Phishing is a common type of cyber-attack that targets individuals through email, text messages, phone calls, and other forms of communication. A phishing attack aims to trick the recipient into falling for the attacker’s desired action, such as revealing financial information, system login credentials, or other sensitive information. Fundamentally, these threats exploit human psychology rather than technical vulnerabilities.
As a popular form of social engineering, phishing uses psychological manipulation and deception whereby threat actors masquerade as reputable entities to mislead users into performing specific actions. These actions often involve clicking links to fake websites, downloading and installing malicious files, and divulging private information, like bank account numbers or credit card information.
Since the mid-1990s, the term “phishing” has been used to identify hackers who use fraudulent emails to “fish for” information from unsuspecting users. However, phishing attacks have become increasingly sophisticated and are now broken down into different types, including email phishing, spear phishing, smishing, vishing, and whaling. Each type is characterized by specific channels and methods of execution—email, text, voice, social media, etc.—all with a similar underlying intention of exploiting human trust and decision-making processes.
Table of Contents
How Phishing Works
A phishing campaign always starts with a malicious message disguised to look like it’s from a legitimate sender, usually a company. The more aspects of the message that mimic the real company, the more likely an attacker will be successful.
While their goals may vary, attackers aim to steal personal information or credentials. An attack is facilitated by injecting a sense of urgency into the message by, for example, threatening account suspension, money loss, or loss of one’s job. Users tricked into an attacker’s demands typically don’t take the time to consider if the demands seem reasonable or if the source is legitimate.
“Cyber criminals know that humans can be easily exploited, either through negligence, compromised identity—or in some instances—malicious intent,” said Ryan Kalember of Proofpoint. “Individuals play a central role in an organization’s security posture, with 74% of breaches still centering on the human element. While fostering a security culture is important, training alone is not a silver bullet. Knowing what to do and doing it are two different things.”
It only takes one person to fall for a phishing attack to incite a severe data breach. That’s why it’s one of the most critical and challenging threats to mitigate, as it requires human defenses.
Why Is Phishing a Problem?
Phishing is a significant problem because it’s easy, cheap, and effective, making them widespread cyber-attacks. Victims of phishing scams may end up with malware infections (including ransomware), identity theft, and data loss. Unlike traditional security threats that target technical vulnerabilities, phishing directly exploits the human element of security—often the most vulnerable link in an organization’s security posture.
Cyber criminals seek data rich with personal identifiable information (PII)—like financial account data, credit card numbers, and tax and medical records—as well as sensitive business data, such as customer names and contact information, proprietary product secrets, and confidential communications. According to Proofpoint’s research, over 90% of targeted attacks start with phishing emails crafted to appear legitimate to the specific recipients.
Phishing is also used to gain direct access to email, social media, and other accounts and obtain permissions to modify and compromise connected systems, like point-of-sale terminals and order processing systems. A simple phishing email may gain enough of a foothold for a cyber criminal to build up to a major data breach.
Personal vs. Workplace Phishing Risks
In personal life, phishing risks often target individual financial accounts, social media profiles, and personal identity information. These attacks can lead to financial losses, identity theft, or compromised personal data.
In the workplace, phishing poses broader risks, potentially compromising entire corporate networks, sensitive business data, and client information. A successful workplace phishing attack can result in significant financial damage, reputational harm, and legal consequences for the organization. While personal phishing mainly affects individuals, workplace phishing can have far-reaching impacts on multiple stakeholders, including employees, customers, and business partners. The human-centric nature of these attacks means that organizations must focus on both technical defenses and employee awareness training to create a comprehensive security culture.
Phishing Examples
Attackers prey on fear by creating a sense of urgency, often using strategies that tell users their account has been restricted or will be suspended if they don’t respond to the email. Because phishing attacks are typically sent to as many people as possible, the messaging is usually thin and generic. The following illustrates a common phishing email example.

In the above message, the user’s name is not mentioned, and the sense of urgency tricks users into opening the attachment.
The attachment could be a web page, a shell script (e.g., PowerShell), or a Microsoft Office document with a malicious macro. The macro and scripts can be used to download malware or trick users into divulging their account credentials. In some email phishing tactics, attackers register domains similar to their official counterparts or occasionally use generic email providers such as Gmail. The messages might contain the official company logo, but the sender’s address would not include the official company domain.
