Overview
Proofpoint researchers have been tracking the rapid development of CryptXXX since they first discovered the ransomware in April [1]. In mid-May, the first major CryptXXX update temporarily broke the decryption tool available from our colleagues at Kaspersky Labs and locked the screens of infected PCs, making it harder to access the file systems [3]. Last week, we observed the latest version of CryptXXX (Version 3.100) in the wild, which introduced additional capabilities including network share encryption. For the time being, at least, it has once again rendered the decryption tool ineffective.
This new round of updates means that even if users are able to decrypt their files, whether through an updated third-party tool or by paying the ransom, CryptXXX can still cause significant downtime by encrypting files on network shares. In this post, we also detail for the first time the StillerX module that underlies the information-stealing capabilities in CryptXXX and allows threat actors to sell credentials or launch targeted attacks.
Network Share Encryption
On May 24, Proofpoint researchers observed a new CryptXXX variant that exhibited interesting scanning activity on port 445. Port 445 is used for SMB (aka Server Message Block), and is primarily associated with Microsoft Windows Domain and Active Directory infrastructure. Infected machines were, in fact, scanning the /24 subnet of their local area network (LAN) in search of MS Windows shared drives. Further analysis demonstrated that this new version of CryptXXX was capable of finding shared resources on the network, enumerating files in every shared directory, and encrypting them one by one.
We can see how this works by examining the SMB traffic between the machine infected with CryptXXX and another machine sharing its resources over the network (Fig. 1). CryptXXX lists files by starting the search at the root of the shared drive, and descending in a breadth-first way into subsequent directories. Figure 2 shows the ransomware retrieving the list of files inside ‘\My Pictures\Sample Pictures’.
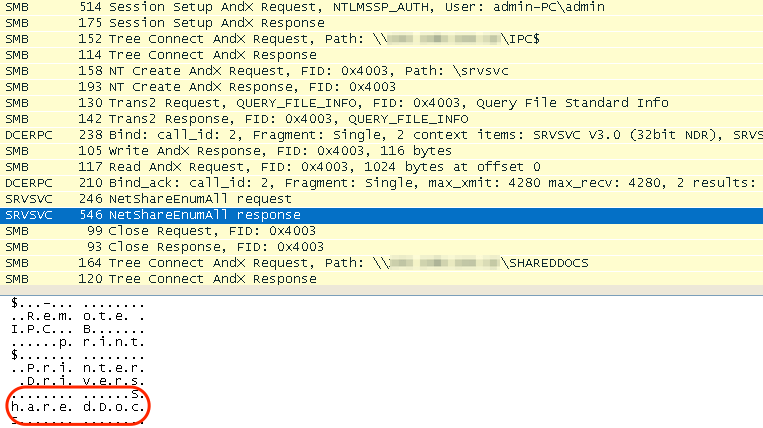
Figure 1: Network capture illustrating CryptXXX using the Inter-Process Communication (IPC) of the SMB protocol to find the shared folder “SharedDocs” on a machine on the same LAN
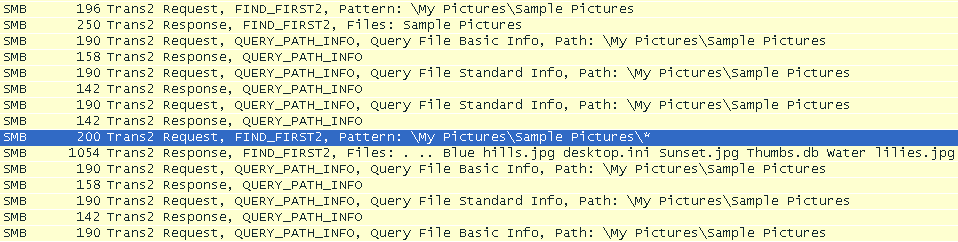
Figure 2: Network capture illustrating CryptXXX listing files in the "\My Pictures\Sample Pictures" folder
For files with extensions matching the list of encryptable files (see the complete list at the end of this post), CryptXXX will then proceed to query basic file information, read the file (Figure 3), and overwrite it with an encrypted version (Figure 4).
