Oman is a small country on the southeastern coast of the Arabian Peninsula. With a population of roughly 4 million, Oman has fewer people than the US state of Kentucky. Yet this quiet Middle Eastern nation has garnered media attention recently because of its country code top-level domain (ccTLD): “.om.”
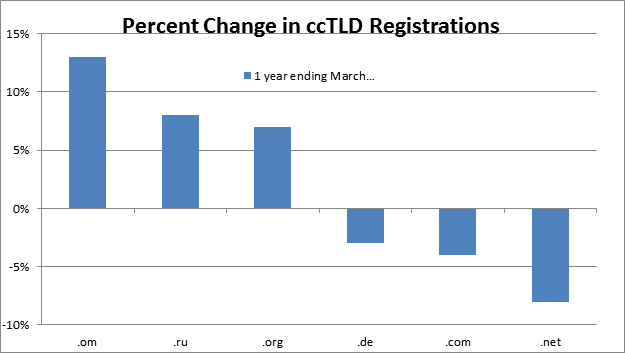
Figure 1: Change in overall percentage of global websites registered with the .om ccTLD versus the 5 largest TLDs on the web in the last year. Data courtesy of w3techs.com (http://w3techs.com/technologies/history_overview/top_level_domain)
Many of the most popular top-level domains such as .com and .net have declined over the last year in their usage as a proportion of domains globally. But .om has steadily increased, as shown in Figure 1, which compares .om growth to the top 5 TLDs on the web. One possible reason: “typosquatting.”
Typosquatting is a method phishers use to capitalize on common misspellings in domain names, in some cases creating malicious domains that closely resemble those of legitimate brands.
Researchers at cybersecurity firm Endgame have been tracking one particular typosquatting campaign and found that over 300 top brands were targeted in February using the .om ccTLD. Endgame posted the full list of suspicious domains, 58 of which target 42 of the top 100 web properties by Alexa rank and 85 of which are associated with Fortune 500 brands and sites. Based on their country-specific Alexa ranks, this campaign had potential targets in the US; China; the UK; France; and elsewhere throughout Europe, Asia, and the Americas. This single campaign gives a sense of the profile and potential reach of typosquatting just using the .om domain, to say nothing of the sites that rely on other TLDs and common misspellings.
The email in Figure 2 is an illustrated example of the sorts of typosquatting emails we see frequently. Logos are often exact copies of real corporate logos, and the emails look legitimate. Note the use of the .om ccTLD to make a malicious website resemble a known .com domain. End users often overlook domain names that differ by a single period or an extra letter. So they click through URLs or respond to emails, which they believe are those of legitimate sites.
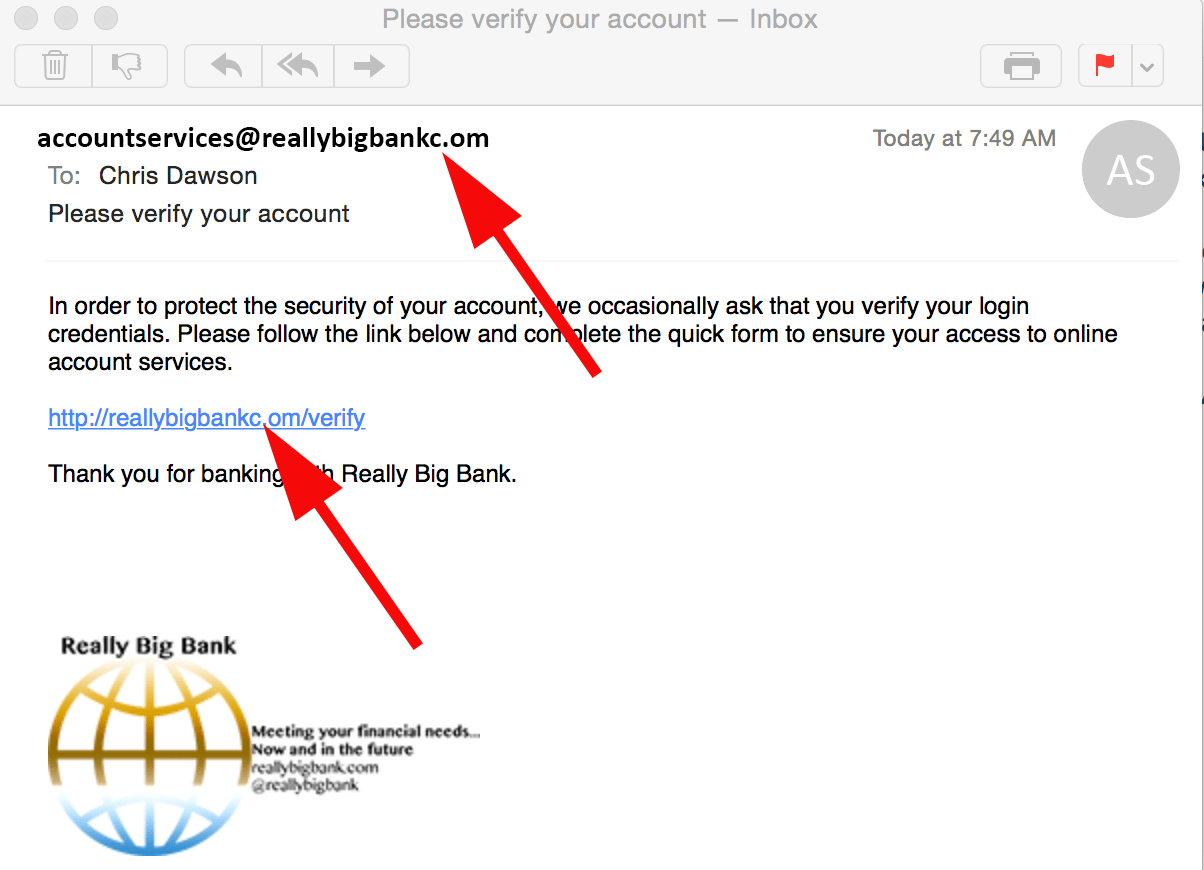
Figure 2: A fake email illustrating common features of typosquatting in a phishing attack
Typosquatting is nothing new. "Goggle.com" was sending accidental visitors to a malicious site with drive-by malware downloads as early as 2006. The World Intellectual Property Organization (WIPO) has well-defined procedures for disputing typo- and cyber-squatting attempts. The U.S. government has even had laws on the books regarding cyber squatting since 1999 with amendments that address typosquatting.
But as new top-level domains emerge and phishing kits give cybercriminals increasingly realistic graphics for their lures, the practice is becoming more common and effective.
