Email fraud today usually consists of two kinds of socially engineered attacks. These attacks are either Business Email Compromise (BEC), where the attacker pretends to be you or Email Account Compromise (EAC), where the attacker becomes you—either way, you are a victim.
These attacks continue to proliferate and cause substantial financial loss for organisations of all sizes. The FBI reported losses of almost $1.7B in 2019 alone. Organisations are struggling to identify the scope of this growing problem. A key step in addressing these attacks is understanding them completely.
What’s the Difference between BEC and EAC?
Both BEC and EAC attacks target people to steal money, data or confidential information. And both are hyper-targeted. While they are intertwined there are key difference between these two attack types.
BEC attacks start with an email from an attacker who poses as someone the victim trusts. The impersonator then makes a legitimate business request. The request can seem routine, which makes it hard to detect because there's no malicious malware or malicious URLs and attachments. Common BEC tactics include domain spoofing, display-name spoofing, and lookalike domains.
With EAC attacks, on the other hand, the goal of the attacker isn’t just to impersonate you—it’s to become you. The attacker will take over a user’s email account using various tactics like password spray, phishing, and malware. Once they gain access to the account, the possibilities are endless. They have access to see how the victim interacts, what vocabulary they use, who they email regularly and can therefore craft very convincing and timely messages to trick the target.
You cannot just protect against BEC and be protected from EAC. BEC and EAC are so complex and difficult to prevent because attackers are smart and adapt to the environment, leveraging multiple tactics to get inside your organisation. They're coming through the web or your supply chain by using your business partners or even your customer's domain. These are your trusted accounts and people you interact with; that is why they can be so hard to identify and why you need to address BEC and EAC comprehensively.
To help you stay protected, here’s a quick guide on what to do (and what not to do) when it comes to BEC and EAC.
When you receive an email
Do:
- Do look carefully at the sender’s email: Accounts are often created to look similar to a trusted source
- Do review the email for grammar and spelling: Cyber criminals have improved over the years with this, but continue to look for abnormal spacing and misspellings
- Do inspect links: Attackers usually embed malicious links into their emails. You can use your mouse to hover over the hyperlink to see if there is an embedded URL
- Do be cautious about opening attachments: Attackers might be able to then get into your email account through you opening or downloading the email attachment
- Do report impersonated or suspect emails: Before giving out any sensitive information, forward the email to your security team
Don’t:
- Don’t trust the sender: Anyone can use a trusted domain to send an email
- Don’t click on attachments or links: These can contain malware giving access to your mailbox
- Don’t click on “verify your account” or “login” links in any email: Always open a new window and type in the URL or type in the official home page to log into an account
- Don’t be embarrassed: There’s a reason why the financial losses from these attacks are on the rise- they are easily disguised. Contact your security team ASAP if you do fall victim to an attack
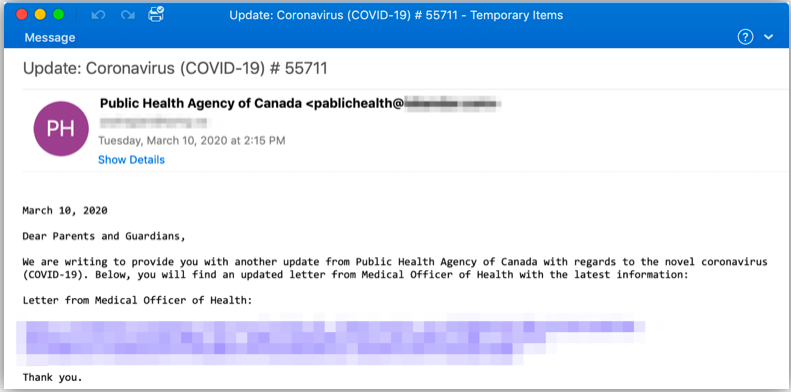
Display name spoofing and using lookalike domains are both common BEC attack tactics. In this example, you can see that the sender’s address is private instead of public. The attacker also leverages parents’ emotions about their children’s well being in order to increase the attacker’s success rate. Down below the message, there’s a URL that links to a compressed Microsoft Word document with macros. Clicking on this link could install a malware that can potentially lead to email account compromise.