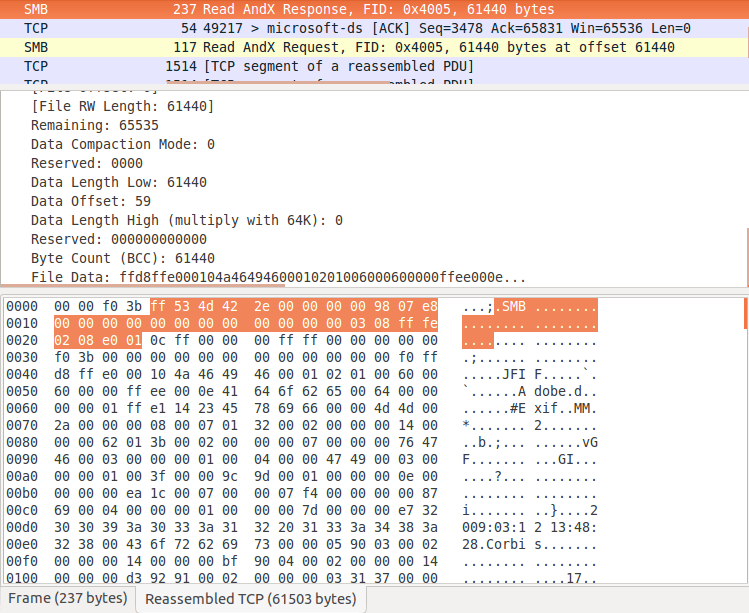
Figure 3: CryptXXX reading an image file over SMB. The JFIF header marker can be easily spotted in the clear-text payload.
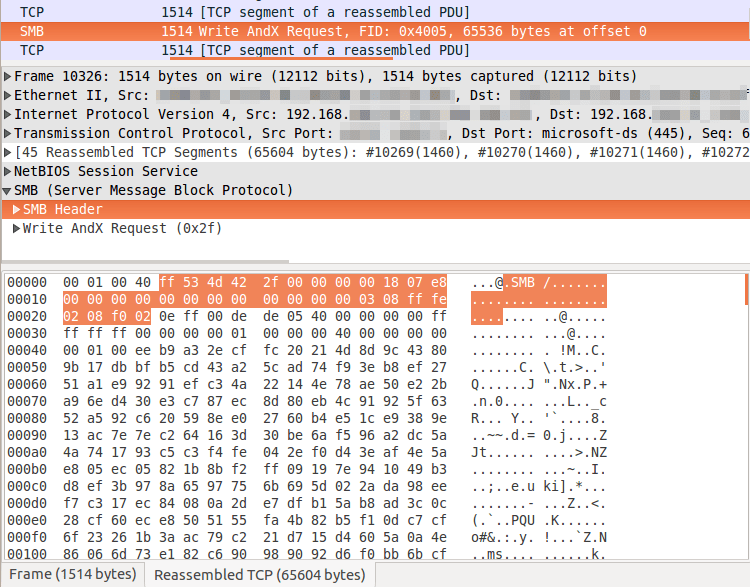
Figure 4: CryptXXX overwriting (offset=0) the same file (FID=0x4005) with its encrypted version: the payload is encrypted and no clear-text image information is visible.
Once the file is overwritten, version 3.100 of CryptXXX renames the encrypted file by appending the filename with the .cryp1 extension. It is worth noting that previous versions of CryptXXX used the .crypt extension. Once the file is renamed, the malware searches the current file path for the presence of the recovery note (the file containing the ransom message). This activity is shown in Figure 5.
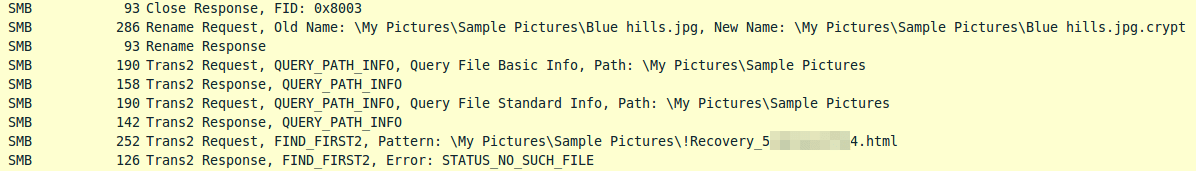
Figure 5: Addition of the .crypt extension and search for the presence of a recovery note in the current directory.
If, as in the case shown above, the recovery note is not found in the current directory, CryptXXX will proceed to upload a new ransom note to the shared directory (Figure 6). Note that this check happens for every encrypted file, as opposed to for every visited directory as one would expect. This means that, even if unnecessary, in a directory with 1000 files to encrypt, CryptXXX will search 1000 times for the presence of a recovery note.
