Overview
Proofpoint researchers have been tracking a new Traffic Distribution System called BlackTDS implicated in the distribution of a variety of malware. BlackTDS is a multitenant TDS tool that has been advertising its services on underground markets since the end of December 2017.
BlackTDS offers a variety of services to its clients that they collectively refer to as a “Cloud TDS.” The operators claim that their Cloud TDS can handle social engineering and redirection to exploit kits (EKs) while preventing detection by bots -- namely researchers and sandoxes. BlackTDS also includes access to fresh domains with clean reputations over HTTPS if required.
The services offered by BlackTDS are summarized in their forum advertisements, the text of which we have left unaltered:
“Cloacking antibot tds based on our non-abuse servers from $3 per day of work. You do not need your own server to receive traffic. API for working with exploit packs and own solutions for processing traffic for obtaining installations (FakeLandings). Dark web traffic ready-made solutions. Placed in 1 click hidden code to use the injection in js on any landings, including on hacked websites.”
“Cost - $6 per day, $45 per 10 days, $90 per month, FREE place on our server, FREE hosting of your file on green https:// domain. 3 DAYS FREE TEST”
* Cloud Antibot Traffic Management System on our non-abuse servers
* API for working with bundles of equities and custom solutions for processing traffic for obtaining installations (Faklendings). Placing your file on a green https: // domain
* Placed in 1 click hidden code to use the injection in js on any landings including on the shells
What we added during the holidays:
* Built-in modes Iframe (a little morally outdated, but asked - we did).
* fake Mirosoft update (breaks the page).
* Fake update Jav and Fake update Flash (the page does not break, the original content is visible).
* uploading a file from your personal account to our server.
* Configure delay for the appearance of fake windows.
* Auto-download when clicking on the window area.
* Updating the Black and Geo databases from 13.01.18.
* increased by breaking through the downloads from 6%-12% to 10%-30%.
* added detailed statistics on users who downloaded the file.
* autostart file in fakes.
And this is only on holidays! We continue to work. Cloud TDS at your service
Figure 1 shows a screen capture of the cost breakdowns and services offered by BlackTDS.
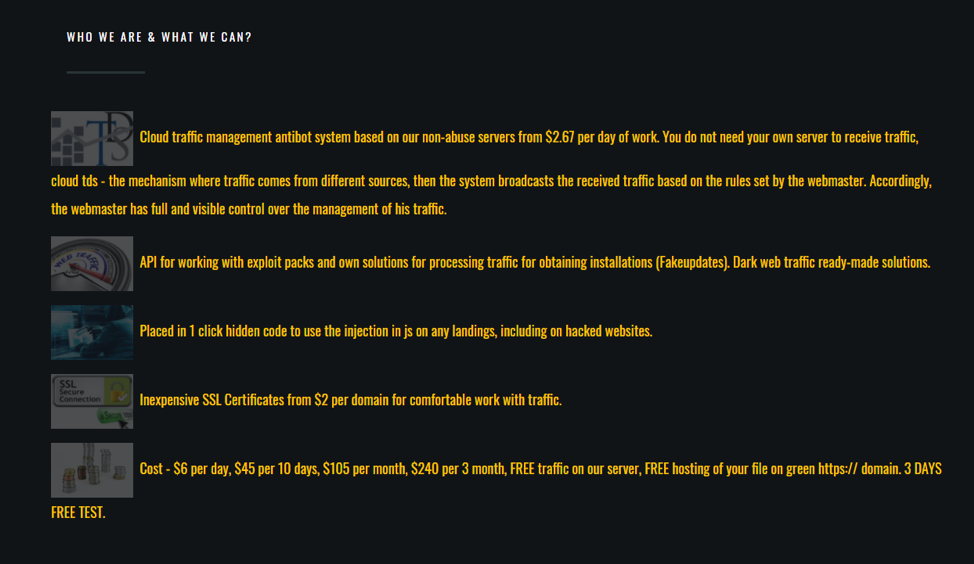
Figure 1: Portion of a BlackTDS advertisement
Threat actors drive traffic to BlackTDS via spam, malvertising, and other means, set up the malware or EK API of their choice, and then allow the service to handle all other aspects of malware distribution via drive-by.
