This expensive new ransomware targets organisations with specially crafted phishing lures

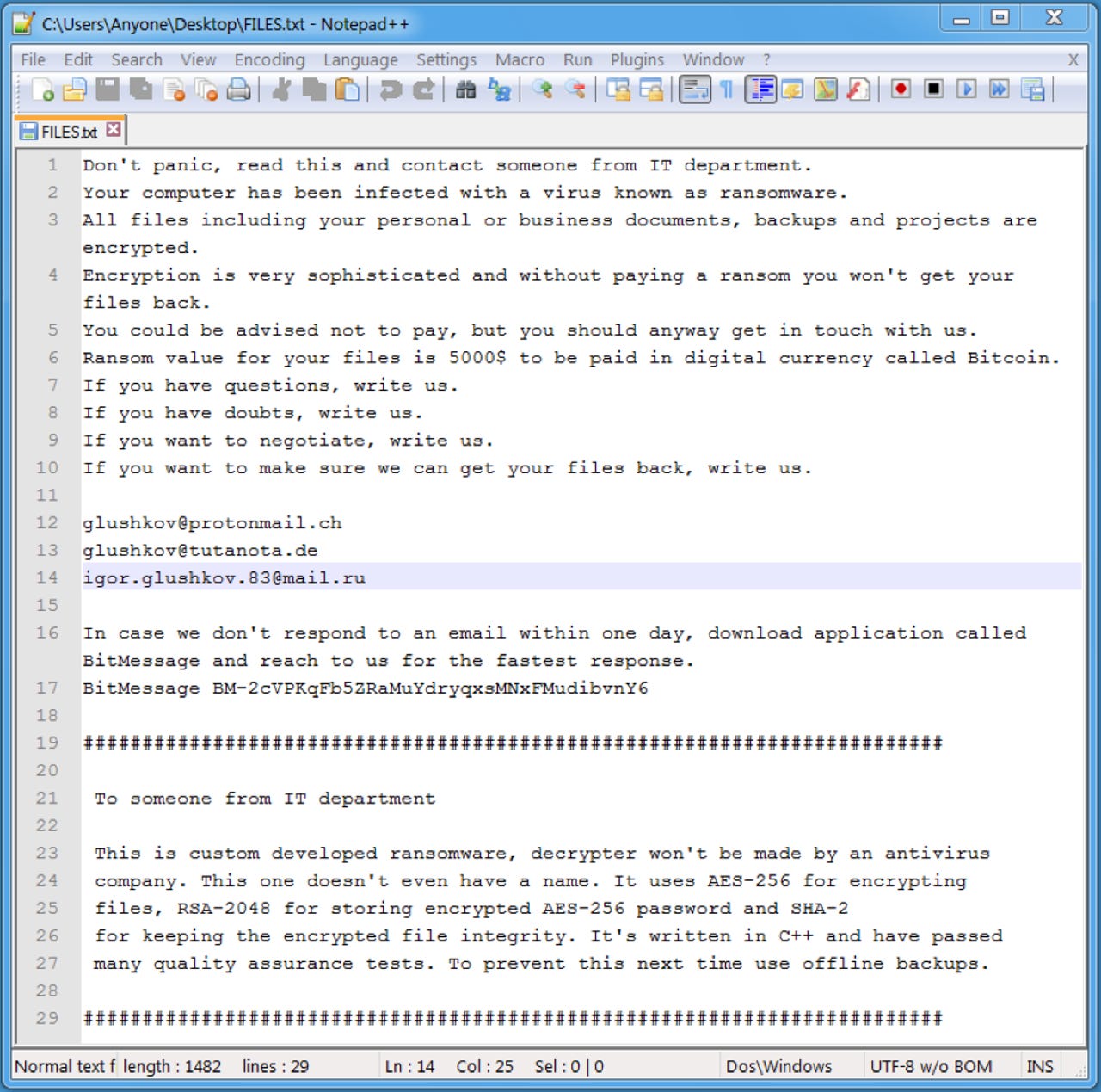
The Defray ransomware note, complete with 'advice' on how to not fall victim to future attacks.
