Multilayered protection through threat intelligence sharing
Your people are the top target for attackers, so you need a multilayered defence to protect them. Our integrations automate orchestration and response in multiple Proofpoint and CrowdStrike solutions by sharing threat intelligence (file, device and user risk) across our platforms. Together we enable security outcomes that make your security programme more effective and productive. Our out-of-the-box integrations are free to any joint Proofpoint and CrowdStrike customers.
Integrations and Benefits
Cloud and Web Security
Proofpoint cloud security products (Web Security, CASB, and Secure Access) can use CrowdStrike Falcon Identity Threat Detection to manage access to your internal, cloud and web apps before malicious actors gain access and cause damage. By combining device risk and user risk assessments across our platforms, together we reduce risk from data loss and lateral movement within internal, cloud and web applications.
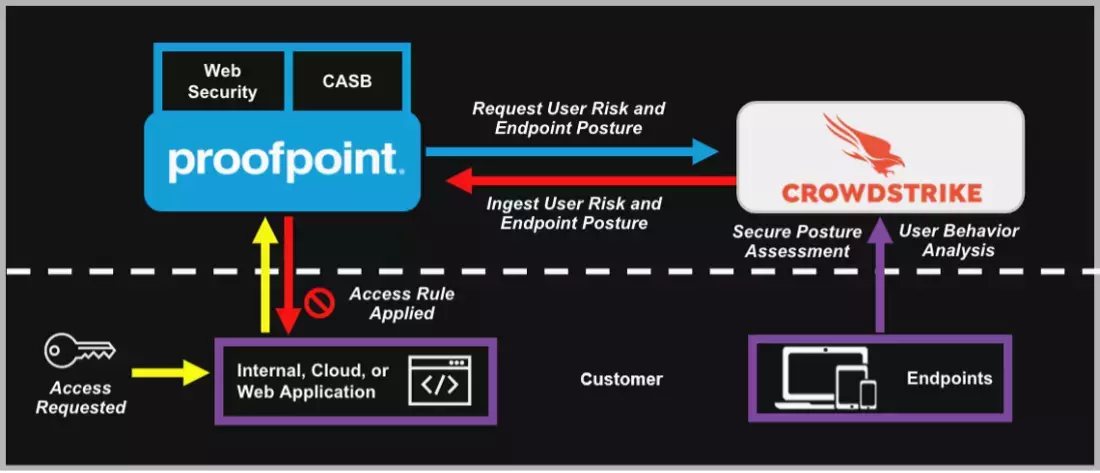
- Proofpoint checks for Endpoint Posture
- Proofpoint queries CrowdStrike for ITD (User Risk) Score
- CrowdStrike provides ITD Score
- Proofpoint applies access rules (allow, isolate or block) by incorporating Nexus People Risk Explorer, Endpoint Posture, and ITD Score
Blog Post: Strengthening Your Defences Against Cloud Threats
Learn more about Proofpoint Web Security
Pre-Delivery Protection for External Email
Proofpoint Targeted Attack Protection (TAP) uses CrowdStrike Falcon Intelligence to help block external emails with malicious attachments at the gateway. You get improved protection through our shared threat intelligence, blocking ransomware, polymorphic malware, keyloggers and zero-day threats from getting to your inbox.
