
Threat actors in the phishing business have adopted a new technique to obfuscate the source code for the forged page by using a custom web font to implement a substitution cipher that looks like plaintext.
When browsers render the phishing page, what users see is the fake landing page created to steal login credentials, as intended by its author.
The source code, however, reveals encoded text that makes it difficult to figure out what it does. This is typically implemented through JavaScript functions.
CSS code to do the job
Using a character substitution cipher to avoid detection is not a new tactic, and reversing the text to its original form is not a challenge for automated systems.
The novelty factor here is that the page source did not have JavaScript functions to carry out the substitution, and this was done from the CSS code for the landing page.
The threat actor used only two fonts, 'woff' and 'woff2,' both hidden via base64 encoding.
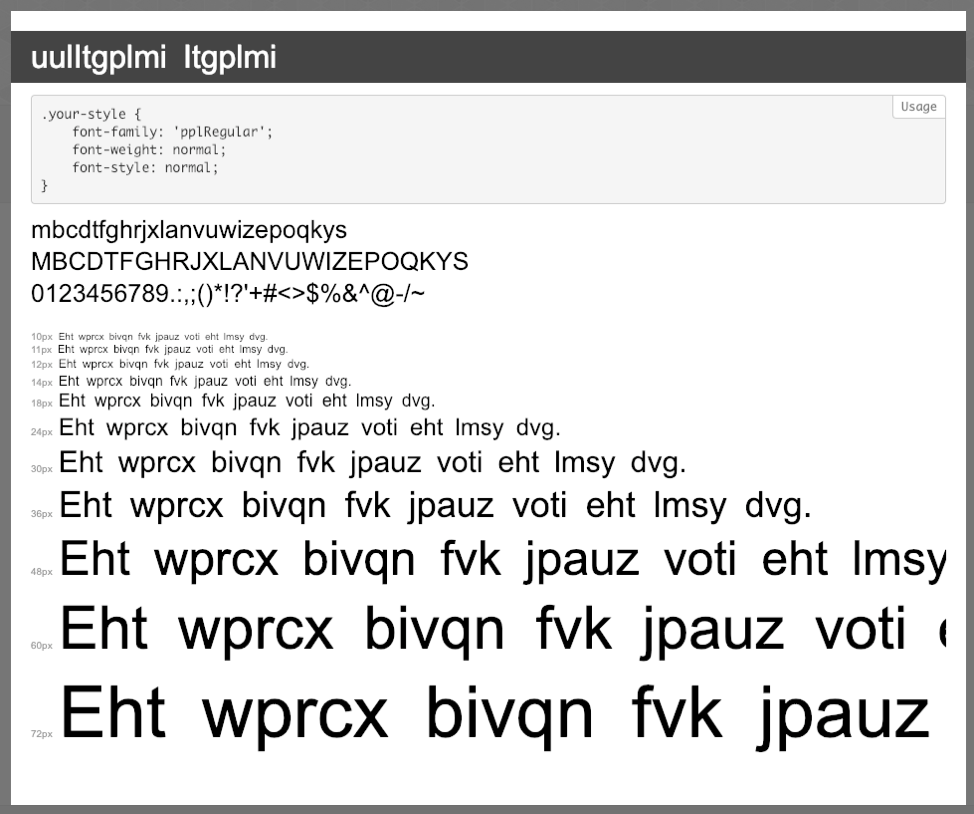
Researchers were able to determine that the phishing page has a custom web font file that enables the web browser to render the ciphertext as plaintext.
"As the Web Open Font Format (WOFF) expects the font to be in a standard alphabetical order, replacing the expected letters "abcdefghi..." with the letters to be substituted, the intended text will be shown in the browser, but will not exist on the page," Proofpoint malware analysts explain in a blog post.
To further obfuscate the phishing attempt, the threat actor used branding imagery in SVG (scalable vector graphics) format, which can be rendered through code, eliminating the need to load them from a location that stores image resources, which would help with detection.
Method used in the wild since at least mid-2018
The new evasion approach has been spotted in a phishing kit with most of its resource files dated early June 2018, but malware researchers first observed it a month earlier.
Given the evasion method used, it is possible that the malicious framework was used in the wild even earlier than this point in time.
Proofpoint experts say that the malicious kit was used in a credential harvesting scheme targeting a major retail bank in the US.
"While encoded source code and various obfuscation mechanisms have been well documented in phishing kits, this technique appears to be unique for the time being in its use of web fonts to implement the encoding," note the researchers.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now