Those of us with a strong interest in restoring trust to the email ecosystem received some great news last month, as the US Department of Homeland Security issued a directive (BOD 18-01) mandating that federal agencies authenticate their email to eliminate spoofers’ ability to impersonate federal agencies. When the directive came out, we were naturally curious about the scale of ongoing spoofing for .gov domains, so our researchers analyzed the metadata of roughly 70 million messages seen in the Proofpoint ecosystem in October across 4,989 unique .gov parent domains (including over 55,488 fully qualified domain names, which includes subdomains), across federal, state, and local agencies.
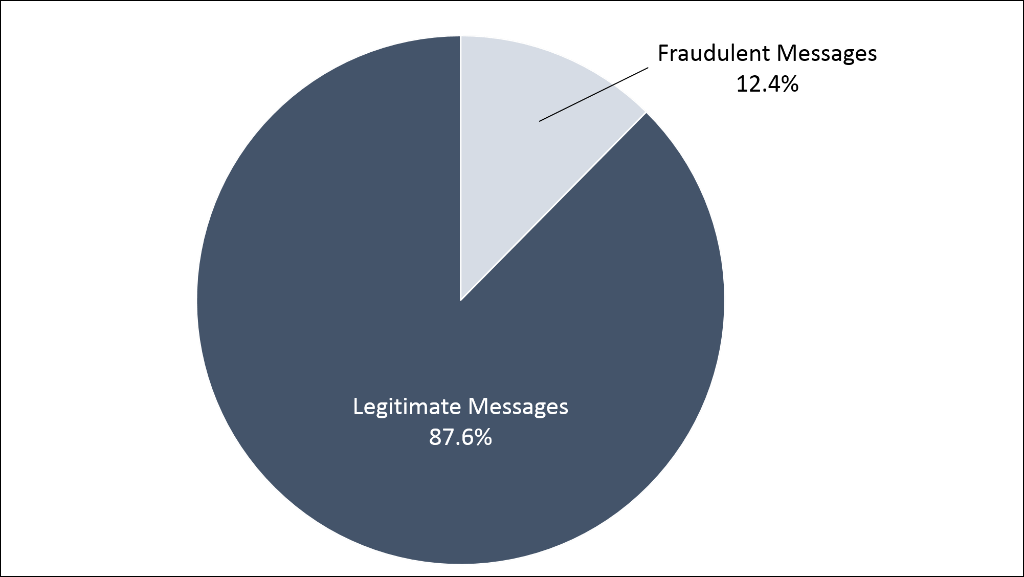
It was no surprise that .gov email spoofing is rampant. We saw over 8.5 million fraudulent messages, almost 10% of which were not even sent from a US-based IP address. In August of this year, one particular agency saw 80% of malicious emails spoofing their identity sent from Russian IPs, a country which accounted for 27% of all such malicious email since January 2016. Meanwhile, IPs in Germany were the source of 26% of fraudulent emails for this agency in the same time frame. That said, this is a much broader problem. Indeed, in October we saw .gov emails sent from 187 different foreign countries.
There are few, if any, justifiable reasons for foreign IP addresses being allowed to send an email representing itself as from a federal agency or user with a .gov email address. This made up 12.4% of all the emails sent from .gov domains, so effectively 1 out of every 8 .gov emails in October was fraudulent.
The cybercriminals used a familiar range of tactics. In 98.5% of cases, they simply spoofed the domain of a government entity – this is precisely what the DHS directive seeks to end. In total, 3,134 different domains were hijacked across 296 federal agencies and departments as well as hundreds of state and local government organizations.
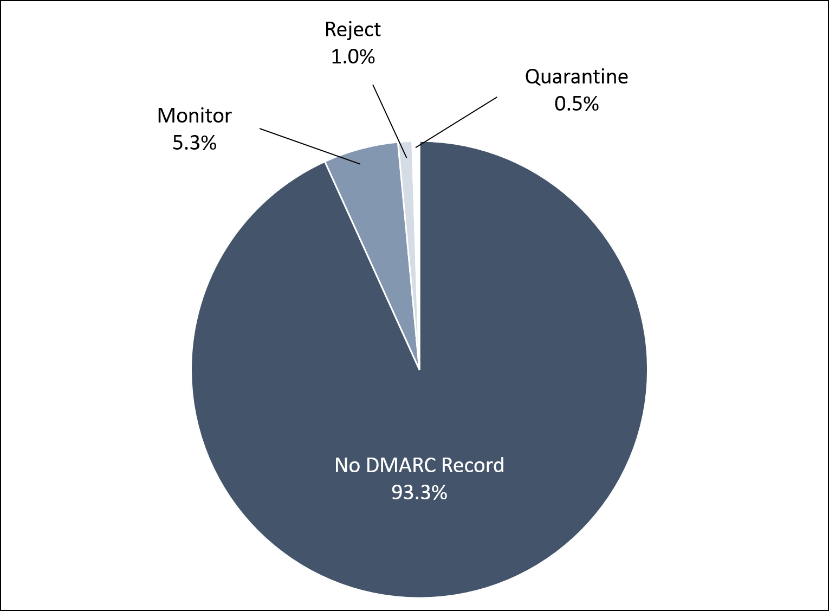
The urgency of BOD 18-01 could not be clearer, as 93.3% of the government domains that were abused had not enabled authentication of emails from their .GOV domains, even in monitoring mode. A mere 31 of the domains had a DMARC reject policy in place, which prevented those spoofed emails from being delivered to their targets by properly configured secure email gateways and service providers. In a minority (1.51%) of cases, the cybercriminal spoofed an unregistered domain. A total of 1,649 unregistered .gov domains were spoofed, highlighting the need to look for those domains as well.
Email authentication can certainly be a challenge, but it’s never been more important to prevent cybercriminals from spoofing critical organizations like government entities. To learn more about how to get started on that journey, please see our guide here:
Subscribe to the Proofpoint Blog

