Roughly 25% of all phishing emails found in a batch of 55 million analyzed emails were marked as clean by the Office 365 Exchange Online Protection (EOP) and reached the users' inboxes, while another 5.3% were whitelisted instead of getting blocked because of admin configurations.
The rest of 69.7% of phishing emails were blocked by Office 365 EOP, with 49% of them getting marked as spam and 20.7% getting tagged as "phishing."
On the whole, Avanan's 2019 Global Phish Report found that 1 out of every 99 emails is part of a phishing attack which uses malicious attachments or links as the attack vector, this being especially interesting given that phishing is seen as a more serious security threat than malware.
To obtain these results, Avanan analyzed approximately 55,5 million emails delivered to organizations with 20 to 100,000 employees using Office 365 and G Suite email platforms.

For Office 365, 546,247 e-mails out of the 52,379,886 examined were marked as being part of a phishing campaign, with 1,04% of the total being phishing messages. On the other hand, 0.5% of the 3,120,114 emails received by G Suite users were phishing mails.
The emails were scanned by Avanan after the default security checked them, allowing the company "to see not only the phishing attacks
that were caught but also those that were missed."
"Our software connects via API inside of the cloud, creating key advantages over conventional solutions to email security, which sit outside (such as
em ail gateways)," says Avanan's report. "For this reason, it can detect and analyze phishing attacks that have evaded Office 365 and Gmail security. Scanning after the default security but before the inbox, the platform catches phishing emails that bypass all other existing security layers."
According to the report, malware phishing was identified as the attack vector in 50,7% of the total of 561,947 phishing mails, followed by credential harvesting (40.9%), extortion (8%), and spearphishing (0.4%).
Avanan also unearthed very interesting info when looking into the indicators which can be used to detect phishing attacks, with 98% of emails containing a cryptowallet addresses and 35% of emails with a link to a WordPress website being part of a phishing scheme.
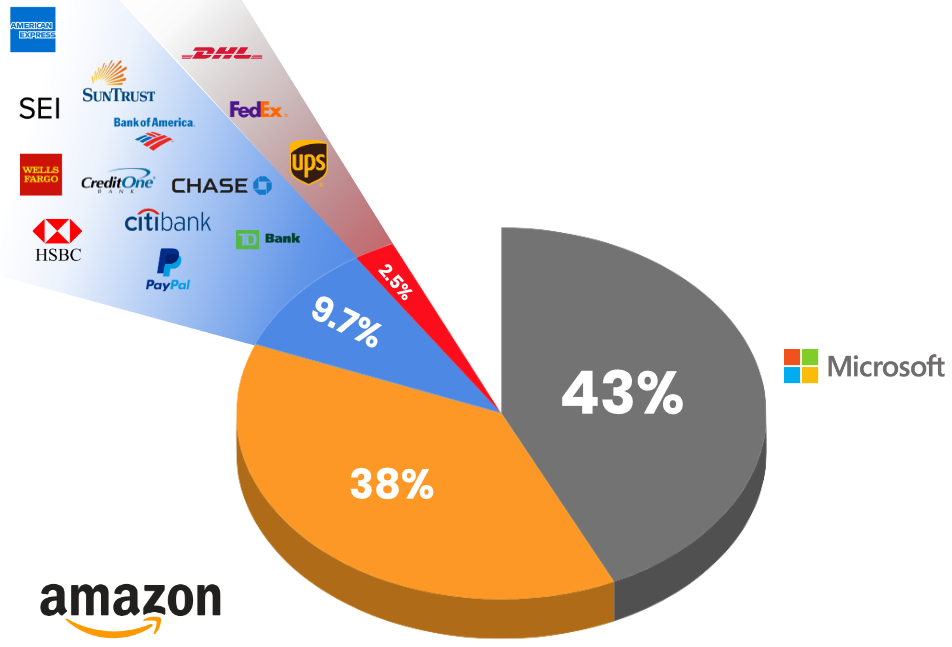
Brand impersonation is also used to camouflage phishing emails as coming from various trusted brands, with Microsoft being used in 43% of brand impersonation-powered phishing attacks and Amazon in roughly 38% of the total of observed phishing messages.
Phishing is utilized by threat actors to trick their victims into going to websites they control and designed to collect confidential information, into downloading attachments containing malware or into clicking links redirecting to malicious websites that drop malware on their computers.
"Cloud-based email, despite all of its benefits, has unfortunately launched a new era of phishing attacks," said Avanan lead security analyst Yoav Nathaniel. "The nature of the cloud provides more vectors for hackers and gives them broader access to critical data when a phishing attack is successful."
Phishing targeting payment data, credentials, and social security info
In related news, Doctor Web's researchers disclosed a novel phishing approach yesterday, with newsletter sign-up forms from the websites of various international trusted brands being used by crooks to effectively camouflage phishing e-mails as official newsletter subscription messages.
Last week, ProofPoint illustrated how phishing campaigns are actively targeting the tax season with the help of realistic-looking phishing emails coupled with malicious attachments.
As discovered by the Microsoft Office 365 Threat Research team during March, Netflix and American Express (AMEX) customers were targeted by two other phishing campaigns, with the bad actors behind targeting both credit/debit cards and social security information.
Another phishing campaign was spotted in February while attempting to steal both Google and Facebook credentials using Google Translate to camouflage itself on mobile browsers as found by Akamai's Security Intelligence Response Team (SIRT) member Larry Cashdollar.


Comments
classicevolutions - 5 years ago
Unfair table of results. The number of emails analysed should match.
rhasce - 5 years ago
HAHAHAHAHAHAHA, This is Microsoft for you, I would not be surprise, Microsoft sucks lol
JohnnyJammer - 5 years ago
Really, this is your response mate? As a O365 Admin, the end user will very rarely see any spam and you know why, because i have configured it properly. Default settings i would agree with you but 5 minutes of setting your conf level and DMARC, DNS, SPF records up and you are basically there, a few mail flow rules and redirects and bingo they are safe.
My concern is what is Avanan doing reading all them envelopes/Emails!