Key takeaways:
- The effectiveness of AI models depends on massive volumes of real-world threat data and an understanding of the threat landscape.
- AI-only tools don’t perform as well as defenses with layers that use a variety of AI techniques and controls.
- Specialized AI models can target specific problems, such as language analysis and relationship graphing. This enables more precise detection of complex threats.
Artificial intelligence is everywhere in cybersecurity marketing today. Every vendor claims to be “AI-powered,” “AI-first,” or “AI-native.” But as organizations increasingly rely on AI to protect their people and data, one uncomfortable truth is becoming clear: not all AI is created equal—and in email security, that difference matters more than ever.
Email remains the No. 1 attack vector for cybercriminals. It’s where phishing, business email compromise (BEC), malware delivery, and credential theft all begin. While AI has dramatically improved our ability to detect and stop these attacks, success depends not on whether AI is used, but how it is applied.
Email security: an early AI success story
Long before generative AI (GenAI) and large language models (LLMs) started being used by everyone, machine learning (ML) was working on email security. That’s partly because it was an ideal problem for it to solve. Early ML techniques, such as Bayesian analysis, were able to deliver real value by learning from large datasets of known “good” and known “bad” emails. These systems could identify patterns, adapt over time, and improve detection accuracy at scale.
As AI technology evolved, so did its effectiveness. More advanced models enabled deeper analysis of language, intent, and context. And this unlocked the ability to detect increasingly sophisticated threats. Yet despite these advances, one principle has remained constant: AI doesn’t work in isolation.
AI must be taught. And this requires two things that are difficult to replicate:
- Deep expertise in the problem domain
- Massive volumes of high-quality, real-world data
Without both, even the most modern AI models struggle to deliver consistent, trustworthy results.
Why narrow, targeted AI works best
One of the most common misconceptions about AI is that bigger is always better. In reality, AI performs best when it is applied to specific, well-defined problems. This is especially true when it comes to cybersecurity.
That’s why a layered detection strategy is so effective. Instead of asking AI to determine whether everything is malicious, strong cybersecurity platforms first eliminate the obvious threats using deterministic and heuristic controls. These layers handle the “known knowns.” As a result, AI can focus on what it does best: identifying subtle, complex, and previously unseen attacks.
Gartner®described this layered approach with the graphic below, which is from its research report “Overcome AI-Powered Attacks by Leveling Up Your Email Security Platform” by Nikul Patel, Deepak Mishra, Max Taggett.
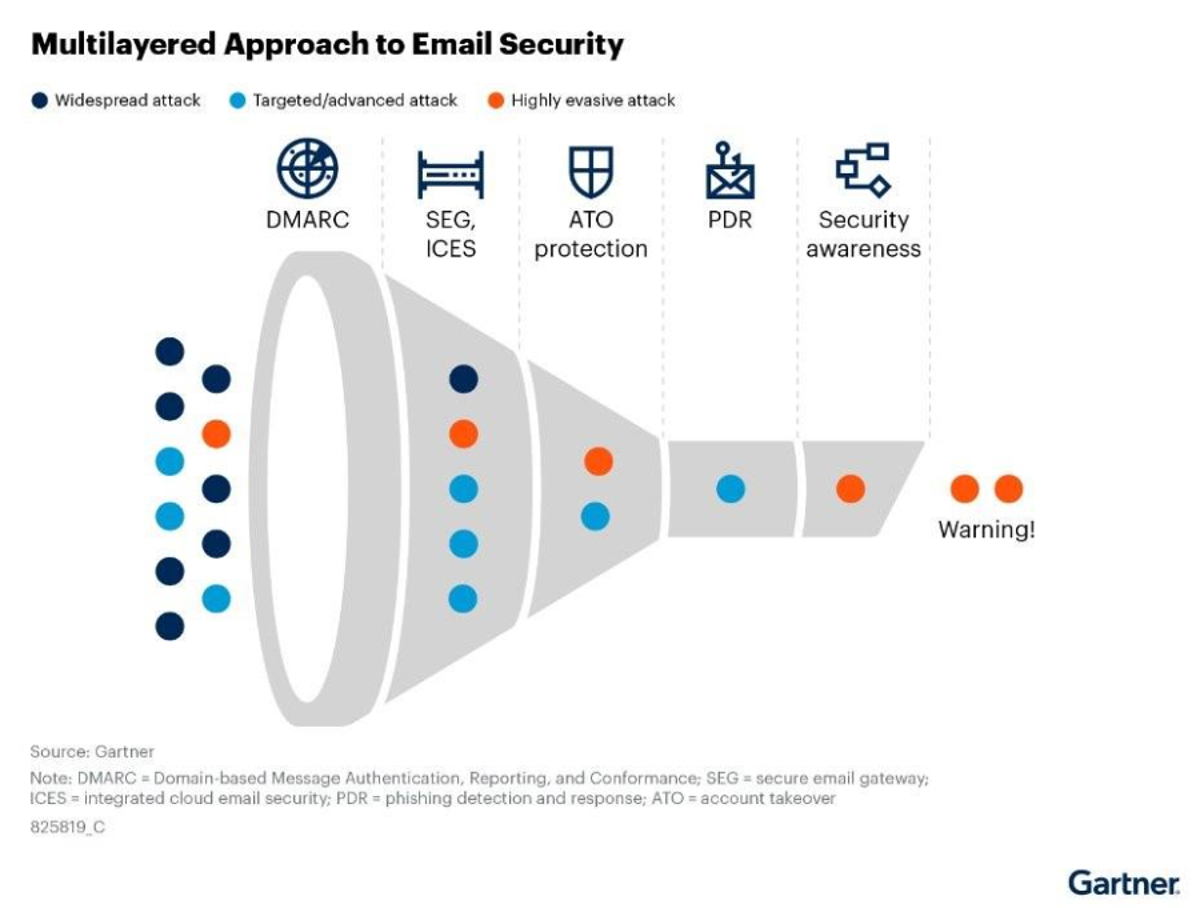
The power of a layered defense
Proofpoint’s approach to email security exemplifies this principle. Over years of defending organizations against real-world attacks, Proofpoint has built a set of detection layers that work together to stop threats at every stage. These layers include controls for:
- Connection-based checks such as domain reputation, SPF, and DMARC
- Identity and spoofing detection to identify impersonated senders and lookalike domains
- Content analysis to detect malicious URLs, weaponized attachments, and files containing embedded links
- Behavioral and contextual analysis informed by evolving attacker techniques
All of these layers use a variety of techniques, including AI. Together, these controls identify the vast majority of known attack methods that are used by threat actors today.
This layered approach dramatically reduces noise and false positives. At the same time, it ensures that clear-cut threats are handled quickly and efficiently. Most importantly, it allows AI models to concentrate on the hardest problems to solve—the highly targeted, socially engineered attacks that are designed to evade traditional detection.
AI where it matters most
When AI is freed from having to solve everything at once, it becomes far more powerful. With rich context from layered detections and unmatched threat intelligence, AI can:
- Understand nuanced intent and social engineering
- Correlate signals across messages, users, and campaigns
- Identify attacks that don’t match known patterns
Proofpoint’s advanced AI-powered engines work together. Each one focuses on a specific problem. We call this ensemble Proofpoint Nexus®.
- Nexus LM™ (Language Model) detects BEC and sophisticated phishing attacks.
- Nexus RG™ (Relationship Graph) identifies subtle behavior changes in user communication.
- Nexus TI™ (Threat Intelligence) understands attackers’ tactics and techniques to proactively protect against new threats.
- Nexus CV™ (Computer Vision) detects the threats that are hidden in visual elements such as QR codes, phishing sites, and fake login pages.
- Nexus ML™ (Machine Learning) uses dynamic and adaptive learning techniques to detect unknown anomalies.
The result is more accurate detection. You get stronger protection without your business operations being disrupted.
The limits of “AI-only” security
In contrast, vendors that rely purely on AI-driven detection face significant challenges. Without layered controls, their AI models must be broader and more generalized. They also lack access to the scale of telemetry, historical data, and real-world attack visibility required to train highly accurate models.
Without depth and diversity of data, AI-only approaches to cybersecurity struggle to keep pace with rapidly evolving threats. They miss context, generate inconsistent results, and often introduce higher false positive rates. And that means security teams must choose between risk and usability.
AI is a tool—not a strategy
AI is undeniably one of the most powerful tools in modern cybersecurity. But it is just a tool.
True protection doesn’t come from AI alone. It comes from combining AI with purpose-built detection layers, decades of threat intelligence, and deep expertise in how attackers actually operate. When AI is used as part of a broader, thoughtfully designed security architecture, it delivers transformative results.
Because in email security—and cybersecurity as a whole—success isn’t about having AI.
It’s about using the right AI, in the right way. To do a deep dive into the importance of AI in cybersecurity, download our e-book: Cybersecurity’s AI Tidal Wave.
Proofpoint Nexus detects threats with 99.999% efficacy. Learn more.