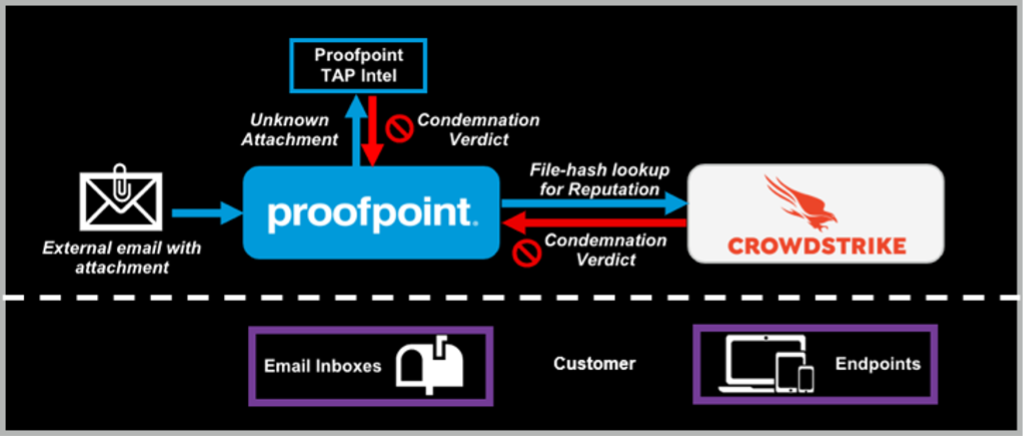
- Proofpoint TAP sandboxes unknown attachments from external emails and simultaneously queries the CrowdStrike Falcon Intelligence API for file reputation
- CrowdStrike informs TAP if it recognizes the file as malicious
- When it does, then both the message and file are condemned, blocking it from ever reaching the end user
Blog Post: Proofpoint and CrowdStrike Release Second Integration
Learn more about Targeted Attack Protection
Pre-Delivery Protection for Internal Email
Proofpoint Internal Mail Defense (IMD) uses CrowdStrike Falcon Intelligence for multilayered protection against the lateral movement of internal emails containing malicious attachments. Our combined visibility and threat detection capabilities work to better protect both your inbox and your endpoint.
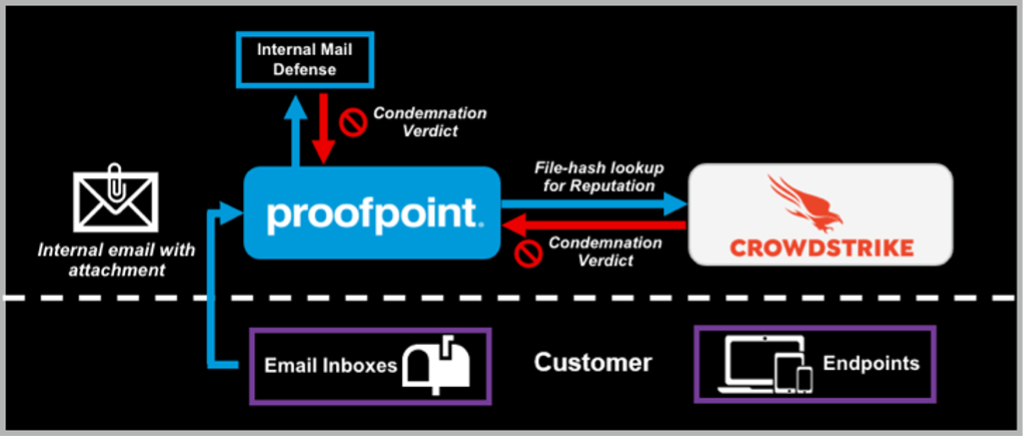
- Proofpoint Internal Mail Defense scans internal-to-internal email communications
- Proofpoint sandboxes unknown attachments from internal emails and queries the CrowdStrike Falcon Intelligence API for file reputation
- If either Proofpoint or CrowdStrike deem the attachment as malicious, Proofpoint automatically quarantines it and all related emails
Blog Post: Stopping Lateral Movement of Malware Threats
Learn more about Internal Mail Defense
Post-Delivery Protection and Automated Remediation
Proofpoint Threat Protection products automatically detect and quarantine any emails or attachments that become malicious post-delivery. Any new intelligence gained about previously unknown threats is also shared with CrowdStrike Falcon Intelligence. This shared intelligence helps to limit future attacks on your endpoints.
