Insider Threat Response
 Information Protection
Information Protection
Accelerate Incident Response with Proofpoint ITM
62% of all insider threat incidents are accidental, not with malicious intent. Why wouldn’t you coach such insiders on security best practices in real-time?
Workflows and easy to understand evidence tailored for user-driven events that require collaboration with teams outside IT and across the digital productivity stack.
Irrefutable visual evidence of wrongdoing
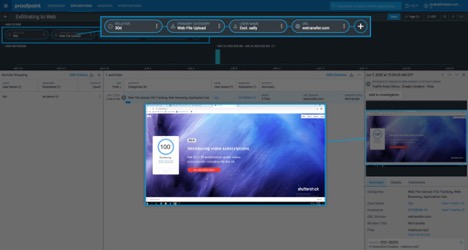
You need clear and irrefutable evidence when insiders commit highly risky behavior on endpoints, servers, and desktop, web and cloud applications, and with files and data.
ITM can visually capture insider activity as screenshots before and after the threat signal(s). With insider threat response you now have irrefutable evidence and compliance documentation that are understood by any team – HR, Legal, Privacy, business units and beyond.
Endpoint specific remediation options
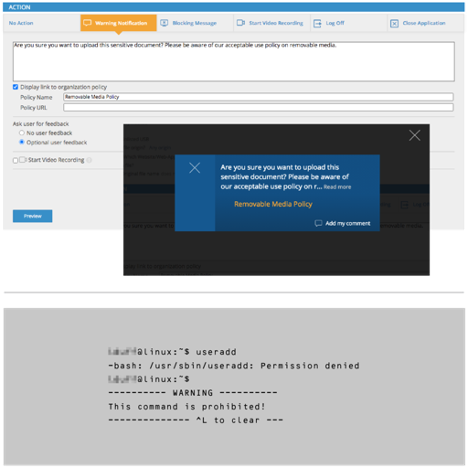
With insider threat response you can coach better security awareness in real-time with optional policy reminders and warning prompts that tie best practices to security violations. No more generic advice!
On Linux/UNIX machines, block risky command execution to stop accidental deletion of files, folders and database rows, inhibit privilege sprawl and block risks of IT sabotage.
Share alerts and evidence with HR, Legal, IT, business units and more
With insider threat response you can package irrefutable evidence as summary reports with step-by-step activity screenshots when you share outside the team. You now have irrefutable evidence and compliance documentation that are understood by any team – HR, Legal, Privacy, business units and beyond.