How an attacker carries out a phishing campaign depends on their goals. Attackers may attach fake invoices to trick an organization’s accounts payable department into sending money.

The button in this example opens a web page with a fraudulent Google authentication form. The page attempts to scam targeted victims into entering their Google credentials so that attackers can steal accounts. These social engineering tactics are designed to bypass technical security measures by manipulating the people who have legitimate access to systems and data.
Phishing Techniques
Cyber criminals use three primary phishing techniques to steal information: malicious web links, malicious attachments, and fraudulent data-entry forms. These techniques are designed to exploit human psychology and behavior, making them particularly effective in bypassing traditional security measures.
Malicious Web Links
Phishing links take users to impostor websites or sites infected with malicious software, known as malware. Malicious links can be disguised as trusted links and are embedded in logos and other images in an email.
Here is an example of an email received by users at Cornell University, displaying “Help Desk” as the sender’s name. However, the email did not originate from the university’s help desk but from the @connect.ust.hk domain. The link embedded in the email points to a page that mirrors the Office 365 login page, attempting to steal user credentials.

Malicious Attachments
While these may look like legitimate file attachments, they are actually infected with malware that can compromise computers and their files.
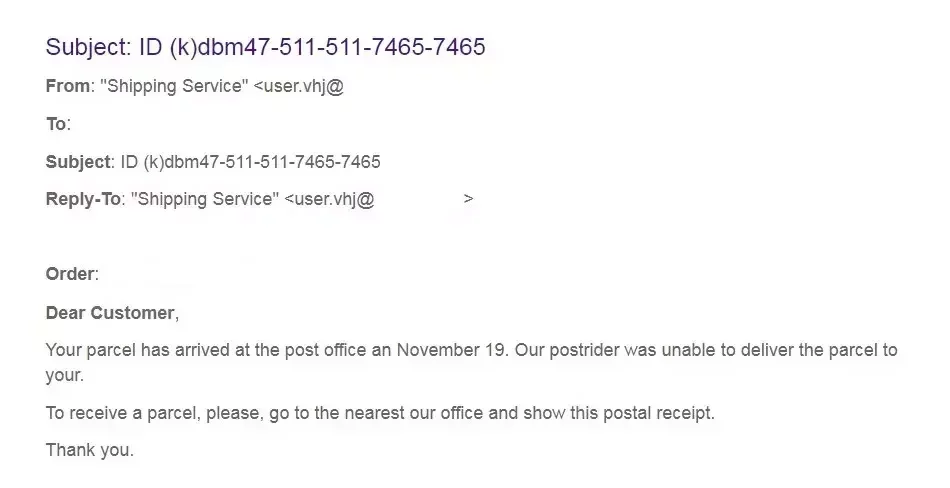
Here’s an example of a phishing email shared by international shipper FedEx on its website. This email encouraged recipients to print a copy of an attached postal receipt and take it to a FedEx location to get a parcel that could not be delivered. Unfortunately, the attachment contained a virus that infected the recipients’ computers. Variations of these shipping scams are prevalent during the holiday shopping season.
Fraudulent Data Entry Forms
These techniques use fake forms that prompt users to fill in sensitive information—such as user IDs, passwords, credit card data, and phone numbers. Cyber criminals use the submitted information for various fraudulent activities, including identity theft.
Here’s an example of a fake landing page mimicking the gov.uk website. After clicking a link in a phishing email, users are routed to this fraudulent page that appears to be part of the HMRC tax collection agency. Users are told they are eligible for a refund but must complete the form first.

Types of Phishing Attacks
Phishing has evolved into more than simple credential and data theft. An attacker’s process depends on the following phishing types:
- Email phishing: The general term for any malicious email message meant to trick users into divulging private information. Attackers generally aim to steal account credentials, personally identifiable information (PII), and corporate trade secrets. However, attackers targeting a specific business might have other motives.
- Spear phishing: These email messages are sent to specific people within an organization, usually high-privilege account holders, to trick them into divulging sensitive data, sending the attacker money, or downloading malware. This hyper-targeted approach exploits the human tendency to trust communications that appear personalized and relevant.
- Link manipulation: Messages contain a link to a malicious site that looks like the official business but takes recipients to an attacker-controlled server where they are persuaded to authenticate into a spoofed login page that sends credentials to an attacker.
