How often do you stop to think before you give out your phone number? Depending on who’s asking, it might not ever occur to you that, when you hand it over, you’re giving away the key to a huge amount of information about yourself. Information that could be dangerous in the wrong hands.
In this article, we’re going to look at the many types of personal information that can be accessed with nothing more than a mobile phone number. Then we’ll explore how that data can be used to build “spear smishing” attacks—highly-targeted phishing that uses SMS rather than email—in record time.
Your world in your pocket
Phones are inherently personal devices. They contain a rich snapshot of our lives, from relationships to finances, to detailed information on our likes and dislikes. This depth of insight into who we are and what matters to us makes them an incredibly valuable target for cyber criminals. Effective social engineering relies on understanding the web of emotions, motivations, and cognitive biases that govern our behavior. In other words, the more a cyber criminal knows about you, the more easily they can manipulate you into downloading a malicious file, sharing sensitive information, or even transferring funds to the wrong account.
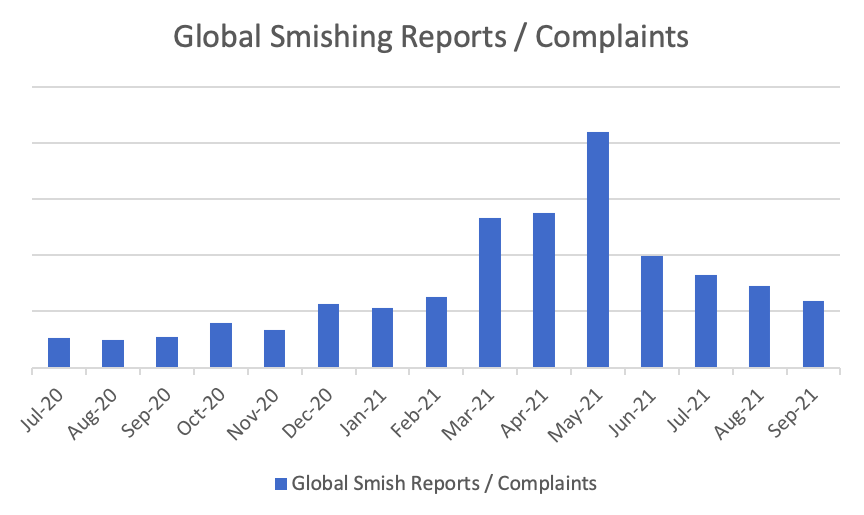
Fig 1. Smishing reports have seen significant growth in 2021
The cellphone shortcut
Most of us read mobile messages within three minutes of receiving them, because the signal to noise ratio of SMS has typically been extremely high. We haven’t been trained to treat mobile messaging with suspicion the way spam and malware have taught us to distrust email and other forms of computer messaging. So, messages received via mobile breach our mental defenses far more quickly than those we receive on other devices.
Mobile Operating System providers recognize this and have instituted various security safeguards to prevent malicious applications being installed. These system-level precautions prevent a lot of illicit app activity, even if many people still either ignore the warnings or allow themselves to be guided through the process of disabling safeguards.
But what if apps aren’t the only risk factor?
What your phone number says about you
As a primary point of connection between the various relationships, networks, and services we interact with day-to-day, our phone numbers are linked to a huge amount of personal information. And it’s just this kind of information that cyber criminals rely on when building traditional spear phishing campaigns. Historically, constructing these campaigns was a lengthy and time-consuming process.
With your number and any one of a number of common people search engines, an attacker could potentially access the following:
- Current and past addresses
- Pinpointing your socio-economic status and physical location
- Names of relatives
- Which can be spoofed to deliver malicious messages
- Home value
- Further detail on socio-economic status
- Social media accounts
- Insight into travel movements, interests, and names of friends for spoofing
- Email addresses
- Targets for malicious email delivery
- Vehicle Identification Number
- Additional socio-economic status, plus potential duplicate ownership documents
- Criminal records, including mugshots
- Information that could be used for blackmail and coercion
- Travel itineraries and information
- More detail on socio-economic status and physical location
- Legal judgements, including bankruptcy, liens, tax cases and so on.
Any single piece of information gleaned from these publicly available sources could greatly enhance the credibility of a socially engineered smishing attack, increasing the chance that you’ll fall prey to it.
