This blog post is part of a monthly series exploring the ever-evolving tactics of today’s cybercriminals. Cybersecurity Stop of the Month focuses on the critical first steps in the attack chain—reconnaissance and initial compromise—in the context of email threats.
The series is designed to help you understand how to fortify your defenses to protect people and defend data against emerging threats in today’s dynamic threat landscape.
The first two steps of the attack chain: reconnaissance and initial compromise.
So far in this series, we have covered the following types of attacks:
In this post, we look at a telephone-oriented attack delivery (TOAD) threat that Proofpoint detected during a recent threat assessment. We also cover the typical attack sequence of TOAD threats. And we take a deeper look into how the artificial intelligence (AI) and machine learning (ML) engines that Proofpoint uses can detect these threats.
The scenario
Social engineering tactics continue to evolve as bad actors look for more creative ways to gain initial access to sensitive systems. TOAD attacks are a testament to that, as attackers try to trick recipients into calling a phone number instead of clicking on URLs within or replying to email messages.
TOAD moves the attack channel from an initial email to the telephone. Since additional protection for phone calls often doesn’t exist, blocking these initial emails is crucial. But TOAD attacks don’t often contain URLs or attachments, which makes them difficult to detect.
Across all threat assessments in August 2023, Proofpoint detected over 19,000 TOAD threats behind 14 different email security solutions. Recently, we detected a TOAD attack at a manufacturing company with over 45,000 employees, which allowed us to break the attack chain.
In this scenario, a bad actor had crafted a fraudulent message about a charge to the recipient’s account for an antivirus subscription with a well-known brand. Instead of including URLs or attachments in the message, the attacker included a phone number. If the recipient called that number, the attacker could then direct the recipient back to their computer and guide them to click on a malicious URL. That could lead to various threats including remote access, exfiltration of sensitive data or the installation of ransomware.
The threat: How did the attack happen?
Here is a closer look at how the recent TOAD attack at the manufacturing company unfolded:
-
The deceptive message: An email claimed to be an alert about an upcoming purchase from this well-known tech company.
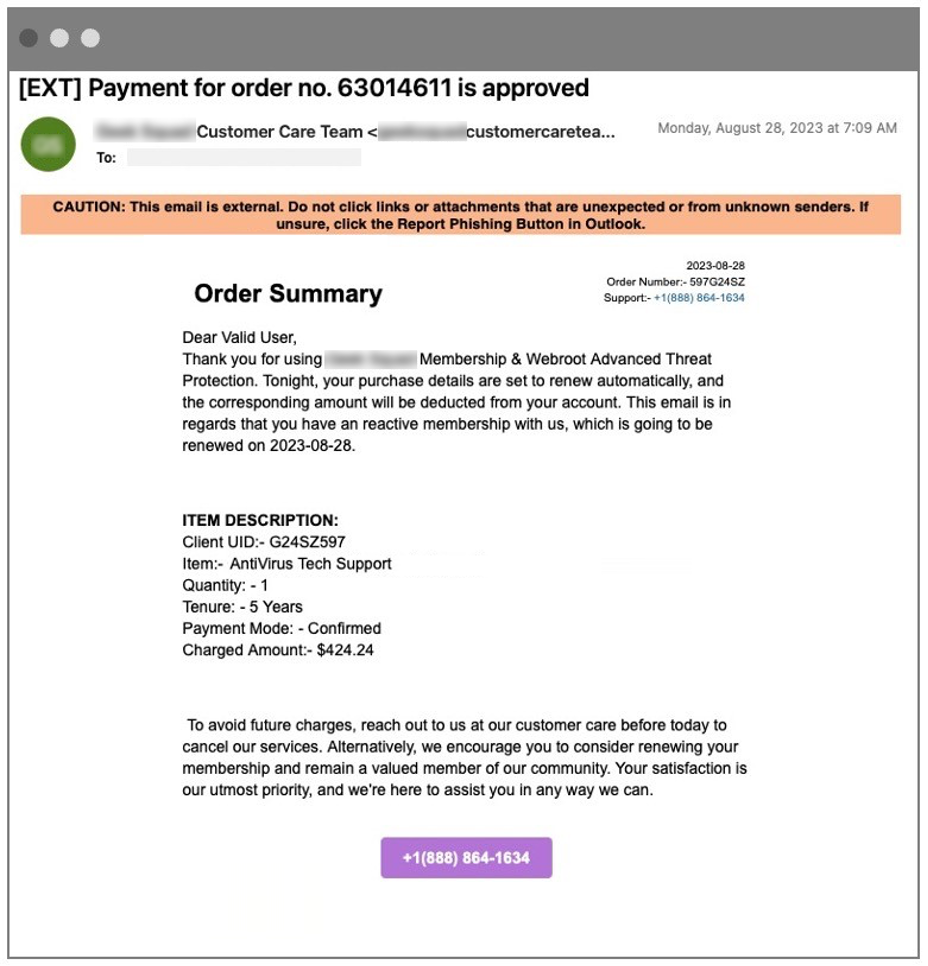
The original malicious email delivered to the recipient’s inbox.
-
TOAD attack sequence: When recipients call phone numbers included within TOAD threats, the bad actors will attempt to trick them into installing malicious software or exposing other sensitive data.