- Whaling (CEO fraud): These messages are typically sent to high-profile employees of a company to trick them into believing the CEO or other executive has requested a money transfer. However, be warned that “A CEO’s executive assistant is statistically more likely to be a very attacked person than a CEO,” Proofpoint’s Ryan Kalember told F1 Solutions.
- Content injection: An attacker who has injected malicious content into an official site tricks users into accessing the site to show them a malicious popup or redirect them to a phishing website.
- Malware: A clicked link or opened attachment might download malware onto devices. Ransomware, rootkits, or keyloggers are common malware attachments that steal data and extort payments from targeted victims.
- Smishing: Using SMS messages, attackers send a text message to a targeted victim with a malicious link that promises discounts, rewards, or free prizes. This technique exploits the increasing reliance on mobile devices and the quick, often less cautious way people interact with text messages.
- Vishing: Attackers use voice-changing software to leave a message telling targeted victims they must call a number where they can be scammed. Attackers also use voice changers when speaking to targeted victims to deceive them.
- “Evil Twin” Wi-Fi: Spoofing free Wi-Fi, attackers trick users into connecting to a malicious hotspot to perform man-in-the-middle exploits.
- Pharming: Pharming is a two-phase attack used to steal account credentials. The first phase installs malware on a targeted victim and redirects them to a browser and a spoofed website, where they are tricked into divulging credentials. DNS poisoning is also used to redirect users to spoofed domains.
- Angler phishing: Attackers reply to social media posts as an official organization to trick users into divulging account credentials and personal information.
- Watering hole: An attacker identifies a site numerous targeted users use, exploits a vulnerability, and uses it to trick users into downloading malware. With malware installed on targeted user machines, an attacker can redirect users to spoofed websites or deliver a payload to the local network to steal data.
Most Targeted Industries
The goal of most phishing attacks is financial gain, so attackers target specific industries and platforms that store payment data. However, these attacks primarily exploit the human element within these industries, targeting employees and customers with access to valuable systems and information. Below are some of the most targeted industries and sectors, according to the latest data from Statista:
- eCommerce/retail: With customers entering both personal and financial information during transactions, these platforms present a significant opportunity for data theft and account for 8% of phishing attacks. Common tactics include sending fake order confirmation emails containing malicious links. These attacks exploit customers’ anticipating order updates and trusting familiar brand communications.
- Social media: Facebook, Instagram, LinkedIn, and other popular social platforms have become a hotbed for phishing, with 30% of attacks targeting these platforms. Cyber criminals exploit users’ trust in these platforms by creating fake profiles and sending malicious messages.
- Banks and other financial institutes: The financial sector remains the prime target for phishers, accounting for 13% of all phishing attacks. Banks, payment platforms, and other financial institutions handle massive amounts of sensitive personal data and have direct access to bank accounts, making them lucrative targets for cyber criminals. The nature of these threats often creates a sense of urgency around account security or financial opportunities.
- Payment systems (merchant card processors): Payment processors, reflecting 5.8% of all phishing attacks, are prime targets for cyber criminals due to the sensitive financial data they handle. Phishers often target employees to steal login credentials, potentially gaining access to vast amounts of financial information.
- Technology: The interconnected nature of tech companies makes them attractive targets for cyber criminals seeking to exploit vulnerabilities in the software supply chain. Alarmingly, 80% of reported cyber crimes in this sector are attributed to phishing attacks. These attacks often target technical employees with elevated access privileges, demonstrating that human-centric security is crucial even in highly technical environments.
- Telecommunication companies: Reflecting 4.9% of phishing attacks, telecom companies operate in a highly risk-laden environment due to the vast amount of customer data they hold. Successful phishing attacks on these companies could lead to service interruptions and potential leakage of sensitive customer information. The human factor is particularly important here, as employees often have access to multiple systems and customer accounts.
- Logistics and shipping: The logistics and shipping industry faces unique cybersecurity challenges due to its critical role in global supply chains. The widespread adoption of IoT devices in logistics has also created new entry points for cyber criminals, leading to 3.1% of phishing schemes.
- Healthcare companies: The healthcare sector, storing vast amounts of highly sensitive patient data, is particularly vulnerable to phishing attacks. The transition from paper to digital records has increased the industry’s exposure to such threats.
- Travel: The travel industry is vulnerable to phishing attacks targeting loyalty programs, attempting to steal points or miles with monetary value. Cyber criminals often create fake travel booking websites or send phishing emails with “too good to be true” deals to lure victims into providing personal and financial information.
