
An ongoing phishing campaign targeting several organizations with the help of DocuSign branded spam e-mails has been observed by Proofpoint's Threat Insight Team while abusing Amazon Web Services (AWS) to host their landing pages.
While various threat actors have been seen utilizing consumer-grade cloud storage such as Dropbox and Google Drive to host malicious content like malware payloads, phishers have also used it for other purposes like phishing kits hosting.
However, as Proofpoint found, some of the phishing actors they monitored throughout 2019 have slowly moved to "enterprise-class public cloud storage providers such as Amazon Web Services (AWS) and Microsoft Azure."
.png)
One of the phishing campaigns Proofpoint analyzed since the start of 2019 is still active and it uses spam e-mail and landing page templates featuring stolen DocuSign branding.
The phishers use nested JavaScript encoding for the landing pages hosted on Amazon S3 storage for evading detection and for hindering analysis, with the Multibyte XOR encoding technique described by Proofpoint in February 2016 being an integral part of the process.
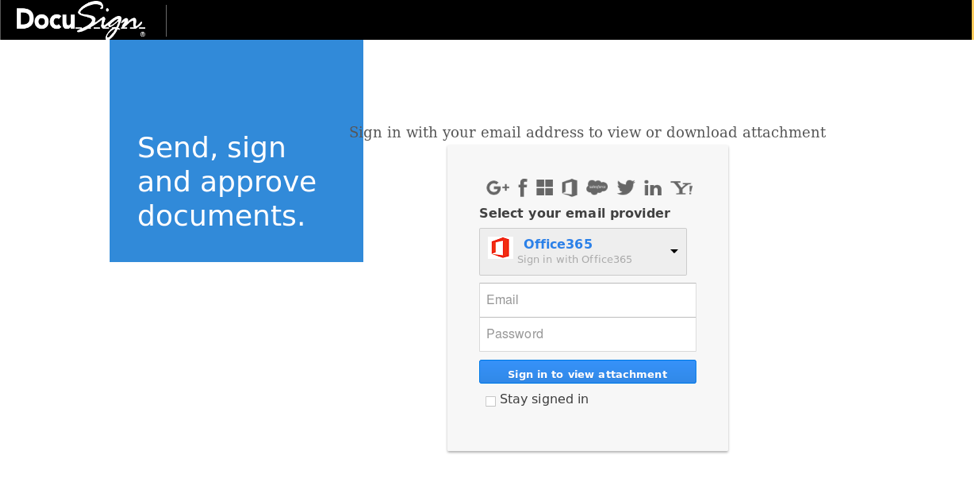
Webmail provider selection menu
The phishing kit used in this campaign features a drop-down menu to allow the targets to choose the e-mail provider they want to log into, with a "Sign in to view attachment" button being used to trick them into entering their credentials.
"After trying to get the credentials on this page, if the visitor enters their information on the DocuSign landing page, they will then be redirected to a lookalike of the webmail service they indicated, and another phishing landing will try to steal the credentials for a second time," adds Proofpoint's report.
This second webmail-themed phishing page will eventually redirect the victims to the real website of their email provider after the attackers have collected their user credentials.
"The actor engaging in this activity is not new to hosting on AWS, as we have observed it in similar low-volume campaigns throughout the year," adds Proofpoint. "All non-AWS domains have utilized 'Let’s Encrypt' TLS certificates, and most appear to be registered with Russian domain registration services."
Even though the threat actor behind this campaign used AWS to host the vast majority of their phishing kits, he has also used various other public storage services to host some parts of the landing pages.
"While Amazon itself appears to be responsive and especially vigilant in taking down abusive accounts hosting this type of material, defenders should be aware of potentially malicious content on webpages hosted on AWS S3 cloud storage," concludes Proofpoint.
Cloud storage services commonly abused by phishers
The phishing campaign observed and analyzed by Proofpoint in their report follows a larger trend of threat actors taking advantage of cloud storage to host phishing kits.
For instance, during February, Edgewave researchers found that phishing campaigns abused Microsoft's Azure Blob Storage to steal Microsoft and Outlook account credentials with the help of very convincing landing pages secured with the windows.net domain's SSL certificates to appear legitimate.
Two months later, MinervaLabs' researcher Omri Segev Moyal shared with BleepingComputer several custom Office 365 rules that can be successfully used to block phishing attacks that use Microsoft's Azure Blob Storage for landing page hosting.
In April, phishing kits were also hosted by crooks on the web-based GitHub code hosting platform, abusing the service's free repositories to deliver phishing landing pages to their targets via github.io domains.
But it's not only Microsoft's cloud services being misused by bad actors to make their phishing pages look legitimate. During early February, a campaign which attempted to steal Google and Facebook credentials utilizing Google Translate as camouflage was observed by Akamai's Security Intelligence Response Team (SIRT).
Last but not least, Cloudflare's IPFS gateway was also utilized by phishing actors to secure their scams using TLS certificates issued by Cloudflare as BleepingComputer found at the time.
Picus Blue Report 2025 is Here: 2X increase in password cracking
46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.










Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now