Addressing Very Cred Phished Persons with TAP SaaS Defence & CASB
Pretty much every organization across the globe is getting pummeled by Credential Phishing. This may seem like a flippant comment, but it is backed up by the data: “Credential compromise increased by more than 70% since 2017… This is of particular concern given that multiple services often sit behind a single password. In addition, reports of data loss have more than tripled since 2016.” Credential phishing is becoming the digital plague of our time. OK, maybe I’m getting a bit hyperbolic, but the problem—and struggle to address it—is real.
But I digress. The fact is that, by definition, cred phish is sent with the purpose of obtaining credentials, which are acquired to compromise an account, or more likely multiple accounts across different apps and platforms due to password reuse, etc. This compromised account is then used to establish persistence, to move laterally across the organization, to exfiltrate data, commit wire fraud, and so on. One of many examples allows the credential phishing attacker to view the victim’s emails, calendar, etc. This allows the attacker to virtually “be” the victim, assuming the victim’s identity and launching BEC attacks, etc.
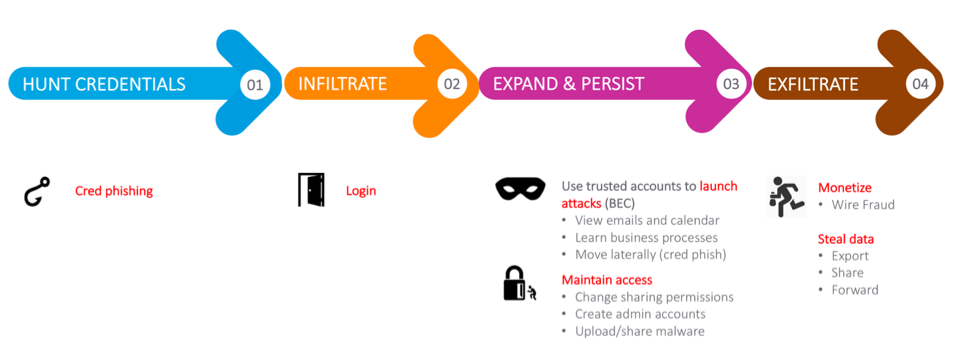
Credential Phishing Diagram
Among the most popular and treasured creds to obtain are those of O365. As users shift to the cloud, so do the cyber threats. O365 is arguably the most successful cloud app on the planet and, as such, has become perhaps the most target-rich cloud app as well. Once the attackers get credentials here, they’ll compromise the account and use it as a launching pad.
I’ve shown how to use the TAP Dashboard to quickly (within seconds) find out the Most Cred Phished people in your organization here. If you want additional visibility into compromised O365 accounts, you already have a vehicle for getting this: it’s a relatively new part of TAP called TAP SaaS Defense (TSD).
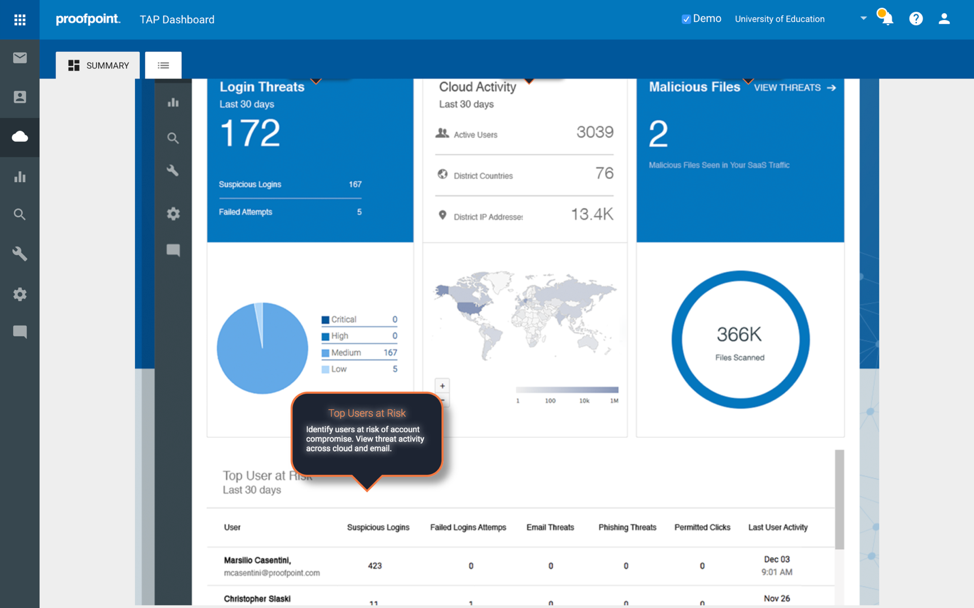
TAP Dashboard
If you have TAP, you already have TSD (and may not even know it). It will surface unusual login locations, too-fast-to-travel instances, excessive login attempts and failures, and too many connections from unknown or unusual IP addresses. In short, some of the same insight and protection that TAP provides for credential phishing threats coming in via email is extended to SaaS-based threats, specifically for O365 and Gmail. Additional apps and functionality (e.g., forensics and remediation) are available with Proofpoint’s CASB products.
Once an account is compromised, it’s easy for attackers to move laterally across the organization, based on identity deception. They appear to be legitimate users, so they exploit the trust inherent in that known internal email address. Internal Mail Defense can be used to protect against these attacks by monitoring internal emails for URL- and attachment-based threats, and automatically pulling and quarantining these messages.
In addition to moving across the organization, attackers will often exfiltrate intellectual property, W2s, employee records, and other sensitive data. The number-one vehicle for doing this is email, so to control this, it’s important to use email Data Loss Prevention (DLP). As more users (and thus more data) move to the cloud and additional apps, attackers are following. Consequently, unifying the policies by which you identify and secure sensitive data (i.e., enforce DLP) across email and cloud is becoming increasingly important. That’s why the DLP and CASB classifiers for things like GDPR, PCI, PII, and other attributes are shared. The whole topic of Unified Policy is probably worthy of another blog at some point.
Summary
In these last three blogs, we discussed how the TAP Attack Index provides insight and visibility into what actors are attacking who inside the organization, when and with which types of cybersecurity threats. This allows us to understand which people represent the most risk, through multiple different lenses. We discussed how to identify Very Attacked People and how to proactively address the risks they present by providing them with customized security awareness training. We also considered Very Attacked Lists and the need to leverage browser isolation to better safeguard list members. Finally, we discussed how those people who are Very Cred Phished may be fooled into offering up their credentials. TAP SaaS Defense monitors for the compromised accounts that frequently result from this.
Read more here:
Cyber Attacks: Visibility, Insight & Action - Part 1
Cyber Attacks: Visibility, Insight & Action - Part 2
If you have questions, please reach out to your Proofpoint Sales Engineer.