Figure 2 shows a screen capture of the BlackTDS website that includes contact information, localization, and recent updates.
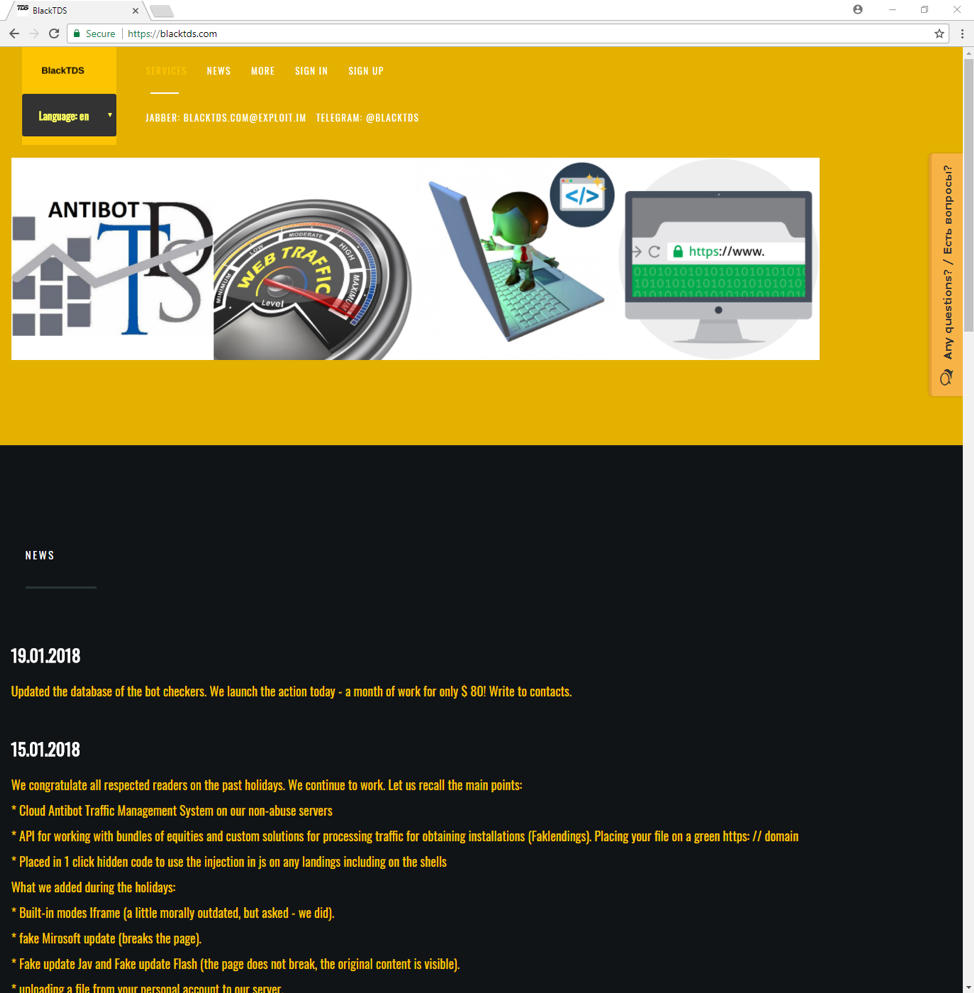
Figure 2: BlackTDS home page
We observed BlackTDS infection chains several times in the wild, distributing malware via fake software updates and other social engineering schemes (Figures 3, 6-8).
