Imagine this scenario: Someone in your organization—let’s call him Fred—is in an airport traveling for business when his colleague, Amy, calls to ask him for information. She will be presenting a performance analysis to the company’s executives and needs clarification about a report Fred developed.
Amy mentions the file’s name, and Fred uses his personal mobile device to download the report from a corporate cloud application so he can look at it and answer Amy’s questions. At the end of this interaction, sensitive corporate information, usually stored in a secure corporate IT-approved location, is now also stored on Fred’s personal mobile device.
The application access and file download may not necessarily be a policy violation event—but what if Fred’s mobile phone is infected with malware, or the device is stolen? The security and IT teams may not have control over the apps installed on Fred’s phone if it’s an unmanaged device.
A simple act of collaboration between employees has now placed sensitive data at risk. And a potential data leakage event like this can result in the loss of customer trust, litigation, and punitive action from regulatory authorities.
The last point of control for cloud data loss prevention
In the chain of events described above that can lead to data theft, there is one critical point where the data can be protected. It was when the user, Fred, was logging in from his personal device to an approved software-as-a-service (SaaS) application. All the other elements in the story—the user, his credentials, the data he downloads from the SaaS application—are part of routine processes. It was the employee’s mobile phone with a potentially malicious app that placed data at risk.
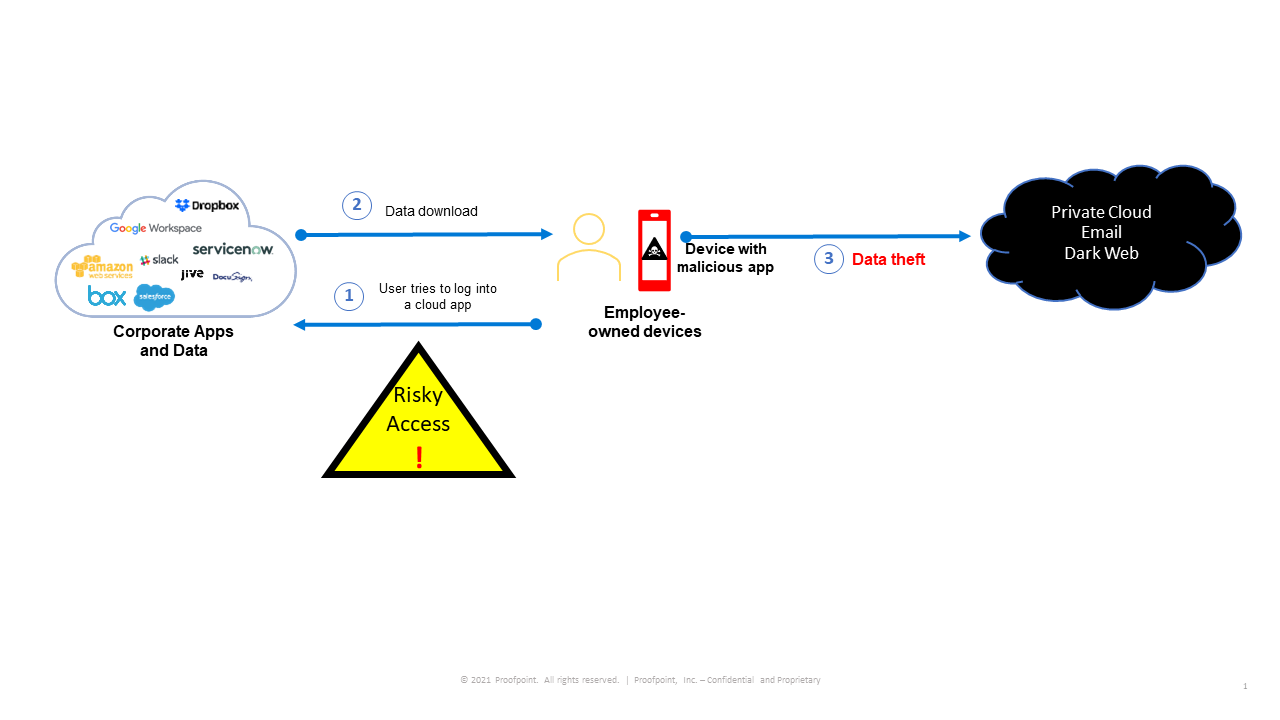
Figure 1. The last point of control chain of events leading up to data theft.
Proofpoint CASB Adaptive Access Controls can provide cloud data loss prevention (DLP) and reduce access risks for your organization’s approved SaaS apps.