Security
A newly discovered form of ransomware is targeting organisations with tailored phishing emails, demanding a huge ransom from unfortunate victims.
The ransomware has been dubbed 'Defray' by the researchers at Proofpoint who uncovered it. The name is based on that of the command-and-control server host in the first observed attack: 'defrayable-listings'.
It's an appropriate name for this new ransomware strain, because to 'defray' means to provide money to pay a cost or expense, and the malware demands $5,000 to be paid in bitcoin in exchange for decrypting the files. This is a much higher fee than is charged by most forms of ransomware.
The campaign is primarily targeting healthcare and education organisations in the US and UK. However, attacks have been seen in the manufacturing and technology sectors; other types of organisations -- including an aquarium -- have also been affected.
Like many ransomware attacks, the campaign uses phishing emails with a Microsoft Word attachment in order to distribute the malicious payload. But rather than using mass spamming, like other forms of ransomware, those behind Defray are customising messages for specific targets, with some campaigns consisting of only a handful of emails.
One particular campaign targeting an unnamed hospital purported to be from the director of information management and technology, and attempted to distribute ransomware via an infected Word file claiming to contain patient reports -- complete with the hospital's logo in the document.
The lure document used in a Defray attack against a hospital.
Attackers used similar tactics in an effort to infect targets in the manufacturing and technology sectors, sending emails supposedly containing quotes related to a deal, with the malicious executable once again in a Word document.
Those behind Defray even specifically customised a campaign to target a UK-based aquarium, with a lure purporting to be from a representative at one of its international locations.
The lure document used in a Defray attack against an aquarium.
These examples show that the attackers are putting time and effort into preparing their nefarious schemes, indicating that Defray is the work of a highly-organised cybercriminal operation.
See also: Ransomware: An executive guide to one of the biggest menaces on the web
It's unclear whether any of the targeted organisations actually became infected with Defray, but the ransomware will deploy and execute if the victim double-clicks on the executable file within the Word document. The victim's files are then encrypted and a ransom note is presented.
The note tells the victim to "read this and contact someone from the IT department" and details what ransomware is and what has happened. The section of the note designed to be read by IT professionals also claims that the ransomware uses AES-256 cryptography and that there's no way of getting files back without paying the $5,000 ransom.
Impudently, the note also recommends the victim to use offline back ups to "prevent this next time".
To pay the ransom, the victim is asked to contact one of three email addresses -- one Swiss, one Russian, and one German -- or to contact the attackers via BitMessage "in case we don't respond within one day".
In addition to holding files hostage, researchers warn that Defray can also disable startup recovery and delete shadow copies of files. On Windows 7, the ransomware also monitors and kills running programs with a GUI, such as the task manager and browsers, although this behaviour isn't replicated on Windows XP.
It's not known who is behind Defray, but researchers note the group is likely to be customising the lures and charging such a high ransom demand as they see it as the easiest way to make money as quickly as possible.
"Ransomware is about return on investment: making money at minimal cost. Attackers have found that highly customized messages offer better financial return on their campaigns -- something marketers have been using for decades to improve response rates," Kevin Epstein, VP of the Threat Operations Center at Proofpoint told ZDNet.
In the aftermath the global spread of WannaCry ransomware, and the subsequent Petya outbreak, cybercriminals appear to be putting a lot of effort into developing particularly vicious strains of ransomware.
Researchers recently uncovered a new strain of Spora ransomware which, in addition to extorting a ransom from victims, also steals their credentials.
Related coverage
How Bitcoin helped fuel an explosion in ransomware attacks
Phishing: Would you fall for one of these scam emails?
There's still plenty more phish in the sea, as workers can't stop clicking on scam emails. Would these ones trick you?
READ MORE ON CYBERCRIME
- Ransomware: The smart person's guide [TechRepublic]
- After WannaCry, ransomware will get worse before it gets better
- Worldwide ransomware hack hits hospitals, phone companies [CNET]
- Ransomware blamed for cyber attack which forced hospitals to cancel operations and shut down systems
- No more ransomware: How one website is stopping the crypto-locking crooks in their tracks