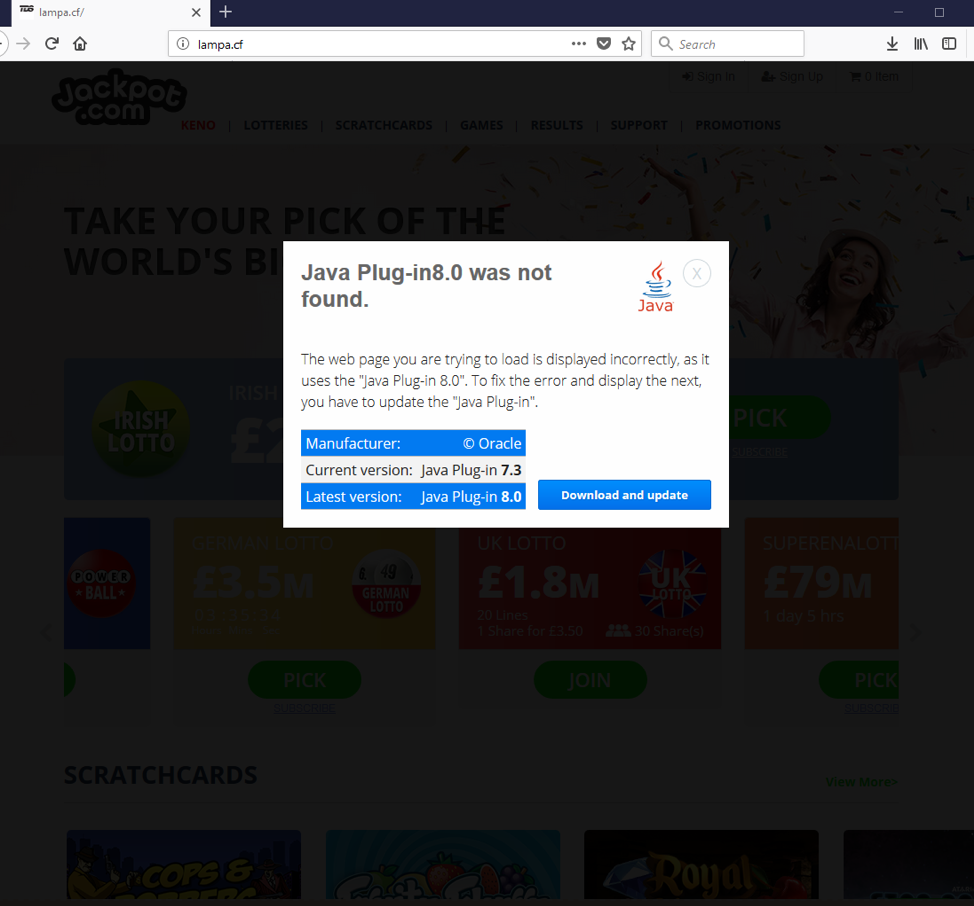
Figure 3: Fake Java Plugin download associated with a BlackTDS drive-by

Figure 4: BlackTDS favicon that appears on all identified sites associated with the TDS
Although identifying BlackTDS sites in the wild was relatively easy based on the presence of a distinctive favicon (Figure 4), effectively associating the traffic with a known actor was difficult and, in some cases, almost impossible.
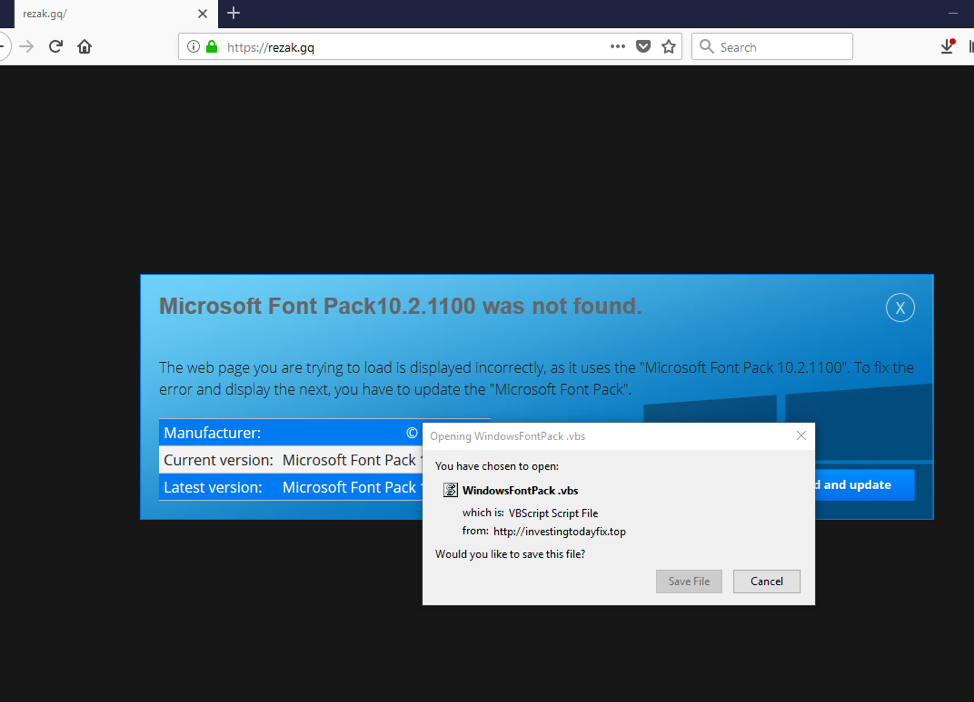
Figure 5: Fake Microsoft Font Pack download associated with a BlackTDS drive-by