Most Impersonated Brands
To exploit as many people as possible, attackers use well-known brands that recipients inherently trust, increasing their success. This strategy leverages the psychological principle of authority, as people are more likely to comply with requests from entities they recognize and respect. Specific company brands are consistently leveraged due to their widespread use and the valuable data associated with their accounts. As of early 2025, the most frequently impersonated brands in phishing attacks include:
- Microsoft
- Apple
- Alibaba
- Amazon
- Adobe
Technology giants and social media platforms dominate the list, reflecting their vast user bases and the critical nature of the accounts they manage. E-commerce giant Alibaba has also entered the top ranks, indicating its growing global presence.
During peak shopping seasons, luxury and popular retail brands like Nike, Adidas, and Lululemon see increased impersonation attempts. Cyber criminals often create fraudulent domains with phony sales and fake discounts to lure unsuspecting shoppers. These seasonal attacks demonstrate how threat actors adapt their human-centric targeting strategies based on predictable changes in consumer behavior and attention.
How AI Is Evolving Phishing
AI is revolutionizing phishing attacks, making them more sophisticated, personalized, and difficult to detect. This technological advancement is reshaping the cybersecurity landscape in several key ways:
Hyper-Personalization
AI-powered tools now enable attackers to craft highly tailored phishing emails by scraping and analyzing vast amounts of publicly available data. These messages can reference recent company news, mimic a colleague’s writing style, or even mention personal details gleaned from social media, making them incredibly convincing.
“Threat actors are notorious for using current events to create enticing social-engineering lures,” said Sherrod DeGrippo, VP of Threat Research and Detection at Proofpoint. “Threat actors are hoping to evoke an emotional reaction and elicit a click without judgment,” she adds.
Increased Volume and Quality
The automation capabilities of AI significantly reduce the cost and effort required to launch phishing campaigns. This allows cyber criminals to scale up their operations, potentially increasing the number of attacks by more than 95% while maintaining or improving success rates. As a result, we can expect a surge in both the volume and quality of phishing attempts in the coming years.
Advanced Deepfake Technology
Deepfake technology has become more accessible and sophisticated, enabling attackers to create convincing audio and video impersonations. This advancement has led to a rise in voice phishing (vishing) attacks, where criminals can clone voices with just an hour of audio footage, making phone-based scams much more believable.
AI-Powered Conversational Phishing
Should a victim respond to an initial phishing attempt, AI-driven chatbots can now engage in natural, context-aware conversations. These bots analyze previous exchanges to deliver timely and believable responses, subtly guiding targets towards revealing sensitive information or clicking malicious links.
Rapid Adaptation
AI enables phishing campaigns to evolve in real time based on victim behavior and response rates. This adaptive capability allows attackers to quickly refine their tactics, abandoning unsuccessful approaches and doubling down on effective strategies.
As AI continues to enhance the sophistication of phishing attacks, organizations and individuals must remain vigilant and adapt their cybersecurity strategies accordingly. This includes implementing advanced AI-powered security solutions, regularly updating phishing awareness training, and adopting a zero-trust approach to digital communications.
Phishing Prevention
Preventing phishing attacks requires a combination of user training to recognize the warning signs and robust cybersecurity systems to stop payloads. Email filters are helpful with phishing, but human prevention is still critical.
Proofpoint’s Sr. Product Marketing Manager Sara Pan warns, “Nine times out of 10, attackers and scammers will try to manipulate our emotions. And one of the most common emotional tools that we see in phishing attacks is fear.” This psychological manipulation is precisely why technical solutions alone cannot fully address the phishing threat landscape.
A few ways your organization can prevent being a victim of phishing:
- Train users to detect a phishing email: a sense of urgency and requests for personal data, including passwords, embedded links, and attachments, are all warning signs. “Attackers will urge victims to take immediate action, so they don’t have time to think, increasing the success rate of their attack,” Pan says. Users must be able to identify these warning signs to defend against phishing.
- Avoid clicking links: instead of clicking a link and authenticating into a web page directly from an embedded link, type the official domain into a browser and authenticate directly from the manually typed site.
- Use anti-phishing email security: artificial intelligence scans incoming messages, detects suspicious messages, and quarantines them without allowing phishing messages to reach the recipient’s inbox. Proofpoint’s advanced email security solutions detect and block an average of 66 million business email compromise (BEC) attacks per month.
