More than 160 days after the last observed Emotet delivery via email, Proofpoint researchers have confirmed its return. Known as a versatile and widely disruptive threat, early versions of Emotet had a module that was used to commit banking fraud, and for years, the malware was widely classified as a banking Trojan. However, later versions of Emotet no longer loaded its own banking module, and instead loaded third party banking malware. More recently, we have observed Emotet delivering third-party payloads such as Qbot, The Trick, IcedID, and Gootkit. Additionally, Emotet loads its modules for spamming, credential stealing, email harvesting, and spreading on local networks.
As of this publication, Proofpoint has observed nearly a quarter million Emotet messages sent on July 17, 2020, and the number continues to climb. The threat actor, TA542, appears to have targeted multiple verticals across the US and UK with English language lures. These messages contain malicious Microsoft Word attachments or URLs linking to Word documents (Figures 1-3). The URLs often point to compromised WordPress hosts.
Similar to lures observed previously, these are simple, with minimal customization. Subject lines like “RE:”, “Invoice #” followed by a fake invoice number are commonly seen, and often include the name of the organization being targeted.
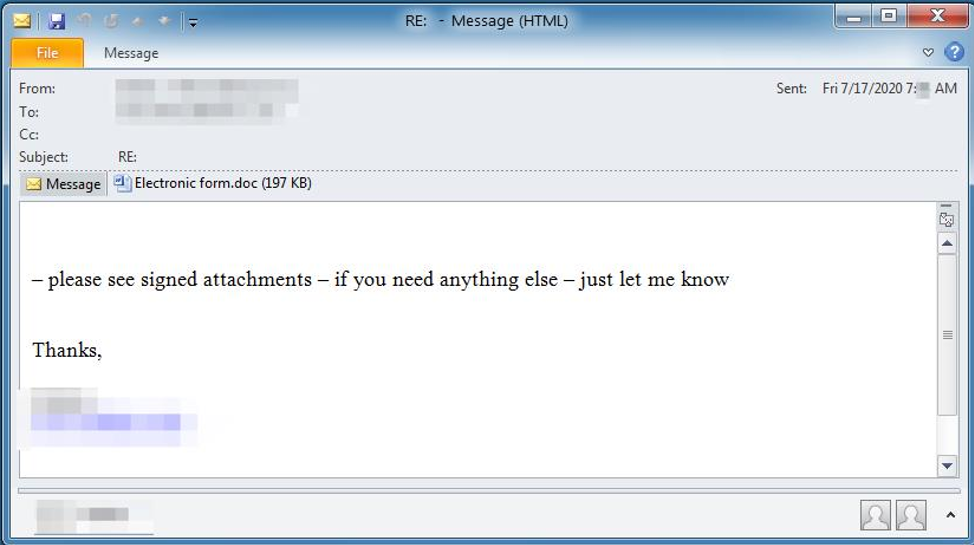
Figure 1: Email lure with malicious Word doc attachment
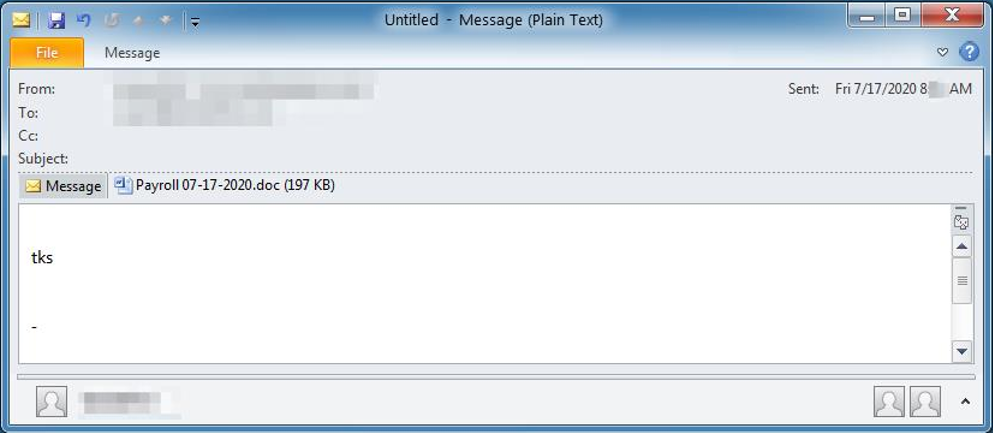
Figure 2: Additional email lure with malicious Word doc attachment
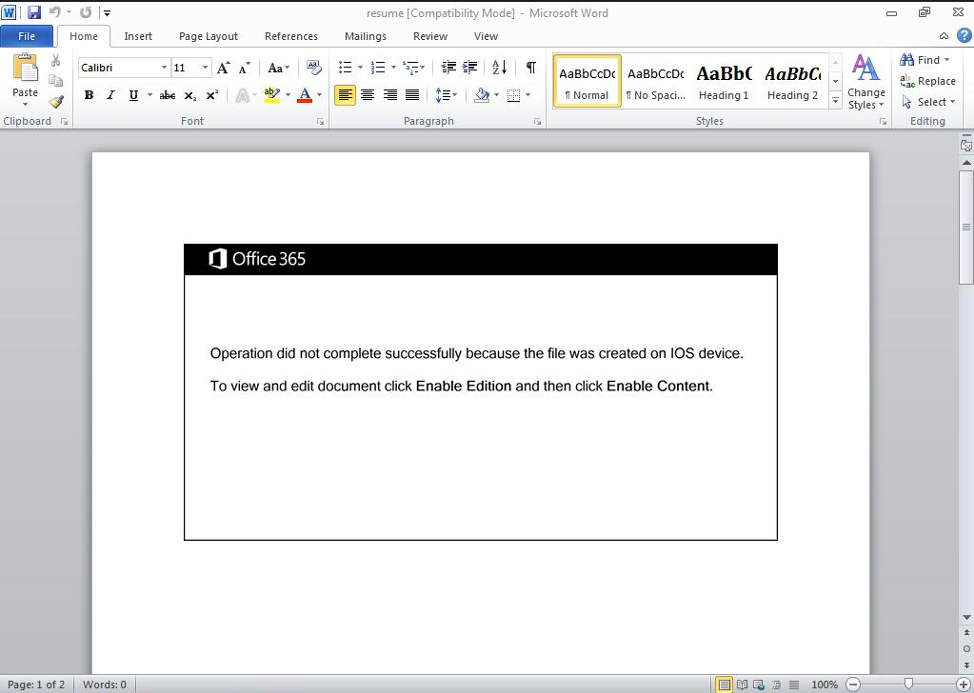
Figure 3: Word document with malicious macros
When the macros are enabled, Emotet is downloaded and installed on the user’s host. Often, Emotet downloads and installs additional modules to steal credentials, harvest emails, and spread itself across local networks.
Sample IOCs
Emotet C2s
5.196.74.210:8080
209.141.54.221:8080
50.116.86.205:8080
78.24.219.147:8080
210.165.156.91:80
37.187.72.193:8080
157.245.99.39:8080
190.55.181.54:443
37.139.21.175:8080
169.239.182.217:8080
104.236.246.93:8080
200.55.243.138:8080
74.208.45.104:8080
5.39.91.110:7080
79.7.158.208:80
SHA256 Hashes
64b341748b4d7b79976592e9eb4f04444436073d12384d8b98834931e9bc84cf
b7056c2e7ac89807060c5de0d28090f2dc827182433c186bbf8a28355a375627
Emerging Threats Network Signatures
2029380 ET TROJAN Win32/Emotet CnC Activity (POST) M8
2842317 ETPRO TROJAN Win32/Emotet CnC Activity (POST) M9
