addition to specific people, there are often shared email lists coming under heavy attack. Why? These are often group lists like sales @acme.com or customersupport@acme.com. These groups are made up of individuals whose very job is to read email, click on URLs, and open attachments. Could there be a more perfect target?
If you were a bad actor seeking to optimize your ROI and drive up your hit rate, these lists would seem to be a great place to focus your time and attention. To make things even more attractive to the bad guys, these lists are easily accessible, given that they are typically splashed all across the web in an effort to be more findable for customers and prospects. And they are not protected by Multi Factor Authentication.
For this scenario, the appropriate control is to put members of these lists into Browser Isolation. The user is protected, because all web activity is rendered and processed in an isolated container (of short duration) in the cloud. Consequently, no web content of any sort is run on any endpoint in the customer’s network (see diagram below). This significantly reduces exposure for these lists and the people on them.
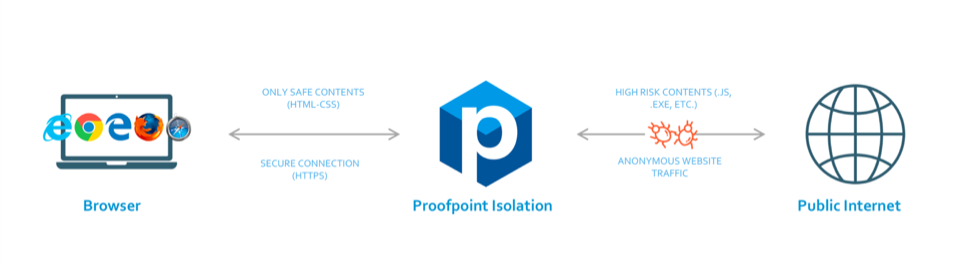
Browser Isolation Diagram
The last scenario I’ll address involves cred phish. It’s substantive enough that we’ll give it its own blog, so watch for it soon. And, if you haven’t yet, be sure to read my first one on the Proofpoint Attack Index.

