Google Chrome users need to be on the lookout for websites trying to trick them into downloading a font update package for their browser, as most chances are that the file is laced with malware.
This infection technique was discovered by Proofpoint researchers, who say that only Chrome users on Windows are targeted, only from specific countries, and only if they navigated to a compromised website using a specific route (referrer), such as search engine results.
Attack replaces HTML tags, destroys web pages
The technique relies on attackers compromising websites and adding their own scripts to the site's source code.
These scripts filter out the incoming traffic and load another malicious script only for Chrome users on Windows.
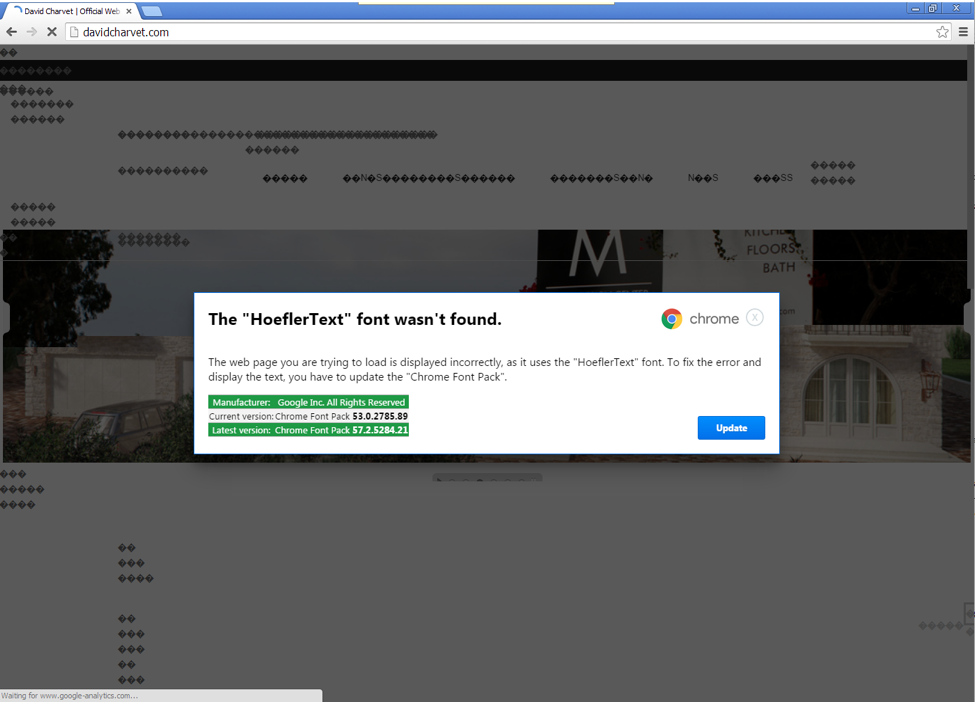
This second script will replace HTML tags with "& # 0," which ruins the site's content and displays "�" characters all over the page.
These characters are often encountered on websites and in software when there's a font and character rendering problem. As such, the crooks display a popup telling the user that a specific font wasn't found on their device, and the user will need to download and install a font package update.
