Overview
Affiliate marketing -- the practice of having “downstream” individuals market and sell products on behalf of so-called upstream managers, thereby dramatically extending their reach -- is hardly a new concept. Pyramid schemes and multi-level marketing have worked in various forms for many years and Amazon built a solid and profitable piece of their business in the late 1990’s based on their affiliate program. Affiliate models in the modern sense exploded at the same time as e-commerce, but, like many legitimate web-based ventures, have been co-opted by cybercriminals and less-than-scrupulous actors.
In reality, a very large percentage of the spam emails that we see is used to drive traffic to affiliate marketing sites, whether for pharmaceuticals, work-from-home schemes, books, dating sites, or any number of services that pay affiliates for clicks through to their sites. Unfortunately, the impact of the affiliate model extends far beyond the massive volumes of spam required to turn small payments per click into meaningful income.
Spam
Most affiliate marketing operates on a pay-per-click or pay-per-action model. Amazon, for example, has a robust, tiered payment model for actual purchases on their site resulting from affiliate links. As such, the payments are reasonably generous, ranging from 1-10% depending on the item, but it often takes a high volume of links and impressions to generate a sale if affiliates are not carefully targeting a relevant audience. Other affiliate programs pay by the click but at a much lower rate, requiring extremely high volumes of clicks to generate reasonable income. In the latter case in particular, affiliates often rely on large spam campaigns to create a sufficient quantity of clicks.
As spam actors become more sophisticated, they often rely on strong brands and enticing subject lines to increase the likelihood of recipients clicking on links in spam emails. These tantalizing links may take recipients directly to affiliate pages selling the goods and services described in the email or, more likely, to an affiliate site. Figure 1, taken from a blog in which we examined election-related spam, uses the Trump brand and typical click-bait to bring recipients to a site selling an e-book.
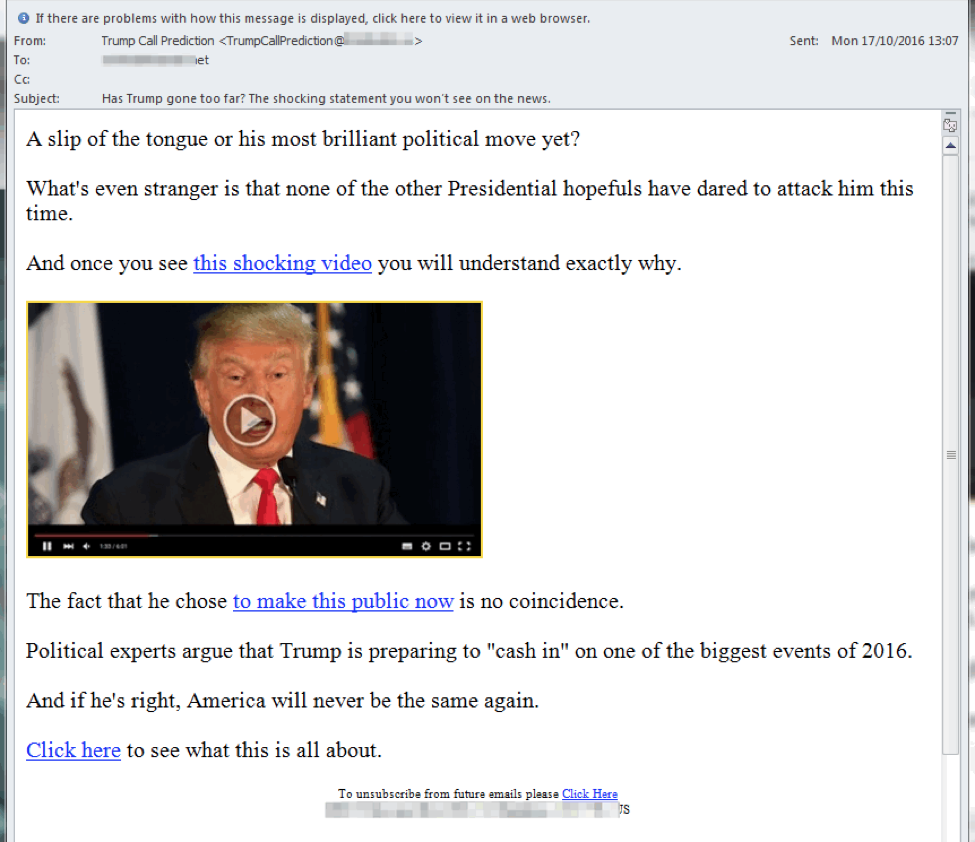
Figure 1: Affiliate spam using a Trump-related lure to bring people to a site selling an e-book
In other cases, links may direct recipients to pages with a variety of affiliate links, giving the actor the opportunity to generate more clicks, and therefore more cash, for each click.
Much of this spam is caught by spam filters or ignored by savvy users. High volume spam campaigns, though, ensure that at least some recipients will click through, generating revenue for the spam actors. Because these actors generally buy email lists to distribute spam, large-scale campaigns also serve the purpose of identifying invalid email addresses, as those emails that bounce back can be cross-referenced with email lists and removed from future campaigns.
