Declines in exploit kit (EK) activity over the course of 2016 have been well-documented, dropping overall by roughly 94% since a January 2016 high (Figure 1). Now it appears, however, that social engineering may be breathing new life into this once-lucrative market.
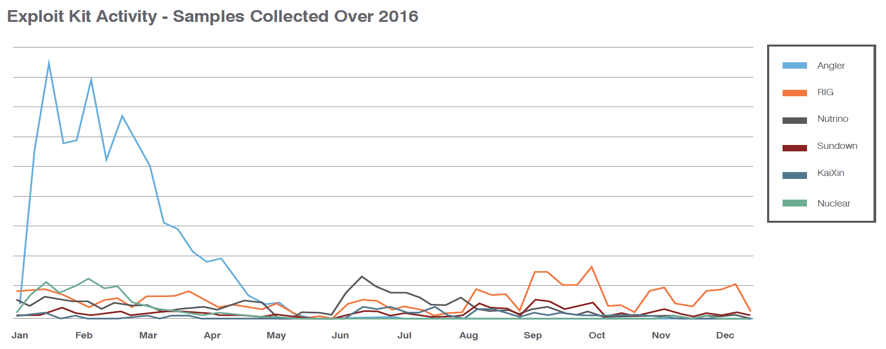
Figure 1: Activity in the top 6 exploit kits over 2016
The arrest of high-profile actors behind the Angler exploit kit in early 2016, and its subsequent disappearance, had a dramatic effect on the EK market. Angler was by far the most widely used and popular EK and while some actors moved to other kits, many just turned to other methods of spreading malware. However, there is another more important reason behind the dramatic decreases in EK activity: software exploits are simply less effective than they used to be. Vendors patch vulnerabilities quickly, organizations patch their systems regularly, and it has simply become more difficult for cybercriminals to justify investments in exploit development.
In particular, Adobe Flash vulnerabilities were the basis for many exploits over the years. As developers move toward more secure platforms, like HTML5, and browsers such as Chrome and Firefox begin blocking Flash Player by default, threat actors must look elsewhere for usable exploits. This explains why Proofpoint researchers are observing new exploits and attack chains that use social engineering, steganography, and other techniques that do not rely on Flash.
For example, our analysis of the AdGholas malvertising activity last year examined ways that the group used careful targeting and filtering to expose as many as one million client machines a day to malvertising while concealing the activity from researchers. At the same time, the group used steganography -- a technique for concealing code in images -- and seemingly low-value information disclosure vulnerabilities with multiple EKs and malicious payloads.
Threat actors are also looking to social engineering to increase the effectiveness of web-based attacks as the zero-days they have traditionally exploited become more difficult to identify and monetize. Recently, for example, Proofpoint researchers discovered a new social engineering component used by EITest, a well-known infection chain that generally relies on compromised websites to drive traffic to exploit kits. In this case, users were filtered by browser and user agent and tricked into downloading and installing malware.
Targeting Chrome users on Windows 10 in particular, the victims were presented with unreadable pages and the option to download a bogus font pack that would “solve” the fake problem of unreadable pages. The font pack in fact installed Fleercivet ad fraud malware. To our knowledge, only one vulnerability has ever been successfully exploited on Chrome, making social engineering approaches necessary to infect Chrome users. In contrast, Internet Explorer users who encounter this attack chain are redirected to traditional EKs.
More recently, we observed a social engineering path added to Magnitude EK, an exploit kit operating primarily in Asia. The animation in Figure 2 provides the end user view of the social engineering attack on Windows 10 Internet Explorer users. Targeted web surfers receive a message that Windows Defender virus and spyware definitions could not be updated, and are led through a series of actions that ultimately results in Cerber ransomware infection.
Again, though, this attack does not rely on a software exploit but rather on users to click through the steps of the social engineering, download the software, and install it themselves. In this case, the EK and a filtering and redirection instance we call Magnigate handle the traffic , but humans carry out the malware installation.
Figure 2: Animation of “Windows Defender Critical Update” social Engineering used by Magnitude actors - March 01, 2017
In the mobile realm, mobile attack kits like Pegasus are targeting vulnerabilities in mobile devices, but with mobile exploits expensive and in short supply, here too we see exploit kits evolving to address larger potential attack surfaces offered by non-PC devices. We recently observed DNSChanger EK attacking vulnerable home routers via normal communication channels between browsers and the routers. DNSChanger did not make use of browser exploits, and was able to leverage vulnerabilities in the router even through fully patched web browsers. Once the home router was compromised, however, DNS redirection exposed every device behind it to malvertising and further attacks, regardless of operating system or vulnerability.
As noted in our 2017 Cybersecurity Predictions we expect exploit kits to increasingly give way to "human kits." The emergence of social engineering in the EK space suggests that threat actors will find new ways to use the underlying technology to distribute malware with assistance from their human victims.
As regular patching regimens have rendered traditional exploits less effective, social engineering in web-based attacks increases the importance of other security measures. Regular backups are critical data protection measures in case of infection, especially with ransomware, while robust user education can help individuals spot social engineering and respond swiftly and appropriately. Avoiding ads and clickbait can improve user and network safety while implementation of multilayered gateway and endpoint security remains a best practice.