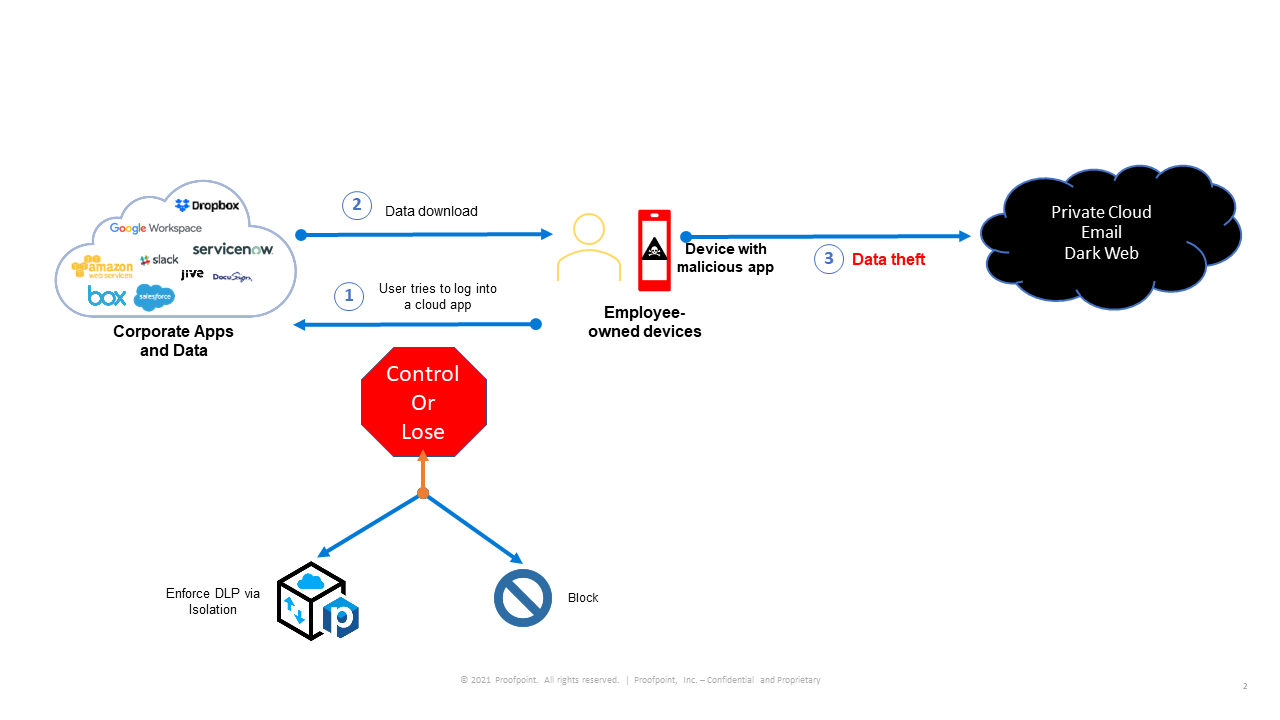
Figure 2. The last point of control chain events showing where enforced DLP via isolation comes into play.
As Figure 2 shows, Proofpoint Cloud App Security Broker (CASB) with adaptive access controls can provide the granular control needed to make sure data isn’t placed at risk.
Adaptive access controls enable you to:
- Take an all-encompassing action like “Block” that would prevent corporate data from being accessed from all personal mobile devices.
- Allow an employee to browse data but prevent them from uploading and downloading files.
- Use Proofpoint Browser Isolation to let employees look at information they need but prevent them from violating DLP rules that you’ve configured.
Proofpoint CASB can determine when to apply one of the three options outlined above, depending on various factors such as geolocation, IP reputation, the employee’s corporate group and the application the employee is accessing.
A more secure approach to BYOD
Now, let’s bring Proofpoint CASB and its context-aware fine-grained adaptive access control into the picture. Say that Fred is accessing the SaaS app from a country that is well-known for not respecting intellectual property or has a high crime rate (think: device theft). In this case, a preconfigured rule would block Fred from accessing the SaaS app from his mobile phone.
Proofpoint CASB can also enable Fred to access information in an isolated browser session but prevent him from downloading data. This access experience is seamless and doesn’t introduce any latency into the user experience. It also doesn’t require Fred to install any additional software on his device.
In a different scenario, if Fred was accessing a SaaS app that doesn’t have confidential data but must not contain certain data types like credit card information or vehicle registration numbers, Proofpoint Enterprise DLP can help enforce this as well. That way, Fred can access the information he needs and is productive without compromising information security or violating regulations.
What if Fred’s phone was a corporate device? Proofpoint CASB can detect such managed devices and implement a different set of rules to achieve the same goals of protecting information and enabling secure access. CASB can also detect suspicious logins (sign-in attempts with stolen credentials) using various parameters and block access.
Proofpoint CASB is part of our Enterprise DLP solution, with all DLP alerts and events across cloud, email, endpoint, and web channels flowing into one platform. Learn more about our fast time to value and multimode Proofpoint CASB.