To give it legitimacy, the popup is marked with Google Chrome's logo and uses classic button styles, as seen on the official Google Chrome website. A GIF showing the entire infection chain is available below:
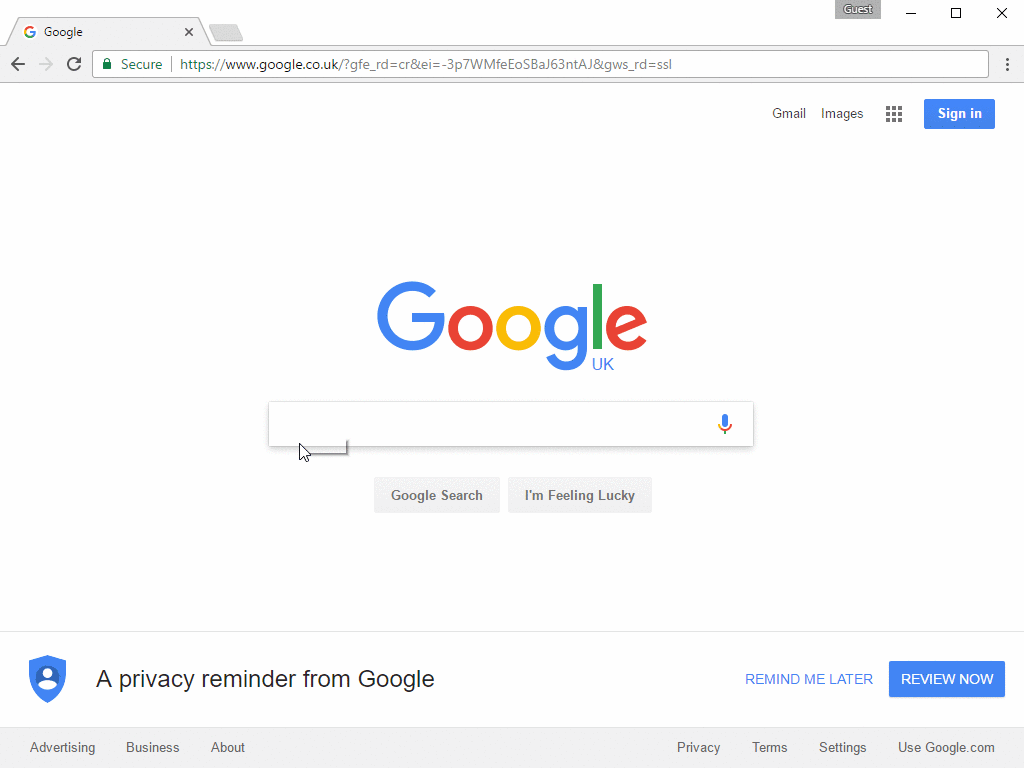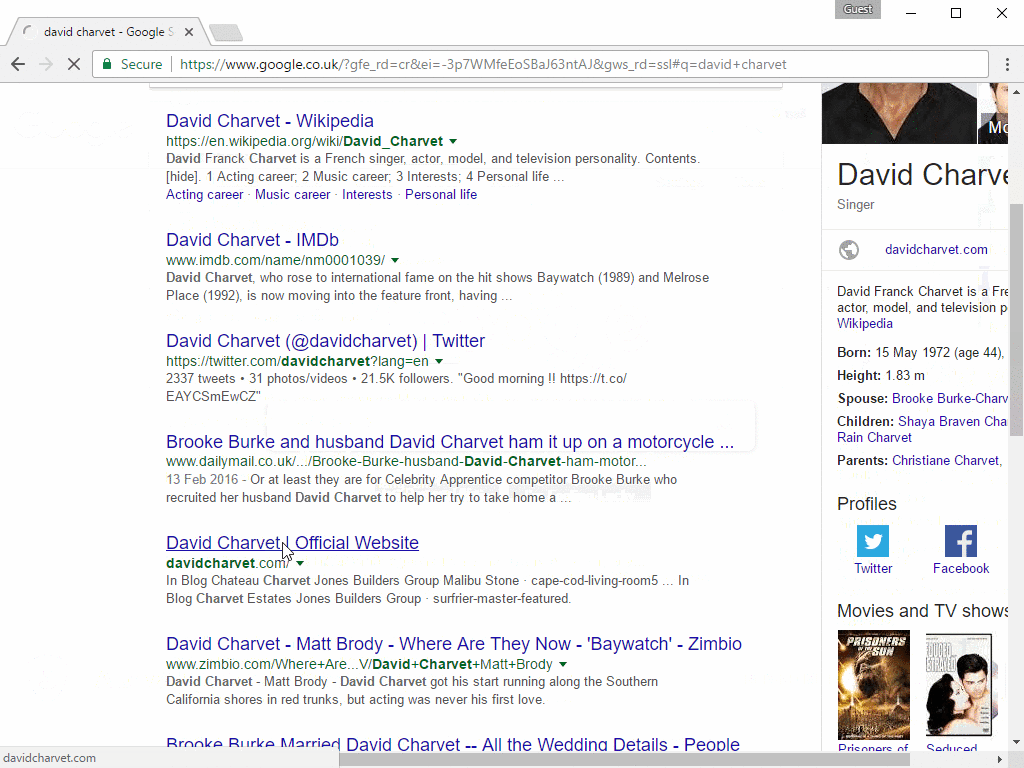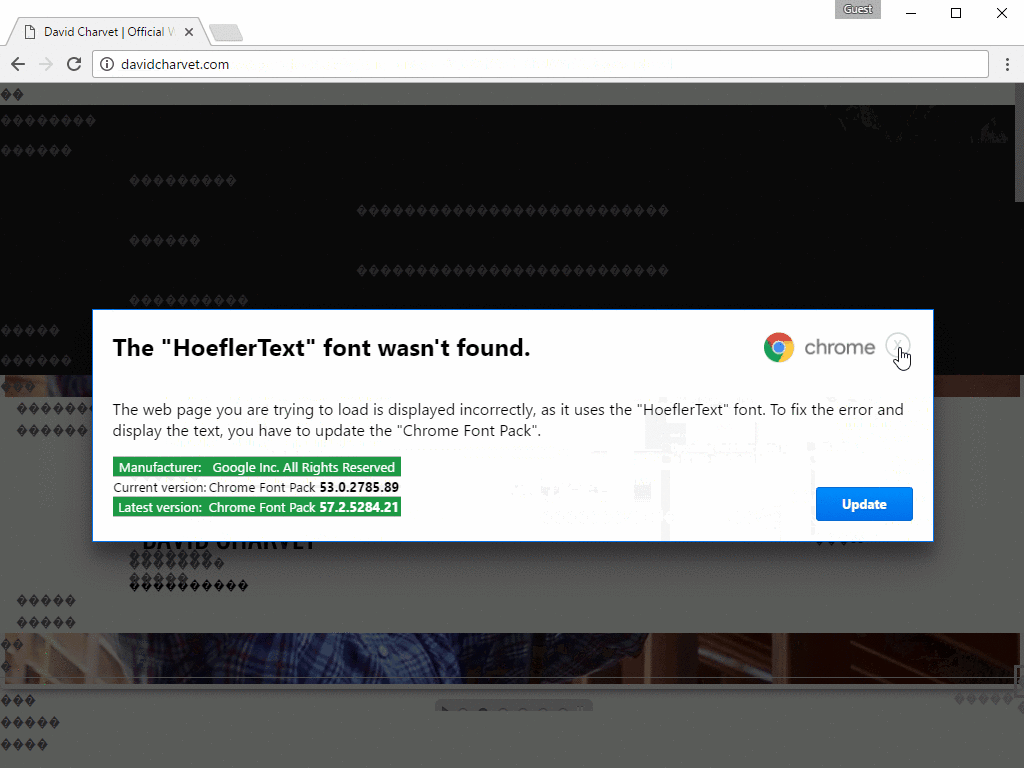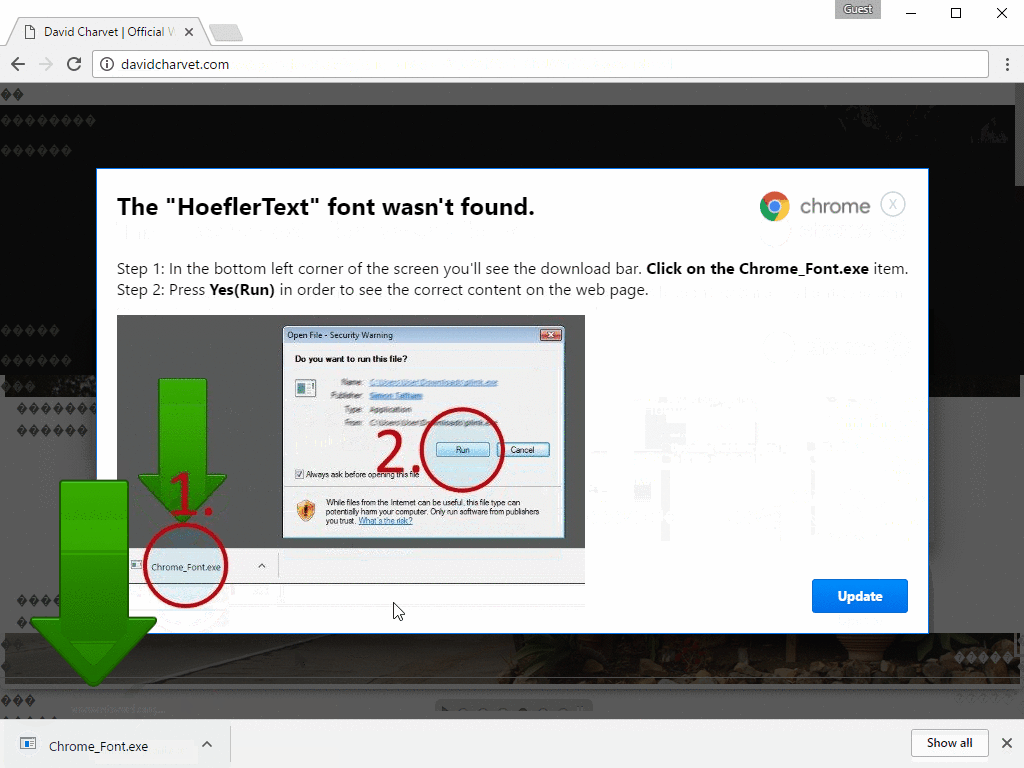
According to Proofpoint, this technique was regularly found on hacked sites, as part of the EITest infection chain. EITest is the nickname given to a malware distribution campaign, similar to pseudo-Darkleech.
The group behind EITest works by compromising a large number of websites, usually WordPress or Joomla, using known vulnerabilities.
They act by stealing small amounts of traffic (users) from these sites and redirecting them to a malicious payload.
The EITest campaign appeared in 2014, and across time, the final payload has varied greatly, hinting that the EITest group is renting out their traffic source to multiple other cyber-criminal operations.