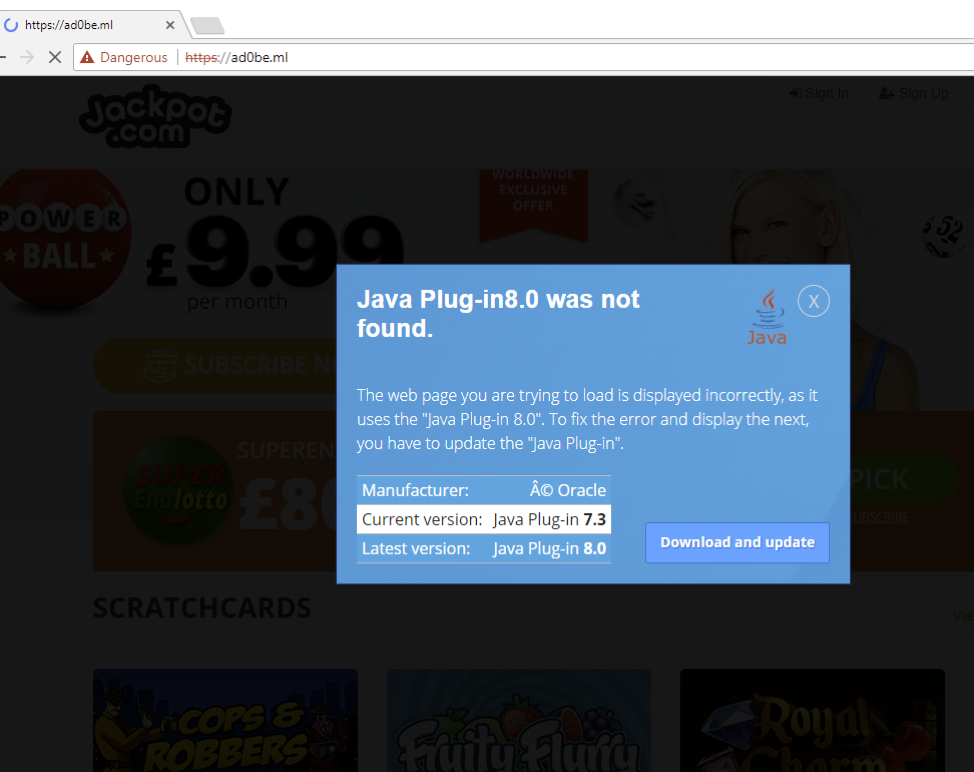
Figure 6: Fake Java Plugin download associated with a BlackTDS drive-by on a typosquatted domain
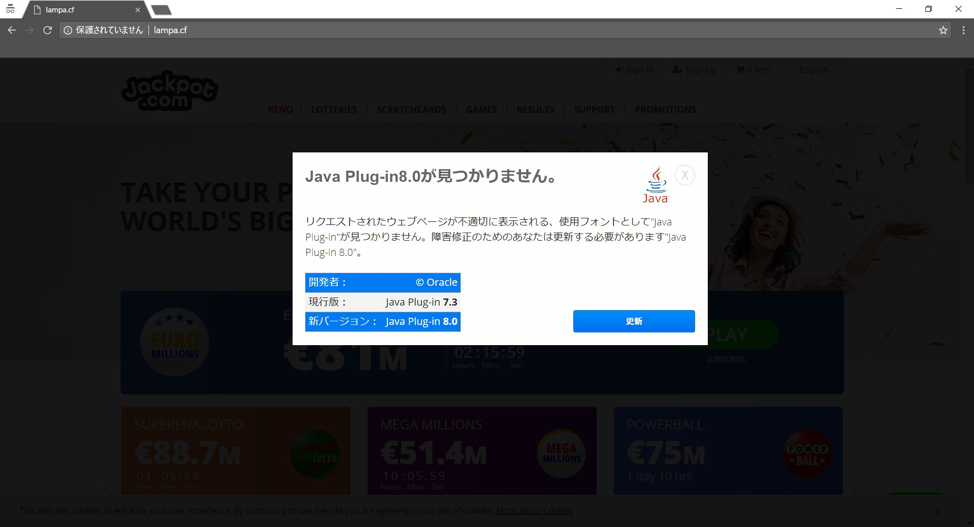
Figure 7: Fake Microsoft Font Pack download associated with a BlackTDS drive-by (source: @Nao_sec)
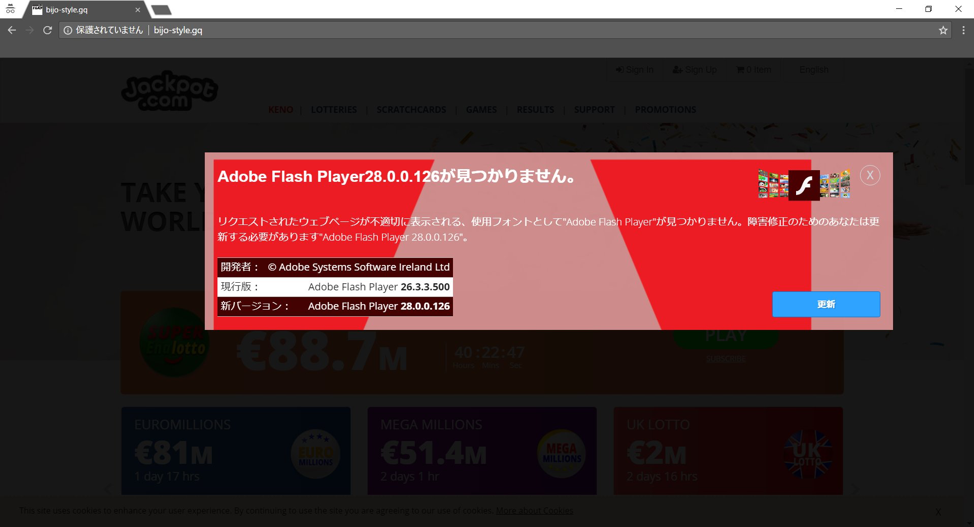
Figure 8: Fake Adobe Flash Player updated associated with a BlackTDS drive-by (source: @Nao_sec)
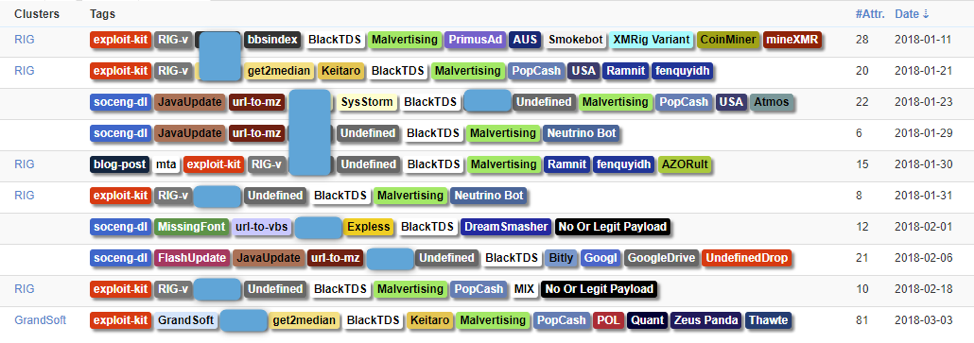
Figure 9: Selection of events we documented involving BlackTDS
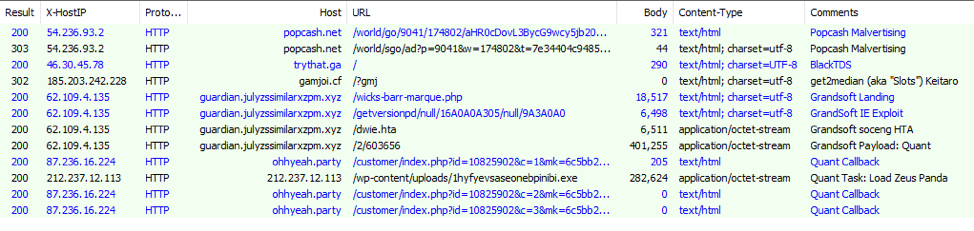
Figure 10: One pass showing a malvertising campaign directing traffic into BlackTDS that ultimately redirected to Keitaro TDS and Grandsoft Exploit Kit
On February 19, we also observed a massive spam campaign from the actor TA505 with PDF attachments containing links to a chain involving BlackTDS before ending on a website purporting to sell discount pharmaceuticals. TA505 has typically distributed ransomware and banking Trojans at enormous scale, making this particular campaign unusual.