Before you reply to an email
Do:
- Do use good judgement: If a trusted person has never requested sensitive information from you before, you should be sceptical
- Do validate the request via another channel: Pick up the phone to verify any requests from the trusted person
- Do open a new window to check out the website: Instead of clicking on the URL, open a browser and type it in
Don’t:
- Don’t be so quick to reply: Sometimes the attacker is just looking to verify if the email address works, you might be helping the attacker confirm that it has reached a recipient
- Don’t send passwords or sensitive information over email: Most legitimate organisations won’t request this over email, so be cautious when you do get an email asking for this
- Don’t share the passwords: You will be compromising the security of your account, and you will not know what they are doing with your access
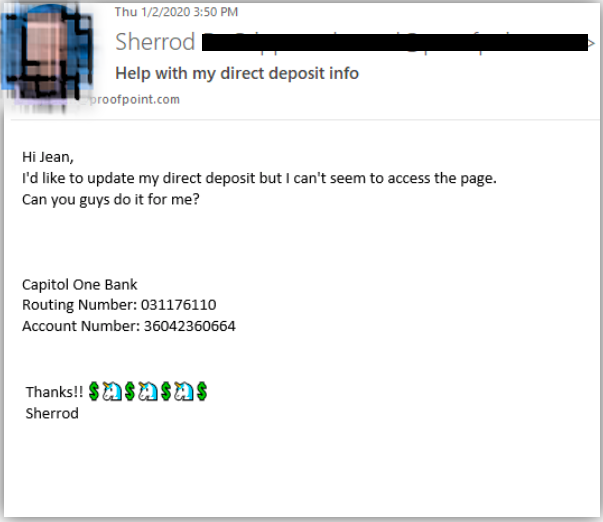
Dos and Don’ts for a Security Professional
Do:
- Do address BEC/EAC holistically: BEC and EAC are intertwined with each other. If you’re only protecting against BEC and are not addressing EAC, your organisation is exposed
- Do implement DMARC and enforce DMARC on 3rd party domains: Implementing DMARC is an effective way to protect against domain spoofing and to prevent fraudulent use of your trusted domain. DMARC also provides domain visibility that will prevent any fraudulent or brand-damaging emails from being sent using your domain
- Do block all access to suspicious websites: Attackers often use phishing technique to compromise email account. Make sure you block all access to suspicious sites that may be stealing end-users’ credentials
- Do implement adaptive controls for those at risk: First, you need to know who is at risk to your organisation. Once you have the visibility into your human attack surface, you can then implement adaptive controls for those who are vulnerable to BEC/EAC
- Do train your end-users: These attacks target people. You must educate your end-users to identity deception tactics and phishing attempts. It’s also crucial to train them on creating strong passwords to reduce risks of EAC
Don’t:
- Don’t seek for a silver bullet for BEC/EAC: It simply does not exist. BEC/EAC is a multi-faceted problem that requires a comprehensive solution encompassing multiple security controls and security awareness training. There’s no single technology that can prevent both BEC and EAC
- Don’t be reluctant to enforce DMARC at your gateway: Enforcing DMARC is an effective way to prevent domain spoofing on inbound email
- Don’t try to cobble point products together: You may end up spinning your wheels trying to make them talk to each other
- Don’t count on end-users: End-users can be click happy. Even though you’ve trained them on phishing identification, you can’t prevent them accidentally clicking on unknown URLs. They don’t think like security professionals, so continue to educate them
Proofpoint has an end-to-end solution to address this $26B problem. BEC/EAC is complex, multi-faceted, and cannot be solved with a single product or technology. We have what it takes to help you detect, block, and mitigate BEC/EAC risks by addressing all attackers’ tactics, meaning going beyond just a gateway or implementing DMARC. To solve it comprehensively, you need to address both BEC and EAC. You need to not only detect and block impostor threats from coming into your organisation, but also stop attackers from breaking in through your cloud apps, supply chain, and other security measures. For more information on the dos and don’ts around BEC and EAC, attend our on-demand webinar where we dive deeper into these