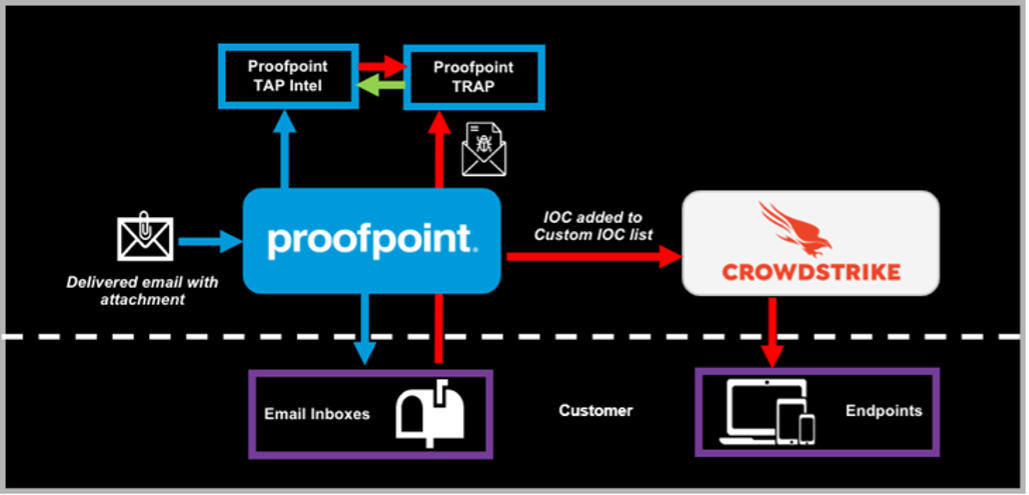
- Proofpoint detects and quarantines any messages with malicious files that have been delivered or forwarded
- If unknown to CrowdStrike Falcon Intelligence, the malicious hash is added to the CrowdStrike list of custom indicators of compromise (IOCs)
- An alert is created if the malicious content tries to execute on the device
Learn more about Automated Remediation
Post-Upload Malicious File Quarantine
Malicious files can be uploaded to the cloud by external attackers or even unknowingly by internal users. Proofpoint CASB and CrowdStrike Falcon Intelligence work together to reduce risk from these malicious files. Our combined visibility and threat detection capabilities help protect your end users and their devices.
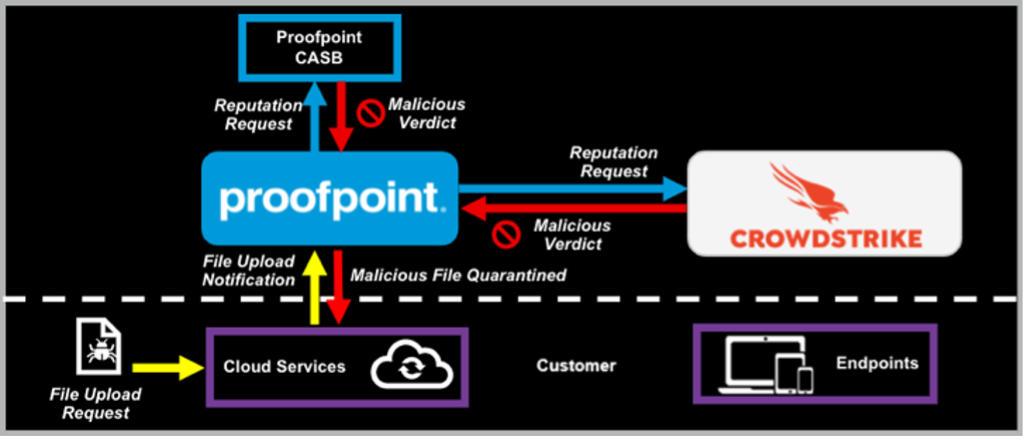
- Proofpoint CASB scans any unknown file that is uploaded to a customer’s cloud service
- While sandboxing unknown cloud files, Proofpoint queries the CrowdStrike Falcon Intelligence API for additional file reputation
- If either Proofpoint or CrowdStrike deem the file as malicious, Proofpoint automatically quarantines the file
Learn more about Proofpoint Cloud App Security Broker
Better protection for Federal Government Agencies
Proofpoint and CrowdStrike combine their extensive threat visibility and detection capabilities to provide unparallelled protection for Federal customers. Through both of our FedRAMP Certified Solutions (Proofpoint TAP and CrowdStrike Falcon Intelligence), we can provide federal agencies multi-layered security to safeguard against today’s threat landscape.