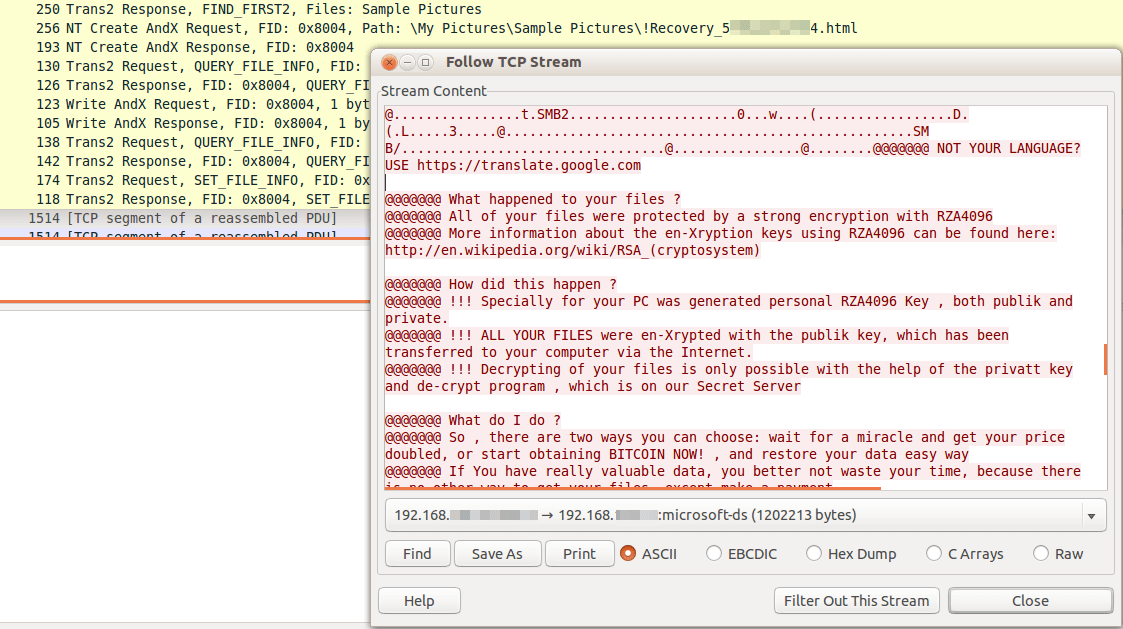
Figure 6: Upload of the ransom note to the shared directory where a file has just been encrypted
Decryption Tool
As noted in previous blogs, our colleagues at Kaspersky Labs developed a decryption tool for files encrypted by CryptXXX Versions 1 and 2 [4]. However, this tool does not work for files encrypted with the latest version of the ransomware, as acknowledged by Kaspersky.
As of the writing of this blog, the Kaspersky "RannohDecryptor" was not yet updated to accept files with the “.crypt1” extension and does not do anything when given one as input. If we manually rename the extension to the old .crypt format, the tool throws an error.
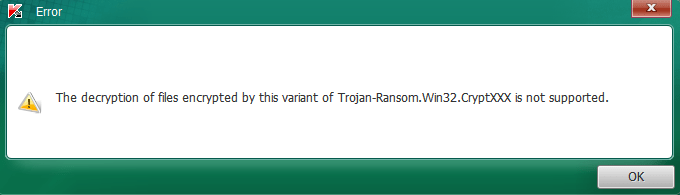
Figure 7: No decryption support for the latest version implemented yet.
Although Kaspersky Labs were able to release an effective decryption tool quickly due to underlying similarities between CryptXXX and the older Rannoh ransomware, organizations and end users should not count on the presence of such a tool. Even when possible, decrypting individual files is time-consuming and scales poorly, especially as CryptXXX begins encrypting many more files across network shares. Similarly, as described below, the information stealing capabilities built into CryptXXX render organizations vulnerable even if they can recover critical files.
StillerX
In order to further monetize the infections, CryptXXX downloads a DLL which acts as a credential stealing module. Internally referenced as "stiller.dll", "stillerx.dll" and "stillerzzz.dll", this DLL works as a plugin, but can also be used as a standalone stealer. The stealer, like the ransomware, is written in Delphi, and uses the object-oriented capabilities offered by the language. Its relatively large size on disk (around 1.2mb) is due to the static linking of several third party libraries such as DCPcrypt used for retrieving and decrypting locally stored credentials.
StillerX appears to be fully-featured and targets the credentials of a wide range of applications from poker software to Cisco VPN credentials. The malware makes extensive use of inheritance and “abstract” classes. Child classes inherit from the abstract classes based on the type of targeted programs (for example, TModule_ICQ2003 inherits from TModule_IM_Abstract). Figure 8 below shows a selection of such classes.