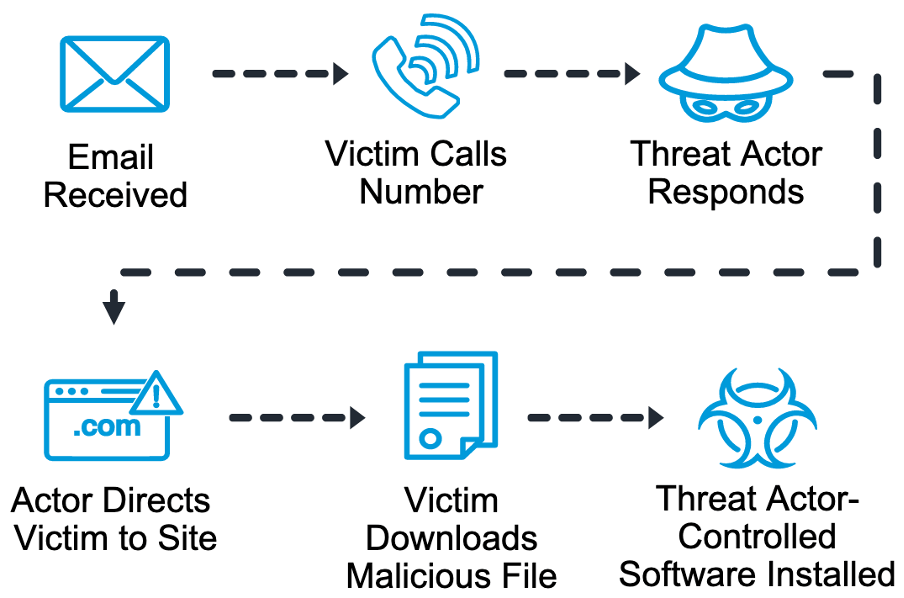
Overview of a typical TOAD attack sequence for malware.
Detection: How did Proofpoint detect the attack?
TOAD threats can be challenging to detect since they rarely include malicious payloads. Adversaries often use well-known domains that belong to Google, Microsoft or other legitimate email services in TOAD attacks.
Since the TOAD threat Proofpoint detected was sent from a Google-owned domain, the message passed email authentication checks like SPF (Sender Policy Framework) and DMARC. Both the passing of email authentication checks and the absence of a malicious payload might explain why the customer’s existing security solution delivered the threat.
Our behavioral AI engine uses multiple message-level signals that enable Proofpoint to detect and block sophisticated phishing attacks and text-based threats like business email compromise (BEC) and TOAD.
By processing the language of the message, we deciphered language pertaining to a financial transaction. Our language analysis also detected urgency in that the transaction was slated to take place the same day as the email was received. That also created an immediate need for the recipient to act.
TOAD attacks always include a phone number for the recipient to call—which is something Proofpoint’s detection engines scan for. In some cases, an additional tell is that the message includes a call to action to use the phone number.
By combining language analysis with other malicious signals, Proofpoint can detect many different forms of social engineering attacks. We conducted a multilayered analysis and found that the recipient hadn’t received email from the sender in the past, based on historical communication patterns. No one in the company had received an email from this sender before, either.
Proofpoint also detected brand abuse despite its unusual origination within the message headers. As is typical with TOAD attacks, bad actors will send messages masquerading as a legitimate brand to try and build implicit trust in the legitimacy of the message. Our analysis detected this tactic.
Summary of Proofpoint’s observations that lead to condemnation.
To enhance the detection of TOAD attacks, Proofpoint uses AI/ML methodologies to analyze and combine various behavioral indicators. This approach is more reliable than just tracking and maintaining a database of previously identified malicious phone numbers associated with TOAD attacks.
We make sure that our ML models are trained on well-labeled, comprehensive and diverse data. That, in turn, allows Proofpoint to detect many different forms of email threats and break the attack chain.
Remediation: What are the lessons learned?
To safeguard against threats like TOAD and other socially engineered threats, businesses need to implement proactive measures like:
- User education. Your employees and customers are your first line of defense. Make sure they get security awareness training about all types of attacks, including deceptive emails, suspicious tasks and unusual requests. This can significantly reduce their chances of falling victim to advanced attacks.
- Preemptive email security. The only way to keep users completely safe is to block malicious messages. Look for a solution that uses a combination of ML algorithms and advanced threat detection to identify and stop these threats—like the threat detection platform from Proofpoint. Other solutions claim to detect these threats, but they do so later in the attack (after the threat has already been delivered to users’ inboxes). That means users are exposed to threats until those messages can be removed.
Proofpoint helps break the attack chain
Attackers will exploit well-known brands, create a sense of urgency and make unusual requests as part of their social engineering attacks. And that’s a strong reminder why multilayered and robust cybersecurity measures are essential for defense.
We invite you to stay tuned to this blog series as we will continue to share information about the latest threats, our detection methodologies and more. By shining a light on the attack chain, we hope to disrupt it and empower businesses to take proactive steps to defend against emerging threats.
Together, we can enhance threat visibility, improve efficacy detection and increase operational efficiencies to help make the digital world safer for everyone.
Stay informed, protected and ahead of the game
To learn how to protect yourself against threats like TOAD attacks, download our e-book, The Definitive Email Cybersecurity Strategy Guide.
