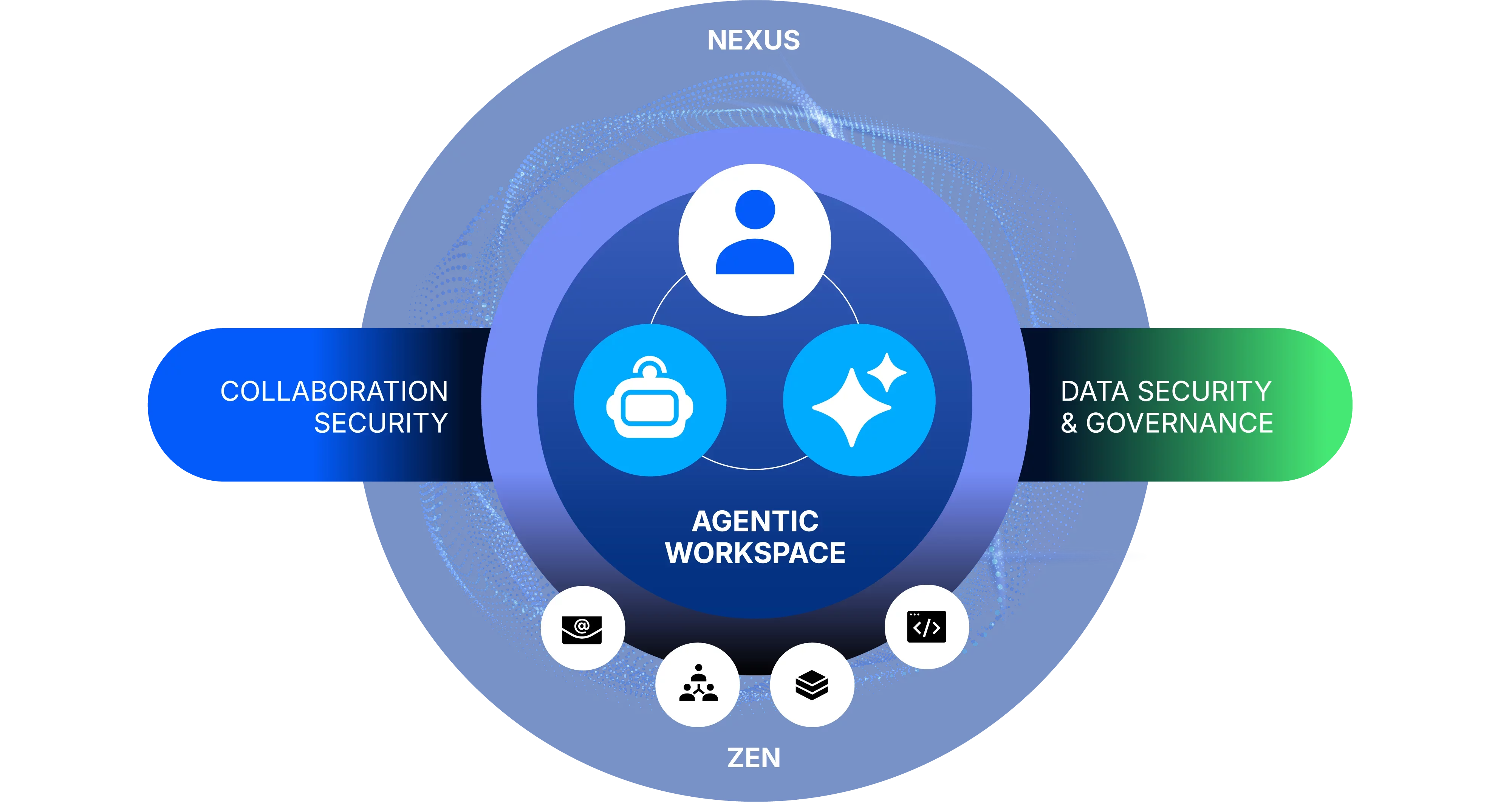
The Proofpoint Platform
Solving the complete set of needs in human and agent-centric security
Employees work in different ways, within different environments and with different tools—from finance teams using collaboration apps at home on their mobile devices to product designers accessing files stored in the cloud.
And in the new agentic workspace, it’s no longer just how people interact—GenAI tools and AI agents are reshaping how work gets done.