For the vast majority of its lifespan, the EITest group has rented traffic to exploit kit operators, who used Flash, Silverlight, IE, and other vulnerabilities to install malware on the users' devices automatically, without the user ever noticing anything wrong.
Chrome users infected with Fleercivet click-fraud malware
These recent "font wasn't found" attacks on Chrome users are different because they rely on users clicking a download button, something that doesn't guarantee the same high level of successful infections that exploit kits assure.
Proofpoint says that the font update packages that users download via this technique are infected with the Fleercivet click-fraud malware, which works by navigating to preset URLs and clicking on hidden ads behind the user's back, earning crooks money.
This same malware was advertised on underground cybercrime services under the name of Simby in early 2015, and Clicool in late 2015 and in 2016.


Comments
irishblake - 7 years ago
Hey there - 2 things.
1 (on article) - how about a hint, or an inkling, on how to prevent this from a general Chrome browser user side, and perhaps even a site owner side? Having that, with this information, would probably be aMost Excellent idea.
2 ( on site) - If I sign in with social, please don't force a regular signup on folks, too. Thats - annoying....
Thanks in Advance
BattIefists - 7 years ago
Never seen this before - interesting.
Bendito999 - 7 years ago
forums.odroid.com also compromised with this sometimes, coming from Google on Windows 10 and Chrome. Look out.
pippofax - 7 years ago
I have had same problems on 22.1.2017 with a institutional website that use WordPress.
Who need file .marry to find the key can write at bpaolo@conica.it
campuscodi - 7 years ago
Have you tried identifying your ransomware using: http://id-ransomware.malwarehunterteam.com ?
daniel-light - 7 years ago
I have this on my computer window 7 , how do i get rid of this stupid encryption ? please help!
chrisxot - 7 years ago
I think this blog post have way more details about the campaign: https://blog.brillantit.com/exposing-eitest-campaign/