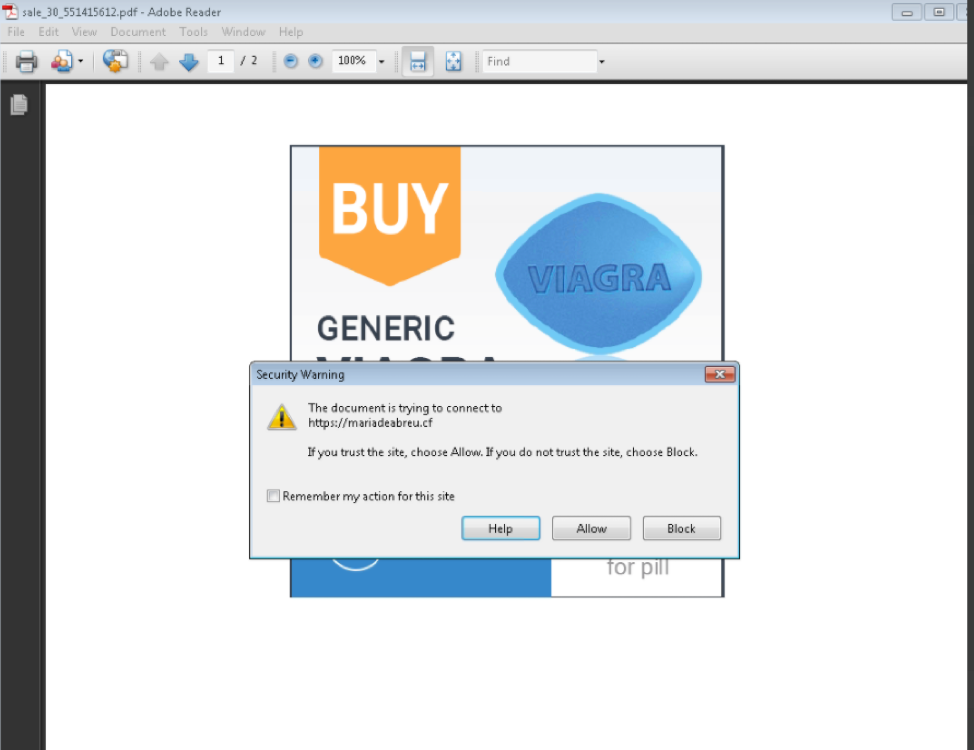
Figure 11: HTTPS URL to BlackTDS in malspam - February 19, 2018
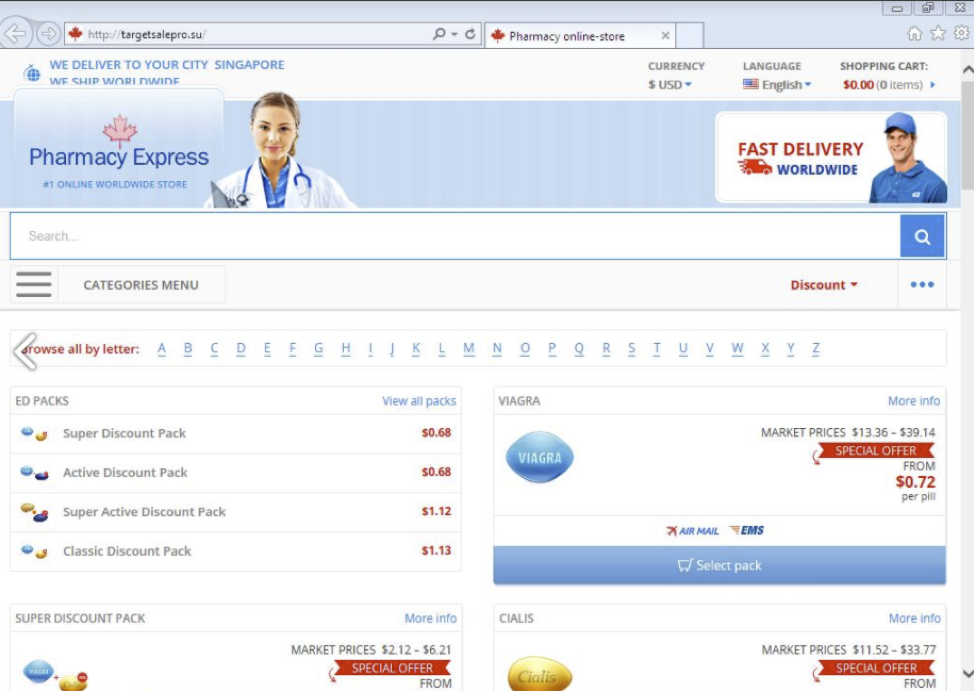
Figure 12: Pharma website receiving the traffic after BlackTDS filtering
It is worth noting that we determined which actor was operating the service itself based on an artefact of this TDS since at least February 2017. We associate the artefact with a traffer we track under the name “BBSindex”.
Figure 13 shows infection activity we associate with both BBSindex and BlackTDS:
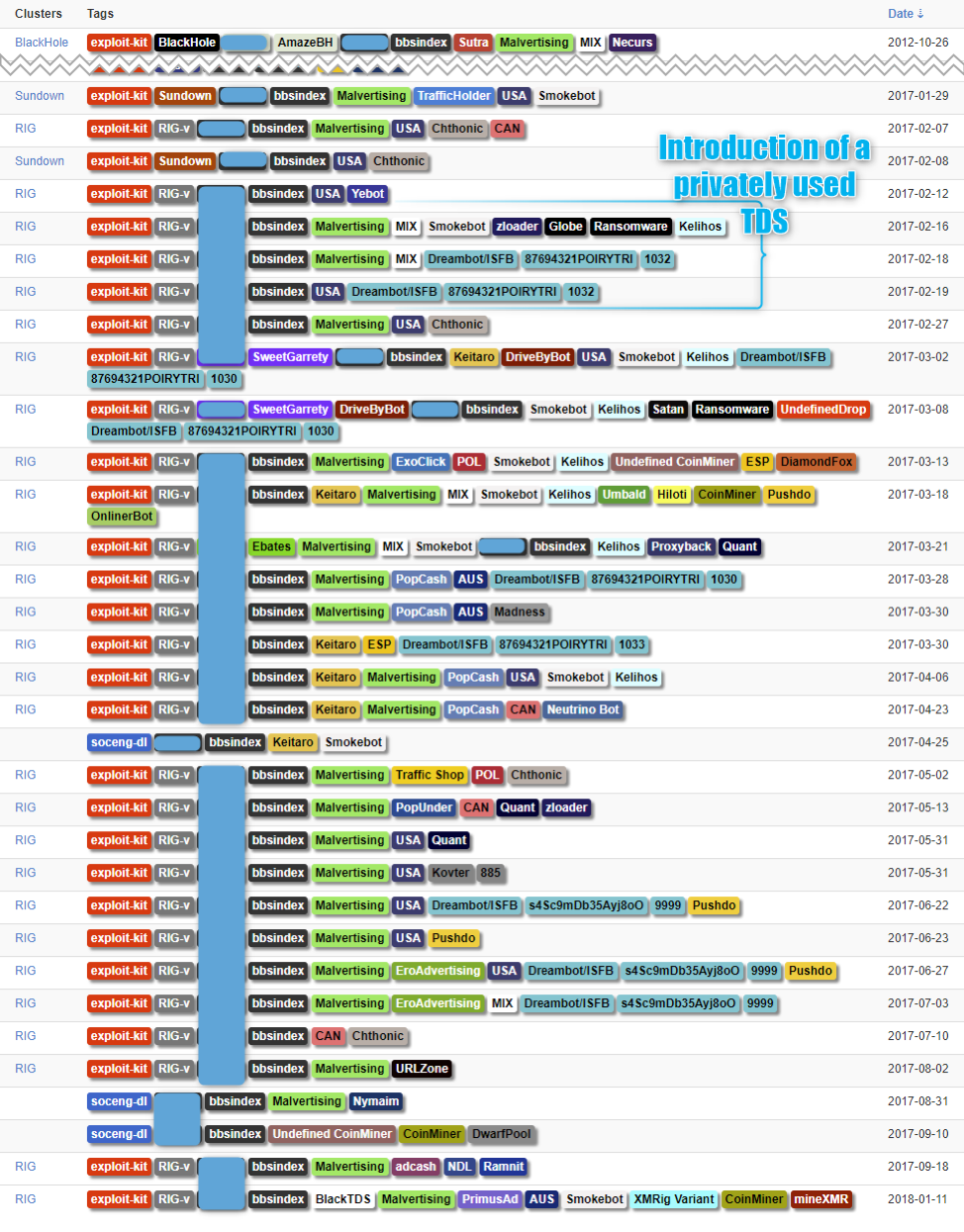
Figure 13: Overview of “bbsindex” traffic activity. We believe the artefact tied to BlackTDS appeared between February 12-19, 2017
BlackTDS runs on a single IP address that proved simple to track. However, at the end of February, after being heavily flagged in many reputation services, the organization changed the IP address.
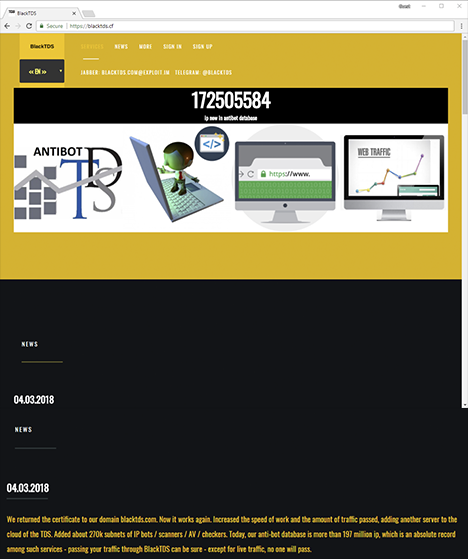