But whatever the work situation, people and the AI tools they rely on experience risk—risk from the threats that are targeting them and the risk in the data they interact with.
With the Proofpoint cybersecurity platform, organisations can protect people, data and AI by taking a human and agent-centric approach. Our cybersecurity platform provides best-of-breed solutions to solve critical concerns—stopping threats for secure collaboration, defending data, and governing AI.
Proofpoint technologies powering human and agent-centric security
Each of these critical solutions are powered by three core technologies from Proofpoint.
The first is our market-leading AI models and detection techniques collected under an ensemble called Proofpoint Nexus®. This is the foundation of our advanced cybersecurity platform, providing seamless, multi-layered protection through advanced AI, and real-time threat intelligence models. It protects your organisation from every angle to keep you ahead of threats, and it is the core of the Proofpoint security ecosystem.

Proofpoint Zen™ identifies and mitigates risk across your entire digital environment

The second piece of technology that empowers all four solutions is Proofpoint Zen™. Zen includes all of our end-user facing technologies that alert, guide and empower your end users to be resilient and guided away from risky behaviour and human-targeted attacks.
Zen identifies and mitigates risk across your entire digital environment, so your team can work without fear of cyberthreats. And it provides you with a level of protection and peace of mind that is unmatched in the industry.
Proofpoint Satori™ powers agentic security operations
The third technology is Proofpoint Satori™, featuring Proofpoint Satori™ Agents and Proofpoint Satori™ MCP Access. Proofpoint Satori AI agents act as a force multiplier for security teams running Proofpoint solutions. The agents automate manual and repetitive tasks such as triaging data security alerts or reviewing user-reported suspicious emails. This frees analysts’ time for complex investigations. Proofpoint Satori Agents can also perform value-add tasks, such as recommending attack-informed phishing simulation campaigns tailored to your company’s environment.
Proofpoint Satori MCP Access opens up a new world of agentic integrations. It leverages the Model Context Protocol (MCP) to efficiently and expediently connect Proofpoint Satori Agents with other leading solutions, such as Microsoft Copilot and CrowdStrike Charlotte. This helps you optimise security operations across your enterprise security fabric.

Threat actors continue to find new ways to exploit human and agent vulnerabilities to achieve their nefarious goals
Defend against threat actors for secure collaboration
From using to craft well-written messages to combining collaboration tools and web links to perform impersonation and supplier-related breaches, there is no end to what will come up with next.
Proofpoint is the only security partner that brings together an end-to-end approach to stop all human and agent-targeted attacks—from email to collaboration tools to web applications.

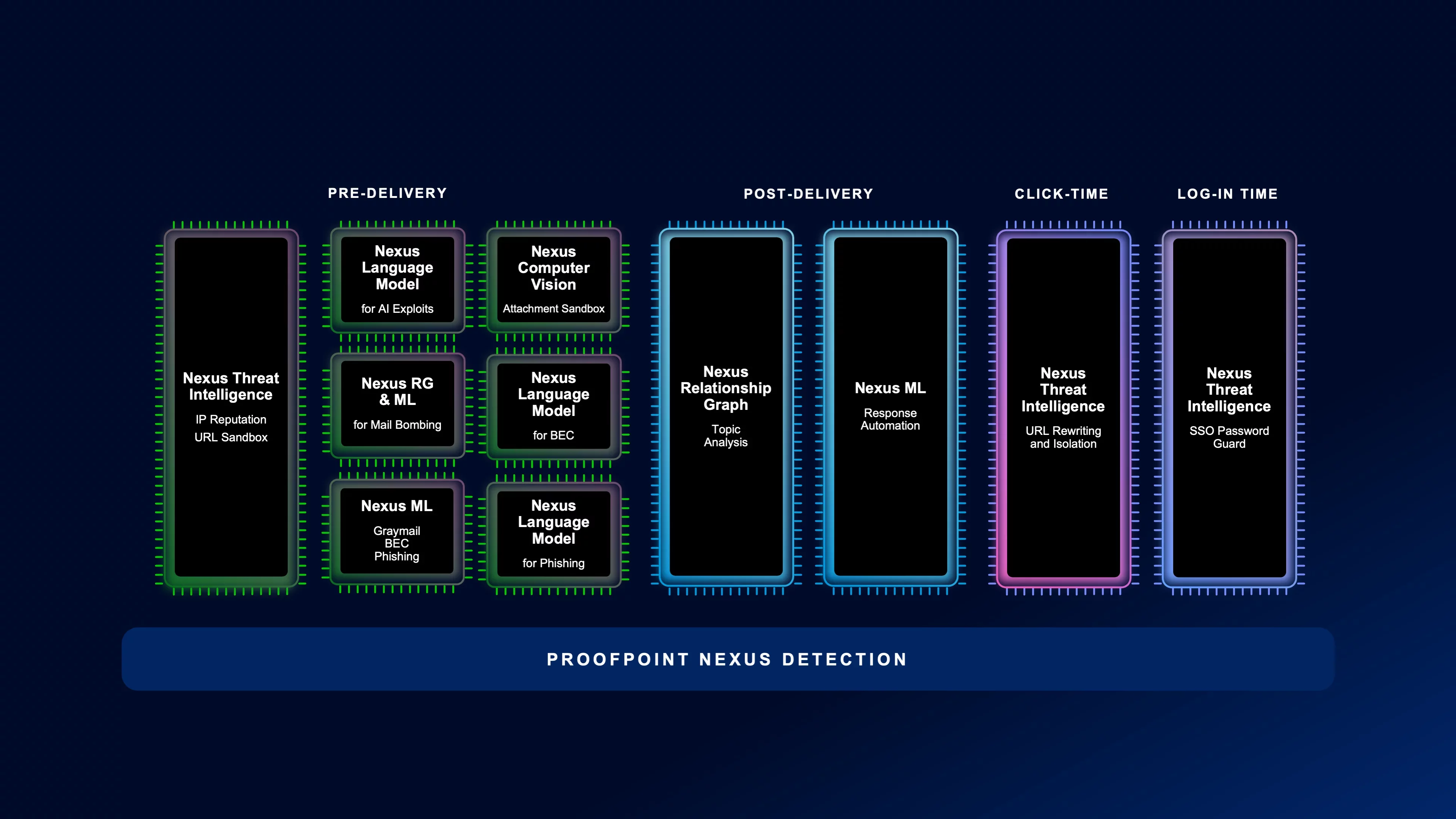
The Proofpoint cybersecurity platform integrates a multi-layered approach that covers the whole threat attack chain—from pre-delivery to post-delivery and to click-time—providing the most effective detection of BEC, phishing and spam messages.
Pre-delivery
Detect malicious intent of email messages using high-performance machine learning and large language models with Proofpoint Nexus®.
Post-delivery
Analyse and remediate messages in the inbox through behavioural analysis and API-based integrations into Microsoft 365.
Click-time
Get time-of-click protection for links included in emails through industry-leading threat intelligence and machine learning-powered sandboxing.
As a single strategic partner invested for your needs today and into the future, Proofpoint cybersecurity platform consolidates all your threat protection needs into a single offering.
Traditional by itself is no longer enough to sustain behaviour change. You need a new approach to help keep your users resilient against human-targeted attacks.