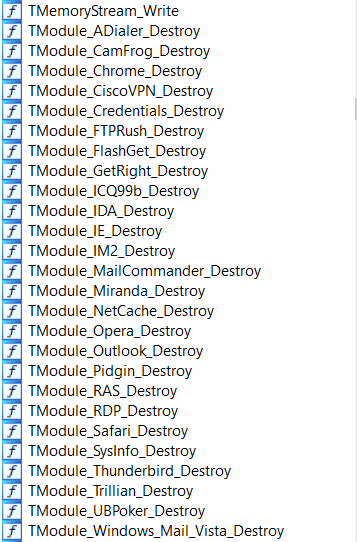
Figure 8: Sampling of class names implemented by the malware
The following is a partial list of targeted data:
- Browser data (history, cookies, stored credentials)
- Dialer credentials
- Download managers credentials
- Email credentials
- FTP credentials
- IM credentials
- Poker software credentials
- Proxy credentials
- Remote administration software credentials
- VPN credentials
- WNetEnum Cached Passwords
- Microsoft Credential Manager data
While the stealer is always deployed by CryptXXX, it is possible that it could be used as a standalone tool (and it is likely that this same malware was distributed in Bedep campaigns between December and March). Alongside the credential grabbing functions, we found unused routines handling system fingerprinting and data exfiltration. The “sysinfo” routine does not seem to be used because this task is carried out by the ransomware itself, but it would make sense in case of a standalone utilization. The “sysinfo” routine collects basic information about the host, such as the username, running processes, operating system details, Windows product ID key, and uptime of the computer. This information could be potentially used to spot fake data fed to the malware by sandboxes. Figure 9 illustrates the data formatting. Data exfiltration is performed using the same communication protocol on port 443.
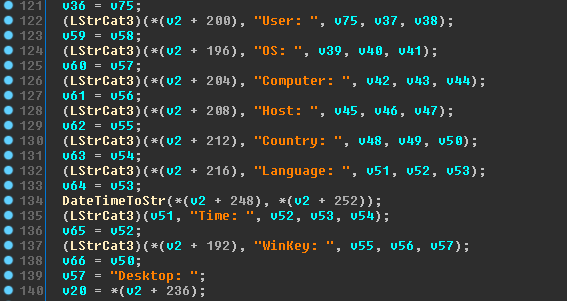
Figure 9: Code snippet showing information collected by the stealer.
New Payment Portal
With the emergence of Version 3.100 on or around May 26, the payment portal received several cosmetic updates as mentioned in [2].
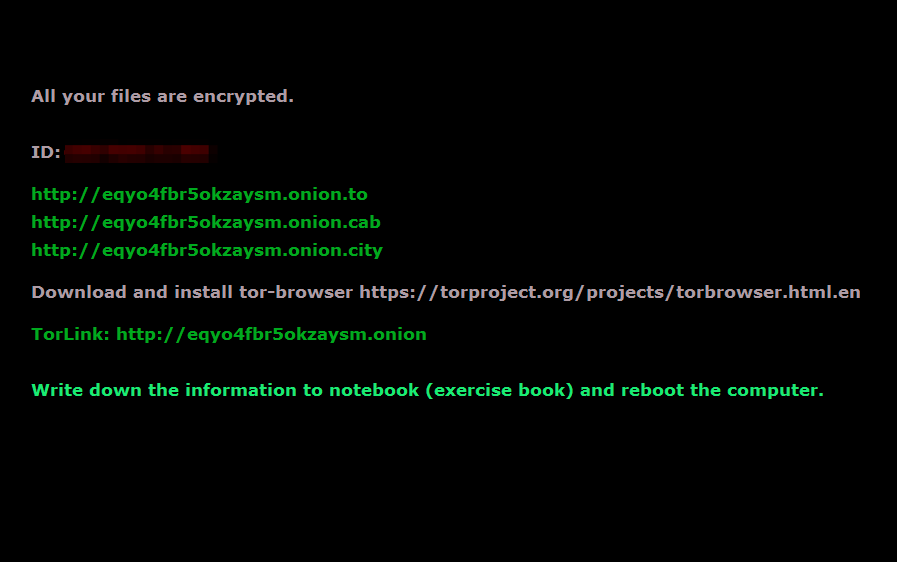
Figure 10: Updated lock screen now looks much simpler. Rebooting the computer gets rid of the lock screen but the user is able to read the ransom message notes left throughout the filesystem.