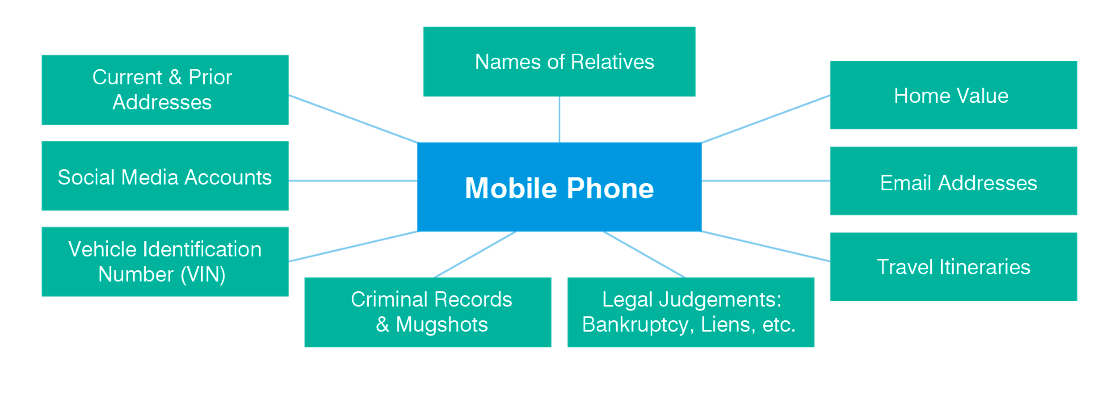
Fig 2. Matrix of connections between mobile phone numbers and searchable personal information
Mobile makes the difference
Of course, since this information is derived from public sources it would still be available in a world without mobile phones. But it would be far less accessible. Your cell phone number acts as a primary key, connecting all these disparate databases and sets of information into a single, searchable index of identity. All of this significantly reduces the time and effort cyber criminals need to devote to research, while also giving them a wider choice of victims and more time to craft their attacks.
The criminal ecosystem often mirrors the legitimate economy, and just as there are many data brokers helping businesses to understand their customers, there are criminal counterparts on the Dark Web selling even more personal information scraped from large-scale data breaches such as those experienced by LinkedIn, Yahoo and Facebook. Between details gleaned through people search and these website leaks, attackers can create the individual profiles they need to manipulate their victims.
Building a campaign
Constructing a traditional spear phishing campaign involves a few discrete steps:
- Collection: gathering information through discovery or reconnaissance
- Construction: creating message assets with fake credentials, photos, and other reassuring signals
- Contact: reaching out to targets through email, chat, SMS
Using your mobile phone number, a cyber attacker can speed through the time-consuming Collection phase. Then by using SMS rather than email, messages are delivered in a far more vulnerable medium during the Contact phase. This all adds up to a faster, more accurate, more penetrating angle of attack than traditional email-based spear phishing.
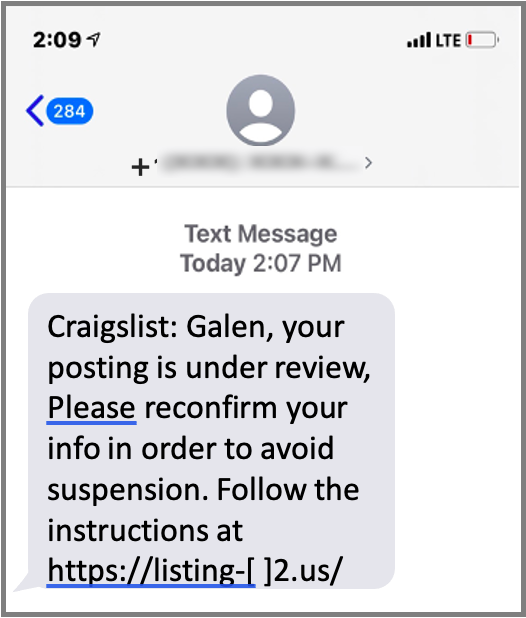
Fig 3. An example of a tailored “spear smishing” message.
Since the rise of the bring-your-own-device (BYOD) model for corporate communications, many, if not most, enterprise workers have corporate accounts on their mobile phone. This expands the risk beyond just personal information and financial loss to potential enterprise exposure.
The ubiquity and sheer utility of mobile phones has elevated them to a central position in our lives. No one is seriously suggesting that you should stop giving out your cell number as you go about your day. So, what can you do to reduce the risk that your number will leave you vulnerable to attack?
As is often the case with cybersecurity, awareness is at least half the battle. If you know just how much information a tenacious criminal can uncover about you, you’ll know just how cautious need to be about even the most convincing unexpected text or mobile chat message.
It’ll only take you three minutes to read the next message you receive on your phone—take a few more to consider if the sender is really who they say they are.
Subscribe to the Proofpoint Blog

