The threat landscape evolved substantially in 2016. Criminals leveraged human vulnerabilities to launch more malicious email campaigns than ever before along with attacks across mobile and social media platforms. Exploit kits declined, ransomware exploded, and targeted attacks grew more sophisticated.
Our latest threat report reviews 2016's top security trends, techniques, and recommendations. In the post below, we review our top findings.
Email and Exploit Kits
Email remains one of the most common vectors cybercriminals leverage to breach enterprise networks and gain access to sensitive consumer, employee, and company data. And in recent months, attackers have sharpened their techniques.
Malicious email campaign volumes jumped dramatically in 2016—Q4's largest campaign was 6.7 times the size of Q3's largest—and malicious JavaScript attachments regularly outnumbered malicious document attachment volumes by a factor of four to six.
Ransomware variants, which multiplied 30 times over last year, became the threat de jour, while overall exploit kit activity fell 93% from its Q1 high.
On the BEC front, we saw CEO-to-CFO spoofing drop 28% between August and December while DMARC (Domain-based Message Authentication Reporting and Conformance) adoption grew 33% as organizations looked to automated means of addressing the BEC threat. Credential phishing on the other hand remains a large-scale threat, usually propagated through malicious links via email.

Figure 1: Indexed malicious message volume by attack type
Mobile
On the mobile front this year, hundreds of thousands of devices were potentially exposed to attacks that redirected users to malicious websites through the DNSChanger exploit kit. DNSChanger EK, however, exploited vulnerable SOHO routers instead of mobile and desktop devices.
In addition, several significant mobile risks emerged beyond the growth of malware, including:
- Risks from malicious clones of popular apps like Pokémon GO
- Increased use of side-loading to distribute unauthorized apps
- The availability of targeted attack tools for mobile devices like Pegasus
The Summer Olympics sparked a new wave of criminal activity: we found that 4,500 mobile apps related to the games and sponsor brands were risky, potentially leaking data to app publishers, or outright malicious.
Social Media
Social media continued to be an emerging hotbed for cybercriminals. Fraudulent social media accounts doubled from the third to the fourth quarter of 2016 and social media phishing attacks increased 500% year-over-year. The latter figure includes angler phishing that intercepts customer support channels on social media.
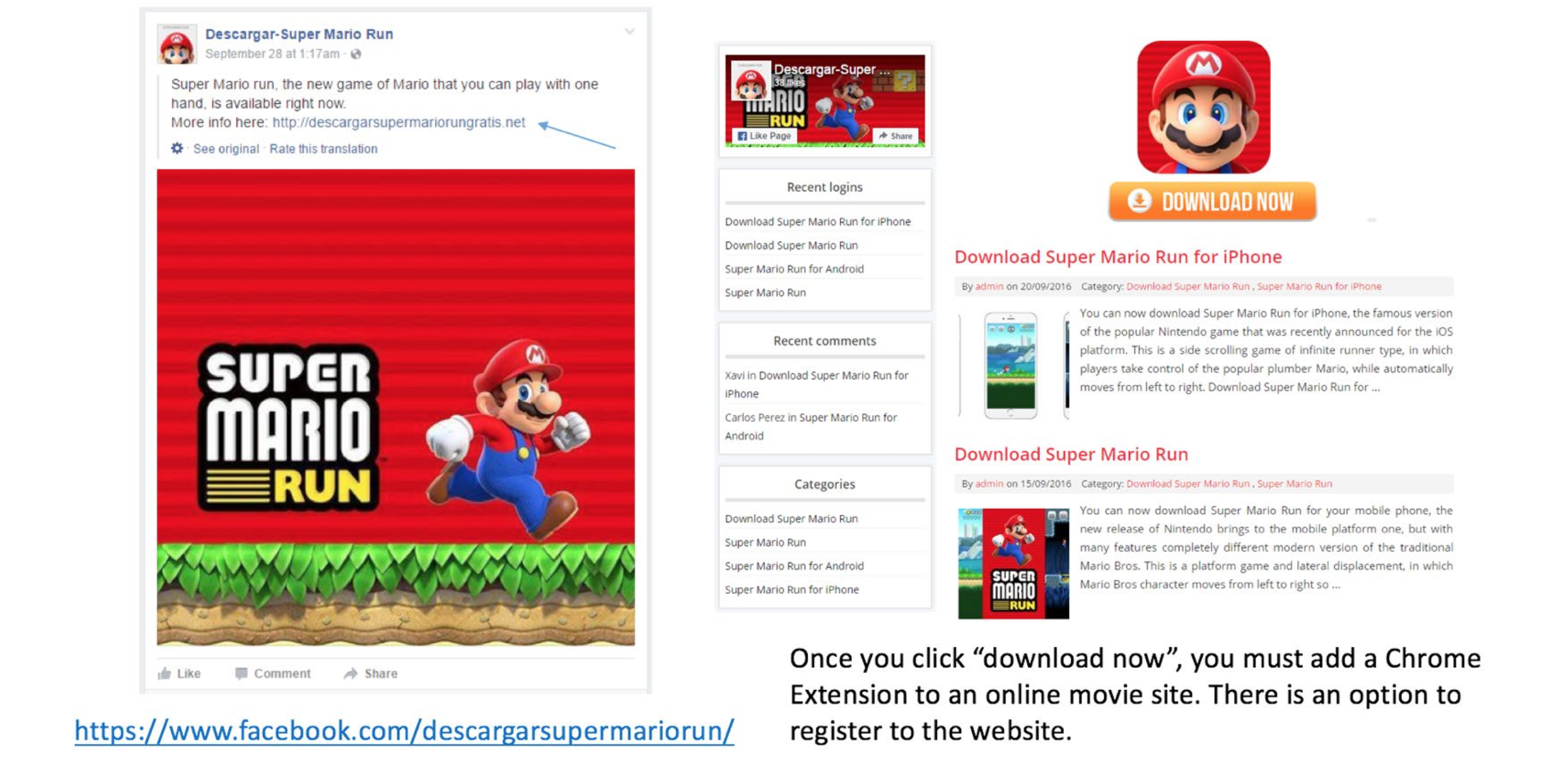
Figure 2: Fake downloads for Super Mario Run
Proofpoint's Recommendations for 2017
What should you do to protect your company and customers in the new year from these evolving and increasingly sophisticated attacks? Here are our top recommendations:
- Assume users will click. Social engineering is increasingly popular. Deploy a solution that identifies and quarantines both inbound email threats targeting employees and outbound threats targeting customers before they reach the inbox.
- Build a robust BEC defense. Highly-targeted, low volume BEC scams usually have no payload at all and are thus difficult to detect. Invest in a solution that has dynamic classification capabilities that you can use to build quarantine and blocking policies.
- Protect your brand reputation and customers. Fight attacks targeting your customers over social media, email, and mobile—especially fraudulent accounts that piggyback on your brand.
- Lock down mobile app environments. Invest in a data-driven solution that works with your mobile device management (MDM) tool and reveals the behavior of apps in your environment.
- Partner with a threat intelligence vendor. Consider a solution that combines static and dynamic techniques to detect new attack tools, tactics, and targets—and then learns from them.
For a deeper dive into the threat landscape in 2016, download our full report here.