Proofpoint ZenGuide enables security teams, small and large, to automate and scale personalized learning paths based on an individual’s unique risk profile, behaviours and role. It uses people-risk insights across the Proofpoint ecosystem to understand human risk. And it delivers relevant interventions that build security champions and reduce risky behaviours.
Adopt risk-based learning that enables organisations to move beyond compliance-driven programmes to provide targeted, context-aware education that addresses specific risks and behaviours.
Scale awareness and behaviour change programmes by automatically enrolling identified risky employees into a targeted, relevant set of education, interactive simulations and other interventions that adapt to behaviours.
Increase employee engagement with in-time learning moments and an employee dashboard that recognises and rewards good security practices, reinforcing desired behaviour and fostering a security-minded culture.
Careless users and ungoverned agents mishandle it. Malicious users walk out the door with it. And compromised user accounts are hijacked to steal it. The unfortunate story of data loss and insider threats never ends because of old technology approaches.
Learn more
A human and agent-centric approach
A new approach is needed—one that is human and agent-centric. This approach brings together understanding of data classification, user intent and threat context. And it uses Proofpoint Nexus® to derive insights and automated policy decisions. Only with this new approach and applying it consistently across email, cloud, endpoint, web and tools can an organisation bring under control the risks around their data.

Regulations and governance
In addition to addressing the needs of and , organisations also need to meet the regulatory requirements around their digital communications.
From responding quickly to e-discovery archive requirements to supervising collaboration communications, we bring these capabilities together with Proofpoint Digital Communications Governance. Through a modern cloud architecture, Proofpoint provides an expansive list of connectors to capture communications across different collaboration applications, and applies AI to perform supervision and compliance actions.
Corporate identities are the root of many ways employees work—from cloud accounts in SaaS applications and authentication tokens that access corporate file repositories, to permissions to traverse across the corporate network.
The new threat landscape
Unfortunately, while these empower employees to work with ease, threat actors also have learned to use this power to achieve their own nefarious goals of ransomware, cloud account takeover or . Cloud account takeover, across attack paths and —these are just a few of the many attack techniques that threat actors have developed as we empower people to work however they choose.

Take an integrated approach
Instead of solving this with product silos, an integrated approach is needed. By taking this approach with the Proofpoint cybersecurity platform, every solution to a threat actor technique can be solved effectively. Do you understand the exposed attack path that a compromised user can create? Can you quickly be alerted with high fidelity, and quickly respond to a change in a user’s cloud application account posture?