For example, using the .om domain appears to be the current go-to typosquatting domain since registering lookalike .com domains is easy. Omani registrations are supposed to be restricted to subdomains like .com.om (the .om ccTLD is normally reserved for official and government entities in Oman). But criminals and researchers have found workarounds and services that can access the top-level .om domain. At a glance, “yourcompanyc.om” looks a lot like “yourcompany.com.” This practice, depicted in our earlier example, has come up frequently with customers.
Figure 2 is an illustration. But we have seen emails like it purporting to be from major banks and using common phishing lures all making use of typosquatting and lookalike domains.
Ultimately, this trend is just a minor twist in a common plot. But it brings up two important points for organizations:
- Phishing puts your organization and users at risk for a variety of cybercrime, ranging from impostor email schemes (also known as business email compromise, or BEC) to credential phishing attacks that are part of larger cyber attacks.
- Phishing that uses typosquatting and otherwise co-opts brands puts your brand at risk.
The first point isn't news. We've been talking about phishing for a long time, and the potential risks in terms of crime are well understood, even if organizations and consumers continue to be victimized every day.
The second point, though, is something that organizations are beginning to consider more carefully. When cyber criminals lure consumers to acmecorpc.om, where they are infected by malware from an exploit kit, the immediate association is not with crime but with Acme Corp itself.
In fact, regularly checking for or proactively registering lookalike and typosquatting domains is considered a best practice. Really Big Bank, for example, could have short-circuited the fictitious attack above by inexpensively registering reallybigbankc.om and redirecting the URL to its own website.
At the same time, best practices for protecting end users from phishing haven't changed. These steps can prevent the majority of phishing-related compromises, whether they come from typosquatting domains or not:
- Use and properly configure secure email gateways. Implement solutions that can detect and mitigate a wide range of threats including impostor emails.
- Implement anti-spoofing rules and features, including
- Adding SPF (Sender Policy Framework) rules to existing DNS information. SPF records are not foolproof but ensure that incoming emails have sender addresses validated.
- Comparison of From header addresses and envelope sender addresses
- Automatic addition of an “External” tag to subject lines from external senders; this would flag messages that purport to be from your organization but actually originate from an external domain
- Designating trusted domains explicitly and comparing header and envelope information against those domains where possible
- Adding DomainKey Identified Mail (DKIM) authentication where possible
- Implement reputation-based content filtering to reduce the likelihood that users can click through a malicious link
- Train users to spot phishing in all of its forms. Users remain critical links in managing security effectively.