Figure 14: New BlackTDS home page, retrieved March 4, 2018
Conclusion
Like so many legitimate services, we are increasingly observing malicious services offered “as a Service.” In this case services include hosting and configuration of the components of a sophisticated drive-by. The low cost, ease of access, and relatively anonymity of BlackTDS reduce the barriers to entry to web-based malware distribution. With full support for social engineering and the flexibility to either distribute malware directly or simply redirect victims to exploit kit landing pages, BlackTDS demonstrates the continued maturation of crimeware as a service. Moreover, it demonstrates that, despite their steady decline, EKs and web-based attacks are not a thing of the past. On the contrary, web-based attack chains are increasingly incorporating social engineering, taking advantage of both existing underlying infrastructure and human fallibility rather than short-lived exploits.
Acknowledgement:
Thanks to @nao_sec for sharing the Japanese regionalized version of the Social Engineering templates.
Indicators of Compromise (IOCs)
|
IOC |
IOC Type |
Description |
|
blacktds[.]com |
Domain |
Customer facing domain from middle of december 2017 to end of february 2018 |
|
blacktds[.]cf |
Domain |
Customer facing domain starting 2018-03-04 |
|
88.99.48[.]65 |
IP |
Both Victim and Customer facing IP from middle of december 2017 to end of february 2018 |
|
46.30.45[.]78 |
IP |
Both Victim and Customer facing IP starting 2018-03-04 |
|
en.sundayloop[.]com| 193.70.73[.]251
|
domain|IP |
BBSindex redirector from 2017-02-06 till 2017-09-18 (earlier version of BlackTDS in private mode) |
|
6a207ea9d9e60a9bc9de7b1c2b87e06fa85ac31cbbf8c69e1627408c8f3d2b7f |
SHA256 |
PDF attachement with link to blackTDS - 2018-02-19 |