Ad-fraud and click-fraud malware
As spam filters become more effective, the clicks and conversions necessary to generate income for affiliates are harder to come by through email alone. Malware designed to open web browser sessions in the background and automatically click links and ads can dramatically increase the number of clicks for which affiliates are paid. So-called “ad-fraud” or “click-fraud” malware can be a simple standalone malicious application or, more commonly, can join an infected device to a larger botnet. In either case, the malware simulates the actions of legitimate users from clicking the ad to viewing the associated landing page. In some cases, the malware also completes a form on the landing page with bogus data to ensure that the click counts as a "conversion" and the ad host or intermediate network are paid accordingly. When the traffic brokers, ad-hosting sites, or other elements of the extended advertising ecosystem are fraudulent, it is actually the cybercriminals who get paid for the traffic they generate via the ad-fraud malware.
Click-fraud malware is often distributed through the same mechanisms as affiliate spam and dubious online ads, namely email and exploit kits. Fleercivet, for example, is itself distributed through an affiliate model via multiple vectors. Its primary purpose is to produce fraudulent traffic to generate revenue for the owner by visiting low quality and potentially fraudulent search sites and "clicking" through ads.
Kovter malware, on the other hand, is known for being especially difficult to detect and remove once installed, allowing it to perform click-fraud in the background without the user’s knowledge and creating a recurring revenue stream for actors distributing the malware whenever their PCs are connected to the Internet. Figure 2 shows a screenshot of a document attachment from a recent Kovter campaign; when the user opens the document and enables macros according to the instructions in the document, the macros install Kovter.
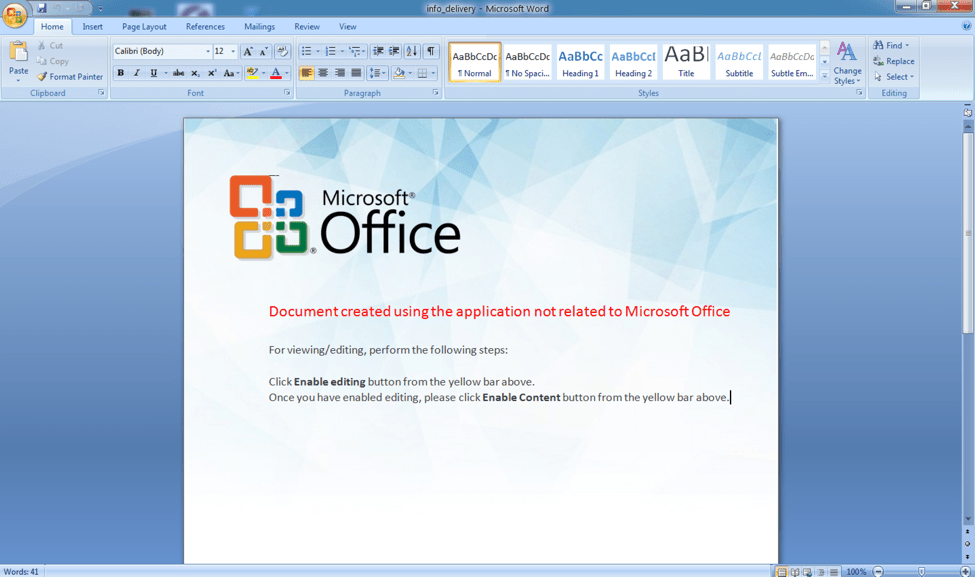
Figure 2: Malicious macro document used to distribute Kovter malware from a recent campaign
Pay-per-install malware
Outside the realms of more traditional spam, affiliate models have also found their way into malware distribution. In the case of malware like Locky, Kovter, many strains of “scareware”, and a variety of different malware families, threat actors are paid based on the number of PCs they infect. Again, these infections can occur through vectors including email and malvertising and, as with affiliate spam, the actors distributing them benefit both from substantial scale and smart targeting and social engineering. Often, the “kingpin”, as the upstream seller is called, can make money not only on the installed malware itself but also by selling access to infected PCs for use in larger botnets, providing sufficient funds to pay affiliates for distributing the malware through the vectors of their choice.
Conclusion
The affiliate model - whether for email marketing or malware distribution - encourages threat actors to operate at significant scale. Payments per-click on links in emails or banner ads on websites are generally very small but accumulate quickly when spamming hundreds of thousands or millions of users. Entire categories of ad-fraud malware have emerged to automatically and fraudulently click these types of links and ads, generating additional payments for the actors. At the same time, actors are recruiting affiliates to distribute malware on a pay-per-install basis, again, encouraging large-scale malicious spam and malvertising campaigns to infect as many machines as possible.
While most affiliate models are wholly legitimate and potentially lucrative for website operators, many others rely on fraudulent extended advertising networks and ecosystems. For organizations and end users, significant financial motivations mean that malicious mail and even run-of-the-mill spam are not going away anytime soon.