- Change passwords regularly: users should be forced to change their passwords every 30-45 days to reduce an attacker’s window of opportunity. Based on Proofpoint’s 2024 State of Phish report, reusing or sharing passwords ranks highest as the most risky behavior.
- Update software and firmware: software and firmware developers release updates to remediate bugs and security issues. Always install these updates to ensure known vulnerabilities are no longer in your infrastructure. This practice helps close potential entry points that phishing campaigns often exploit.
- Install firewalls: firewalls control inbound and outbound traffic. Malware installed from phishing silently eavesdrops and sends private data to an attacker, but a firewall blocks malicious outgoing requests and logs them for further review.
- Avoid clicking on popups: attackers change the location of the X button on a popup window to trick users into opening a malicious site or downloading malware. Popup blockers stop many popups, but false negatives are still possible. Teaching users to recognize these manipulation tactics is essential to building security awareness.
- Be cautious about disclosing credit card data: unless you know the site is entirely trustworthy, never give credit card data to a website you don’t recognize. Any site promising gifts or money should be used with caution. This vigilance should extend to QR codes and other emerging phishing vectors that Sara Pan identifies as growing threats.
Technology is pivotal in preventing phishing attacks, but awareness is equally vital. “Since people are the primary target of these evolving phishing attacks, you want to empower them with the right knowledge and tools to protect themselves and your organization,” Pan highlights.
How AI Is Advancing Detection
AI is revolutionizing phishing detection, making it more sophisticated and effective in combating increasingly advanced cyber threats. Here’s how AI is transforming the landscape of phishing defense:
- Machine learning for pattern recognition: AI-powered systems utilize machine learning algorithms to analyze vast amounts of email, web traffic, and user behavior data. This enables the detection of subtle patterns and anomalies that may indicate phishing attempts, even when traditional rule-based systems fail.
- Real-time threat analysis: Unlike traditional tools, AI can process and evaluate potential threats in real time, significantly reducing the window of opportunity for attackers. This rapid response capability is crucial in preventing successful phishing attacks before they can cause harm.
- Advanced email filtering: AI systems now analyze email headers, content, and metadata with unprecedented accuracy. By leveraging natural language processing and contextual analysis, these systems can identify sophisticated phishing attempts that might otherwise slip through conventional filters.
- Visual-AI for phishing detection: Innovative Visual-AI technologies are being integrated into phishing detection workflows. These systems visually analyze emails and web pages, mimicking human perception of high-risk elements that code-based detection might miss. This approach provides an additional layer of security, especially against visually deceptive phishing tactics.
- Behavioral analysis and anomaly detection: AI models can monitor and learn from user behavior patterns, enabling them to detect anomalies such as unusual login attempts or suspicious clicks. This behavioral analysis adds another dimension to phishing detection, making it harder for attackers to mimic legitimate user actions.
- Continuous learning and adaptation: Perhaps most importantly, AI-powered phishing detection systems continuously learn and adapt. As new phishing techniques emerge, these systems update their models, ensuring they remain effective against evolving threats.
“Some of the scarier tools are being birthed out of the dark web. You break into an email server, and then the AI goes and reads all the conversations and tells you how to best scam this organization,” notes Bastien Treptel, Co-founder of CTRL Group.
By leveraging these AI-driven approaches, organizations can significantly enhance their defenses against phishing attacks, providing a more robust and dynamic security posture in the face of increasingly sophisticated cyber threats.
Phishing Protection
Phishing protection is the security measures organizations can take to mitigate phishing attacks on their employees and systems. Security awareness training and education through real-world examples and exercises help users identify phishing. Organizations often work with experts who send simulated phishing emails to employees and track who opened the email and clicked the link.
Some email gateway solutions can catch and classify phishing emails based on the known bad reputation of the embedded URLs. However, these solutions are not always reliable in detecting well-crafted phishing messages from compromised legitimate websites.
The most effective systems identify suspicious emails based on unusual traffic patterns, rewrite the embedded URL, and monitor the URL for in-page exploits and downloads. Monitoring tools quarantine suspicious email messages so administrators can research ongoing phishing attacks. If a high number of phishing emails are detected, administrators can alert employees and reduce the chance of a successful targeted phishing campaign.
Another critical line of defense is user-based awareness training on the latest phishing and social engineering techniques to reduce the risk of breaches and generate a culture of cybersecurity.