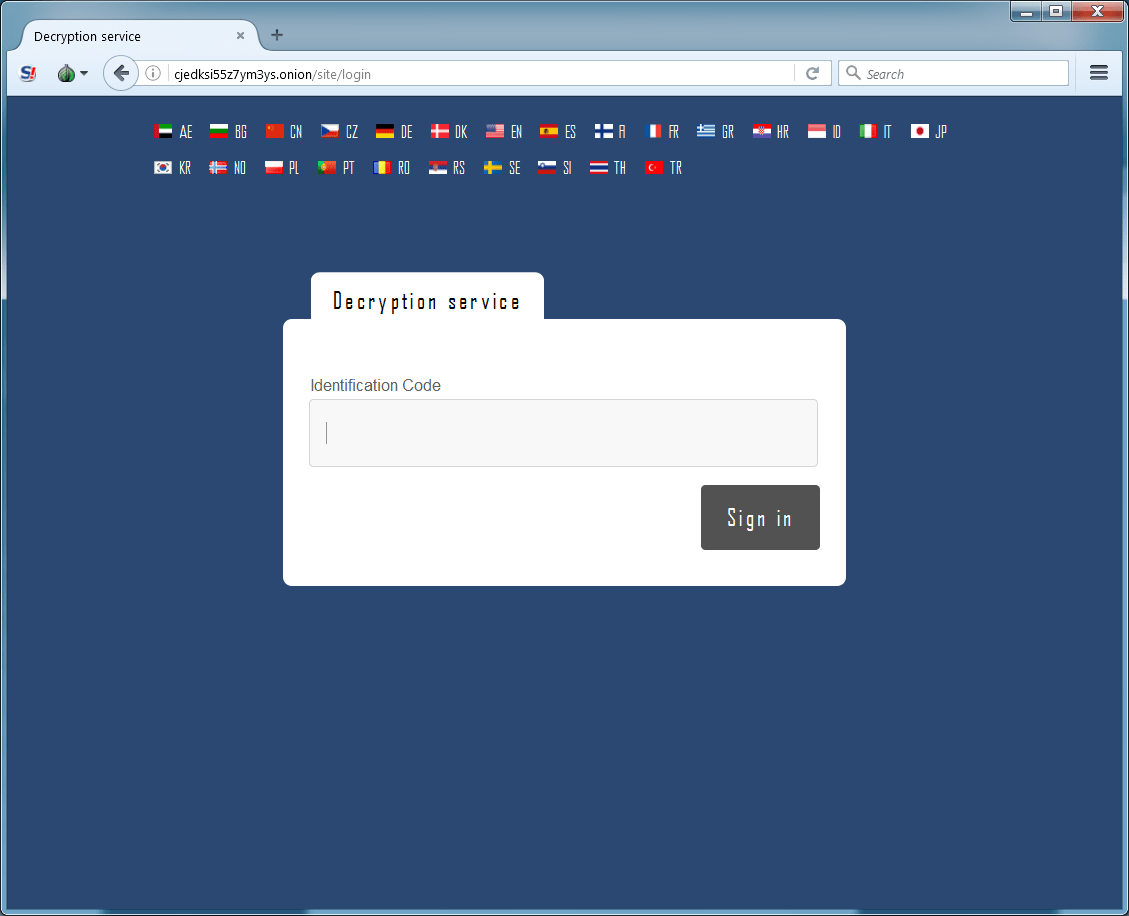
Figure 11: Home page of the payment portal hosted on an onion site, before the user enters their Identification Code
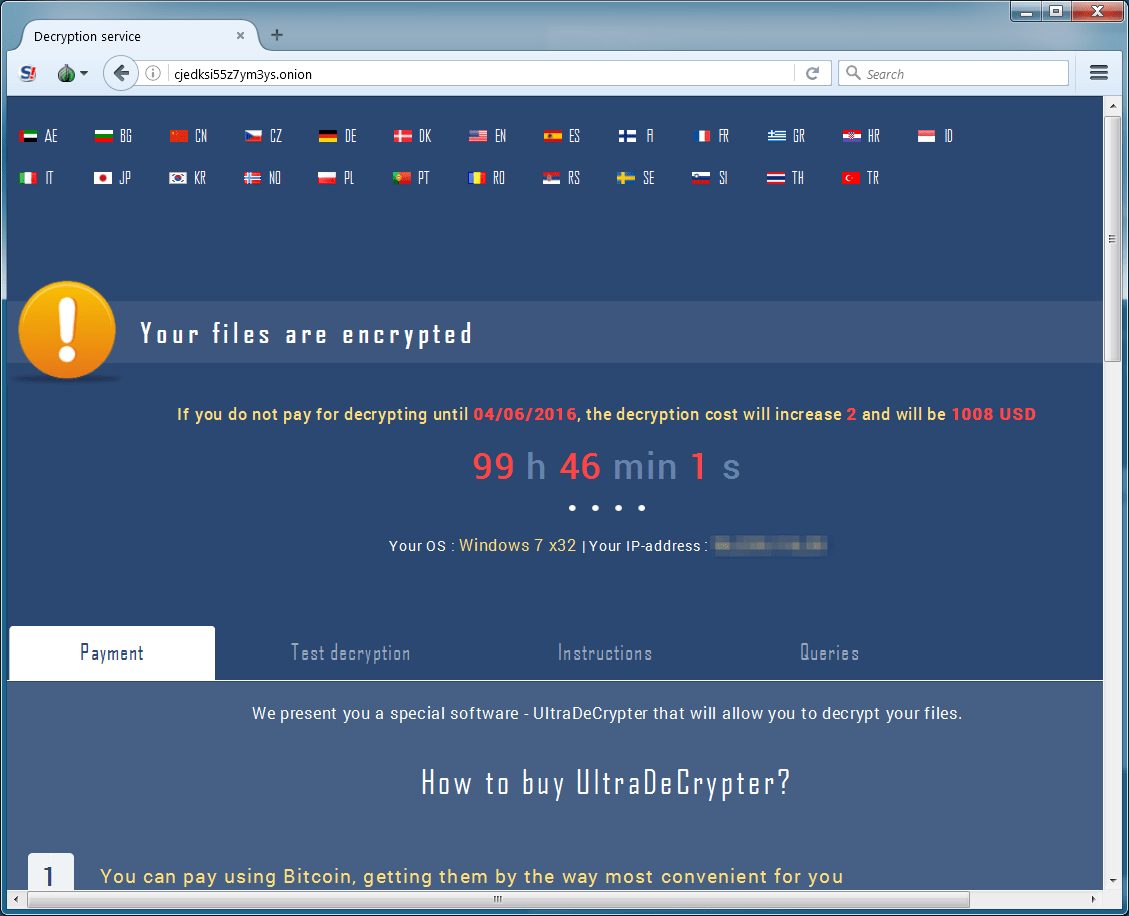
Figure 12: After entering their Identification Code, the user is allowed into the portal and has the option to pay in order to download the “UltraDeCrypter”
The versioning history for CryptXXX as observed in Proofpoint data is as follows:
- 1.001 on April 16th
- 2.000 on April 29th
- 2.006 on May 9th
- 2.007 on May 11th
- 3.000 on May 16th
- 3.002 on May 24th
- 3.100 on May 26th
Conclusion
CryptXXX has become quite widespread, especially with a number of TeslaCrypt actors shifting operations to CryptXXX recently [5]. At the same time, the actors behind CryptXXX have continued to rapidly refine the ransomware with updates to encryption, scanning for network shares, cosmetic updates, and updates to lock screen behavior. Because CryptXXX also includes robust information-stealing capabilities, multilayered network and endpoint protection are also critical to prevent data exfiltration in case of infection. CryptXXX updates have appeared very quickly over the last month and, without an available decryption tool, users and organizations must focus on detection and prevention.
References
- https://www.proofpoint.com/us/threat-insight/post/cryptxxx-new-ransomware-actors-behind-reveton-dropping-angler
- http://malware-traffic-analysis.net/2016/05/26/index.html
- https://www.proofpoint.com/us/threat-insight/post/cryptxxx2-ransomware-authors-strike-back-against-free-decryption-tool
- https://support.kaspersky.com/viruses/disinfection/8547?_ga=1.239751559.581761610.1462815600#block1
- https://threatpost.com/master-decryption-key-released-for-teslacrypt-ransomware/118179/
Indicators of Compromise (IOC)
|
IOC |
IOC Type |