What to Do If You’ve Fallen Victim
Once an attacker has accessed your information to an attacker, they will likely disclose it to other scammers. You may receive vishing and smishing messages, new phishing emails, and voice calls. Always be alert for suspicious messages asking for your information or financial details.
If you respond to a phishing email, “you’ll need to act quickly to mitigate the damage,” emphasizes Cybersecurity Analyst Dave Cook. In this post, he outlines steps to take if you’ve responded to a phishing email (condensed below):
- Change passwords: Immediately update passwords and ensure they are complex and unique.
- Report incident: Promptly inform the IT department or email provider about the phishing email.
- Enable MFA: Implement multifactor authentication for an extra layer of security.
- Monitor accounts: Scan devices for malware and check for any suspicious activity.
- Contact affected organization: Alert the company impersonated in the phishing attempt.
- Educate yourself: Learn about phishing tactics and how to identify suspicious emails.
At the company-wide level, Cook suggests that organizations “establish clear guidelines so that users know exactly what to do if they fall prey to a phishing scam. These guidelines should include changing passwords, notifying IT, enabling 2FA, checking for malware, and remaining vigilant in the future.”
The Federal Trade Commission has a website dedicated to identity theft to help you mitigate damages and monitor your credit score. To detect and remove the malware, ensure your antivirus software is up-to-date and has the latest patches installed.
Stay Vigilant with the Right Human-Centric Security Provider
Phishing remains a highly dynamic and evolving cybersecurity threat in 2025, demanding constant vigilance and adaptation from organizations and individuals alike. As attackers leverage advanced technologies like AI and machine learning, phishing attempts have become increasingly sophisticated, personalized, and difficult to detect. The surge in AI-powered attacks, coupled with the expansion of attack vectors beyond traditional email to include social media, messaging apps, and even voice communications, has made phishing a pervasive threat across all digital platforms.
The landscape is constantly shifting, with billions of phishing emails daily and new techniques like polymorphic attacks and white noise phishing. As social engineering tactics become more refined and targeted, the human element remains a critical vulnerability. Phishing continues to be a significant contributor to data breaches and financial losses, so organizations must adopt a multi-faceted approach that combines advanced technical defenses, continuous employee education, and real-time threat intelligence to stay ahead of this ever-evolving threat. Learn more about partnering with Proofpoint, a global cybersecurity leader in human-centered phishing prevention.
Learn more about Proofpoint Human-Centric Security platform.
Phishing FAQs
How to Report Phishing Emails
If you think you’re the target of a phishing campaign, the first step is to report it to the appropriate people. On a corporate network, it’s best to report it to IT staff to review the message and determine if it’s a targeted campaign. For individuals, you can report fraud and phishing to the FTC.
What Is Trap Phishing?
Phishing has many forms, but one effective way to trick people into falling for fraud is to pretend to be a sender from a legitimate organization. A phishing trap lures users to a malicious website using familiar business references and the same logo, designs, and interface as a bank, ecommerce, or other recognizable popular brands. This is also known as a Watering Hole attack.
What Is Barrel Phishing?
To avoid filters, an attacker might send an initial benign-looking email to establish trust first, and then send a second email with a link or request for sensitive information. Barrel phishing takes more effort from the attacker, but the effect can be more damaging as targeted users feel they can trust the email sender.
How to Spot a Phishing Email
The main goal of phishing is to steal credentials (credential phishing), sensitive information, or trick individuals into sending money. In order to spot a phishing email, always be wary of messages that ask for sensitive information or provide a link where you immediately need to authenticate.
What Is the Most Common Type of Phishing?
Email phishing remains the most common type, with 3.4 billion malicious emails sent daily in 2025. Attackers frequently impersonate brands like Microsoft and Google, using deceptive links to trick recipients into sharing credentials or downloading malware. These emails mimic trusted sources like Amazon or banks, often compelling you to act urgently. Always verify sender addresses and avoid clicking suspicious links, even if the message appears legitimate.
What Are Examples of Phishing?
Phishing examples include deceptive emails claiming to be from banks requesting account verification, fake shipping notifications with malicious links, social media messages with suspicious attachments, and text messages impersonating government agencies. Other common tactics include phony login pages for popular services like Microsoft 365 or Google, fraudulent password reset requests, and urgent messages claiming your account has been compromised. Always verify the sender and avoid clicking suspicious links.