Description |
|
7e6ef093a00b60cc4d487725b1b02103a94b5a9299f5a752d48510e9180e2f88 |
SHA256 |
StillerX sample (2016-04-29) |
|
011ff7879fbc4a51fd5acea6ef8a0cc7ee7afda35452063b627efe6cfb7c23de |
SHA256 |
StillerX sample (2016-06-01) |
|
36b96a2a476449f8a8653b04d4d5f506409d110235eafc60613207aba762d62c |
SHA256 |
CryptXXX sample (2016-05-28) |
|
139c9a4f3d8c2b244408644a78be6fdac353cc173727b47cb087e5b9fff10863 |
SHA256 |
CryptXXX sample (2016-05-31) |
|
85.25.194.116 |
IP address |
CryptXXX C&C (communication is non-SSL TCP on port 443) |
Select ET Signatures that would fire on such traffic:
2819805 || ETPRO TROJAN CryptXXX CnC Beacon
2022840 || ET TROJAN Possible CryptXXX Ransomware Renaming Encrypted File SMB v2
2820097 || ETPRO TROJAN CryptXXX 2.06 Checkin
File Types Encrypted by CryptXXX 3.100
.3DM .3DS .3G2 .3GP .4DB .4DL .4MP .A3D .ABM .ABS .ABW .ACCDB .ACT .ADN .ADP .AES .AF2 .AF3 .AFT .AFX .AGIF .AGP .AHD .AIC .AIF .AIM .ALBM .ALF .ANI .ANS .APD .APK .APM .APNG .APP .APS .APT .APX .ARC .ART .ARW .ASC .ASE .ASF .ASK .ASM .ASP .ASPX .ASW .ASX .ASY .ATY .AVI .AWDB .AWP .AWT .AWW .AZZ .BAD .BAY .BBS .BDB .BDP .BDR .BEAN .BIB .BM2 .BMP .BMX .BNA .BND .BOC .BOK .BRD .BRK .BRN .BRT .BSS .BTD .BTI .BTR .BZ2 .C4D .CAL .CALS .CAN .CD5 .CDB .CDC .CDG .CDMM .CDMT .CDR .CDR3 .CDR4 .CDR6 .CDT .CER .CFG .CFM .CFU .CGI .CGM .CIMG .CIN .CIT .CKP .CLASS .CLKW .CMA .CMD .CMX .CNM .CNV .COLZ .CPC .CPD .CPG .CPP .CPS .CPT .CPX .CRD .CRT .CRWL .CRYPT .CSR .CSS .CSV .CSY .CUE .CV5 .CVG .CVI .CVS .CVX .CWT .CXF .CYI .DAD .DAF .DB3 .DBF .DBK .DBT .DBV .DBX .DCA .DCB .DCH .DCS .DCT .DCU .DCX .DDL .DDOC .DDS .DED .DF1 .DGN .DGS .DHS .DIB .DIF .DIP .DIZ .DJV .DJVU .DM3 .DMI .DMO .DNC .DNE .DOC .DOCB .DOCM .DOCX .DOCZ .DOT .DOTM .DOTX .DP1 .DPP .DPX .DQY .DRW .DRZ .DSK .DSN .DSV .DT2 .DTA .DTD .DTSX .DTW .DVI .DVL .DWG .DXB .DXF .DXL .ECO .ECW .ECX .EDB .EFD .EGC .EIO .EIP .EIT .EMD .EMF .EML .EMLX .EPF .EPP .EPS .EPSF .EQL .ERF .ERR .ETF .ETX .EUC .EXR .FAL .FAQ .FAX .FB2 .FB3 .FBL .FBX .FCD .FCF .FDB .FDF .FDR .FDS .FDT .FDX .FDXT .FES .FFT .FH10 .FH11 .FH3 .FH4 .FH5 .FH6 .FH7 .FH8 .FIC .FID .FIF .FIG .FIL .FLA .FLI .FLR .FLV .FM5 .FMV .FODT .FOL .FP3 .FP4 .FP5 .FP7 .FPOS .FPT .FPX .FRM .FRT .FT10 .FT11 .FT7 .FT8 .FT9 .FTN .FWDN .FXC .FXG .FZB .FZV .GADGET .GBK .GBR .GCDP .GDB .GDOC .GED .GEM .GEO .GFB .GGR .GIF .GIH .GIM .GIO .GLOX .GPD .GPG .GPN .GPX .GRO .GROB .GRS .GSD .GTHR .GTP .GWI .HBK .HDB .HDP .HDR .HHT .HIS .HPG .HPGL .HPI .HPL .HTC .HTM .HTML .HWP .I3D .IBD .IBOOKS .ICN .ICON .IDC .IDEA .IDX .IFF .IGT .IGX .IHX .IIL .IIQ .IMD .INDD .INFO .INI .INI0 .INI4 .INI8 .INID .INIH .INIL .INIP .INIT .INIX .INK .IPF .IPX .ITDB .ITW .IWI .J2C .J2K .JAR .JAS .JAVA .JB2 .JBMP .JBR .JFIF .JIA .JIS .JKS .JNG .JOE .JP1 .JP2 .JPE .JPEG .JPG .JPG2 .JPS .JPX .JRTF .JSP .JTX .JWL .JXR .KDB .KDBX .KDC .KDI .KDK .KES .KEY .KIC .KLG .KML .KMZ .KNT .KON .KPG .KWD .LAY .LAY6 .LBM .LBT .LDF .LGC .LIS .LIT .LJP .LMK .LNT .LP2 .LRC .LST .LTR .LTX .LUA .LUE .LUF .LWO .LWP .LWS .LYT .LYX .M3D .M3U .M4A .M4V .MAC .MAN .MAP .MAQ .MAT .MAX .MBM .MBOX .MDB .MDF .MDN .MDT .MEF .MELL .MFD .MFT .MGCB .MGMT .MGMX .MID .MIN .MKV .MMAT .MML .MNG .MNR .MNT .MOBI .MOS .MOV .MP3 .MP4 .MPA .MPF .MPG .MPO .MRG .MRXS .MS11 .MSG .MSI .MT9 .MUD .MWB .MWP .MXL .MYD .MYI .MYL .NCR .NCT .NDF .NEF .NFO .NJX .NLM .NOTE .NOW .NRW .NS2 .NS3 .NS4 .NSF .NV2 .NYF .NZB .OBJ .OC3 .OC4 .OC5 .OCE .OCI .OCR .ODB .ODG .ODM .ODO .ODP .ODS .ODT .OFL .OFT .OMF .OPLC .OQY .ORA .ORF .ORT .ORX .OTA .OTG .OTI .OTP .OTS .OTT .OVP .OVR .OWC .OWG .OYX .OZB .OZJ .OZT .P12 .P7S .P96 .P97 .PAGES .PAL .PAN .PANO .PAP .PAQ .PAS .PBM .PC1 .PC2 .PC3 .PCD .PCS .PCT .PCX .PDB .PDD .PDF .PDM .PDN .PDS .PDT .PE4 .PEF .PEM .PFF .PFI .PFS .PFV .PFX .PGF .PGM .PHM .PHP .PI1 .PI2 .PI3 .PIC .PICT .PIF .PIX .PJPG .PJT .PLT .PLUGIN .PMG .PNG .PNI .PNM .PNTG .PNZ .POP .POT .POTM .POTX .PP4 .PP5 .PPAM .PPM .PPS .PPSM .PPSX .PPT .PPTM .PPTX .PRF .PRIV .PRIVATE .PRT .PRW .PSD .PSDX .PSE .PSID .PSP .PSPIMAGE .PSW .PTG .PTH .PTX .PVJ .PVM .PVR .PWA .PWI .PWR .PXR .PZ3 .PZA .PZP .PZS .QCOW2 .QDL .QMG .QPX .QRY .QVD .RAD .RAR .RAS .RAW .RCTD .RCU .RDB .RDDS .RDL .RFT .RGB .RGF .RIB .RIC .RIFF .RIS .RIX .RLE .RLI .RNG .RPD .RPF .RPT .RRI .RSB .RSD .RSR .RSS .RST .RTD .RTF .RTX .RUN .RW2 .RWL .RZK .RZN .S2MV .S3M .SAF .SAI .SAM .SAVE .SBF .SCAD .SCC .SCH .SCI .SCM .SCT .SCV .SCW .SDB .SDF .SDM .SDOC .SDW .SEP .SFC .SFW .SGM .SIG .SITX .SK1 .SK2 .SKM .SLA .SLD .SLDX .SLK .SLN .SLS .SMF .SMIL .SMS .SOB .SPA .SPE .SPH .SPJ .SPP .SPQ .SPR .SQB .SQL .SQLITE3 .SQLITEDB .SR2 .SRT .SRW .SSA .SSK .STC .STD .STE .STI .STM .STN .STP .STR .STW .STY .SUB .SUMO .SVA .SVF .SVG .SVGZ .SWF .SXC .SXD .SXG .SXI .SXM .SXW .T2B .TAB .TAR .TB0 .TBK .TBN .TCX .TDF .TDT .TEX .TEXT .TFC .TG4 .TGA .TGZ .THM .THP .TIF .TIFF .TJP .TLB .TLC .TM2 .TMD .TMP .TMV .TMX .TNE .TPC .TPI .TRM .TVJ .TXT .U3D .U3I .UDB .UFO .UFR .UGA .UNX .UOF .UOP .UOT .UPD .USR .UTF8 .UTXT .V12 .VBR .VBS .VCF .VCT .VCXPROJ .VDA .VDB .VDI .VEC .VFF .VMDK .VML .VMX .VNT .VOB .VPD .VPE .VRML .VRP .VSD .VSDM .VSDX .VSM .VST .VSTX .VUE .WAV .WB1 .WBC .WBD .WBK .WBM .WBMP .WBZ .WCF .WDB .WDP .WEBP .WGZ .WIRE .WKS .WMA .WMDB .WMF .WMV .WP4 .WP5 .WP6 .WP7 .WPA .WPD .WPE .WPG .WPL .WPS .WPT .WPW .WRI .WSC .WSD .WSF .WSH .WTX .WVL .X3D .X3F .XAR .XCODEPROJ .XDB .XDL .XHTM .XHTML .XLC .XLD .XLF .XLGC .XLM .XLR .XLS .XLSB .XLSM .XLSX .XLT .XLTM .XLTX .XLW .XML .XPM .XPS .XWP .XY3 .XYP .XYW .YAL .YBK .YML .YSP .YUV .Z3D .ZABW .ZDB .ZDC .ZIF .ZIP .ZIPX .ZZ3
Subscribe to the Proofpoint Blog

